Customize baseline configuration profiles
AFA includes a set of built-in baseline configuration compliance profiles suitable for all device brands which appear as options in the Baseline Configuration Compliance Profile drop-down list and in the /usr/share/fa/data/baseline_profiles/ directory.
Note: CIS Baseline Compliance report for Check Point
The CIS Baseline Compliance report for Check Point devices provides guidance how to establish a secure configuration posture for Check Point Firewall versions R75.x – 80.x installed on Gaia Platform.
If desired, you can create custom baseline compliance profiles.
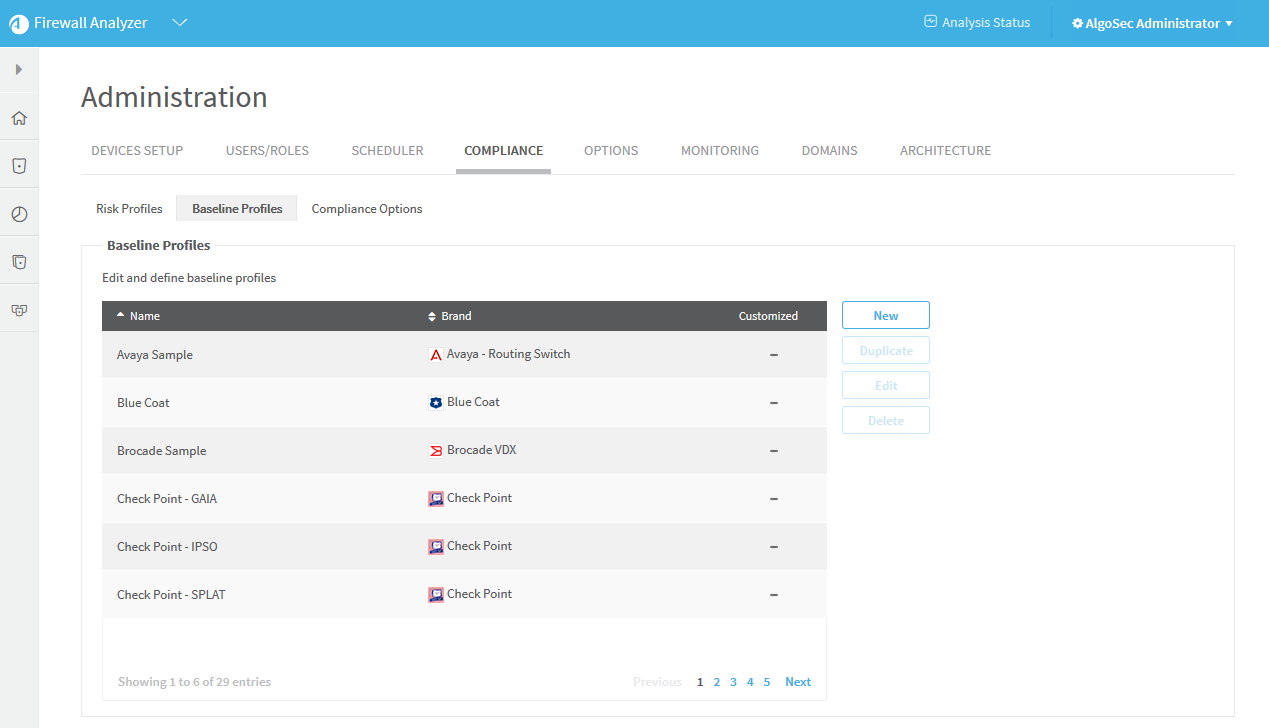
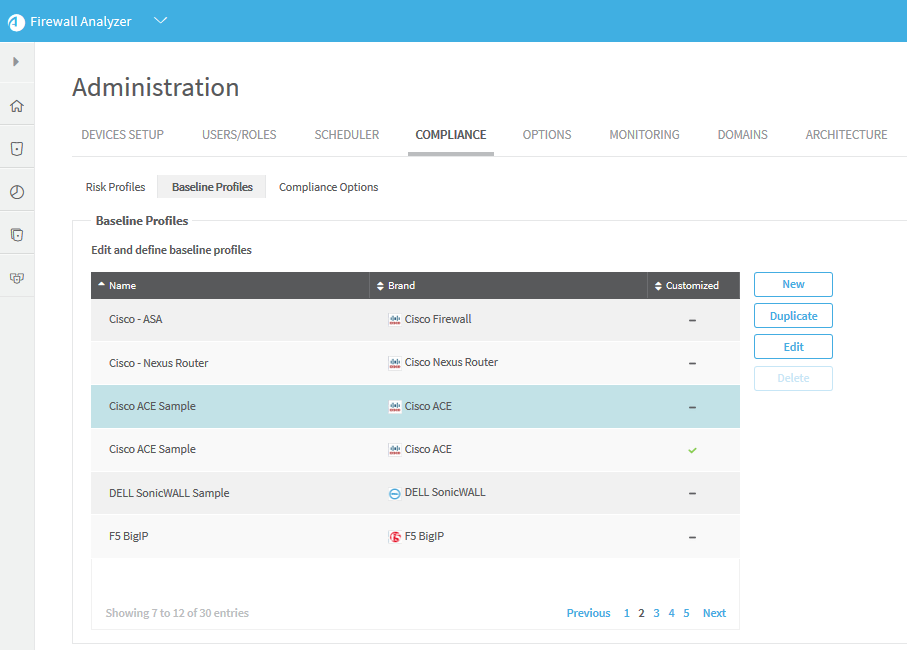
Access baseline profiles configuration
Do the following:
-
In the toolbar, click your username.
A drop-down menu appears.
-
Select Administration.
The Administration page appears, displaying the Options tab.
-
Click the Compliance tab.
The Compliance tab appears, displaying the Risk Profiles sub-tab.
-
Click the Baseline Profiles sub-tab.
A list of baseline profiles appears.
Add a custom baseline configuration compliance profile
Do the following:
-
Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
Click New.
The baseline profile form appears.
- Complete the fields using Example: Customize a baseline configuration compliance profile.
-
Click Save.
The new custom baseline profile appears in the baseline profile table.
Note: A  appears in the Customized field of all custom baseline profiles.
appears in the Customized field of all custom baseline profiles.
Duplicate a baseline configuration compliance profile
You can create a custom baseline configuration compliance profile by duplicating an existing baseline profile and editing the duplicate.
Do the following:
-
Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
Select one of the baseline profiles.
-
Click Duplicate.
The baseline profile form appears with the values of the original profile.
-
Edit the fields, as desired, using Example: Customize a baseline configuration compliance profile.
Note: To prevent the creation of two baseline profiles with the same display name, change the Profile Name.
-
Click Save.
The new custom baseline profile appears in the baseline profile table.
Note: A  appears in the Customized field of all custom baseline profiles.
appears in the Customized field of all custom baseline profiles.
Edit a baseline configuration compliance profile
You can create a custom baseline configuration compliance profile by editing an existing baseline profile.
Note: The original baseline profile will not be over-written, but it will not be available to use unless you delete the new custom baseline profile.
Do the following:
-
Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
Select a baseline profile.
-
Click Edit.
The baseline profile form appears.
- Edit the fields using Example: Customize a baseline configuration compliance profile.
-
Click Save.
The new custom baseline profile appears in the baseline profile table.
Note: A  appears in the Customized field of all custom baseline profiles.
appears in the Customized field of all custom baseline profiles.
Delete a custom baseline configuration compliance profile
Note: You can only delete custom baseline profiles. Custom baseline profiles are indicated with a  in the Customized field.
in the Customized field.
Do the following:
- Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
Select one of the custom baseline profiles.
-
Click Delete.
-
Click OK.
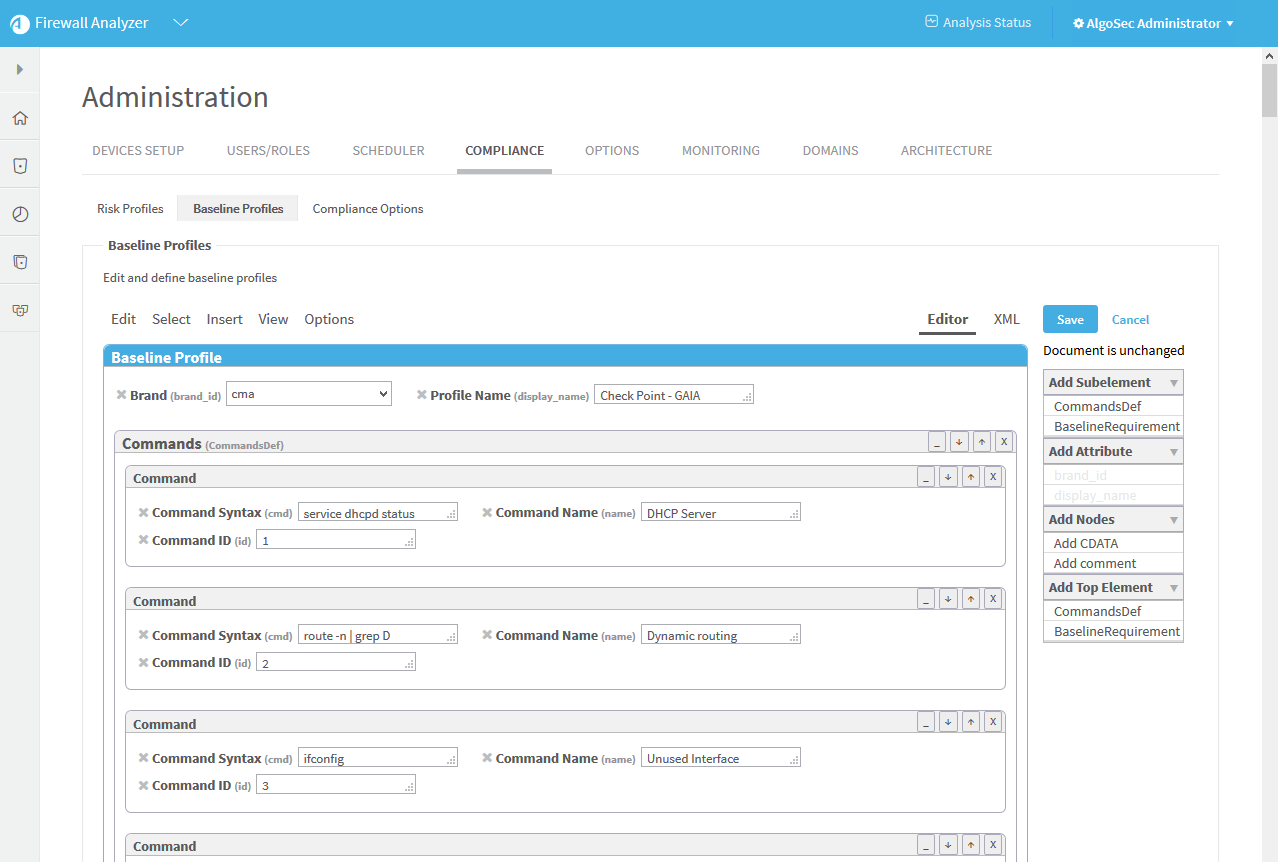
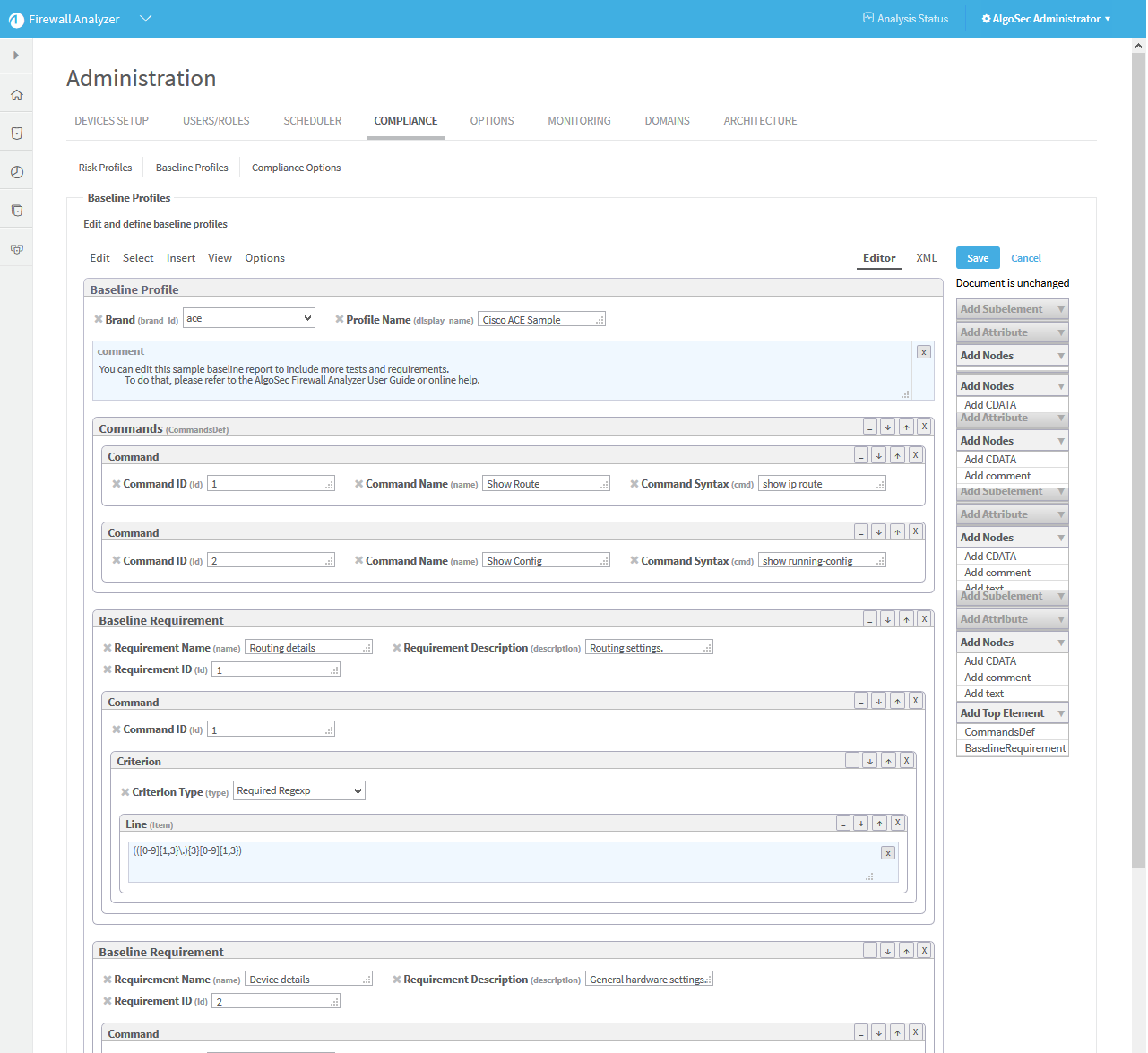
Example: Customize a baseline configuration compliance profile
The following is an example of adding an additional command and baseline requirement to an existing Cisco baseline profile.
-
Access the Baseline Profile configuration area. For details, see Access baseline profiles configuration.
-
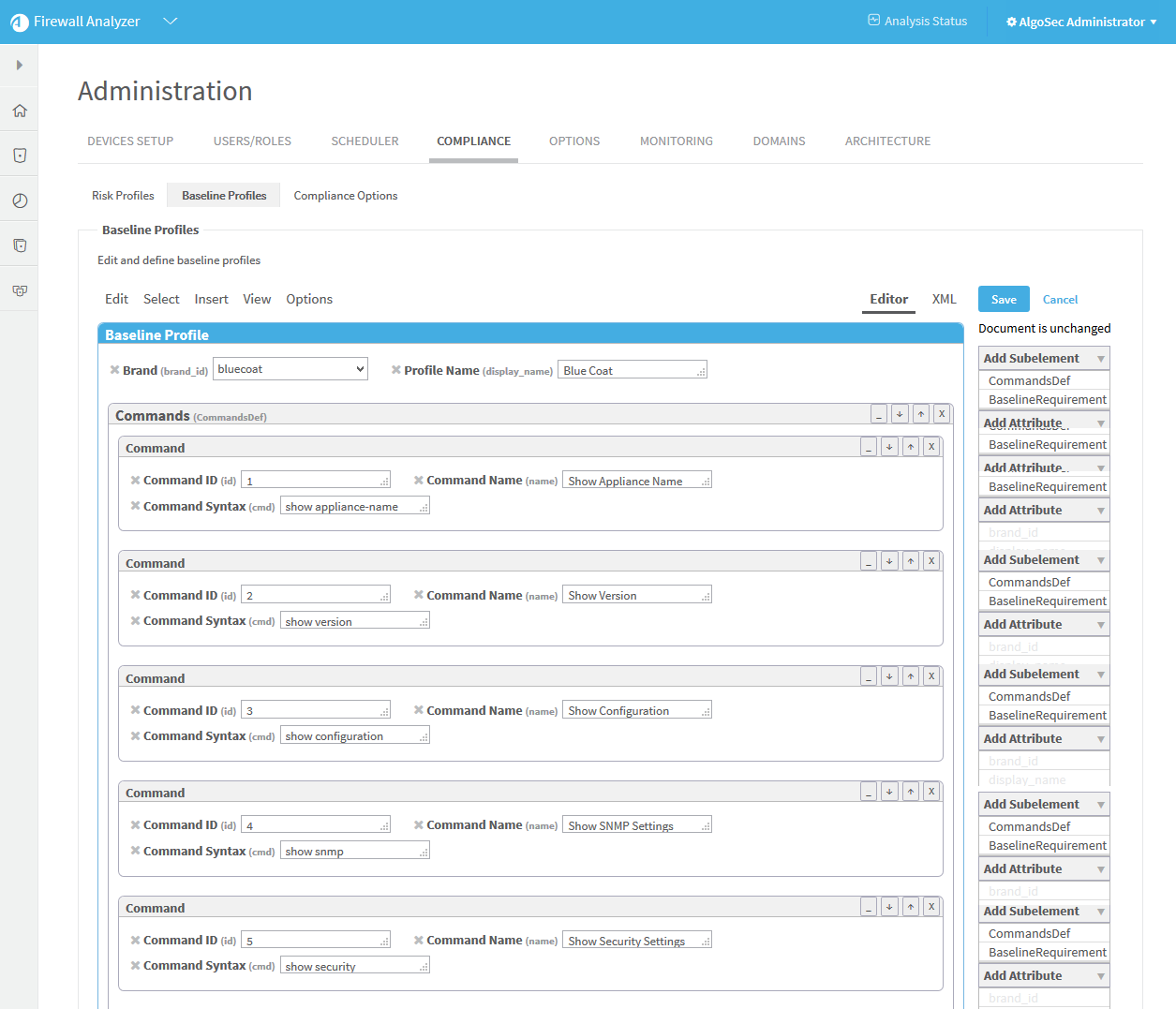
Select a baseline profile.
In this example, we selected the Cisco ACE Sample profile. The profile is highlighted in blue.
-
Click Edit.
The baseline profile form appears.
-
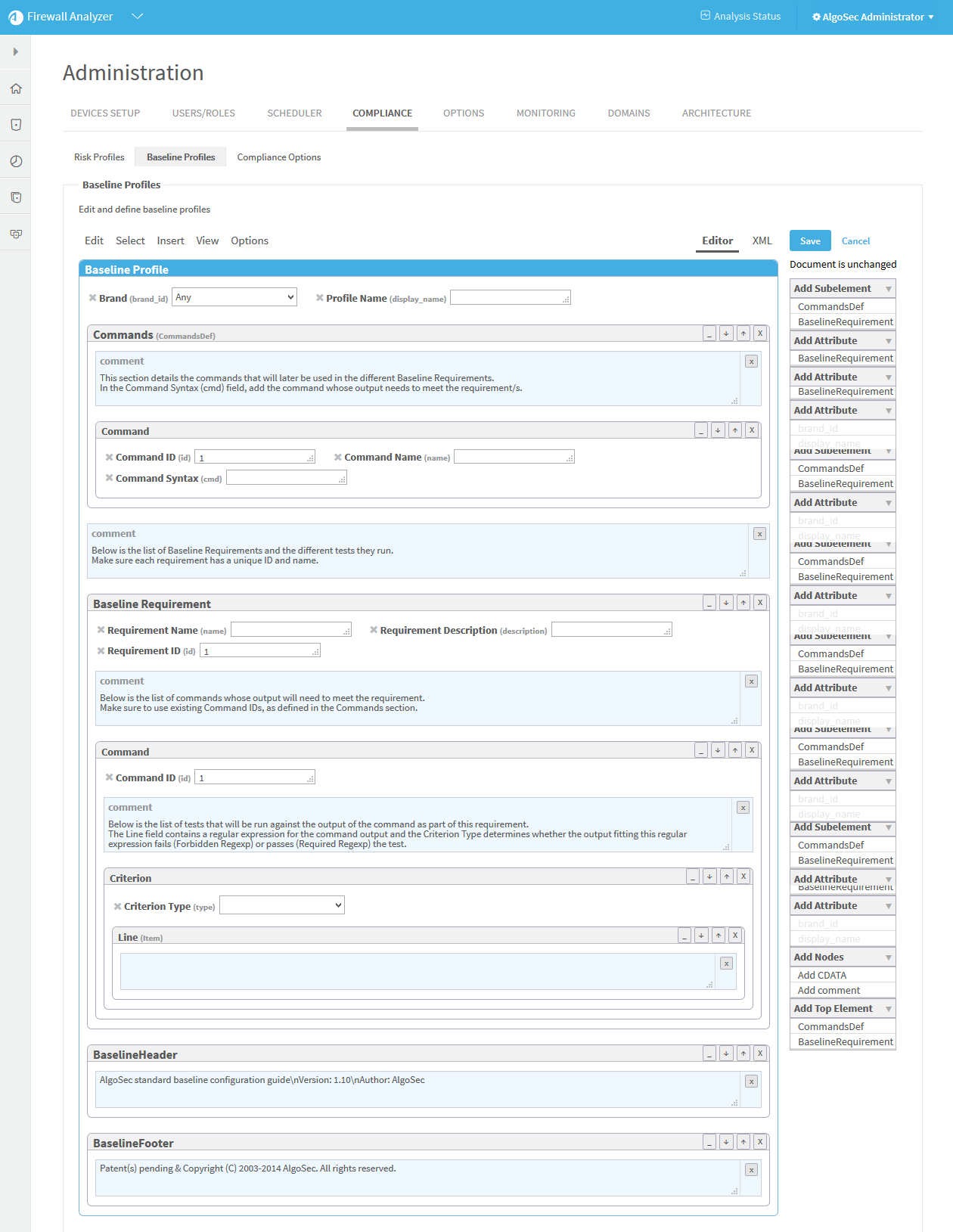
To add a command to the profile:
-
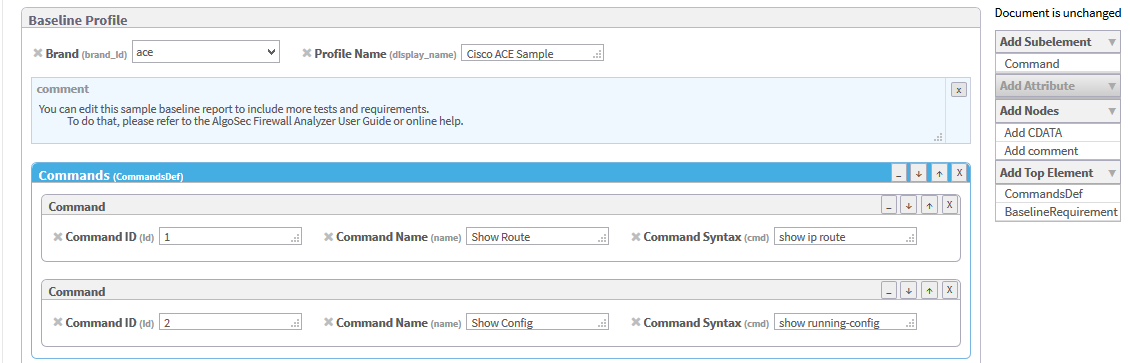
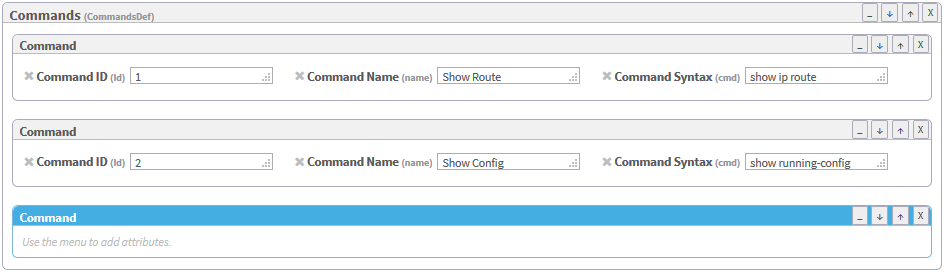
Click Commands (CommandDef).
The Commands area is highlighted in blue.
-
In the Add Subelement menu on the right side of the workspace, click Command.
An additional Command window appears in the profile.
Note: You can click X at anytime to remove a Top Element, Subelement, or Attribute from the profile.
-
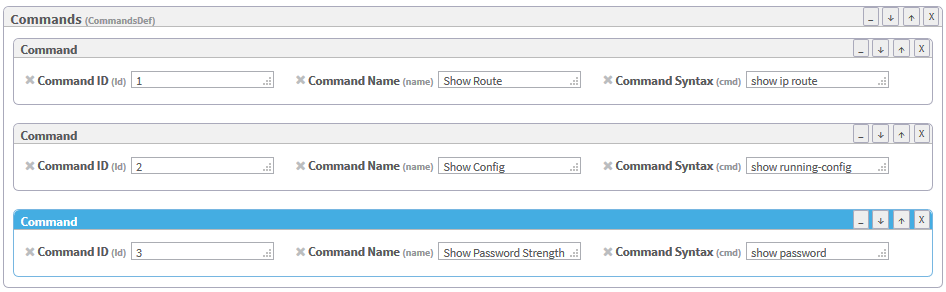
- In the Add Attribute menu on the right side of the workspace, click attributes to add to the command. Available options are id (Command ID), name (Command Name), and cmd (Command Syntax). For details, see Command.
-
Fill in attribute fields.
Note: The Command ID must be unique.
-
To add a baseline requirement to the profile:
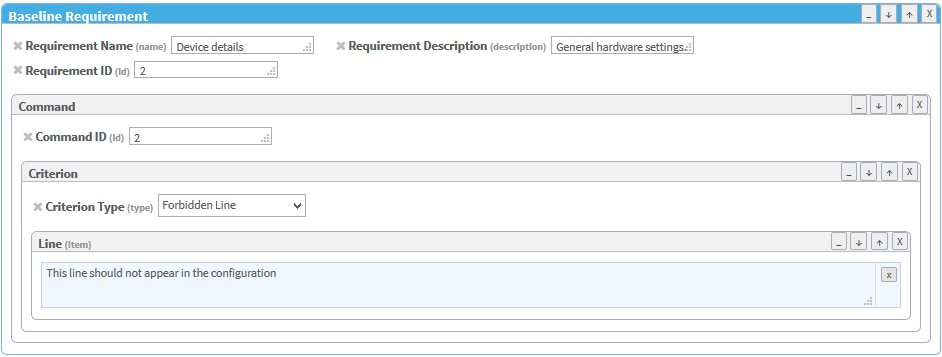
In the Add Top Element menu on the right side of the workspace, click BaselineRequirement.
A additional Baseline Requirement window appears in the profile.

-
In the Add Subelement menu on the right side of the workspace, you can add the following subelements in hierarchical order:
- Command
- Criterion
- Line (Item)
For more details, see Tag Reference,
-
Click Add Attribute to add attributes to the baseline requirement or any of the subelements.
-
Fill in attribute fields.
Note: The Command ID must be unique.
-
Click Save.
This reference describes the use of each tag in the baseline configuration compliance profile. The tags are listed in the same order as they appear in the file.
Tag syntax is presented as follows:
- All parameters are presented in italics.
- All optional elements of the tag appear in square brackets [ ].
Syntax
BaselineProfile brand_id="id" display_name="name"
Description
This is the main tag for the baseline compliance profile, and it identifies the profile.
Parameters
| brand_id |
String. The brand ID of the device brand relevant to the baseline configuration compliance report. The brand_id for each device brand is configured in the brand's brand_config.xml file in /usr/share/fa/data/plugins/brand_name. See the Id parameter in the DEVICE tag. |
| display_name |
String. The name of the baseline configuration compliance profile. The name will appear at the head of the Baseline Configuration Compliance Report. |
Subtags
Example
The following example describes a baseline profile for a Cisco ASA device with the name "Cisco ASA".
BaselineProfile brand_id="asa" display_name="Cisco ASA"
SyntaxCommandsDefDescription
This tag specifies the sequence of commands that AFA should run on the device during analysis.
Parameters
None.
Subtags
Syntax
BaselineRequirement name="name" id="id"
Description
This tag specifies a requirement that the device must meet in order to be considered "in compliance". The requirement consists of a list of required outputs for the commands that AFA will run on the device, specified in the CommandsDef) tag.
Parameters
| name |
String. The requirement's name. Note: Name must not exceed 255 characters. |
| id |
Integer. The requirement's ID and order number. Commands are displayed in numerical order in the Baseline Compliance Report. |
Subtags
ExampleBaselineRequirement name="First" id="1"
Syntax
Command id="id" [name="name"] cmd="cmd"
Description
This tag specifies a command that AFA should run on the device.
Parameters
| id |
Integer. The command's ID and order number. Commands are implemented in numerical order. |
| name |
String. The command's name. |
| cmd |
String. The command that AFA should run on the device. |
Subtags
ExampleCommand id="1" name="Check Access" cmd="show access-list"
Syntax
Criterion type="type"
Description
This tag specifies a criterion that the command output must meet.
Parameters
| type |
String. The criterion type. This can be any of the following:
|
Subtags
- Item)
ExampleCriterion type="Custom Function"
Syntax
Item [comments="comments"]
Description
This tag specifies information about a criterion that the command output must meet.
Parameters
| comments |
String. Comments about a criterion that the command output must meet. |
Contents
This tag contains further details about a criterion that the command output must meet.
Subtags
None.
Example
<Item comments="first required line for command 2">extended permit ip 207.193.122.0 255.255.255.0</Item>
Syntax
BaselineHeader title="title"
Description
This tag specifies information about the header text of the Baseline Compliance Report.
Parameters
| title |
String. The title that should appear in the header section of the report page. |
Contents
This tag contains the header text that should appear in the Baseline Compliance Report.
Subtags
None.
Example<BaselineHeader title="Introduction">Introduction to the report</BaselineHeader>
Syntax
BaselineFooter title="title"
Description
This tag specifies information about the footer text of the Baseline Compliance Report.
Parameters
| title |
String. The title that should appear in the footer section of the report page. |
Contents
This tag contains the footer text that should appear in the Baseline Compliance Report.
Subtags
None.
Example<BaselineFooter title="Summary">Summary of the report</BaselineFooter>
Sample Baseline Configuration Compliance Profile
<BaselineProfile display_name="Custom Profile" brand_id="asa">
<CommandsDef>
<Command id="1" name="Check Access" cmd="show access-list" />
</CommandsDef>
<BaselineRequirement name="First" description="This is first requirement."
id="1">
<Command id="1">
<Criterion type="Required Line">
<Item comments="">extended permit ip 207.193.122.0 255.255.255.0</Item>
<Item comments="">extended permit tcp object-group</Item>
</Criterion>
<Criterion type="Required Regexp">
<Item>.*\.company\.com</Item>
</Criterion>
<Criterion type="Forbidden Line">
<Item>extended deny ip host 100.77.20.9 192.168.52.0</Item>
</Criterion>
<Criterion type="Custom Function">
<Item>perl /home/shira/.fa/check_resolv.pl</Item>
</Criterion>
</Command>
</BaselineRequirement>
<BaselineHeader title="Introduction">Introduction to the report - freetext
</BaselineHeader>
<BaselineFooter title="Summary">Summary of the report - freetext
</BaselineFooter></BaselineProfile>
Out-Of-Box commands for baseline compliance reports per vendor/device type
The following are a list of OOB commands available to run baseline compliance reports per vendor/device type:
-
Exit expert mode
-
Minimum Password Length
-
Disallow Palindrome setting
-
Password Complexity
-
Password reuse setting
-
History length setting
-
Password Expiration setting
-
Warn Users before Password Expiration x days setting
-
The lockout users after x days setting
-
The Deny access to unused accounts setting
-
The Days of non-use before lock-out setting
-
Force users to change password at first login
-
The Deny access after failed login attempts setting
-
The Deny access after failed login attempts setting
-
The Allow access again after time setting
-
Shows configuration message settings
-
Ensure Core Dump is enabled
-
Ensure Config-state is saved
-
Disables the unused interface
-
Show primary DNS
-
Show secondary DNS
-
Show tetiary DNS
-
Check IPv6 status
-
Check hostname
-
Status of the telnet
-
Status of the DHCP Server
-
Check whether the SNMP agent is configured
-
Check whether the SNMP agent-version v3-only is configured
-
Check whether the SNMP traps are configured
-
Check whether the SNMP traps receivers are configured
-
Check the status of NTP
-
Verify the IP address is configured for Primary and Secondary NTP server
-
Verify the Timezone
-
Verify the last successful backup
-
List of snapshots taken on the system
-
CLI Session Timeout value
-
WebUI Session Timeout value
-
Check TACACS+ server status
-
Check TACACS+ servers list
-
Check RADIUS servers list
-
Device access restrictions
-
Verify the mgmtauditlogs
-
verify the auditlog
-
verify the cplogs
-
service dhcpd status
-
route -n | grep D
-
ifconfig
-
cat /etc/ssh/sshd_config | grep Protocol
-
cat $FWDIR/conf/snmp.C
-
service telnet status
-
service vsftpd status
-
service tftpd
-
more $FWDIR/conf/objects_5_0.C | grep rlogin_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep telnet_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep client_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep session_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep tcpstarttimeout
-
more $FWDIR/conf/objects_5_0.C | grep tcptimeout
-
more $FWDIR/conf/objects_5_0.C | grep tcpendtimeout
-
more $FWDIR/conf/objects_5_0.C | grep udptimeout
-
more $FWDIR/conf/objects_5_0.C | grep icmptimeout
-
more $FWDIR/conf/objects_5_0.C | grep othertimeout
-
exit 1
-
show configuration ntp
-
show configuration dns
-
show version all
-
show password-controls complexity
-
echo show ssh server protocol | clish
-
echo show voyager ssl-level | clish
-
echo show snmp community | clish
-
echo show ssh server login-grace-time | clish
-
echo show dhcp server all | clish
-
echo show ospf summary | clish
-
echo show rip summary | clish
-
(echo show interfaces | clish) | egrep -v '(Type|IP)'
-
echo show net-access telnet | clish
-
echo show net-access ftp | clish
-
echo show net-access tftp | clish
-
more $FWDIR/conf/objects_5_0.C | grep rlogin_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep telnet_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep client_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep session_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep tcpstarttimeout
-
more $FWDIR/conf/objects_5_0.C | grep tcptimeout
-
more $FWDIR/conf/objects_5_0.C | grep tcpendtimeout
-
more $FWDIR/conf/objects_5_0.C | grep udptimeout
-
more $FWDIR/conf/objects_5_0.C | grep icmptimeout
-
more $FWDIR/conf/objects_5_0.C | grep othertimeout
-
echo show ntp active | clish
-
echo show ntp servers | clish
-
echo show message all | clish
-
echo show message all status | clish
-
echo show dns primary | clish
-
echo show dns secondary | clish
-
echo ver | clish
-
echo show syslog all | clish
-
echo show password-controls all | clish
-
service dhcpd status
-
route -n | grep D
-
ifconfig
-
cat /etc/ssh/sshd_config | grep Protocol
-
cat $FWDIR/conf/snmp.C
-
service telnet status
-
service vsftpd status
-
service tftpd
-
more $FWDIR/conf/objects_5_0.C | grep rlogin_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep telnet_max_auth_allowed
-
more $FWDIR/conf/objects_5_0.C | grep client_max_auth_allowed
-
more $FWDIR/conf/objects_.C | grep session_max_auth_allowed
-
more /opt/spwm/conf/cp_http_admin_server.conf | grep SESSION_TIMEOUT
-
more $FWDIR/conf/objects_5_0.C | grep tcpstarttimeout
-
more $FWDIR/conf/objects_5_0.C | grep tcptimeout
-
more $FWDIR/conf/objects_5_0.C | grep tcpendtimeout
-
more $FWDIR/conf/objects_5_0.C | grep udptimeout
-
more $FWDIR/conf/objects_5_0.C | grep icmptimeout
-
more $FWDIR/conf/objects_5_0.C | grep othertimeout
-
cat /etc/sysconfig/ntp
-
timezone -show
-
dns
-
ver
-
cat /etc/syslog.conf
-
cat /etc/ssh/sshd_config | grep LoginGraceTime
-
show running-config
-
show version
-
show route | begin Gateway
-
more system:running-config | grep snmp-server | grep community
-
show running-config ntp
-
show running-config dns server-group
-
show running-config
-
show version system
-
show route | begin Gateway
-
show running-config | grep snmp-server | grep community
-
show ntp
-
show dns system
-
show running-config
-
show version
-
show snmp community
-
show ntp associations
-
show ip interface
-
show cef interface | include IP unicast RPF check
-
show running-config
-
show version
-
show password strength-check
-
show ip interface
-
show banner motd | count
-
show running-config | begin vty
-
show running-config | begin console
-
show hosts
-
show running-config security
-
cat /var/local/scf/algosec
-
list sys ntp all-properties
-
list sys sshd all-properties
-
list sys syslog remote-servers
-
list auth password-policy all-properties
-
list sys snmp all-properties
-
list sys global-settings console-inactivity-timeout
-
list sys global-settings mgmt-dhcp
-
list sys dns
-
show net route dynamic
-
list net self-allow
-
cat /var/local/scf/algosec
-
list sys ntp all-properties
-
list sys sshd all-properties
-
list sys syslog remote-servers
-
list auth password-policy all-properties
-
list sys snmp all-properties
-
list sys global-settings console-inactivity-timeout
-
list sys global-settings mgmt-dhcp
-
list sys dns
-
show net route dynamic
-
list net self-allow
-
get system status
-
end
-
config global
-
show system ntp | grep set
-
get system snmp sysinfo
-
show full-configuration | grep ''
-
show system global
-
show system dns
-
show system sflow
-
show system central-management
-
show log syslogd setting
-
show system password-policy
-
get system info admin ssh
-
get config
-
get system
-
get hostname
-
get console
-
get snmp
-
get ssh
-
get vr untrust proto ospf config
-
get admin auth banner
-
get dns host settings
-
show version
-
show configuration | display inheritance | display set | no-more use_listener="yes"
-
show configuration system name-server
-
show configuration system login retry-options
-
show version
-
show configuration | display inheritance | display set | no-more use_listener="yes"
-
show configuration system name-server
-
show configuration system login retry-options
-
show config running
-
show system info
-
show ntp
-
show config pushed-template | match snmp
-
configure
-
show deviceconfig system dns-setting
-
show mgt-config password-complexity
-
show deviceconfig system snmp-setting
-
show template deviceconfig system dns-setting
-
show template mgt-config password-complexity
-
exit