Set up the Azure Traffic Sensor
This topic provides step-by-step instructions for setting up the Azure Traffic Sensor within your Application Discovery environment. The Azure Traffic Sensor queries Traffic analytics in Azure , which analyzes Network Watcher flow logs to provide insights about traffic flows in your Azure cloud. It captures traffic between different security groups, as well as traffic that flows through a Network Security Group (NSG) associated with a subnet or virtual network.
Note: While Traffic Analytics is not specifically designed for monitoring traffic within the same security group, it can provide some level of visibility depending on your network configuration and application logging practices.
Note: Azure Traffic Sensors support both NSG Flow Logs and VNet Flow Logs. However, VNet Flow Logs are typically the preferred option because they offer a broader scope, are easier to configure, and align with Microsoft's plans to phase out NSG Flow Logs in the future.
The Azure traffic sensor: is installed wherever the Application Discovery Server is running on your system.
Prerequisites
Before setting up the Azure Traffic Sensor, ensure the following prerequisites are met:
-
Open Port TCP/9745 for communication between the Application Discovery server hosting the Azure Traffic Sensor and the Central Manager.
-
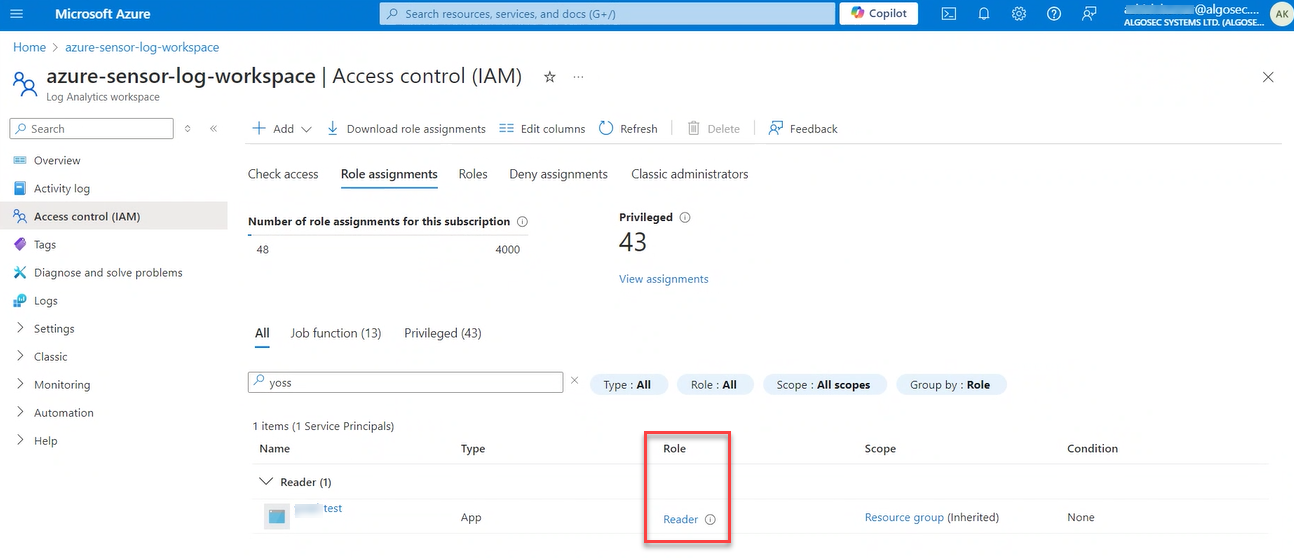
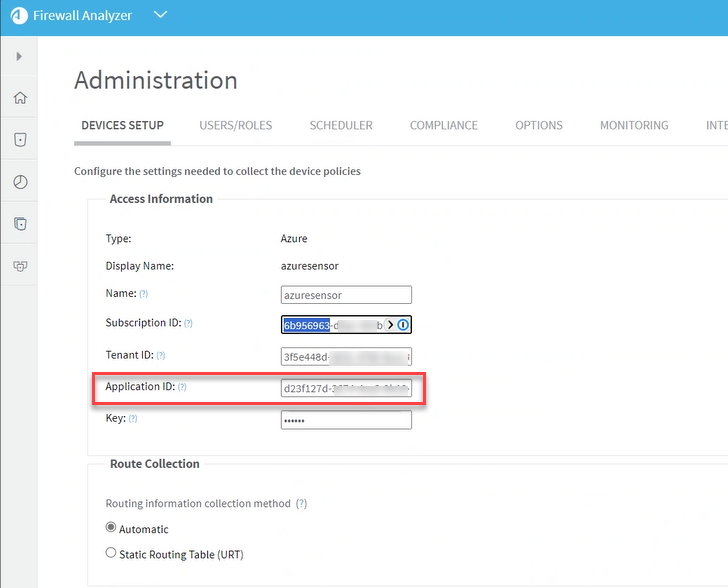
Enterprise Application Permissions: The Enterprise Application as defined in the Azure Portal must have at least the "Reader" role to access the resource group containing the Log Analytics workspace ID.
-
NSG Flow Log Support: Only NSG flow log version 2 is supported.
-
Recommended Flow Log: It is recommended to use VNET flow logs.
-
Subnet Configuration: If necessary, update the subnet in the AAD configuration to include the flows for discovery.
Configuration Steps
Do the following:
-
Configure an Azure subscription in AFA: Ensure that you have an Azure subscription onboarded to AFA. For instructions, see Add Microsoft Azure subscriptions in AFA.
-
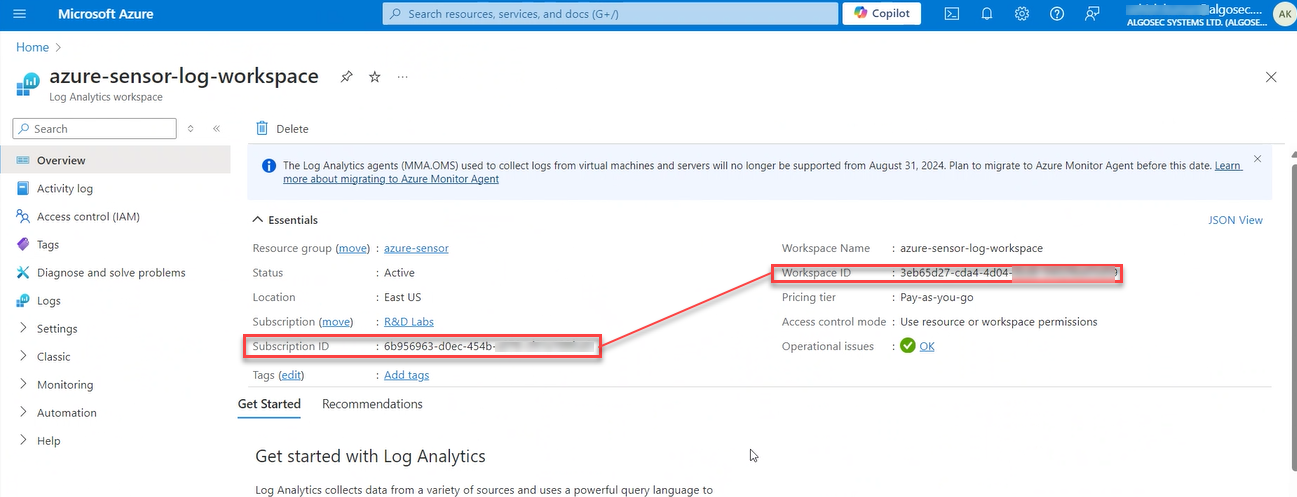
Set Workspace ID(s) per subscription: For each Azure subscription, configure the Workspace ID for the Azure Traffic Sensor, by editing the properties file located at /data/algosec-ms/config/ms-aad-azure-sensor-prod.properties.
For each Azure subscription, add the Azure Device Name (from AFA) and list of Workspace IDs to the properties file as follows:
azure.device.nameToWorkspaceIdMap.<DEVICE_NAME>=<WORKSPACE_ID1>,<WORKSPACE_ID2>
for example:
azure.device.nameToWorkspaceIdMap.azuresensor=3eb65d27-cda4-4d04-8bd6-04029be03d59
-
Set Data Fetching Interval: Set the Azure sensor to retrieve data from the analytics workspace at either 10-minute or 60-minute intervals.
Add the following line to the properties file located at /data/algosec-ms/config/ms-aad-azure-sensor-prod.properties:
azure.log.collector.query.time.interval.minutes=60
-
Set Fetch past data: When the Azure sensor is restarted or used for first time, add the following to the to the properties file to fetch the past data:
azure.log.collector.query.initial.time.interval.hours=1
-
Analytic Workspace Configuration: In the Azure Portal, configure a single analytic workspace to ingest either NSG or VNET flow logs, but not both.
-
Restart the Azure Sensor service by running the following command:
service ms-aad-azure-sensor restart
-
Configure an Application Discovery subnet: for instructions see Configure an Application Discovery subnet.