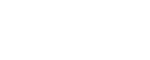Troubleshoot AlgoSec SaaS HTTPS tunnel
This topic explains how to check tunnel connectivity, and to start, restart and stop the HTTPS tunnel for troubleshooting purposes only.
Check tunnel connectivity if Chisel service is unresponsive
If Chisel service is unresponsive, check connectivity between ASMS and the AlgoSec SaaS Services.
Do the following:
Run a cURL command based on your environment using the following Kafka host IPs or FQDNs for your host region:
Kafka host
|
NORTH AMERICA |
EMEA |
APAC (ANZ) |
|
| IPs |
3.93.27.93 3.89.34.12 54.156.78.221 |
3.126.155.34 18.195.164.119 18.158.179.49 |
54.79.229.77 52.63.122.113 3.24.129.179 |
| FQDNs | kafka1.us.algocare.algosec.com kafka2.us.algocare.algosec.com kafka3.us.algocare.algosec.com | kafka1.eu.algocare.algosec.com kafka2.eu.algocare.algosec.com kafka3.eu.algocare.algosec.com | kafka1.anz.algocare.algosec.com kafka2.anz.algocare.algosec.com kafka3.anz.algocare.algosec.com |
-
No Proxy Server: If you are not using a proxy server, run the following cURL command on the ASMS machine terminal for each of the Kafka host IPs in your host region:
Copycurl -v -X CONNECT http://<IP or FQDN of the Kafka host in your region>:8082/health
-
With Proxy Server: If you are using a proxy server, run the following cURL command on the ASMS machine terminal for each of the Kafka hosts IPs in your host region:
Copycurl -pvx <proxy-server-ip>:<proxy-server-port> -U <proxy-server username>:<proxy-server password> -X CONNECT http://<IP or FQDN of the Kafka host in your region>:8082/health
The cURL command checks that the tunnel can be established. A successful result returns:
200 OK
Any other result shows that there are routing rules in the customer environment that block the traffic.
Note: If you cannot connect to the Kafka host via FQDN but you can using the host IP, check that you have a DNS server configured.
About the HTTPS tunnel
When you integrate AlgoSec SaaS solutions ObjectFlow, and AlgoSec Cloud, with ASMS in A32.10, the HTTPS tunnel automatically starts to route traffic from ASMS to AlgoSec SaaS. The tunnel encapsulates traffic and encrypts it with the Public Key certificate mechanism.
Note: The HTTPS tunnel can run with or without a customer proxy server. If you have configured a proxy server in ASMS (see Define a device proxy) the HTTPS tunnel automatically routes traffic through it.
If you are using a proxy server, the Proxy Content Inspection should be disabled to avoid redundant encryption and resulting degradation of the connection.
The following diagram illustrates the HTTPS tunnel architecture:
To start/restart the HTTPS tunnel
We recommend you perform the following procedure on the Central Manager since changes to the HTTPS tunnel will be propagated, in any case, to all nodes. If required, you can also start and restart the tunnel on specific nodes.
Note: When the HTTPS tunnel is not running, the Start HTTPS tunnel option appears in the steps below. When it is already running, the Restart HTTPS tunnel option appears.
Do the following:
-
In the algosec_conf main menu, enter 14 Product and cloud configuration.
-
Enter 3 Cloud Integration.
-
Enter 3 HTTPS tunnel Configuration.
-
Enter 1 Start/Restart HTTPS tunnel.
-
Confirm by entering y. The tunnel starts/restarts.
To remove the HTTPS tunnel
We recommend using the HTTPS tunnel. If you do choose to remove the tunnel, ASMS-AlgoSec SaaS secure communication takes place over TLS, using port TCP/9094.
Do the following:
-
In the algosec_conf main menu, enter 14 Product and cloud configuration.
-
Enter 3 Cloud Integration.
-
Enter 3 HTTPS tunnel Configuration.
-
Enter 2 Remove HTTPS tunnel.
-
Confirm by entering y. The tunnel is removed.