This topic describes how to add and modify advanced AFA configuration parameters, as well as a reference of parameters available.
Add a new AFA configuration parameter and value
This procedure descries how to add a new advanced configuration parameter to AFA. Use this procedure to override various system defaults or implement hotfix updates.
Do the following:
-
In the toolbar, click your username and select Administration to access the AFA Administration area.
-
Navigate to Options > Advanced Configuration.
-
Click Add, and enter the name and value of your configuration parameter.
- Click OK to close the dialog, and then OK again to save your changes.
Advanced AFA configuration parameter reference
The following tables list commonly used AFA configuration parameters and their possible values.
Use the alphabetical links below to jump between tables.
A-B | C | D | E-J |L | M | N-R | S-W
| Parameter | Description |
|---|---|
|
Active_Change_Backups_Number |
CLI only. Define the number of backup files stored by AFA for Cisco firewalls, Juniper SRX devices, Fortinet or Panorama devices. Default= 50 |
|
AddOnlyChildren |
Determines whether the add_device_to_group and create_device_group SOAP APIs add both the parent and children devices to the group. Possible values:
|
|
Defines the maximum number of rules returned by Advanced Policy Search . If exceeded, the search is aborted and an error message is displayed.
Note: This parameter also controls the behavior of the following API parameters: The actual maximum number of rules returned for the APIs will be the lower value between ADV_SEARCH_MAX_RESULTS parameter and BASIC_ADV_SEARCH_MAX_RESULTS/FULL_ADV_SEARCH_MAX_RESULTS, respectively. |
|
|
Defines maximum number of comparisons (== and !=) that can be used in a search query in Advanced Policy Search. If the number of comparisons exceeds this value, the search is aborted and an error message is displayed.
(Setting the parameter affects both UI and API behavior). |
|
|
Defines the maximum duration for Advanced Policy Search. If exceeded, the search is aborted and an error message is displayed.
(Setting the parameter affects both UI and API behavior). |
|
|
AFA_URL |
Defines the server used for email notification and other AFA related links. Can be an IP address or host name. For example:
|
| ALGOSEC_EA_PANORAMA_EDL |
Enables early access support for parsing for Panorama EDLs.
|
| ALLOW_ALL_IPS_SUBNET |
By default, interfaces are not created for 0.0.0.0/0 subnets. To enable the creation of interfaces for 0.0.0.0/0 subnets, add the following parameter: ALLOW_ALL_IPS_SUBNET=yes |
| Allow_Copy_Paste_Password |
Determines whether or not a user can copy their password and paste it into the Password Confirmation input field when resetting their password.
|
|
analyze_only_changed_reports |
Determines whether analysis is always run, even if the configuration has not changed. Possible values:
|
|
Auto_Create_Users |
Automatically create user in AFA from LDAP (if LDAP is defined).
|
|
AUTOREMOVE_REPORT_NAS_CONFIGURED |
Customers with NAS configured might experience disk space issues due to a non-optimized file cleanup. In such a case, setting this parameter to true could potentially resolve this.
|
| Avoid_Unnamed_Object_Htmls |
Determines whether or not device analysis will skip unnamed objects in the Hostgroup and Service HTMLs. This can significantly reduce the size of reports containing a large number of internal "AFA created" Hostgroups and Services. If the parameter is not defined, the behavior is the same as setting it to no. Possible values:
|
|
AWS_DC_FILTERS_USED |
When an AWS account has resources with a different Owner-ID (such as in the case of shared VPCs), AFA data collection filters out those resources. Set this parameter to false to collect the missing resources.
|
| AWS_ENABLE_VPC_REPORTS |
Determines whether or not to generate reports for AWS devices on the VPC level. If the parameter is not defined, the behavior is the same as setting it to no.
|
|
If required, use this parameter to switch between ACE and Firewall Analyzer as the Network Elements Collection Source.
For instructions how to change this parameter setting, see Configuring the AWS Network Elements Collection Source. |
|
|
Backup_Firewall_History |
Determines whether backup files include change history. Possible values:
|
| BACKUP_RESTORE_TIMEOUT_MINUTES |
Defines the timeout for the backup-restore process. Default= 15 (minutes) |
|
Defines the maximum number of rules returned by the Advanced Policy Search-Basic API. If exceeded, the search is aborted and an error message is displayed.
Note: The actual maximum number of rules returned will be the lower value between ADV_SEARCH_MAX_RESULTS parameter and BASIC_ADV_SEARCH_MAX_RESULTS. See ADV_SEARCH_MAX_RESULTS. |
|
|
Bulk_Delete_Max_Timeout_Seconds |
Defines the timeout for each bulk delete device operation as explained in Enable / Disable early availability support for Bulk Add/Update/Delete devices. Default= 240 (seconds) Minimum allowed value= 30 (seconds) |
| Bulk_Max_Failed_Attempts |
Determines the maximum number of failed add/update bulk operations permitted before aborting the bulk action request. This also impacts the Early Availability feature Add/Update/Delete devices in bulk from xslx file. Default= 5 |
|
BUSINESSFLOW_ADDRESS |
Determines the IP address of the BusinessFlow host, if not local. |
| Parameter | Description |
|---|---|
|
CHANGE_HISTORY_DAYS |
Determines the number of days that legacy changes are kept in report change histories. Default= 90 (days) |
|
Determines whether or not an administrator needs to enter the Admin password when creating or changing a user password. Possible values:
|
|
|
Defines the chart threshold value for all condition type charts, including the built-in compliance charts. Possible value: Integer Default= 23 |
|
|
Checkpoint_Adtlog_Exclude_Fields |
Defines a pipe-separated list of Check Point audit log fields that are ignored. For example: CKP_Adtlog_Exclude_Fields=CLCStatus|threshold_event_uint Note: Regular expressions are supported. |
| CISCO_ACI_SKIP_SUFFIX |
Use this parameter to remove the Cisco ACI suffix from networks and subnets in the network map, merging them with matching ones from other devices. If the parameter is not defined, the behavior is the same as setting it to no. Possible values:
|
|
CKP_ACTIVE_CHANGE_DISABLE_POLICY_BACKUP |
Determines policy backup on Checkpoint FW during a policy change/removal.
|
|
CKP_Data_Collection_Collect_Tables_One_By_One |
By default, this property is not defined and all firewall policy and rule information is collected via a single request. If analysis of firewall policy and rule information fails due to a timeout error, using multiple requests to collect each firewall's data individually may speed up processing and resolve this issue. To activate, set value to yes. |
|
CKP_DNS_Cache_Duration_Seconds |
Defines the cache duration (in seconds) for Check Point DNS resolution of network objects. By default, DNS resolutions are not cached. For example: CKP_DNS_Cache_Duration_Seconds=3000 |
|
CKP_optimizations_per_policy |
Determines whether policy optimization items are shown for all rules in the policy, and not only those installed on the analyzed module. Default= yes |
|
CKP_PASS_ANALYSIS_ON_DATA_CENTER_FAILURE |
no (default): CKP analysis fails when unable to connect to a data center that is not in use. yes: Prevents analysis from failing if unable to connect to the defined data center. |
|
CKP_turbo_log_collection |
Determines whether a dummy environment is used to speed up log collection on Check Point devices. Default= no |
| CLOUD_DEVICES_CHECK_ROUTED |
Determines whether or not to check if the cloud-connected device has a route to the TSQ destination when generating the TSQ results. If the parameter is not defined, the behavior is the same as setting it to no. Possible values:
|
|
CLUSTER_USE_VIP |
Determines whether a VIP is shown instead of a MIP in Check Point cluster topologies. Default= yes |
|
CollapseDevicesTreeOnLogin |
Determines whether the device tree appears fully collapsed or expanded by default. Possible values:
|
| Collector_TO |
The SSH connection timeout between the master and collector, in seconds. Default value (if not defined) is: 180 |
|
Comments_Regex_Match |
Determines whether comments match or do not match the regular expression defined in Comments_Regex. Possible values:
|
|
Compliance_Score_Max_Red |
Number between 1-99 that defines the point in which the red stops and the yellow starts in the compliance score. (Default= 50) |
|
Compliance_Score_Min_Green |
Number between 1-99 that defines the point in which the yellow stops and the green starts in the compliance score. (Default= 85) |
|
Compliance_Score_Star_Weight |
Number between 0-1 that defines the weight of the star status when calculating the compliance score. (Default= 0.5) |
|
comprehensive_mode |
Determines whether comprehensive mode is enabled, where AFA queries all services that appear in any rule in the policy. Default= yes |
|
CONSIDER_MULITPLE_NHG |
Determines whether all multiple routes for each range are saved and used for FIP. Supported only for IOS. Default= yes |
|
covered_exclude_services |
Defines a colon-separated list of values. Rules that contain any of the listed values as services are not listed as covering rules. Default= null (no exclusions) |
| Email_With_Embeded_Content |
Determines whether information about changes detected on the device is included in the email body.
|
|
Enable_Ms_Traffic_Logs_Processing |
Determines whether traffic log collection is enabled using the ms_trafficlogmanager service. Possible values:
|
|
Export_Policy_Tab_With_Objects_Content |
Determines whether the exported PDF report's Policy page shows the network object content as well as the network object names. Possible values:
|
|
EXPECT_TIMEOUT |
Defines the timeout, in seconds, for processing a single command in the Expect data collection. Default= 120 (seconds) |
|
FailCLIOnMissingUIDs |
Determines whether the CLI is generated even in case of missing UIds in Cisco PIX devices. Possible values:
|
|
Fetch_Primary_Routing |
Determines backplane interface between VRs to provide interconnection in order to route traffic when primary routing table is specified. Note: This parameter is relevant for Juniper (SRX) Possible values:
|
|
FGATE_ENABLE_PROXY_POLICY_LOG_PARSING |
To enable support for audit/traffic logs with policytype="proxy-policy", do the following:
|
|
FIP_MAX_DEVICES_SEARCH_PATHS_FOR_DESTINATION_ANY |
Defines a maximum number of devices for which to run a query with a FIP destination of any. Default= 100 |
| FIP_Group_Names_To_Skip |
ASMS uses a Firewalls in Path (FIP) algorithm to identify the relevant devices for TSQ. Sometimes members of a group of devices are not found in the path. Use this parameter to force TSQ to go through the devices in the specified group(s).
In this example, any TSQ executed on groups group1, group2, or group3 will go through all the devices that exist in those groups. |
|
FireFlowXmlEncoding |
Determines whether FireFlow XML change files are encoded as UTF-8 or ISO-8859-1. Possible values:
|
|
ForceErrorEmailsToAdmins |
|
|
FORTIMANAGER_Auto_Tree_Update_Enabled |
This parameter impacts the general behavior for FortiManager and the managed FortiGate/VDOMs throughout the system. If the parameter is not defined, the behavior is the same as setting it to no.
|
|
FORTIMANAGER_ADOM_UNATTACHED_OBJECTS |
|
|
Defines the maximum number of rules returned by the Advanced Policy Search-Full API. If exceeded, the search is aborted and an error message is displayed.
Note: The actual maximum number of rules returned will be the lower value between ADV_SEARCH_MAX_RESULTS parameter and FULL_ADV_SEARCH_MAX_RESULTS. See ADV_SEARCH_MAX_RESULTS. |
|
|
FWFiles_Directory |
Defines the path of the Analyze from file firewalls. Default= $HOME/algosec/fwfiles |
|
Group_Query_Print_Missing_Paths |
Whether to display missing paths table in group query result (useful for FIP troubleshooting)
|
|
Determines whether to omit change details from emails about new reports and change alerts, for all users. Possible values:
|
|
| HTTP_Tunnel_Enabling |
Determines whether the ASMS connection to the AlgoSec SaaS environment is established via an HTTPS tunnel over TCP/8082, or directly over TLS on TCP/9094. Possible values:
If the parameter is not defined, the behavior is the same as setting it to yes. |
|
IGNORE_NON_LOCAL_ROUTES_IF_DIRECTLY_CONNECTED |
For devices with source-based routing, routing priority can be set as follows:
|
|
IPT_Density_Action_Limit |
The maximum density of a sparse object. When this limit is exceeded, the object is considered semi-dense. Default= 50 |
|
IPT_Ranges_Number |
Divide each hostgroup range to this number of parts. (default is 256) |
|
IPT_Recommendation_Max_Ranges |
Defines the maximum number of CIDR blocks into which IPT will recommend splitting a host object, if the original object contains more IP addresses/ranges than defined in IPT_Recommendation_Max_Subnets_Per_Range. Default= 20 |
|
IPT_Recommendation_Max_Services |
The maximum number of services or applications from which IPT will recommend composing a new object. Default= 20 |
|
IPT_Recommendation_Max_Subnets_Per_Range |
Defines the maximum number of CIDR blocks into which IPT will recommend splitting a host object. IPT recommends creating a new object only when the number of used IP addresses/ranges is smaller than the defined number. Default= 4 |
|
Junos_Parallel_Monitoring |
Determines whether to change from sequential to parallel monitoring for Juniper SRX firewalls. Possible values:
|
| LOAN_BGP_ROUTER_INTERFACE |
Set this parameter to yes to ensure that interfaces are appropriately loaned between Cisco IOS VRFs based on their participation in the BGP tunnel. Possible values:
|
|
Locate_in_rules_include_any |
Determines whether rule search results include rules that contain the searched IP only in Any source or destination. Possible values:
|
|
LOCK_WAIT_FREQUENCY |
Defines how often the Check Point and IOS data collection lock file is sampled, in seconds. The value of this parameter, multiplied by the value of the MAX_LOCK_WAIT parameter equal the total wait time for IOS devices. Default= 10 (seconds) |
|
Log_Analysis_Days_Before |
Defines the analysis log lookup, in days. Default= 60 (days) |
|
Log_Analysis_Months_Before |
Defines the time period for which traffic database is retained, in months. Traffic logs older than the defined value are deleted. Default= 12 (months) |
|
Log_Time_Interval_Minutes_Before_Error |
Defines the time period, in minutes, before which a device's log collection status is set to failure, in case log collection finds no new logs for a specific server for one of the following reasons:
Default= 180 (minutes) |
|
Log_Timeout_Minutes |
Defines the timeout for the entire log collection process, in minutes. Default= 900 (15 hours) |
|
LowDiskSpaceThreshold |
Threshold in MBs, for sending 'low disk space on AlgoSec server' alerts (E-mail + syslog). Even if available disk space less than this value, the operation continues. Checked before space consuming operations such as analysis / log collection / monitoring. (Default = 10000 (10GB)) |
|
mailSuffix |
Defines an email address to use as a default if a new or edited user email address is left empty. Default= null |
|
MAP_BLACK_LIST |
Determines whether to ignore defined devices in AFA when creating the map. Default= null |
|
When you export a Changes Summary Report to an XLS file, the maximum number of characters allowed in a cell is limited to 255 (default). If there are more than 255 characters, the additional characters are moved to a tool tip that is accessed by hovering over the cell. By changing the value of this parameter, you can change the maximum characters limit, as long as the new limit is smaller than 255. You cannot exceed the limit of 255 characters per cell. |
|
|
MAX_LOCK_WAIT |
Defines a time to wait for the Check Point, IOS, or NSM data collection lock file, in seconds. Default= 7200 (2 hours) |
|
MAX_LOCK_WAIT_NSC |
Defines a time to wait for the NSC data collection file, in seconds. Default= 7200 (2 hours) |
|
Max_Parallel_Analyses |
Determines the maximum number of analyses that are allowed to run in parallel. Default: The number of CPUs on the machine. |
|
Max_Parallel_Logcollect |
Determines the maximum number of log collections running in parallel. Possible values:
|
|
Max_Parallel_Monitor |
Max monitors to run in parallel. If not set - monitor will go according to Max_Parallel_Analyses. |
|
Max_Rows_To_Sort |
Determines whether sorting and filtering in AFA report tables is enabled, and if so, for how many rows. Sorting and filtering large tables may take a long time. Possible values:
Default= 10,000 |
|
MGMT_ROUTING_FREQUENCY |
Defines the frequency of routing information collection for management devices, such as Panorama, in minutes. Default= 60 (minutes) |
|
Minimize_Analysis_Logs_History |
Use this param to decrease the algosec-support.zip file size and also remove unneeded files from report's directory. Default= no |
|
Monitor_exclude_PIX |
Defines a single regular expression, including a simple string, to exclude from comparisons during monitoring. Tip: Even though this supports a single regular expression only, define multiple matches using an OR pipe (|). For example: (log\s+in|log\s+out) |
|
Monitor_Force_Data_Coll_Ckp_Min |
Defines how often data collection runs on Check Point devices, in minutes, even if no new logs are found. Default= 720 (minutes) |
|
Monitor_Force_Data_Coll_Cycles_Num |
Defines the number of cycles without audit logs before initiating a full monitor cycle with data collection. Not relevant for Check Point and Juniper NSM. Default: 12 |
|
Defines how often the monitoring process runs. When Monitor_Frequency <= 60, the value determines the frequency in minutes. Default= 5 (minutes) When Monitor_Frequency > 60, the monitoring frequency is dependent upon the parameter MONITOR_USE_FREQUENCY_AS_HOUR_OF_DAY.
|
|
|
When parameter Monitor_Frequency > 60, determines whether the monitoring schedule set by Monitor_Frequency is the hour or hours of the day at which monitoring is started. By default, this parameter is not defined and the behavior is the same as setting it to no. Possible values:
|
|
|
MONITORING_HISTORY_DAYS |
Defines the number of days to retain monitoring changes. Default= 90 (days) |
|
NSM_optimizations_per_policy |
Determines whether to show policy optimization items for all the rules in a policy, and not only for those that have the analyzed device in their target. Possible values:
|
|
Num_Of_Status_Recent_Reports |
Number of recent reports to show in status page. Set to 0 to show only running analyses in the status page. (Default = 10) |
| Number_of_covered_rules_per_page |
Determines the number of covered rules to display on each page of the Policy Optimization - Covered Rules report. Possible values: 10 (default) - 500 Note: After setting the parameter, rerun the analysis to update the Policy Optimization results. |
| PA_URL_CAT_DNS_LIMIT |
Determines the max number of URLs parsed (relevant only to EDL type URL).
|
| PAN_EDL_COLLECT_TIMEOUT |
Determines the max time to wait (in seconds) for retrieving response from an EDL list source.
|
|
Panorama_Prefer_Other_Objects_Over_Url_Category |
When a Panorama local object has the same name as a shared URL category, set this parameter to true to force AFA to prefer the local object instead of the shared URL category. Possible values:
|
|
Policy_Tab_Limitation |
The max rules to show on the Policy tab. Default value for supported browsers 1000 and less. This value can be overwritten by adding this parameter. |
|
Policy_Tab_Rules_Per_Page |
Number of rules per page for the paging of the policy tab (Default = 10). |
|
Determines if routing queries and traffic simulation queries prioritize paths that begin and end with a subnet (and not a cloud) for destinations.
|
|
|
Determines whether subnets are prioritized for sources in routing and traffic simulation queries. Possible values:
|
|
|
Query_Disable_NAT_Logic |
If a query destination can be reached by a NAT rule, AFA replaces the query destination to * and then intersects with the destination. This way, even if given the post-NAT address, the query will find the relevant rules.
|
|
Query_Disable_NAT_Print |
|
|
Query_Timeout |
Defines the timeout for a single query, in seconds. Default= 15 (seconds) |
|
QueryByPolicy |
Determines whether traffic simulation group query results include all devices in device groups, or are grouped by policy with a single representative device for each policy. Note: This setting affects group traffic simulation query results and batch traffic simulation query results. It also affects initial plan query results in FireFlow. Possible values:
|
|
RADIUS_FetchData |
Determines whether to fetch data and groups from LDAP for users authenticated by a Radius server. Default= no |
|
REMOVE_DELETED_DEVICE_REPORTS |
Determines whether to remove reports for all deleted devices. Possible values:
|
|
AppViz uses an improved method for finding risks for traffic flows. In order to determine the risk profile used by the new method, you need to define this global parameter. If not set, the risk profile used in the last completed report is used for the AppViz risk calculation. If not set, and there is no last completed report, by default the Standard risk profile will be used. There are two options:
|
|
|
Routing_Element_Monitor_Frequency |
Determines the frequency for which to run monitoring on routing elements, in minutes. Default= 5 |
|
Rule_Selection_Limit |
Defines the maximum number of rules allowed to be selected for a single FireFlow change request. Tip: Avoid using large numbers to prevent performance issues in FireFlow. Default= 50 |
|
run_full_data_collection_always |
Relevant for Palo Alto, Juniper SRX, McAfee SideWinder, Cisco ASA/PIX/FWSM brands:
|
| Parameter name | Description |
|---|---|
|
SCORE_MAXIMAL_RED |
Number between 1-99 that defines the point in which the red stops and the yellow starts in the Security Rating Slider (Default = 30) |
|
SCORE_MINIMAL_GREEN |
Number between 1-99 that defines the point in which the yellow stops and the green starts in the Security Rating Slider. (Default = 70) |
|
Security_Rating_Max_Days |
Maximum days before current day to display in the security rating graph. (Default = 180 days) |
| SG_MEMBERS_TO_NAMES |
Creates a one-to-one mapping between PBR (policy based redirect) configuration and devices added in AFA. Example: To map a PBR (pbr_name1) to 2 AFA devices and map a second PBR (pbr_name2) to a third AFA device: pbr_name1:afa_device_name1, pbr_name1:afa_device_name2, pbr_name2:afa_device_name3 |
|
Allows nodes (Remote Agents / Central Manager) to receive syslog messages for devices they do not directly manage.
For example: Device syslog configurations are synced between the Central Manager and Remote Agent RemoteOne: SharedSyslogConfigRAs=RemoteOne Device syslog configurations are synced between the Central Manager, and Remote Agents RemoteOne and RemoteTwo: SharedSyslogConfigRAs=RemoteOne,RemoteTwo Note: After first setting the configuration, edit any device on each Remote Agent to synchronize its configuration with other Remote agents in the shared group. Note: When this parameter is set, define on the device the node to where the syslog message will be sent. |
|
|
Show_DeviceNet_Threshold |
The maximal number of elements shown when the map initially loads or when it is refreshed. (Default= 500). |
|
SHOW_ONLY_NODES_IN_PATH |
Determines whether the network map shown in query results shows only the nodes in the network path, without surrounding devices and objects. Possible values:
|
|
SHOW_UNASSIGNED_SECURITY_GROUPS_AWS |
Determines whether or not security groups which do not have EC2 resources under them will be displayed in the AFA Device Tree. Not including these security groups in the tree may impact the map content, TSQ, and AFF recommendations.
|
|
Skip_Packages |
For Check Point devices R80 and higher we collect all packages during data collection by default. But some of the packages are not related to device or may not be fully configured, causing analysis to fail.
Set the value of this parameter to the package names to skip. Use a comma (",") as the separator between package names. |
|
SKIP_RISKY_RULES_VULNERABILITIES |
Determines whether or not vulnerability information will be skipped for the analyzed devices. When enabled, analysis time is optimized (especially for devices with large number of rules) and vulnerability information in the log file is reduced. Possible values: no (default): Collect vulnerability information yes: Do not collect vulnerability information |
|
Skip_unattached_objects_in_report |
Exclude unattached objects from the device report by setting this parameter to yes. If the parameter is not defined, unattached objects appear in the device report.
|
|
SMTPUseSSLEnhanced |
Adds support for TLS1.1 & 1.2 to SMTP Emails.
|
|
SpreadhSheetImportRiskSeverity |
The severity of the risks imported from spreadsheet (case insensitive). Can be one of: Ignore
|
|
SRX_parse_Tunnels_WithIp_As_L3 |
If SRX tunnels are not created correctly, add this parameter to parse the tunnels as layer 3 interfaces instead of layer 2 interfaces. SRX_parse_Tunnels_WithIp_As_L3=yes |
|
syslog_dump_interval |
Defines the maximum amount of time between syslog collection and memory dump to files, in minutes. |
|
TarFormat |
Determines support file download attributes.
|
|
trust_rfc1918 |
Determines that risk calculation is skipped for private networks. This means that most Z## risks will not be triggered. Possible values:
|
|
TSQ_DIRS_LIMIT |
Maximum number of queries (query-xxx) folders that can be created under reports and monitor directories. Default= 2000 |
|
Tsq_dirs_Expiration_Hours_Time |
Maximum number of hours query-xxx folders persist. Affects auto-remove and disk space usage. Default= 48 (hours) Note: This parameter cannot be set to 0. |
|
TSQ_HIDE_RESOLVE_BUTTON |
Disables the "Resolve" button on the TSQ results page.
|
|
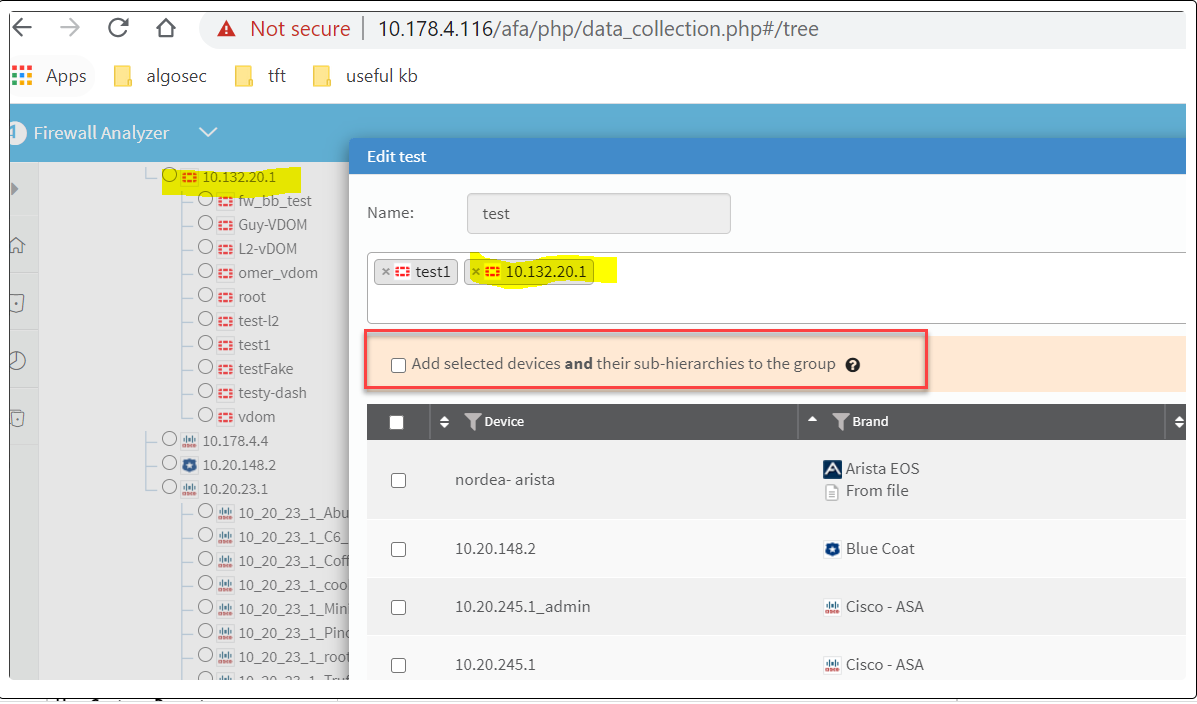
Uncheck_Parent_Addition_Checkbox |
Determines whether or not the Add selected devices and their sub-hierarchies to the group checkbox is selected by default when adding a group to AFA:
|
|
Controls how the URL Category is considered when the destination is not 'any' and there are URL Categories defined.
|
|
|
Determines whether custom report pages are enabled. For more details, see Custom report pages. Possible values:
|
|
|
Use_Nexus_Wildcards |
Determines whether Traffic Simulation Query results on Cisco Nexus devices use wildcard IP ranges. Possible values:
|
| Applicable to Cisco PIX only. When set to "yes", AFA produces a log message for any interface in the .urt file that does not exist in user_routing.urt. | |
|
WEBGUI_SESSION_LENGTH |
Defines the maximum length of a UI session that is not active, in minutes. Any session that goes on for longer than the defined setting is automatically ended. Default= 300 (minutes) |