Customize the regulatory compliance report
Remove and add compliance reports
Do the following:
-
In the toolbar, click your username.
A drop-down menu appears.
-
Select Administration.
The Administration page appears.
-
Click the Compliance tab.
The Compliance page appears.
-
Click the Compliance Options sub-tab.
-
Next to Regulatory compliance reports to be included in the device analysis, click Select.
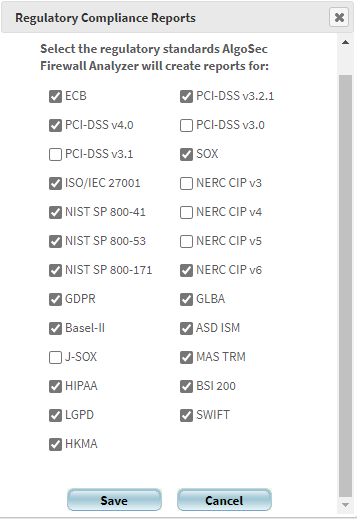
The Regulatory Compliance Reports dialog is displayed.
For a description of each standard, see Supported regulatory compliance reports.
-
To enable a report, select its check box.
-
To disable a report, clear its check box.
-
Click Save.
Note: When upgrading AFA, any newly supported reports are automatically enabled.
Supported regulatory compliance reports
|
Standard |
Description |
|---|---|
| US Centric | |
|
SOX |
Sarbanes-Oxley Act (SOX) compliance is required for publicly traded companies on US markets. |
| NERC CIP v3, v4, v5 |
Required for Power manufacturing and distribution, including Oil, Gas and Nuclear. The customer may choose to analyze against either v3, v4 or v5 of the NERC CIP standards, to evaluate readiness for future standard deadlines. |
|
HIPAA |
Required for protecting patient data in US healthcare companies. |
| NIST SP 800-171 | This report uses the National Institute of Standards and Technology (NIST) document Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations, Revision 1 (June 2015). |
|
NIST SP 800-53 |
Required by US DoD. This report uses the National Institute of Standards and Technology (NIST) Security and Privacy Controls for Federal Information Systems and Organizations, Revision 4 (April 2013). |
|
NIST SP 800-41 |
Required by US DoD. This report uses the National Institute of Standards and Technology (NIST) Guidelines on Firewalls and Firewall Policy, Revision 1 (Sep 2009). |
|
GLBA |
Consumer identity safety requirements for US companies. |
| Europe Centric | |
|
ISO/IEC 27001 |
ISO/IEC 27001:2022 formally specifies an Information Security Management System (ISMS), a suite of activities concerning the management of information security risks. |
|
Basel-II |
This addresses the Basel Committee on Banking Supervision's framework International Convergence of Capital Measurement and Capital Standards (June 2006). |
| BSI 200 | This addresses the recommendations from the German Federal Office for Information Security (BSI) on methods, processes, procedures, approaches and measures for information security as laid out in the BSI standard 200-1 information security management systems (ISMS) and its supplementary standard, the BSI standard 200-2 IT-Grundschutz methodology. |
| GDPR | This addresses the European Parliament and the Council of the European Union's regulation, on the protection of natural persons with regard to the processing of personal data and on the free movement of such data. |
| ECB | This addresses the European Central Bank (ECB) which is the central bank of the European Union countries which have adopted the euro. The assessment guide has been developed by the European Forum on the Security of Retail Payments, SecuRe Pay (The Forum), on the basis of the final recommendations for the security of internet payments. |
| DORA | DORA covers all financial entities operating within EU member states, standardizing digital resilience and cybersecurity requirements across diverse financial markets. By doing so, DORA aims to strengthen the overall stability and security of the EU financial ecosystem against cyber threats and ICT disruptions. |
| Global | |
|
PCI DSS 3.0, 3.1, 3.2.1, 4.0 |
The Payment Card Industry Data Security Standard (PCI DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally. PCI DSS provides a baseline of technical and operational requirements designed to protect cardholder data. You can optionally indicate which servers are in your PCI zone. Specifying these servers enables AFA and AppViz to provide you with more specific security information for PCI applications. See Configure the PCI zone. |
| SWIFT | The SWIFT Customer Security Programme (CSP) supports customers in the fight against cyber-fraud. The CSP establishes a common set of security controls designed to help customers to secure their local environments and foster a more secure financial ecosystem. |
| Australia Centric | |
|
ASD-ISM |
Firewall configuration guidelines from Australian Government. |
| Japan Centric | |
|
J-SOX |
Japanese version of SOX. |
| Singapore Centric | |
|
MAS-TRM |
Guidelines for information security for Singapore operating banks, published by the government banking regulator. |
| Hong Kong Centric | |
|
HKMA |
Guidelines for information security for Hong Kong operating banks, published by the government banking regulator. |
| Brazil Centric | |
|
LGPD |
Guidelines for the protection of personal data as stipulated in the General Data Protection Law of the Federative Republic of Brazil. |
Customize the compliance score value
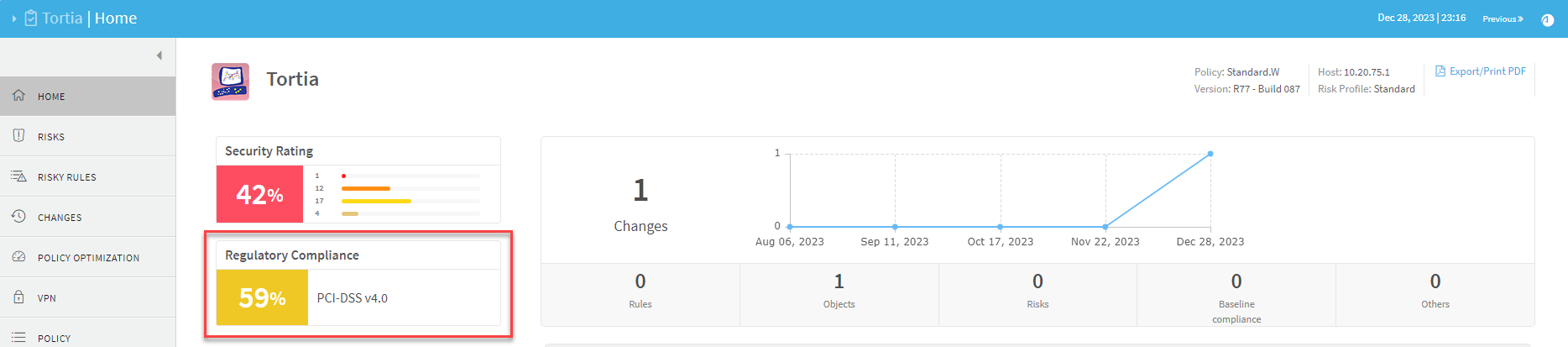
AFA reports' Regulatory Compliance page displays a compliance score which indicates the device's degree of compliance with each compliance report. AFA calculates the compliance score with the following formula:
Compliance score = (X1 + WX2)/(X1 + X2 + X3)
|
This variable... |
Represents... |
|---|---|
|
X1 |
The total number of requirements in the compliance report for which the device policy is compliant. Each of these requirements has a status of |
|
X2 |
The total number of requirements in the compliance report for which additional information or manual verification is necessary for the device policy to meet the requirement. Each of these requirements has a status of |
|
X3 |
The total number of requirements in the compliance report for which the device policy is not compliant. Each of these requirements has a status of |
|
W |
The weight of the number of requirements for which additional information or manual verification is necessary to meet the requirement. The default value is 0.5. |
You can customize the compliance score value by changing the value of the "W" variable.
Do the following:
-
In the toolbar, click your username.
A drop-down menu appears.
-
Select Administration.
The Administration page appears, displaying the Options tab.
-
Click the Advanced Configuration tab.
The Advanced Configuration tab appears.
-
Click Add.
The Add New Configuration Parameter dialog is displayed.
-
In the Name field, type Compliance_Score_Star_Weight.
-
In the Value field, type the value you wish to assign to the "W" variable.
-
Click OK.
-
Click OK.
Customize compliance score severity thresholds
AFA provides the ability to customize the compliance score severity thresholds.
By default, a bad score is 55% and below (red), a moderate score is between 55% and 70% (yellow), and a good score is 70% and above (green).
Do the following:
-
In the toolbar, click your username.
A drop-down menu appears.
-
Select Administration.
The Administration page appears, displaying the Options tab.
-
Click the Advanced Configuration tab.
The Advanced Configuration tab appears.
-
To adjust the threshold for a bad score, do the following:
-
Click Add.
The Add New Configuration Parameter dialog is displayed.
-
In the Name field, type Compliance_Score_Max_Red.
-
In the Value field, type the maximum value for a bad score.
For example, if you want a score of 60% and below to be a bad score, type 60.
-
Click OK.
-
-
To adjust the threshold for a good score, do the following:
-
Click Add.
The Add New Configuration Parameter dialog is displayed.
-
In the Name field, type Compliance_Score_Min_Green.
-
In the Value field, type the minimum value for a good score.
For example, if you want a score of 80% and above to be a good score, type 80.
-
Click OK.
-
-
Click OK.
Configure the PCI zone
Specifying the servers in the PCI zone enables AFA to specify the vulnerability of PCI applications in the PCI regulatory compliance report. Additionally, configuring these servers enables AppViz to tag which network objects intersect the PCI Zone and the applications that use these servers.
Note: This feature is only relevant when using AppViz.
AFA can only show the vulnerability of PCI applications in the PCI report when AppViz is integrated with a vulnerability scanner. When using AppViz without a vulnerability scanner, AppViz will still tag the network objects and applications that intersect the PCI zone with the PCI label.
Do the following:
-
In the toolbar, click your username.
A drop-down menu appears.
-
Select Administration.
-
The Administration page appears, displaying the Options tab.
-
Click the Compliance tab.
The Compliance tab appears, displaying the Risk Profiles sub-tab.
-
Click the Compliance Options sub-tab.
-
In the Regulatory Compliance area, in the PCI zone field, type an IP address, range, or CIDR.
-
To add another entry, click
 , and type the additional value in the field.
, and type the additional value in the field. -
To remove a field, click
 .
. -
In the Vulnerability level threshold field, select the threshold for acceptable vulnerability in the drop-down menu.
Applications with the selected vulnerability level (or lower) will be considered vulnerable in PCI reports. For example, selecting Medium will cause applications with medium or low security scores to be considered vulnerable.
Note: Specifying the vulnerability level threshold is only relevant when AppViz is integrated with a vulnerability scanner.
 .
. .
. .
.