Customize baseline configuration profiles
AFA includes a set of built-in baseline configuration compliance profiles suitable for all device brands which appear as options in the Baseline Configuration Compliance Profile drop-down list and in the /usr/share/fa/data/baseline_profiles/ directory.
Note: CIS Baseline Compliance report for Check Point
In A32.10, we’ve added a new CIS Baseline Compliance report for Check Point devices. The report provides guidance how to establish a secure configuration posture for Check Point Firewall versions R75.x – 80.x installed on Gaia Platform.
If desired, you can create custom baseline compliance profiles.
In this topic:
- Access baseline profiles configuration
- Add a custom baseline configuration compliance profile
- Duplicate a baseline configuration compliance profile
- Edit a baseline configuration compliance profile
- Delete a custom baseline configuration compliance profile
- Example: Customize a baseline configuration compliance profile
- Out-Of-Box commands for baseline compliance reports per vendor/device type
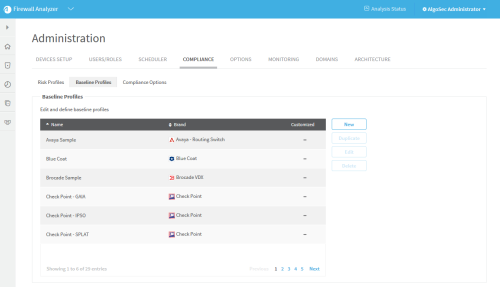
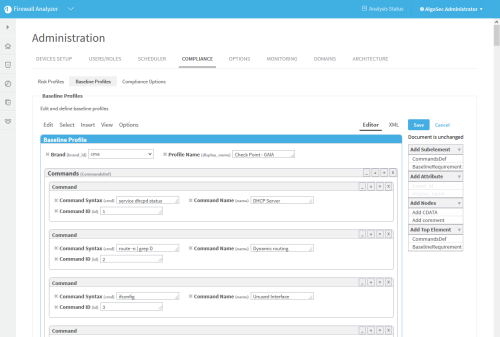
Access baseline profiles configuration
Do the following:
-
In the toolbar, click your username.
A drop-down menu appears.
-
Select Administration.
The Administration page appears, displaying the Options tab.
-
Click the Compliance tab.
The Compliance tab appears, displaying the Risk Profiles sub-tab.
-
Click the Baseline Profiles sub-tab.
A list of baseline profiles appears.
Add a custom baseline configuration compliance profile
Do the following:
-
Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
Click New.
The baseline profile form appears.
- Complete the fields using Example: Customize a baseline configuration compliance profile.
-
Click Save.
The new custom baseline profile appears in the baseline profile table.
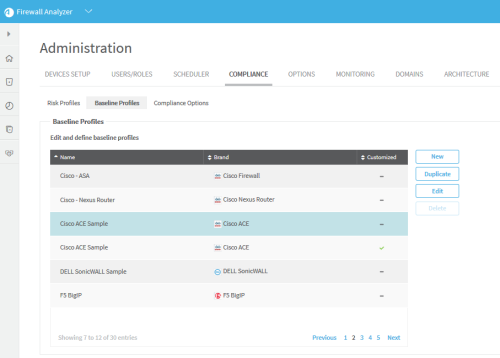
Note: A  appears in the Customized field of all custom baseline profiles.
appears in the Customized field of all custom baseline profiles.
Duplicate a baseline configuration compliance profile
You can create a custom baseline configuration compliance profile by duplicating an existing baseline profile and editing the duplicate.
Do the following:
-
Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
Select one of the baseline profiles.
-
Click Duplicate.
The baseline profile form appears with the values of the original profile.
-
Edit the fields, as desired, using Example: Customize a baseline configuration compliance profile.
Note: To prevent the creation of two baseline profiles with the same display name, change the Profile Name.
-
Click Save.
The new custom baseline profile appears in the baseline profile table.
Note: A  appears in the Customized field of all custom baseline profiles.
appears in the Customized field of all custom baseline profiles.
Edit a baseline configuration compliance profile
You can create a custom baseline configuration compliance profile by editing an existing baseline profile.
Note: The original baseline profile will not be over-written, but it will not be available to use unless you delete the new custom baseline profile.
Do the following:
-
Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
Select a baseline profile.
-
Click Edit.
The baseline profile form appears.
- Edit the fields using Example: Customize a baseline configuration compliance profile.
-
Click Save.
The new custom baseline profile appears in the baseline profile table.
Note: A  appears in the Customized field of all custom baseline profiles.
appears in the Customized field of all custom baseline profiles.
Delete a custom baseline configuration compliance profile
Note: You can only delete custom baseline profiles. Custom baseline profiles are indicated with a  in the Customized field.
in the Customized field.
Do the following:
- Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
Select one of the custom baseline profiles.
-
Click Delete.
-
Click OK.
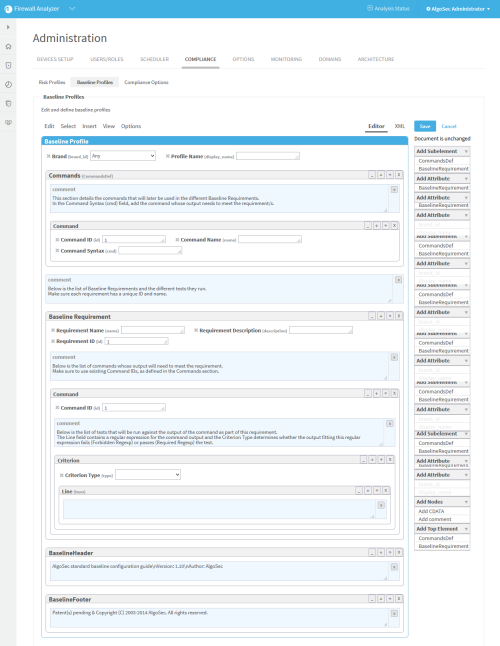
Example: Customize a baseline configuration compliance profile
The following is an example of adding an additional command and baseline requirement to an existing Cisco baseline profile.
-
Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
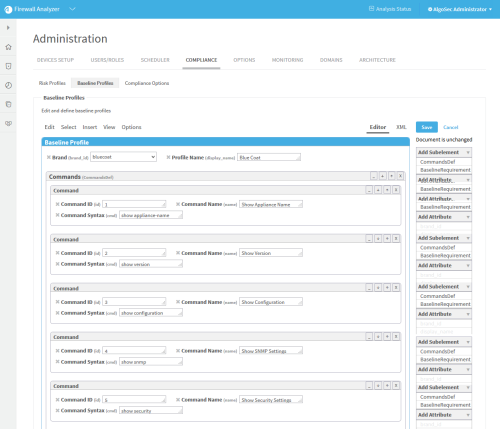
Select a baseline profile.
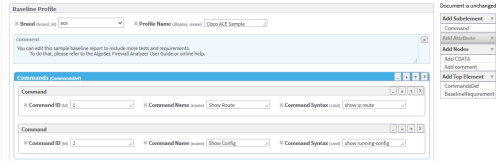
In this example, we selected the Cisco ACE Sample profile. The profile is highlighted in blue.
-
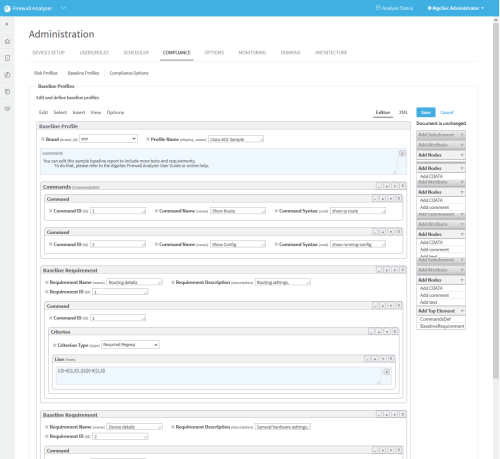
Click Edit.
The baseline profile form appears.
-
To add a command to the profile:
-
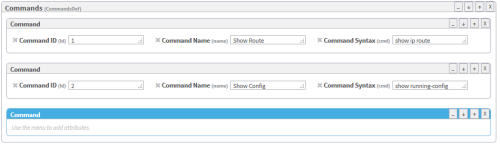
Click Commands (CommandDef).
The Commands area is highlighted in blue.
-
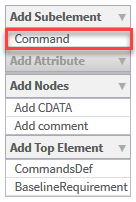
In the Add Subelement menu on the right side of the workspace, click Command.
An additional Command window appears in the profile.
Note: You can click X at anytime to remove a Top Element, Subelement, or Attribute from the profile.
-
- In the Add Attribute menu on the right side of the workspace, click attributes to add to the command. Available options are id (Command ID), name (Command Name), and cmd (Command Syntax). For details, see Command.
-
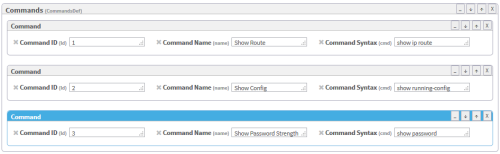
Fill in attribute fields.
Note: The Command ID must be unique.
-
To add a baseline requirement to the profile:
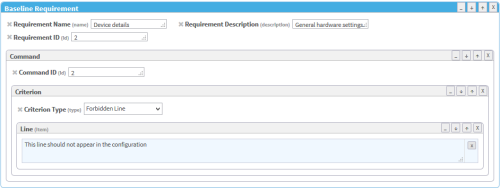
In the Add Top Element menu on the right side of the workspace, click BaselineRequirement.
A additional Baseline Requirement window appears in the profile.

-
In the Add Subelement menu on the right side of the workspace, you can add the following subelements in hierarchical order:
- Command
- Criterion
- Line (Item)
For more details, see Tag Reference,
-
Click Add Attribute to add attributes to the baseline requirement or any of the subelements.
-
Fill in attribute fields.
Note: The Command ID must be unique.
-
Click Save.
This reference describes the use of each tag in the baseline configuration compliance profile. The tags are listed in the same order as they appear in the file.
Tag syntax is presented as follows:
- All parameters are presented in italics.
- All optional elements of the tag appear in square brackets [ ].
Sample Baseline Configuration Compliance Profile
<BaselineProfile display_name="Custom Profile" brand_id="asa">
<CommandsDef>
<Command id="1" name="Check Access" cmd="show access-list" />
</CommandsDef>
<BaselineRequirement name="First" description="This is first requirement."
id="1">
<Command id="1">
<Criterion type="Required Line">
<Item comments="">extended permit ip 207.193.122.0 255.255.255.0</Item>
<Item comments="">extended permit tcp object-group</Item>
</Criterion>
<Criterion type="Required Regexp">
<Item>.*\.company\.com</Item>
</Criterion>
<Criterion type="Forbidden Line">
<Item>extended deny ip host 100.77.20.9 192.168.52.0</Item>
</Criterion>
<Criterion type="Custom Function">
<Item>perl /home/shira/.fa/check_resolv.pl</Item>
</Criterion>
</Command>
</BaselineRequirement>
<BaselineHeader title="Introduction">Introduction to the report - freetext
</BaselineHeader>
<BaselineFooter title="Summary">Summary of the report - freetext
</BaselineFooter></BaselineProfile>
Out-Of-Box commands for baseline compliance reports per vendor/device type
The following are a list of OOB commands available to run baseline compliance reports per vendor/device type: