Advanced Configuration
This topic describes how to add and modify advanced AFA configuration parameters, as well as a reference of parameters available.
Add a new AFA configuration parameter and value
This procedure descries how to add a new advanced configuration parameter to AFA. Use this procedure to override various system defaults or implement hotfix updates.
Do the following:
-
In the toolbar, click your username and select Administration to access the AFA Administration area.
-
Navigate to Options > Advanced Configuration.
-
Click Add, and enter the name and value of your configuration parameter.
- Click OK to close the dialog, and then OK again to save your changes.
Advanced AFA configuration parameter reference
The following tables list commonly used AFA configuration parameters and their possible values.
Use the alphabetical links below to jump between tables.
A-B | C | D | E-I |L | M | N-R | S-W
| Parameter | Description |
|---|---|
| Active_Change_Backups_Number |
CLI only. Define the number of backup files stored by AFA for Cisco firewalls, Juniper SRX devices, or Panorama devices. Default: 50 |
| AddOnlyChildren |
Determines whether the add_device_to_group and create_device_group SOAP APIs add both the parent and children devices to the group. Possible values:
|
| AFA_URL |
Defines the server used for email notification and other AFA related links. Can be an IP address or host name. For example:
|
| ALGOSEC_EA_ARISTA |
Determines whether AFA administrators can add Arista devices to AFA. Default: FALSE |
| AlgoSec_EA_Azure_ActiveChange |
Determines whether AFA administrators can define ActiveChange options for Azure devices. Default: FALSE |
| AlgoSec_EA_Cisco_ACI_ActiveChange |
Determines whether AFA administrators can define ActiveChange options for Cisco ACI devices. Default: FALSE |
| ALGOSEC_EA_CISCOMERAKI |
Determines whether AFA administrators can add Cisco Meraki devices to AFA. Default: FALSE |
| analyze_only_changed_reports |
Determines whether analysis is always run, even if the configuration has not changed. Possible values:
|
| Auto_Create_Users |
Automatically create user in AFA from LDAP (if LDAP is defined).
|
|
AUTOREMOVE_REPORT_NAS_CONFIGURED |
Customers with NAS configured might experience disk space issues due to a non-optimized file cleanup. In such a case, setting this parameter to true could potentially resolve this.
|
| AWS_Network_Elements_Parse_From_AFA |
If required, use this parameter to switch between AlgoSec Cloud and Firewall Analyzer as the Network Elements Collection Source.
AWS_Network_Elements_Parse_From_AFA=false Default setting, parses and pushes routing data via AlgoSec Cloud.
AWS_Network_Elements_Parse_From_AFA=true parses and pushes routing data via AFA.
To learn more, see Configuring the AWS Network Elements Collection Source. |
| AWS_Socket_Timeout_Millis | Configures the socket timeout to AWS. A socket timeout monitors the continuous incoming data flow. If the data flow is interrupted for the specified timeout, the connection is regarded as stalled/broken. This only works with connections that have a continuous flow of data. AWS_Socket_Timeout_Millis = X ms. |
| AWS_Connection_Timeout_Millis |
Configures the connection timeout to AWS in milliseconds. AWS_Connection_Timeout_Millis = X ms. |
| Backup_Firewall_History |
Determines whether backup files include change history. Possible values:
|
| BUSINESSFLOW_ADDRESS |
Determines the IP address of the BusinessFlow host, if not local. |
| Enable_Ms_Traffic_Logs_Processing |
Determines whether traffic log collection is enabled using the ms_trafficlogmanager service. Possible values:
|
| Export_Policy_Tab_With_Objects_Content |
Determines whether the exported PDF report's Policy page shows the network object content as well as the network object names. Possible values:
|
| EXPECT_TIMEOUT |
Defines the timeout, in seconds, for processing a single command in the Expect data collection. Default: 120 |
| FailCLIOnMissingUIDs |
Determines whether the CLI is generated even in case of missing UIds in Cisco PIX devices. Possible values:
|
| Fetch_Primary_Routing |
Determines backplane interface between VRs to provide interconnection in order to route traffic when primary routing table is specified. Note: this parameter is relevant for Juniper (SRX) Possible values:
|
| FIP_MAX_DEVICES_SEARCH_PATHS_FOR_DESTINATION_ANY |
Defines a maximum number of devices for which to run a query with a FIP destination of any. Default: 100 |
| FireFlowXmlEncoding |
Determines whether FireFlow XML change files are encoded as UTF-8 or ISO-8859-1. Possible values:
|
| ForceErrorEmailsToAdmins |
|
|
FORTIMANAGER_Auto_Tree_Update_Enabled |
This parameter impacts the general behavior for FortiManager gateways throughout the system.
|
| FWFiles_Directory |
Defines the path of the Analyze from file firewalls. Default: $HOME/algosec/fwfiles |
| Group_Query_Print_Missing_Paths |
Whether to display missing paths table in group query result (useful for FIP troubleshooting)
|
| hide_change_details |
Determines whether to omit change details from emails about new reports and change alerts, for all users. Possible values:
|
|
IPT_Density_Action_Limit |
The maximum density of a sparse object. When this limit is exceeded, the object is considered semi-dense. Default: 50 |
| IPT_Ranges_Number | Divide each hostgroup range to this number of parts. (default is 256) |
|
IPT_Recommendation_Max_Ranges |
Defines the maximum number of CIDR blocks into which IPT will recommend splitting a host object, if the original object contains more IP addresses/ranges than defined in IPT_Recommendation_Max_Subnets_Per_Range. Default: 20 |
|
IPT_Recommendation_Max_Services |
The maximum number of services or applications from which IPT will recommend composing a new object. Default: 20 |
|
IPT_Recommendation_Max_Subnets_Per_Range |
Defines the maximum number of CIDR blocks into which IPT will recommend splitting a host object. IPT recommends creating a new object only when the number of used IP addresses/ranges is smaller than the defined number. Default: 4 |
| Locate_in_rules_include_any |
Determines whether rule search results include rules that contain the searched IP only in Any source or destination. Possible values:
|
| LOCK_WAIT_FREQUENCY |
Defines how often the Check Point and IOS data collection lock file is sampled, in seconds. The value of this parameter, multiplied by the value of the MAX_LOCK_WAIT parameter equal the total wait time for IOS devices. Default: 10 |
| Log_Analysis_Days_Before |
Defines the analysis log lookup, in days. Default: 60 |
| Log_Analysis_Months_Before |
Defines the time period for which traffic database is retained, in months. Traffic logs older than the defined value are deleted. Default: 12 |
| Log_Time_Interval_Minutes_Before_Error |
Defines the time period, in minutes, before which a device's log collection status is set to failure, in case log collection finds no new logs for a specific server for one of the following reasons:
Default: 180 |
| Log_Timeout_Minutes |
Defines the timeout for the entire log collection process, in minutes. Default: 900 (15 hours) |
| LowDiskSpaceThreshold | Threshold in MBs, for sending 'low disk space on AlgoSec server' alerts (E-mail + syslog). Even if available disk space less than this value, the operation continues. Checked before space consuming operations such as analysis / log collection / monitoring. (Default = 10000 (10GB)) |
| Parameter name | Description |
|---|---|
| SCORE_MAXIMAL_RED | Number between 1-99 that defines the point in which the red stops and the yellow starts in the Security Rating Slider (Default = 30) |
| SCORE_MINIMAL_GREEN | Number between 1-99 that defines the point in which the yellow stops and the green starts in the Security Rating Slider. (Default = 70) |
| Security_Rating_Max_Days | Maximum days before current day to display in the security rating graph. (Default = 180 days) |
| SharedSyslogConfigRAs |
Allows nodes (Remote Agents / Central Manager) to receive syslog messages for devices they do not directly manage.
For example: Device syslog configurations are synced between the Central Manager and Remote Agent RemoteOne: SharedSyslogConfigRAs = RemoteOne Device syslog configurations are synced between the Central Manager, and Remote Agents RemoteOne and RemoteTwo: SharedSyslogConfigRAs = RemoteOne,RemoteTwo Note: After first setting the configuration, edit any device on each Remote Agent to synchronize its configuration with other Remote agents in the shared group. Note: When this parameter is set, define on the device the node to where the syslog message will be sent. |
| Show_DeviceNet_Threshold | The maximal number of elements shown when the map initially loads or when it is refreshed. (Default: 500). |
| SHOW_ONLY_NODES_IN_PATH |
Determines whether the network map shown in query results shows only the nodes in the network path, without surrounding devices and objects. Possible values:
|
| Skip_Packages | For CKP devices R80 and higher we collect all packages during data collection. But some of the packages are not related to device or may not be fully configured, causing analysis to fail.
Set the value of this parameter to the package names to skip. Use a comma (",") as the separator between package names. |
|
SKIP_RISKY_RULES_VULNERABILITIES |
Determines whether or not vulnerability information will be skipped for the analyzed devices. When enabled, analysis time is optimized (especially for devices with large number of rules) and vulnerability information in the log file is reduced. Possible values: no (default): Collect vulnerability information yes: Do not collect vulnerability information |
| Skip_unattached_objects_in_report |
Exclude unattached objects from the device report by setting this parameter to yes. (By default, this property is not defined)
|
| SMTPUseSSLEnhanced |
Adds support for TLS1.1 & 1.2 to SMTP Emails.
|
| SpreadhSheetImportRiskSeverity |
The severity of the risks imported from spreadsheet (case insensitive). Can be one of: Ignore
|
| syslog_dump_interval |
Defines the maximum amount of time between syslog collection and memory dump to files, in minutes. |
| TarFormat |
Determines support file download attributes.
|
| trust_rfc1918 |
Determines that risk calculation is skipped for private networks. This means that most Z## risks will not be triggered. Possible values:
|
| TSQ_DIRS_LIMIT | Maximum number of query folders (query-xxx) that can be created under reports and monitor directories.
Default: 2000 |
|
Tsq_dirs_Expiration_Hours_Time |
Maximum number of hours query-xxx folders persist. Affects auto-remove and disk space usage. Default: 48 Note: This parameter cannot be set to 0. |
| TSQ_HIDE_RESOLVE_BUTTON |
Disables the "Resolve" button on the TSQ results page.
|
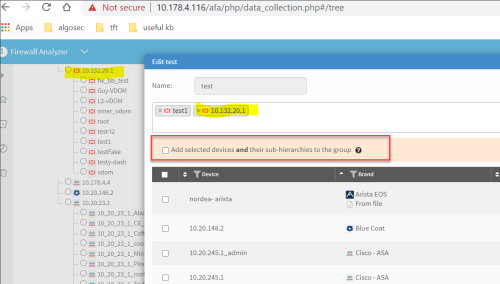
| Uncheck_Parent_Addition_Checkbox |
Determines whether or not the Add selected devices and their sub-hierarchies to the group checkbox is selected by default when adding a group to AFA:
|
| Use_Custom_Report |
Determines whether custom report pages are enabled. For more details, see Custom report pages. Possible values:
|
| Use_Nexus_Wildcards |
Determines whether Traffic Simulation Query results on Cisco Nexus devices use wildcard IP ranges. Possible values:
|
| VALIDATE_USER_ROUTING_URT |
Applicable to Cisco PIX only. When set to "yes", AFA produces a log message for any interface in the .urt file that does not exist in user_routing.urt. |
| WEBGUI_SESSION_LENGTH |
Defines the maximum length of a UI session that is not active, in minutes. Any session that goes on for longer than the defined setting is automatically ended. Default: 300 |