Customize risk items
In addition to creating a custom risk profile, you can customize individual risk items or add new ones from scratch.
In this topic:
- Edit, duplicate, or add a custom risk item
- Risk Info fields
- Risk Query fields
- Risk Details fields
- Delete a risk item
- Disable a risk item
Edit, duplicate, or add a custom risk item
Edit risk items, duplicate them to create new items based on existing risk items, or add a new custom risk item from scratch.
Do the following:
-
View the Risk Profile with the risk items you want to edit. For details, see View a risk profile.
-
Do one of the following:
Edit an existing risk item Select the risk in the grid, and click Edit.
The risk item is opened for editing. Make your changes as needed, and then click OK.
Duplicate an existing risk item Select the risk in the grid, and click Duplicate.
A new risk item is opened for editing, with the same values as the risk item you had originally selected.
Make your changes as needed, especially giving the new risk item a new name, and click OK.
Create a new risk item Click New, and then select one of the following options:
- Basic risk. Create a basic risk
- Risk with destination threshold. Create a risk item with a specific destination threshold
- Risk with source threshold. Create a risk with a specific source threshold
- Risk with specific IP addresses. Create a risk with specific IP addresses, an IP address range, or a subnet
- PCI risk. Create a risk that refers to PCI zones
-
Populate the fields as needed for your risk item type. For details, see:
- When you're done, click OK to return to your risk profile.
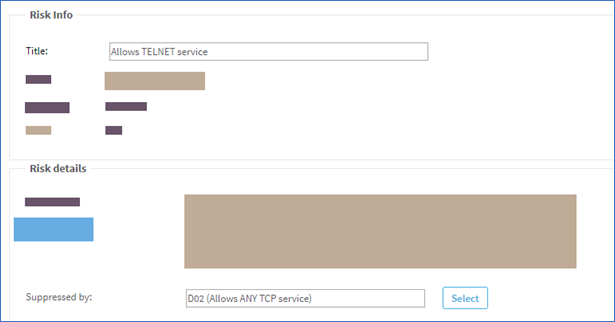
Risk Info fields
All risk types include the following data in the Risk Info area:
- Title. Enter a name for your new risk.
- Level. Select a risk severity level.
- Template. Displays the type of risk item you're editing.
- Code. An automatically assigned code for this risk item. For example, user-defined items have a code that start with U.
Risk Query fields
Risk query fields will differ depending on the type of risk item you're editing.
| Name | Description |
|---|---|
|
From zone / To Zone |
Relevant for basic risks and risks with source or destination thresholds Select the zone types that represent where the traffic you want to analyze is coming from and going to. |
|
With service |
Relevant for all risk types Select a service you want to consider as risky in this risk item. Supported services include pre-defined services, user-defined services, or device-defined services. Note: Selecting a device-defined service imports the service from the device, and creates a new user-defined service with the same details. In such cases, the new service's name is the same as the device-defined service, with an additional prefix of algosec_. Tip: Alternately, create a new service group that consists of one or more services. To do this, click Create New. For more details, see Customize services. |
|
Source / Destination / PCI zone |
Relevant for: risks with specific IP addresses or PCI risks Enter one or more IP addresses or address ranges. Separate multiple addresses and address ranges with commas. Alternately, click Add to use a wizard. There, select a method to use to define your source or destination, including:
Enter subsequent values to continue through the wizard, following on-screen instructions as needed. |
|
Trust VPN IP addresses |
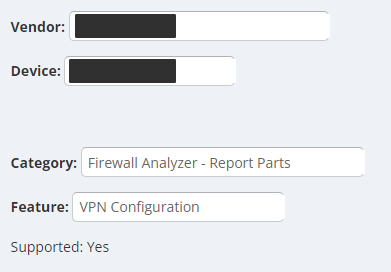
Relevant for basic risks and risks with source or destination thresholds Select to determine that VPN traffic be excluded from this risk item, and not shown in the AFA report. Note: Relevant only for devices whose VPN Configuration is supported by AFA. To determine if a device VPN is supported, see in the Support Matrix: The VPNs are defined on the device. Default = Enabled |
|
Threshold on Destination / Source IP address |
Relevant for risks with source or destination thresholds only Enter the threshold for the source or destination IP address, depending on the type of risk item you're editing. |
|
Advanced |
Relevant for all risk types Define an XQL query for the risk item. Click Advanced and enter your query in the Advanced Query Editor. Warning: Setting an invalid query format may cause analysis errors when creating future reports. Follow the guidelines needed for the risk type you're editing. For details, see Advanced risk editing. |
Tip: Click Auto Fill to load pre-defined values from a template in to the Risk details area below, based on the values you've selected. Any existing values are overwritten.
For more details, see Customize risk items.
Risk Details fields
The Risk Details includes the following data for all risk types:
| Assessment / Remedy |
Enter a description of the risk and risk remedy. These texts are displayed in the AFA report whenever this risk item is triggered.
|
| Description |
Enter a general description of the risk, using terms that are not tied to any particular device. This text appears in Group reports whenever a device in the group has triggered this risk item. |
| Suppressed by |
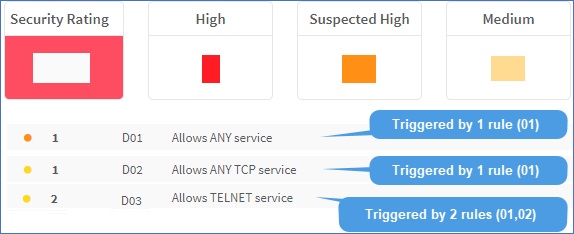
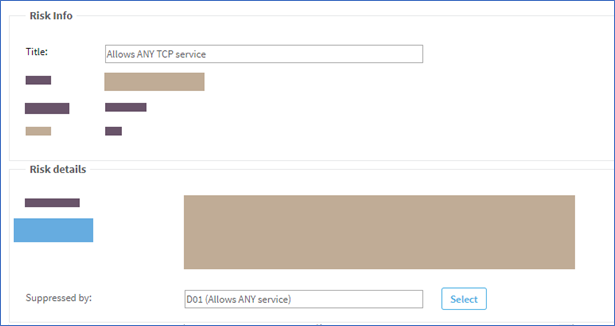
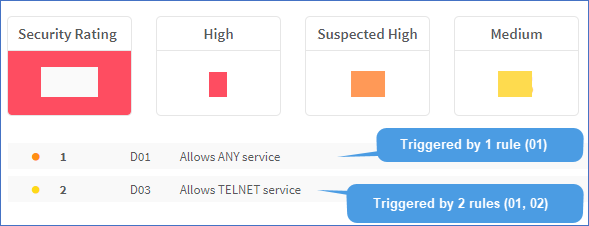
Enter the codes of other risk items that should prevent the current risk item from appearing in AFA reports or click Select to select them from a list. Note: Configuring suppression for your risks helps to avoid clutter and double-reporting in your AFA reports. However, overall security rating scores do also consider suppressed risks. Additionally, risks are not suppressed unless the suppression resolves all cases of that risk. For more details, see Suppression in AFA. |
Delete a risk item
Delete custom risk items that you don't need anymore.
Warning: Do not delete risks with a prefix of unnamed or AlgoSec. Deleting these items may damage a risk profile.
Tip: While Standard risk items cannot be deleted, they can be disabled. For details, see Disable a risk item.
Do the following:
- View the risk profile with the risk item you want to delete. For details, see View a risk profile.
- In the grid, select the risk item you want to delete, and click Delete.
- Click OK to confirm.
The risk item is deleted, and will no longer be included in future AFA reports.
Disable a risk item
Disable standard or custom risk items when you want to prevent them from being included in all AFA reports, but you don't want to remove them from the system.
Warning: Do not disable any risks with a prefix of unnamed or AlgoSec. Disabling these items may damage a risk profile.
Do the following:
- View the risk profile with the risk item you want to disable. For details, see View a risk profile.
- In the grid, select the risk item you want to disable, and click Edit.
- In the Level field, select Ignore, and then click OK.
The risk item is disabled, and will not be included in future AFA reports.