Edit work orders
FireFlow enables you to edit work orders by adding notes to the work order, by editing the list of recommendations, or renaming the objects that FireFlow creates for the work order.
Supported editing scope
You may want to edit a FireFlow work order, such as when you want to provide specific names for objects on your device. Depending on your configuration or the device you're making the change to, editing may be required before continuing on in the flow.
In other cases, editing a work flow is not supported at all, such as for work orders with a drop action, or for AWS or Symantec Blue Coat![]() devices.
devices.
When editing a workflow, keep in mind that change requests that include traffic with NAT only include the relevant addresses in the request, as follows:
- Requests for devices that are located before NAT only include the before-translation address.
- Requests for devices that are located after NAT only include the after-translation address.
- Requests for devices that perform NAT includes both the before- and after-translation addresses.
Edit a work order
Do the following:
-
View the change request. For details, see View change requests.
-
If the change request has multiple devices or policies, click
 next to a device.
next to a device. -
If the work order is not available, or the device policies have changed since the work order was created, refresh the work order by clicking Recalculate.
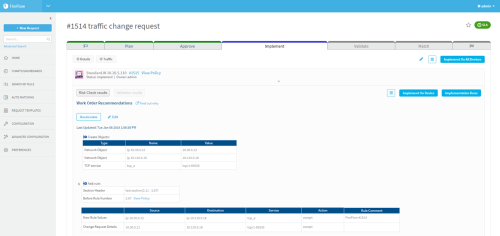
The work order and any device action buttons are shown in the Work Order Recommendations area.
For example:
This area shows FireFlow's recommendations for implementing the change specified in the change request.
Note: If the traffic is already allowed by the device, your recommendation may be No action required.
For more details, see:
-
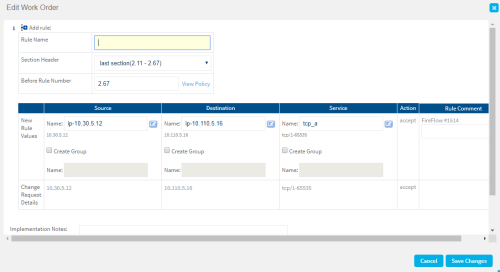
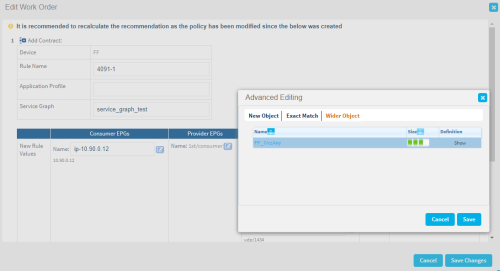
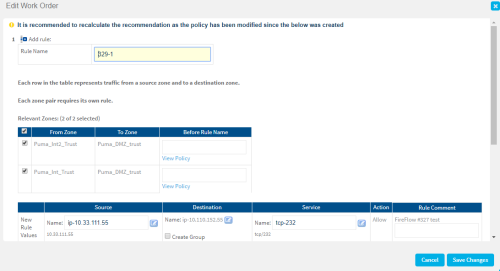
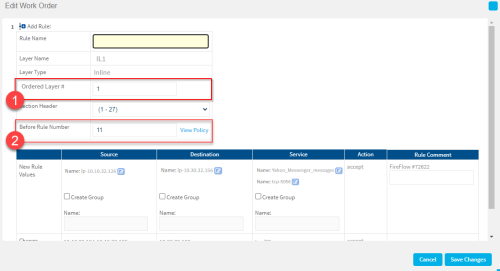
If your change request includes only an Allow action, edit the values recommended by FireFlow as needed. Do the following:
-
At the top of the Work Order Recommendations area, click
 .
.The Edit Work Order window appears.
-
Edit the fields as needed, and click Save Changes. For more details, see Work order recommendation details.
Note: If CLI commands were generated, editing the work order will cause the CLI commands to be regenerated.
-
-
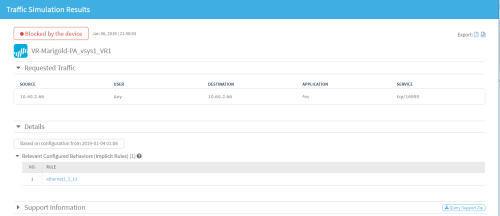
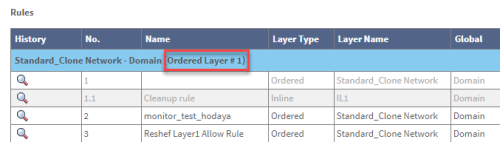
To view the query on which the recommendation is based, in the Work Order Recommendations area, click
 . The query details open in a new tab. For example:
. The query details open in a new tab. For example: -
To add comments, scroll down to the Implementation Notes area at the bottom, and click Edit.
Enter your comment in the text box, and then click OK back up at the top.
Your work order is updated.
Work order recommendation details
Work order recommendations and editing scope vary greatly, depending on your scenario, configurations, and device types. For example:
- Fields where exactly one suitable option exists will be pre-filled with the relevant option and read-only.
- If no suitable object option exists, you may be able to enter the name of a new object to create. Your object name must be valid and unique.
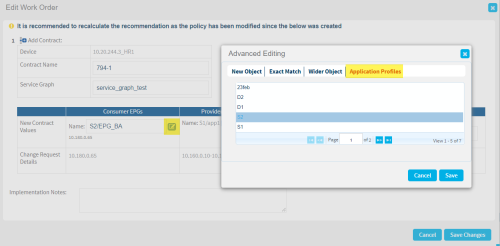
- For source, destination, and service fields, use the Advanced Editing wizard to access additional options. For details, see The Advanced Editing wizard
Related Topics: