Add Zscaler Internet Access (ZIA)
ASMS supports ZIA as follows:
-
Policy Visibility for policy type: Firewall Policy Control
-
Report Generation
-
Topology including VPN tunnels
-
Change analysis and monitoring
-
Risks Calculation
-
Map Visibility (IPSec and GRE tunnels)
-
Regulatory Compliance
-
Traffic Simulation Query
-
Policy Optimization
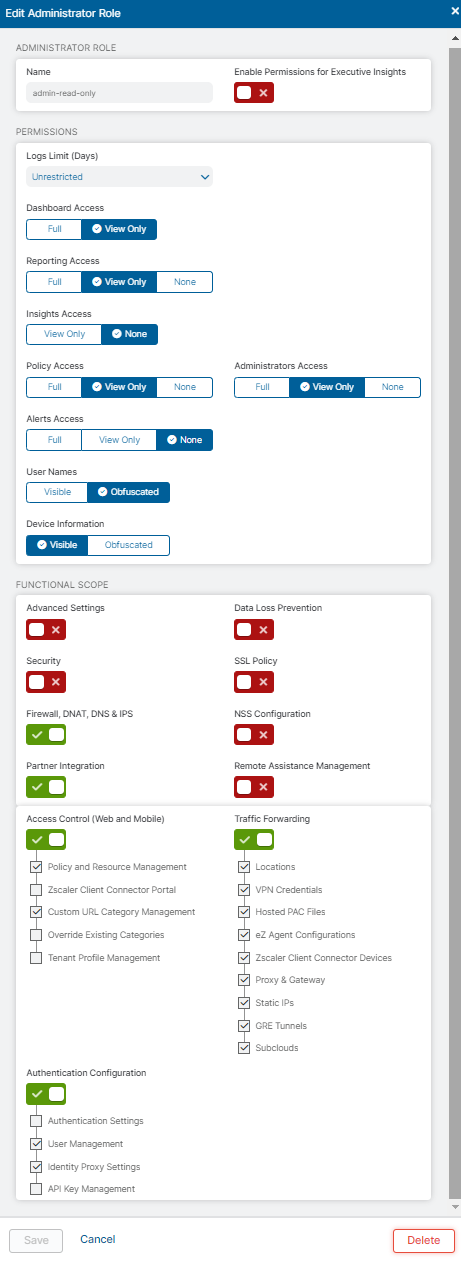
The following sections describe how ASMS connects to ZIA public services:
From AFA, we communicate with ZIA via Rest API over HTTPS protocol.
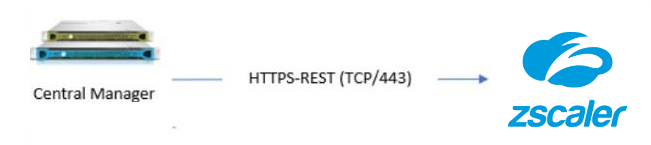
Required user role permissions
User role permissions are defined in Zscaler Cloud Portal and require the following minimal read-only permissions and functional scope:
Do the following:
-
Create a user in Zscaler based on the minimal read-only permissions.
 To create the user
To create the user
-
Log in to the Zscaler Cloud Portal. Navigate to Administration > Role Management > Add Administrator Role based on the enabled permissions and functional scope. See Required user role permissions.
-
Navigate back to Administration > Administrator Management > Add an Administrator.
-
Insert the following:
Login ID: Based on your domain
Email Address and Name
Role: The role you created above
Scope: Select organization
Enable Set Password if Needed (if required by your configured authentication method).
-
Navigate to Activation. Click Active to save the settings
-
-
Get a Zscaler Cloud Service API Security Key according to the Zscaler Cloud Portal
- In AFA, go to Administration
- Click the Devices Setup tab
- From New drop-down, select Devices
-
Select Zscaler
-
Select Zscaler Internet Access
- Enter:
- Display name: Add a meaningful name. The display name must not contain spaces.
- User name: The Login ID in Zscaler Administration Management page (for example, user_name@domain_name)
- Password
- Zscaler Cloud name (for example, zscalerone.net, zscaler.net)
- API Key: The API Security KeyZscaler Cloud Service API Security Key
- (optional): If the ASMS machine needs to communicate to Zscaler services through a proxy server, click Set Proxy and define the proxy server.
-
Select the options as required:
Real-time change monitoring Select this option to enable real-time change monitoring. For details, see Configure real-time monitoring.
Set user permissions
Select this option to set user permissions to use this device in AFA
- Click Finish