Traffic Logs and Audit Logs
Traffic Logs are produced whenever traffic hits a rule which has been enabled for logging.
There are two kinds of Audit Logs:
-
Logs produced and stored on the device each time a user makes a change to the configuration of a device.
-
Logs that record any alterations made by users within the ASMS interface including login or logout, configuration of users and roles, and changes to risk profiles.
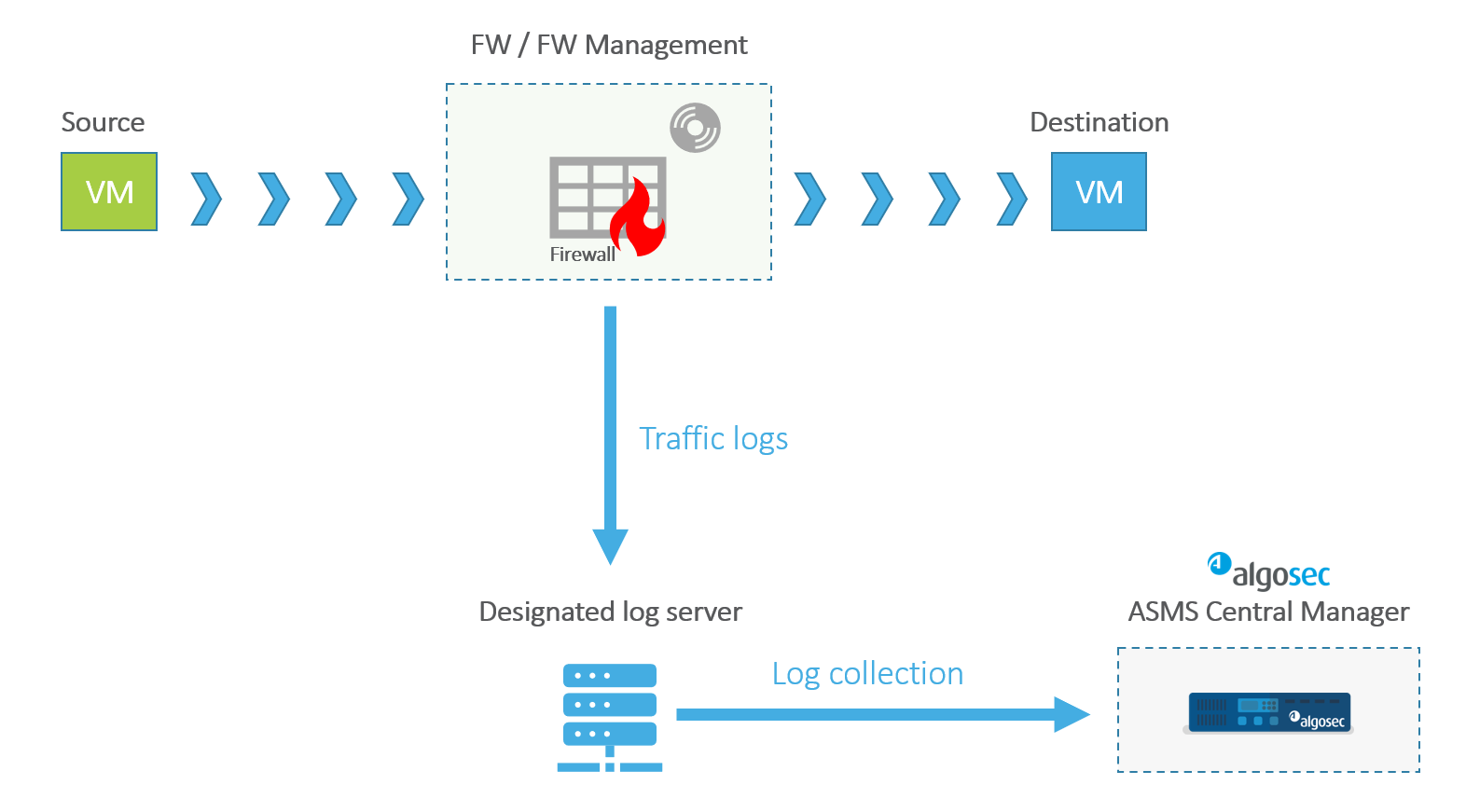
Traffic Logs
Incoming or outgoing traffic through a device is filtered by rules that either allow or disallow (deny) the traffic. For every event that is allowed or denied by a rule enabled for logging, a traffic log is written on the designated log server.
AFA collects the logs from the log server, processes them, crunches matching records, and writes the crunched records to the database tables. The traffic log information is used in AFA analysis and the Policy Optimization page of the report.
Traffic Logs and Policy Optimization
Depending on the Log Collection mode used (for example, standard, extensive, etc.), Policy Optimization analyzes the traffic log records for frequency of rule usage, exposing rules that are hardly used or never used.
The Policy Optimization rule recommendations displayed on the a device report's POLICY OPTIMIZATION page page use traffic logs to provide:
-
Suggestions for Rule Reordering
-
Rule usage statistics including -
-
Unused rules
-
Unused objects within rules
-
Least used rules
-
Most used rules
-
All rule usage (count, last date)
-
All NAT rule usage (count, last date)
-
Policy tuner analysis for all rules, including suggestions for tightening permissive rules
-
Troubleshooting Traffic Logs
Traffic logs are not present for the device
Do the following:
-
If there are no traffic logs for a particular device on the log server, check that there are rules on that device that are configured to send traffic logs.
-
Log into the designated ASMS log server and using dump, make sure that the server is receiving traffic logs in general.
Identifying Traffic Logs
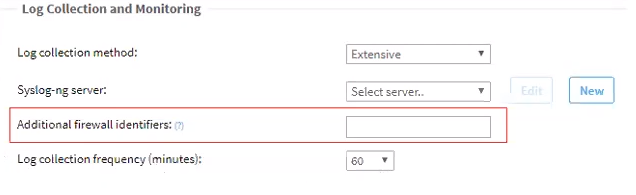
Sometimes additional identifiers are required in order to match between traffic logs and the device that generated them (as a result of load balancing or NAT, etc.). These identifiers must be added to the device configuration Log Collection and Monitoring section in Additional firewall identifiers field. When this field is updated in the device configuration, the device configuration on the log server will be updated.
Note: For devices with hierarchy, add these identifiers via the fwa.meta parameter of the device's meta file:
~/.fa/firewalls/<device name>/fwa.meta.
Audit Logs
Audit logs in the ASMS serve a critical role in maintaining system integrity and security. They capture detailed information about every action that alters the system, split into two distinct categories:
Both types of logs are essential for a comprehensive overview of system activities. They not only facilitate troubleshooting and operational audits but also contribute to regulatory compliance by providing a verifiable record of system changes.
User-Initiated Changes to ASMS
These logs record any alterations made by users within the ASMS interface. Whether it's a user login or logout, configuration of users and roles, or changes to risk profiles, the audit trail includes specifics about the nature of the change, the identity of the user who executed it, and the exact timestamp of the modification.
-
These Audit logs are saved in /var/log/messages. Up to five files of up to 8 MB each are stored. Use the ll command to list them:
-
You can search specific events using the event ID/name. Available options to search from are:
-
Create User
-
Modify User
-
Delete User
-
Create Role
-
Modify Role
-
Delete Role
-
Create Risk Profile
-
Delete Risk Profile
-
Modify Risk Profile
-
Successful login
-
Unsuccessful login
-
Unsuccessful impersonation
-
Login Failed - System Error
-
Manual logout
-
Session expired logout
-
-
By default, these messages are enabled. To disable these messages, use the AUDIT_LOG advanced parameter. See AUDIT_LOG.
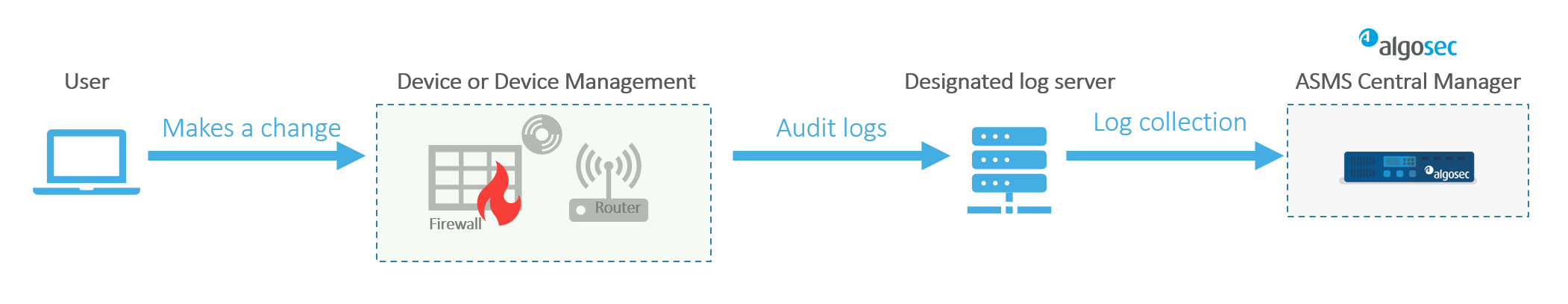
Device-Level Changes
In contrast, device-level logs capture changes made directly on the devices managed by ASMS. Similar to user-initiated logs, these records detail what the change was, who made it, and when it occurred.
Audit logs, produced each time a user makes a change to the configuration of a device, are collected by ASMS during both the Log Collection Process and the Monitoring Process . They feed the Changed by fields of the Changes page of the Report and the Changes tab for the device.
-
Audit logs record changes on ASMS configuration files. You can see and edit the list of monitored configuration files in /etc/audit/rules.d/audit.rules.
-
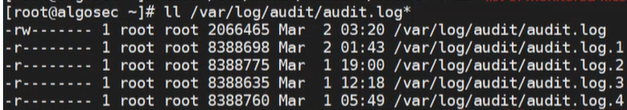
The Audit logs are saved in /var/log/audit/audit.log and similarly named files. Up to five files of up to 8 MB each are stored. Use the ll command to list them:
-
Use the ausearch command and the key value AlgoSec to filter for ASMS audit logs:
[root@algosec ~]# ausearch -k AlgoSec | less
Troubleshooting Device-Level Changes logs
The following can be signs of misconfiguration:
-
No information in the Changed by column of the Changes tab
-
Log Collection status is red, indicating Log Collection failure
Do the following:
-
Check the Device Configuration to verify that the correct log server is configured and that this is the log server that Log Collection is querying.
-
See Algopedia articles that refer to audit log troubleshooting.