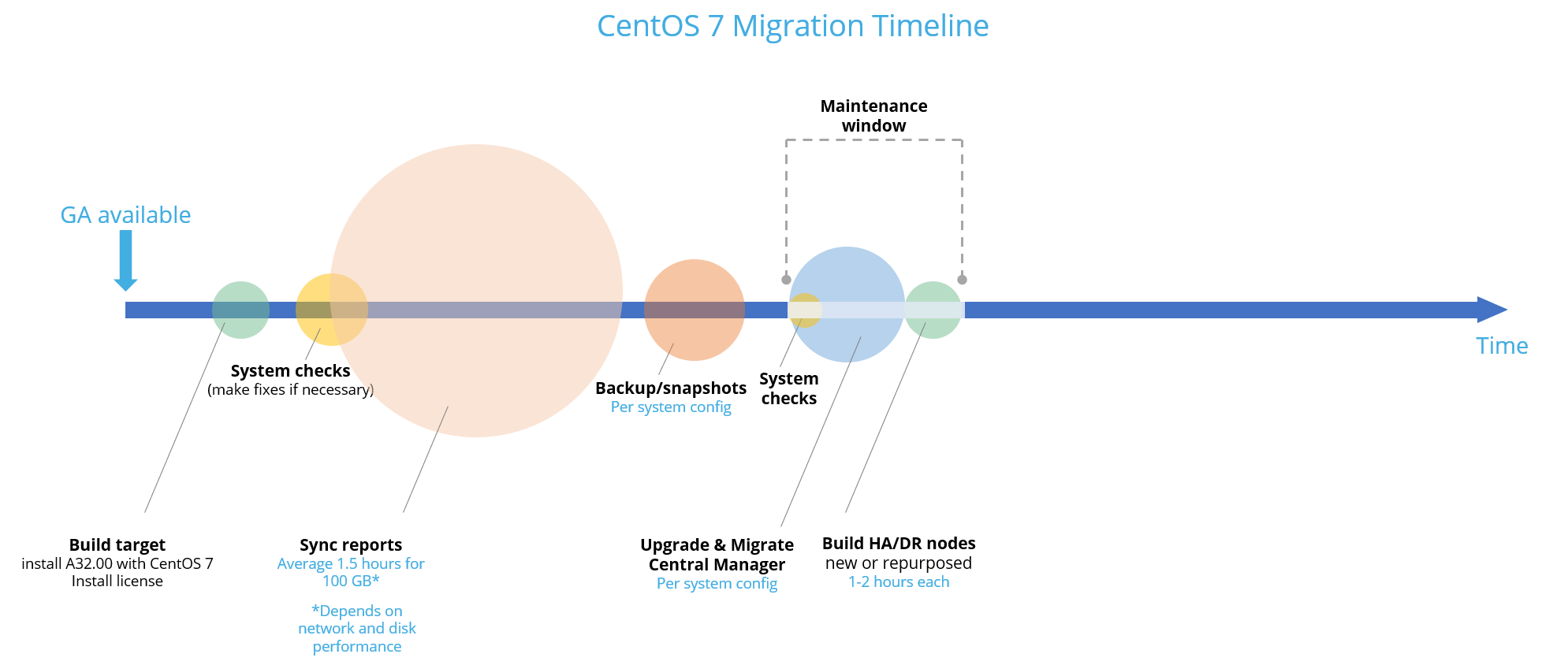
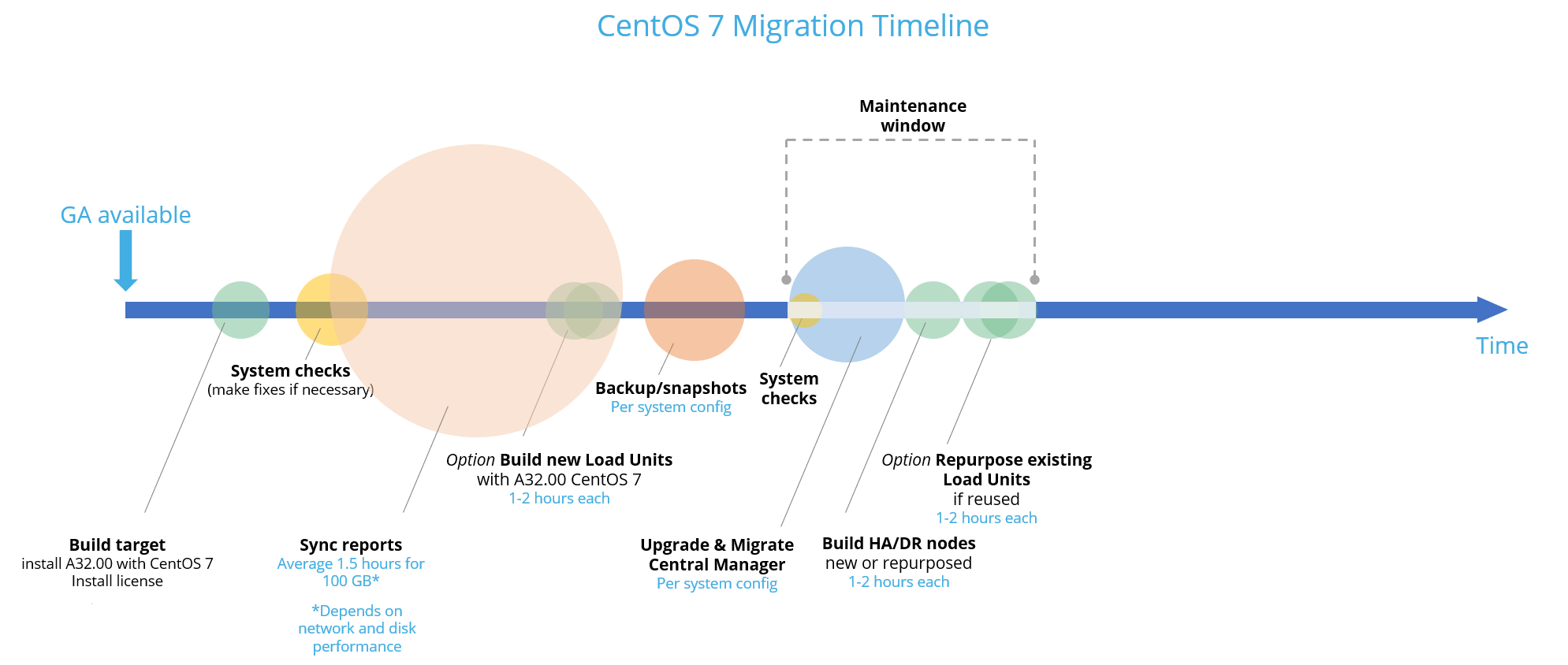
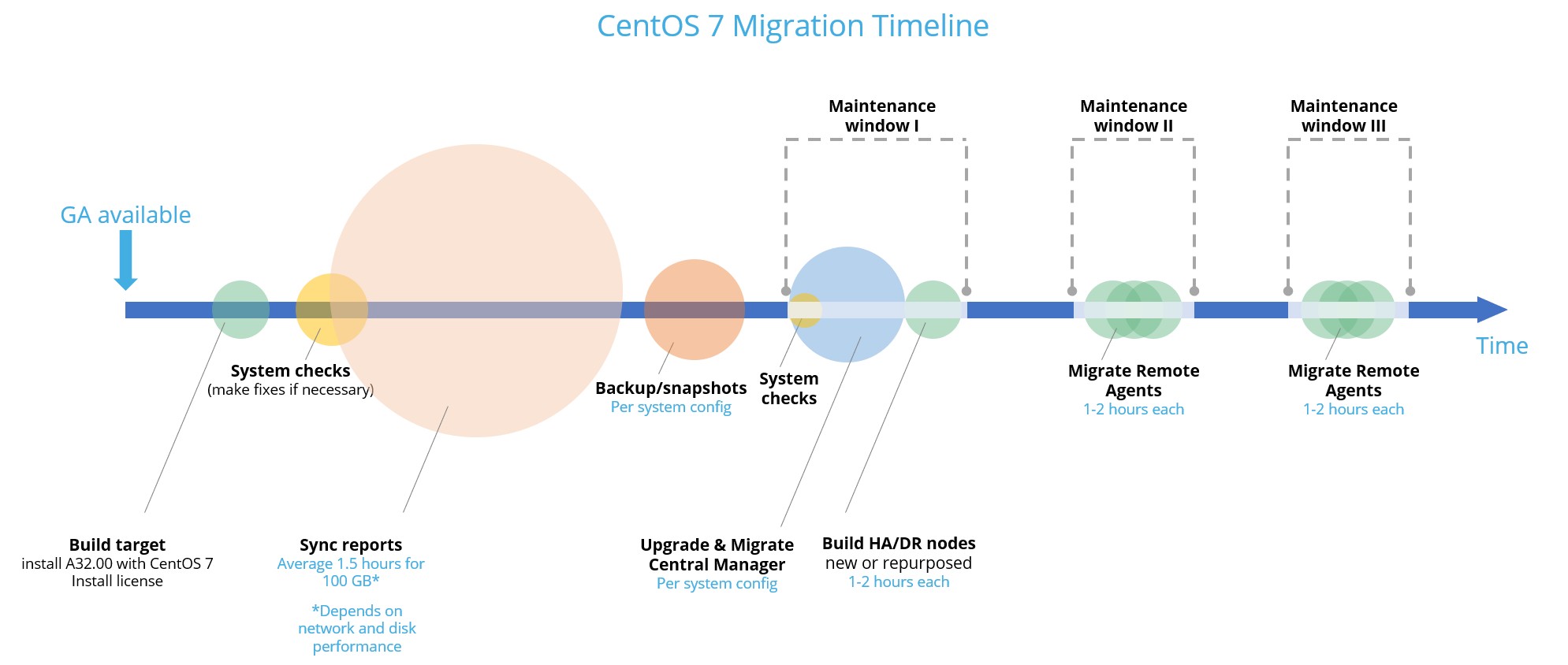
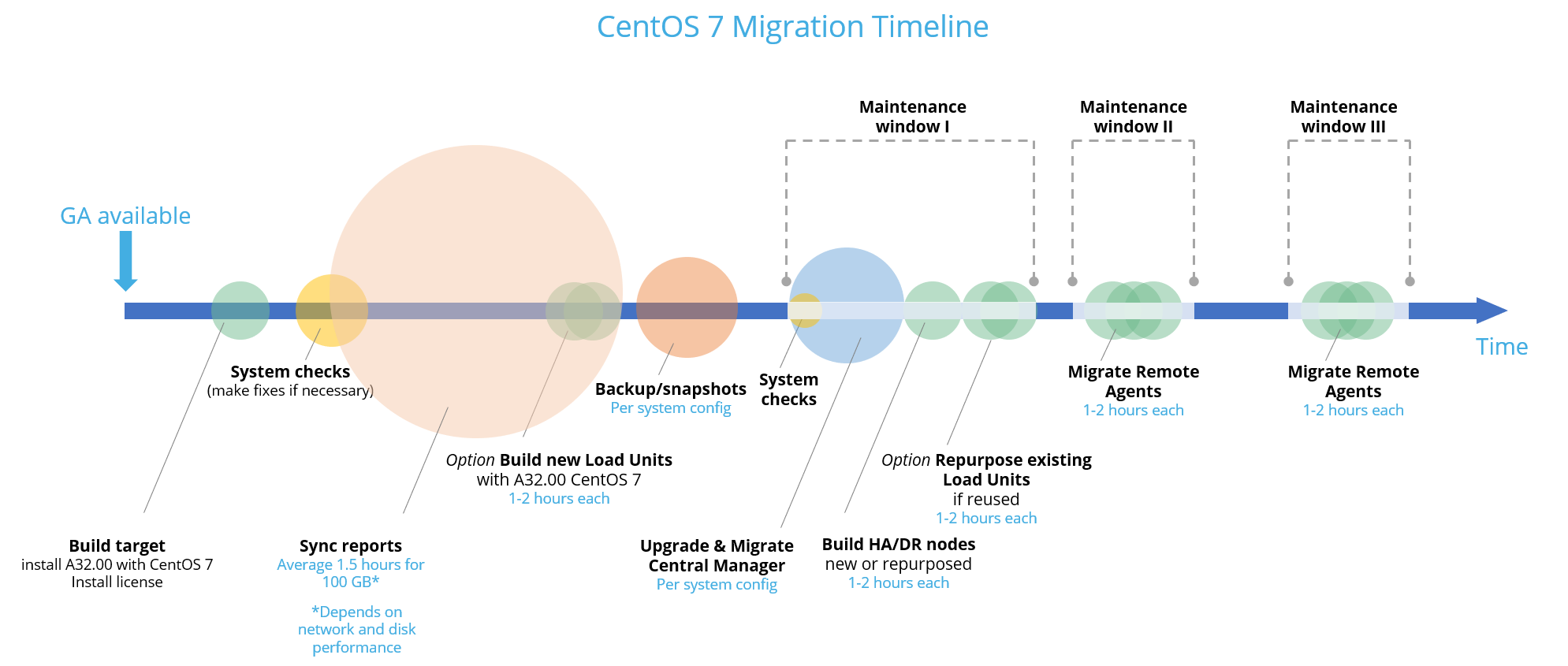
Upgrade/migration steps
This topic describes the upgrade/migration to A32.00 with CentOS 7, based on your system topology.
Make sure you have reviewed the following topics related to the CentOS 7 migration before doing the steps in this topic:
- CentOS 7 Migration Checklist on the Portal.
- Upgrade/migration prerequisites
- CentOS 7 migration target
- Migration target license
If you run into any problems during the migration, see Upgrade/migration troubleshooting.
Procedures for upgrade/migration
Note: Traffic logs that are sent to ASMS during the upgrade procedure may be discarded.
These instructions describe how to upgrade/migrate your system to A32.00 with CentOS 7 based on your system topology. For more details about supported deployments see Supported deployments per architecture structure
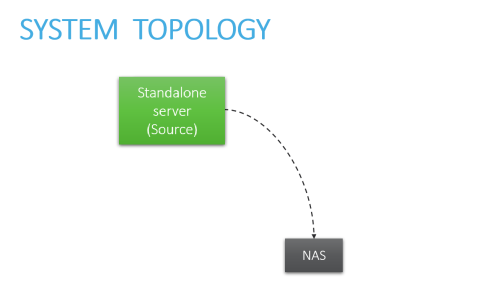
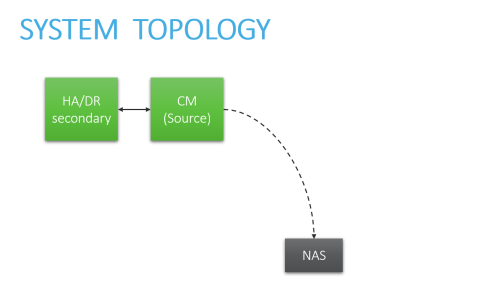
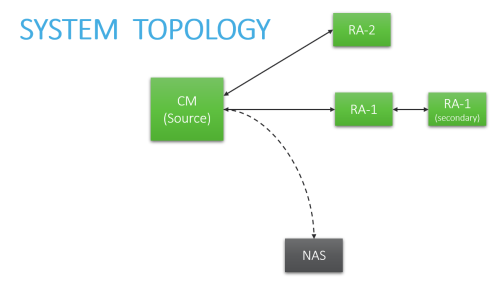
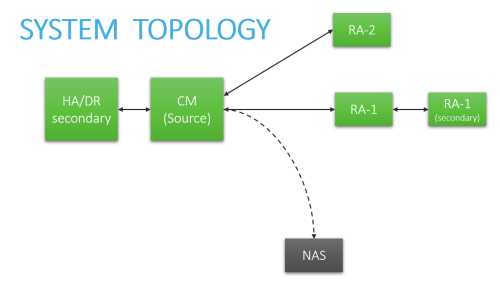
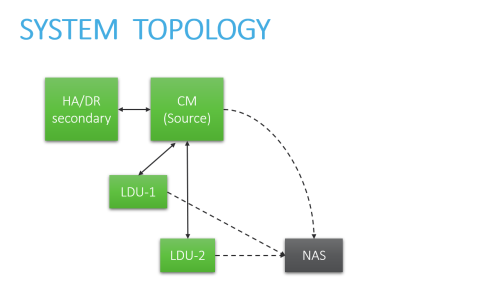
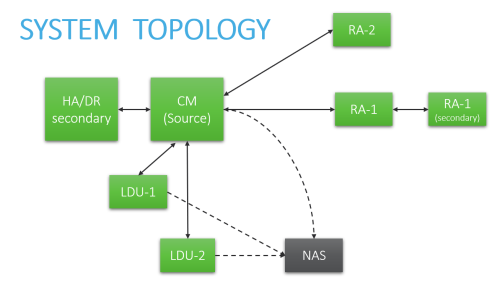
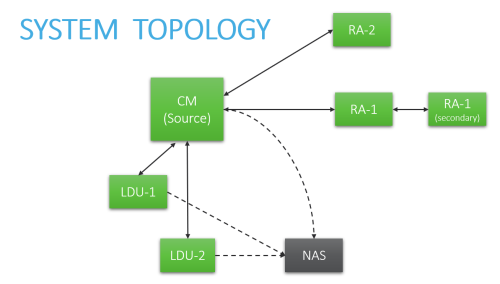
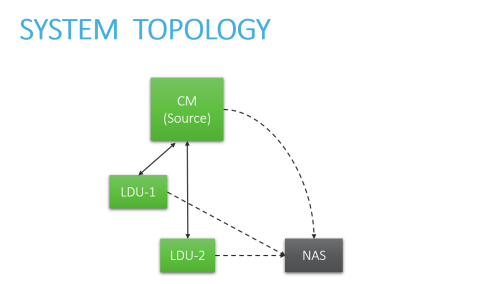
For specific instructions, click the boxes below to select the elements that make up your system architecture:
For a Native Linux Standalone server, follow procedures in Upgrade/migrate to A32.00 from a Native Linux server.
|
CM - Central Manager server HA - High Availability cluster DR - Disaster Recovery cluster RA - Geographic Distribution (Remote Agent) LDU - Load Distribution Unit NAS - External Storage |
Standalone Server
-
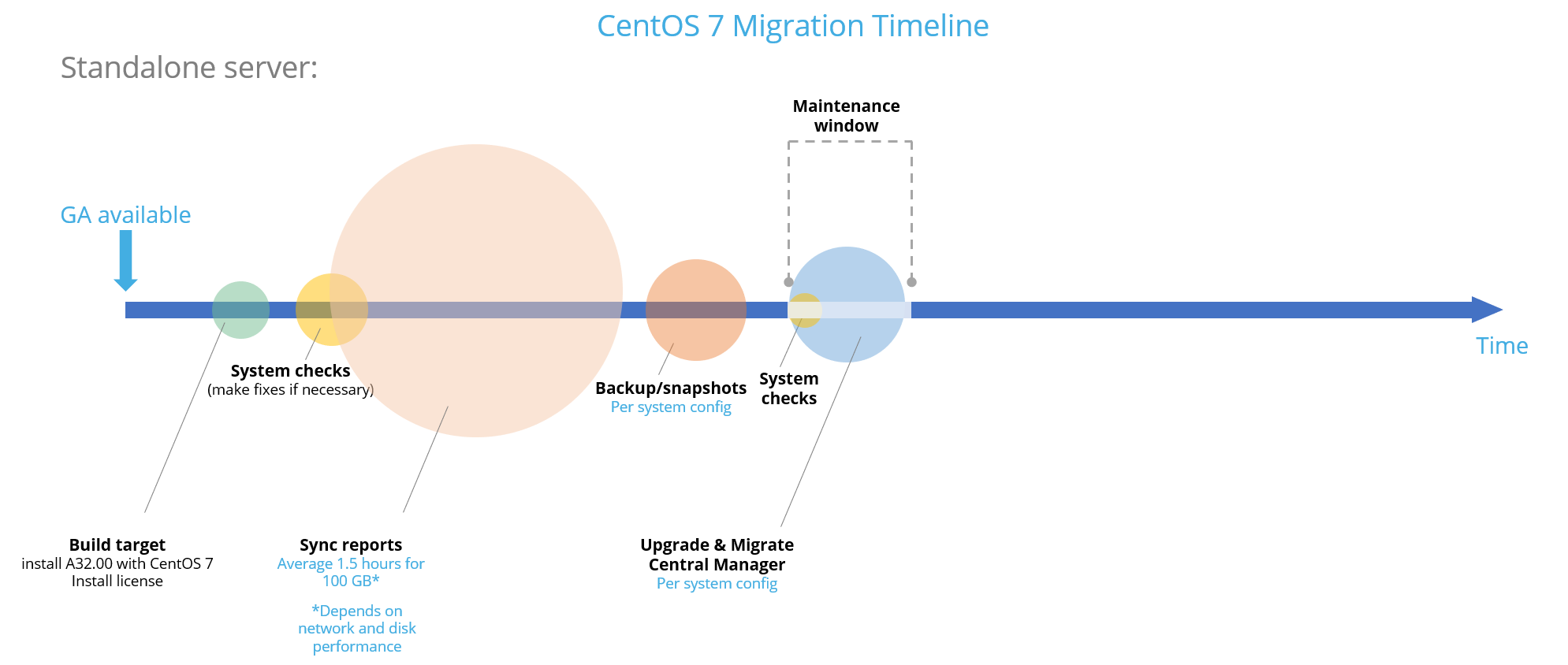
 Build your migration target
Build your migration target
Do the following:
- Choose your target type. See Choose your migration target appliance type.
-
Build the target machine according to target system requirements. See Migration target system requirements.
Important: Do not perform any hardening procedures that are not mentioned in Migration target system requirements. Doing so at this point may cause the migration to fail. For steps you can take once your system is successfully running A32.00, see ASMS system security.
-
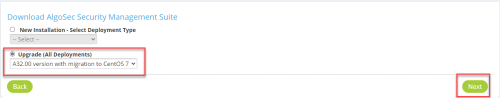
Download upgrade packages from the Portal (Downloads > Software > AlgoSecSecurity Management Suite):
-
Select Upgrade (All Deployments) and specify A32.00 version with migration to CentOS 7.
-
Click Next. The Upgrade to ASMS A32.00 with Migration to CentOS 7 page appears.
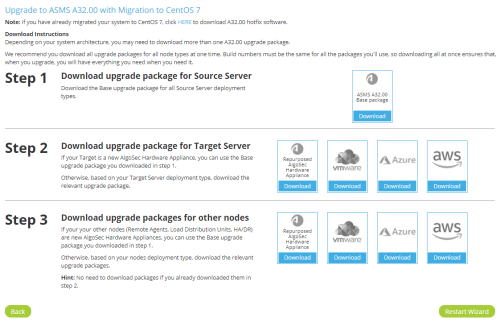
-
Follow steps to download all upgrade packages for all node types at one time. Build numbers must be the same for all the packages you'll use, so downloading all at once ensures that, when you upgrade, you will have everything you need when you need it.
Tip: Save all packages to a secure location. You will need them later.
-
Step 1: Download upgrade package for Source Server: Click to download the ASMS A32.00 base package.
Note: If you have FIPS deployment, click I need the FIPS version. For more details, see Upgrade/migration steps.
Click Download Selected.
Note: The upgrade package consists of four build files:
- fireflow-3200.0.0-bbb.x86_64.run
- fa-3200.0.0-bbb.x86_64.run
For non-FIPS:
- algosec-appliance-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-3200.0.0-aaa-el7.x86_64.run
For FIPS:
- algosec-appliance-fips-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run
- Step 2: Download upgrade package for Target Server: If your Target is a new AlgoSec Hardware Appliance, you can use the base upgrade package you downloaded in step 1.
Otherwise, based on your Target Server deployment type, download the relevant upgrade package.
-
Step 3: Download upgrade packages for other nodes: If your your other nodes (Remote Agents, Load Distribution Units, HA/DR) are new AlgoSec Hardware Appliances, you can use the base upgrade package you downloaded in step 1.
Otherwise, depending on your nodes deployment type, download the relevant upgrade packages.
Tip: No need to download packages again if you already downloaded them in step 2.
-
-
-
On Target
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
For new appliances, follow steps in Deploy standalone appliances (not necessary for repurposed appliances).
-
For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
- Install the valid ASMS migration license on the target machine. See Migration target license . For instructions to install the license, see ASMS licensing.
- Verify the required ports are opened between source and target machine. See Required port connections. (In particular see the far right column, Central Manager (or Standalone Server) Migration).
-
Disable any NAT configuration between source and target machines.
-
 Run system checks
Run system checks
Do the following:
On Source
-
Perform source environment checks on the source server:
-
Check that required ASMS services are running. Go to the algosec_conf menu and enter option 17 Check services status. For details, see Test ASMS processes.
Note: Even if some services are not running, the upgrade process asks you confirm whether you would like to continue. We recommend contacting AlgoSec customer support to start these services before continuing.
- Last upgrade status must be successful.
- Last upgrade status must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
-
Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
- Last upgrade status, including remote nodes (RA/LDU), must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
-
- Verify that all system nodes are at same date and time. Nodes can be in different time zones, but they have to be at the same time relative to UTC.
- If you are not currently using FireFlow, make sure that the value of the FireFlow_configured parameter in /home/afa/.fa/config is set to no.
FireFlow_configured=no - For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
-
Follow the steps in the AlgoPedia article: CentOS 7 Migration | Preventive action for A32.0.
-
If you have configured an SSL certificate pass phrase, remove it now (recommended) or copy the ssl pass phrase file.
 To remove the SSL certificate pass phrase:
To remove the SSL certificate pass phrase:
-
On the CLI, enter the following script to print the pass phrase:
echo -e '#!/bin/bash\necho "Enter your SSL Passphrase here"' > /etc/httpd/conf.d/sslpassphrase
chmod 700 /etc/httpd/conf.d/sslpassphrase
-
Configure httpd to use the pass phrase script by entering the following:
-
Edit /etc/httpd/conf.d/ssl.conf
-
Change text from:
SSLPassPhraseDialog builtin
to:
SSLPassPhraseDialog exec:/etc/httpd/conf.d/sslpassphrase
-
-
Check that httpd starts without having to enter a pass phrase. Enter:
/etc/init.d/httpd restart
 To copy the SSL certificate pass phrase:
To copy the SSL certificate pass phrase:
-
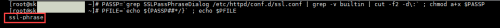
Log in to Source as root user.
-
Run the commands:
PASSP=`grep SSLPassPhraseDialog /etc/httpd/conf.d/ssl.conf | grep -v builtin | cut -f2 -d\:` ; chmod a+x $PASSP
PFILE=`echo ${PASSP##*/}` ; echo $PFILE -
Copy the CLI printed output.
In this case, ssl-phrase.
-
Run the following replacing the actual Target IP:
rsync -rtu $PASSP <TARGET_IP>:/usr/libexec/ -
Enter password when prompted.
-
-
Log in to Target as root user and enter the following replacing the string you copied from step 1:
\cp -rpv /usr/libexec/httpd-ssl-pass-dialog{,.BACKUP_COPY} ; \cp -rpv /usr/libexec/<Copied string from step 1> /usr/libexec/httpd-ssl-pass-dialogFor Example, if the copied string is <ssl-phrase>, the command will be:
\cp -rpv /usr/libexec/ssl-phrase/usr/libexec/httpd-ssl-pass-dialog
-
Verification: Restart httpd and ensure httpd starts up:
service httpd restart
-
-
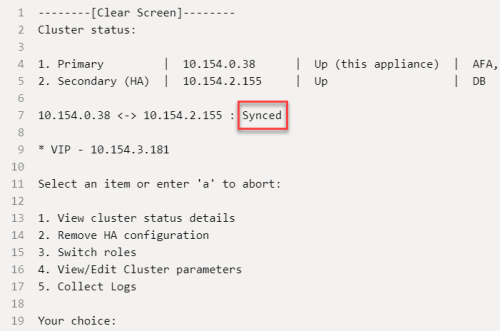
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Close ⌃-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
-
 Run system prerequisites
Run system prerequisites
Use the first part of the upgrade routine to run the automatic system prerequisites checks even without upgrading. If any of the prerequisite checks fail, the system notifies which items need to be fixed. After getting the system checks prerequisites results, stop before upgrading by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).Do the following:
On Source
-
Verify that your system is ready for the upgrade by running automatic prerequisite checks. checks are finisheddo not continue to the upgrade process:
-
Copy the upgrade package you saved previously to the /root/AlgoSec_Upgrade/ directory on the source server.
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
Note: Java11 is installed the first time option 8 is run to support prerequisite checks. It will not affect any of the existing system functionality.
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run on both the source and migration target machine. When the checks are finished manually stop the process by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).If you continue to upgrade at this point, you risk losing data.
-
-
-
 Fix prerequisite check errors
Fix prerequisite check errors
Since the next step, Sync Reports from Source to Target, is done on the Target, you can fix on the source the issues that are discovered during the automatic system prerequisites while the next step is running: Except for the following two issues. If either or both is discovered, fix them before proceeding:
Remote node [nodeIP], must be a standalone machine
For instructions, see Remote node must be a standalone machine The following ports are filtered from
local node to node x.x.x.x: [Port#, Port#]The following ports are filtered from
node x.x.x.x to local node: [Port#, Port#]For instructions, see Firewall(s) detected filtering traffic between source (x.x.x.x) and target (x.x.x.x) for ports: [ports] For instructions to resolve automatic system prerequisites checks issues, see Resolve automatic system prerequisites checks issues.
Close ⌃ -
 Sync reports from source to target
Sync reports from source to target
Important: If you use a NAS in your system, there is no need to sync reports since your reports data is already offloaded from the source.
Reports are pulled from the source to the target. The process runs in the background, which will save you a lot of downtime during the upgrade & migration process. If during the interim after time you sync reports and before you upgrade & migrate enough new reports accumulate, you may be prompted by the system to sync again before you upgrade & migrate.
Note: You can only sync reports from one server. If after syncing reports you choose to change to another server, only data from the most recent server synced will be retained.
Note: During the sync, to abort press Ctrl+D on the keyboard. Enter algosec_conf to return to the algosec_conf menu.
Do the following:
On Target
-
Make sure that the amount of free space of the /data/ folder on the new target machine is larger than the sum of the folder sizes of the following on the source:
-
/home/afa/algosec/firewalls/
-
/home/afa/algosec/groups/
-
/home/afa/algosec/matrices/
-
-
Go to the algosec_conf menu, and enter option 16 - Migrate ASMS units. Enter option 3 -Sync reports from peer node.
-
Enter the IP address and root password of the peer (the source) node. Reports are synced to the target node.
Warning: Make sure you enter the correct IP for the peer (source) node, otherwise data can be overwritten.
-
-
 Backup your system
Backup your system
Do the following:
On Source
-
Upgrade your system to the latest build version of either A30.00 or A30.10, if you haven't already. Download latest build from the AlgoSec portal.
Note: The latest build is the build available on the portal on the day you migrate. You may need to restore your system with this build so save the files to a secure location.
-
Perform a backup of the source server to an external or network drive. Make sure to include traffic logs and reports in your backup. See Backup and restore.
Additionally, for virtual and host-based appliances, when available, power-off the machine and take a snapshot (cold snapshot).
Important: If your system has a cluster (CM and/or RA), the order in which you take the snapshots is critical.
 To find out the order in which you should take the snapshots:
To find out the order in which you should take the snapshots:
-
Go the algosec_conf menu and run option 13 HA/DR Setup.
-
Run option 1. View cluster status details.
-
Take a snapshot first from the node without DB in its row and then take a snapshot of the node with DB in its row.
For example, if the results are:
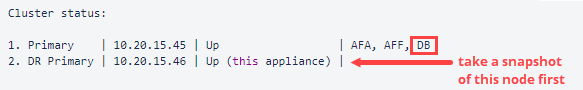
Node 2. DR Primary doesn’t show the DB in its row, so its snapshot should be taken first.
Node 1. Primary shows the DB in its row, so its snapshot should be taken second.
-
-
-
 Migrate source server
Migrate source server
Note about custom scripts:
- Before migrating to CentOS 7, all custom scripts should be located in the folder: /usr/share/fireflow/local/etc/site/lib/. If you have customizations placed in other folders, move them to /usr/share/fireflow/local/etc/site/lib/. After the migration, you can return them to their previous locations.
- If you use custom scripts and other code that was especially made for you by the AlgoSec PS team, we recommend that you check with the AlgoSec before migrating your data to ensure that the codes migrate successfully.
Note: Communicate to your organization that users must not connect to the AlgoSec user interface during the upgrade process. Connections to the AlgoSec user interface during the data migration process can cause migration failure.
Note: During the migration process, any scheduled backup will be disabled.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Do the following:
On Source
-
If you are not already connected to the ASMS Administration interface (algosec_conf), connect now. For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
-
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run including a check for new reports that may need to be synced. If all checks pass, continue by entering y.
Note: If errors are discovered or new reports need to be synced, we recommend you stop now and follow the suggested steps. When done, run the upgrade again by going to the algosec_conf menu, and run option 8 - upgrade software.
- If you backed up your system in the previous section, press y to continue. Otherwise, we recommend you stop now and backup your system.
- When the upgrade finishes successfully, data migration from server to target starts automatically.
- During data migration, if there are any errors, the process will stop. See Upgrade/migration troubleshooting for instructions to address issues that occur. Once resolved, re-initiate the data migration process. From algosec_conf menu, run option 8 - upgrade software.
-
-
When data migration is completed, based on the appliance type of your source and target servers (see CentOS 7 migration target), either:
Repurpose the source machine for use as official machine Repurpose the source machine. See Install ASMS from a bootable flash drive.
Migrate data from target back to the repurposed machine. On the source, from the algosec_conf menu, run option 16 - Migrate ASMS units.
Target replaces source as official machine Use target as official machine and dispose of old source machine. -
If you have repurposed your source machine:On SourceFor FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
If your target replaces the source as the official machine: On target (Recommended) Reassign the IP address of the replaced source node to the target (the new Central Manager). See Basic configurations.
-
-
For a local syslog (on the Central Manager) and your target replaces the source as official machine:
-
On Target Reassign the IP address of the replaced source node to the new Central Manager (the target node). See Basic configurations.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new CM (or standalone server) IP.
-
- For external syslog-ng server:
- Upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
 If you use AutoDiscovery, migrate it now:
If you use AutoDiscovery, migrate it now:
Note: ASMS A32.00 connects to the new A32.00 AutoDiscovery server only, not to the old one.
The new A32.00 AutoDiscovery server is hosted on a dedicated Remote Agent node in ASMS. See AutoDiscovery server system requirements.
Do the following:
- Deploy the new AutoDiscovery server. See Deploy the AutoDiscovery server.
- Migrate data from the old AutoDiscovery server to the new one. See Migrate data from earlier AutoDiscovery versions.
- Redirect your Netflow target to the new AutoDiscovery server IP.
- Redefine user roles as part of ASMS. See Configure AutoDiscovery.
- Upgrade remote AutoDiscovery sensors, if exist, to A32.00. See Upgrade remote AutoDiscovery sensors.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the step in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the step in After the upgrade/migration.
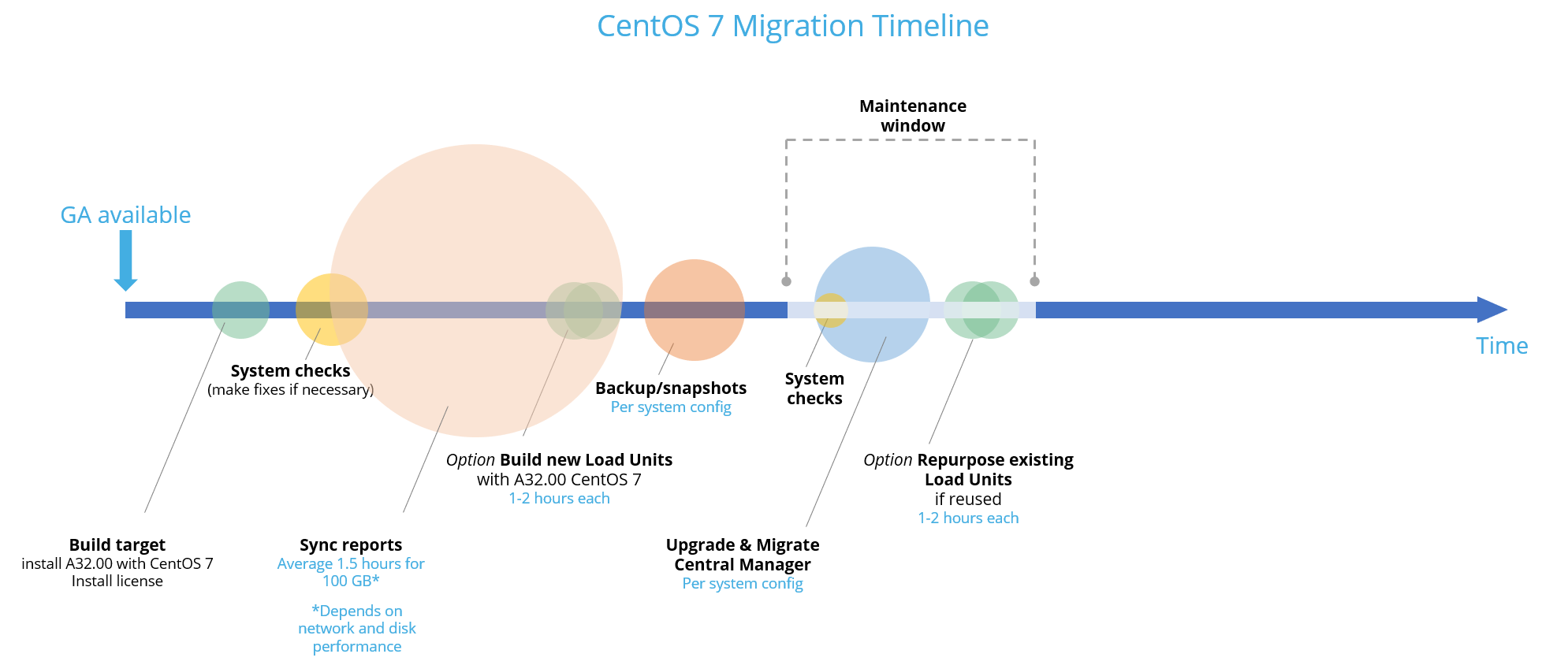
Central Manager with High Availability / Disaster Recovery cluster
-
 Build your migration target
Build your migration target
Do the following:
- Choose your target type. See Choose your migration target appliance type.
-
Build the target machine according to target system requirements. See Migration target system requirements.
Important: Do not perform any hardening procedures that are not mentioned in Migration target system requirements. Doing so at this point may cause the migration to fail. For steps you can take once your system is successfully running A32.00, see ASMS system security.
-
Download upgrade packages from the Portal (Downloads > Software > AlgoSecSecurity Management Suite):
-
Select Upgrade (All Deployments) and specify A32.00 version with migration to CentOS 7.
-
Click Next. The Upgrade to ASMS A32.00 with Migration to CentOS 7 page appears.
-
Follow steps to download all upgrade packages for all node types at one time. Build numbers must be the same for all the packages you'll use, so downloading all at once ensures that, when you upgrade, you will have everything you need when you need it.
Tip: Save all packages to a secure location. You will need them later.
-
Step 1: Download upgrade package for Source Server: Click to download the ASMS A32.00 base package.
Note: If you have FIPS deployment, click I need the FIPS version. For more details, see Upgrade/migration steps.
Click Download Selected.
Note: The upgrade package consists of four build files:
- fireflow-3200.0.0-bbb.x86_64.run
- fa-3200.0.0-bbb.x86_64.run
For non-FIPS:
- algosec-appliance-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-3200.0.0-aaa-el7.x86_64.run
For FIPS:
- algosec-appliance-fips-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run
- Step 2: Download upgrade package for Target Server: If your Target is a new AlgoSec Hardware Appliance, you can use the base upgrade package you downloaded in step 1.
Otherwise, based on your Target Server deployment type, download the relevant upgrade package.
-
Step 3: Download upgrade packages for other nodes: If your your other nodes (Remote Agents, Load Distribution Units, HA/DR) are new AlgoSec Hardware Appliances, you can use the base upgrade package you downloaded in step 1.
Otherwise, depending on your nodes deployment type, download the relevant upgrade packages.
Tip: No need to download packages again if you already downloaded them in step 2.
-
-
-
On Target
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
For new appliances, follow steps in Deploy standalone appliances (not necessary for repurposed appliances).
-
For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
- Install the valid ASMS migration license on the target machine. See Migration target license . For instructions to install the license, see ASMS licensing.
- Verify the required ports are opened between source and target machine. See Required port connections. (In particular see the far right column, Central Manager (or Standalone Server) Migration).
-
Disable any NAT configuration between source and target machines.
-
 Run system checks
Run system checks
Do the following:
On Source
-
Perform source environment checks on the source server:
-
Check that required ASMS services are running. Go to the algosec_conf menu and enter option 17 Check services status. For details, see Test ASMS processes.
Note: Even if some services are not running, the upgrade process asks you confirm whether you would like to continue. We recommend contacting AlgoSec customer support to start these services before continuing.
- Last upgrade status must be successful.
- Last upgrade status must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
-
Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
- Last upgrade status, including remote nodes (RA/LDU), must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
-
- Verify that all system nodes are at same date and time. Nodes can be in different time zones, but they have to be at the same time relative to UTC.
- If you are not currently using FireFlow, make sure that the value of the FireFlow_configured parameter in /home/afa/.fa/config is set to no.
FireFlow_configured=no - For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
-
Follow the steps in the AlgoPedia article: CentOS 7 Migration | Preventive action for A32.0.
-
If you have configured an SSL certificate pass phrase, remove it now (recommended) or copy the ssl pass phrase file.
 To remove the SSL certificate pass phrase:
To remove the SSL certificate pass phrase:
-
On the CLI, enter the following script to print the pass phrase:
echo -e '#!/bin/bash\necho "Enter your SSL Passphrase here"' > /etc/httpd/conf.d/sslpassphrase
chmod 700 /etc/httpd/conf.d/sslpassphrase
-
Configure httpd to use the pass phrase script by entering the following:
-
Edit /etc/httpd/conf.d/ssl.conf
-
Change text from:
SSLPassPhraseDialog builtin
to:
SSLPassPhraseDialog exec:/etc/httpd/conf.d/sslpassphrase
-
-
Check that httpd starts without having to enter a pass phrase. Enter:
/etc/init.d/httpd restart
 To copy the SSL certificate pass phrase:
To copy the SSL certificate pass phrase:
-
Log in to Source as root user.
-
Run the commands:
PASSP=`grep SSLPassPhraseDialog /etc/httpd/conf.d/ssl.conf | grep -v builtin | cut -f2 -d\:` ; chmod a+x $PASSP
PFILE=`echo ${PASSP##*/}` ; echo $PFILE -
Copy the CLI printed output.
In this case, ssl-phrase.
-
Run the following replacing the actual Target IP:
rsync -rtu $PASSP <TARGET_IP>:/usr/libexec/ -
Enter password when prompted.
-
-
Log in to Target as root user and enter the following replacing the string you copied from step 1:
\cp -rpv /usr/libexec/httpd-ssl-pass-dialog{,.BACKUP_COPY} ; \cp -rpv /usr/libexec/<Copied string from step 1> /usr/libexec/httpd-ssl-pass-dialogFor Example, if the copied string is <ssl-phrase>, the command will be:
\cp -rpv /usr/libexec/ssl-phrase/usr/libexec/httpd-ssl-pass-dialog
-
Verification: Restart httpd and ensure httpd starts up:
service httpd restart
-
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Close ⌃-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
-
 Run system prerequisites
Run system prerequisites
Use the first part of the upgrade routine to run the automatic system prerequisites checks even without upgrading. If any of the prerequisite checks fail, the system notifies which items need to be fixed. After getting the system checks prerequisites results, stop before upgrading by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).Do the following:
On Source
-
Verify that your system is ready for the upgrade by running automatic prerequisite checks. checks are finisheddo not continue to the upgrade process:
-
Copy the upgrade package you saved previously to the /root/AlgoSec_Upgrade/ directory on the source server.
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
Note: Java11 is installed the first time option 8 is run to support prerequisite checks. It will not affect any of the existing system functionality.
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run on both the source and migration target machine. When the checks are finished manually stop the process by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).If you continue to upgrade at this point, you risk losing data.
-
-
-
 Fix prerequisite check errors
Fix prerequisite check errors
Since the next step, Sync Reports from Source to Target, is done on the Target, you can fix on the source the issues that are discovered during the automatic system prerequisites while the next step is running: Except for the following two issues. If either or both is discovered, fix them before proceeding:
Remote node [nodeIP], must be a standalone machine
For instructions, see Remote node must be a standalone machine The following ports are filtered from
local node to node x.x.x.x: [Port#, Port#]The following ports are filtered from
node x.x.x.x to local node: [Port#, Port#]For instructions, see Firewall(s) detected filtering traffic between source (x.x.x.x) and target (x.x.x.x) for ports: [ports] For instructions to resolve automatic system prerequisites checks issues, see Resolve automatic system prerequisites checks issues.
Close ⌃ -
 Sync reports from source to target
Sync reports from source to target
Important: If you use a NAS in your system, there is no need to sync reports since your reports data is already offloaded from the source.
Reports are pulled from the source to the target. The process runs in the background, which will save you a lot of downtime during the upgrade & migration process. If during the interim after time you sync reports and before you upgrade & migrate enough new reports accumulate, you may be prompted by the system to sync again before you upgrade & migrate.
Note: You can only sync reports from one server. If after syncing reports you choose to change to another server, only data from the most recent server synced will be retained.
Note: During the sync, to abort press Ctrl+D on the keyboard. Enter algosec_conf to return to the algosec_conf menu.
Do the following:
On Target
-
Make sure that the amount of free space of the /data/ folder on the new target machine is larger than the sum of the folder sizes of the following on the source:
-
/home/afa/algosec/firewalls/
-
/home/afa/algosec/groups/
-
/home/afa/algosec/matrices/
-
-
Go to the algosec_conf menu, and enter option 16 - Migrate ASMS units. Enter option 3 -Sync reports from peer node.
-
Enter the IP address and root password of the peer (the source) node. Reports are synced to the target node.
Warning: Make sure you enter the correct IP for the peer (source) node, otherwise data can be overwritten.
-
-
 Backup your system
Backup your system
Do the following:
On Source
-
Upgrade your system to the latest build version of either A30.00 or A30.10, if you haven't already. Download latest build from the AlgoSec portal.
Note: The latest build is the build available on the portal on the day you migrate. You may need to restore your system with this build so save the files to a secure location.
-
Perform a backup of the source server to an external or network drive. Make sure to include traffic logs and reports in your backup. See Backup and restore.
Additionally, for virtual and host-based appliances, when available, power-off the machine and take a snapshot (cold snapshot).
Important: If your system has a cluster (CM and/or RA), the order in which you take the snapshots is critical.
 To find out the order in which you should take the snapshots:
To find out the order in which you should take the snapshots:
-
Go the algosec_conf menu and run option 13 HA/DR Setup.
-
Run option 1. View cluster status details.
-
Take a snapshot first from the node without DB in its row and then take a snapshot of the node with DB in its row.
For example, if the results are:

Node 2. DR Primary doesn’t show the DB in its row, so its snapshot should be taken first.
Node 1. Primary shows the DB in its row, so its snapshot should be taken second.
-
-
-
 Migrate source server
Migrate source server
Note about custom scripts:
- Before migrating to CentOS 7, all custom scripts should be located in the folder: /usr/share/fireflow/local/etc/site/lib/. If you have customizations placed in other folders, move them to /usr/share/fireflow/local/etc/site/lib/. After the migration, you can return them to their previous locations.
- If you use custom scripts and other code that was especially made for you by the AlgoSec PS team, we recommend that you check with the AlgoSec before migrating your data to ensure that the codes migrate successfully.
Note: Communicate to your organization that users must not connect to the AlgoSec user interface during the upgrade process. Connections to the AlgoSec user interface during the data migration process can cause migration failure.
Note: During the migration process, any scheduled backup will be disabled.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Do the following:
On Source
-
If you are not already connected to the ASMS Administration interface (algosec_conf), connect now. For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
-
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run including a check for new reports that may need to be synced. If all checks pass, continue by entering y.
Note: If errors are discovered or new reports need to be synced, we recommend you stop now and follow the suggested steps. When done, run the upgrade again by going to the algosec_conf menu, and run option 8 - upgrade software.
- If you backed up your system in the previous section, press y to continue. Otherwise, we recommend you stop now and backup your system.
- When the upgrade finishes successfully, data migration from server to target starts automatically.
- During data migration, if there are any errors, the process will stop. See Upgrade/migration troubleshooting for instructions to address issues that occur. Once resolved, re-initiate the data migration process. From algosec_conf menu, run option 8 - upgrade software.
-
-
When data migration is completed, based on the appliance type of your source and target servers (see CentOS 7 migration target), either:
Repurpose the source machine for use as official machine Repurpose the source machine. See Install ASMS from a bootable flash drive.
Migrate data from target back to the repurposed machine. On the source, from the algosec_conf menu, run option 16 - Migrate ASMS units.
Target replaces source as official machine Use target as official machine and dispose of old source machine. -
If you have repurposed your source machine:On SourceFor FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
If your target replaces the source as the official machine: On target (Recommended) Reassign the IP address of the replaced source node to the target (the new Central Manager). See Basic configurations.
-
-
For a local syslog (on the Central Manager) and your target replaces the source as official machine:
-
On Target Reassign the IP address of the replaced source node to the new Central Manager (the target node). See Basic configurations.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new CM (or standalone server) IP.
-
- For external syslog-ng server:
- Upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
 If you use AutoDiscovery, migrate it now:
If you use AutoDiscovery, migrate it now:
Note: ASMS A32.00 connects to the new A32.00 AutoDiscovery server only, not to the old one.
The new A32.00 AutoDiscovery server is hosted on a dedicated Remote Agent node in ASMS. See AutoDiscovery server system requirements.
Do the following:
- Deploy the new AutoDiscovery server. See Deploy the AutoDiscovery server.
- Migrate data from the old AutoDiscovery server to the new one. See Migrate data from earlier AutoDiscovery versions.
- Redirect your Netflow target to the new AutoDiscovery server IP.
- Redefine user roles as part of ASMS. See Configure AutoDiscovery.
- Upgrade remote AutoDiscovery sensors, if exist, to A32.00. See Upgrade remote AutoDiscovery sensors.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the step in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the step in After the upgrade/migration.
-
 Migrate HA/DR cluster
Migrate HA/DR cluster
-
Install A32.00 with CentOS7 on a new or repurposed HA/DR machine:
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
- For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
- Build cluster with HA/DR machine. See Deploy clusters and distributed architectures.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
-
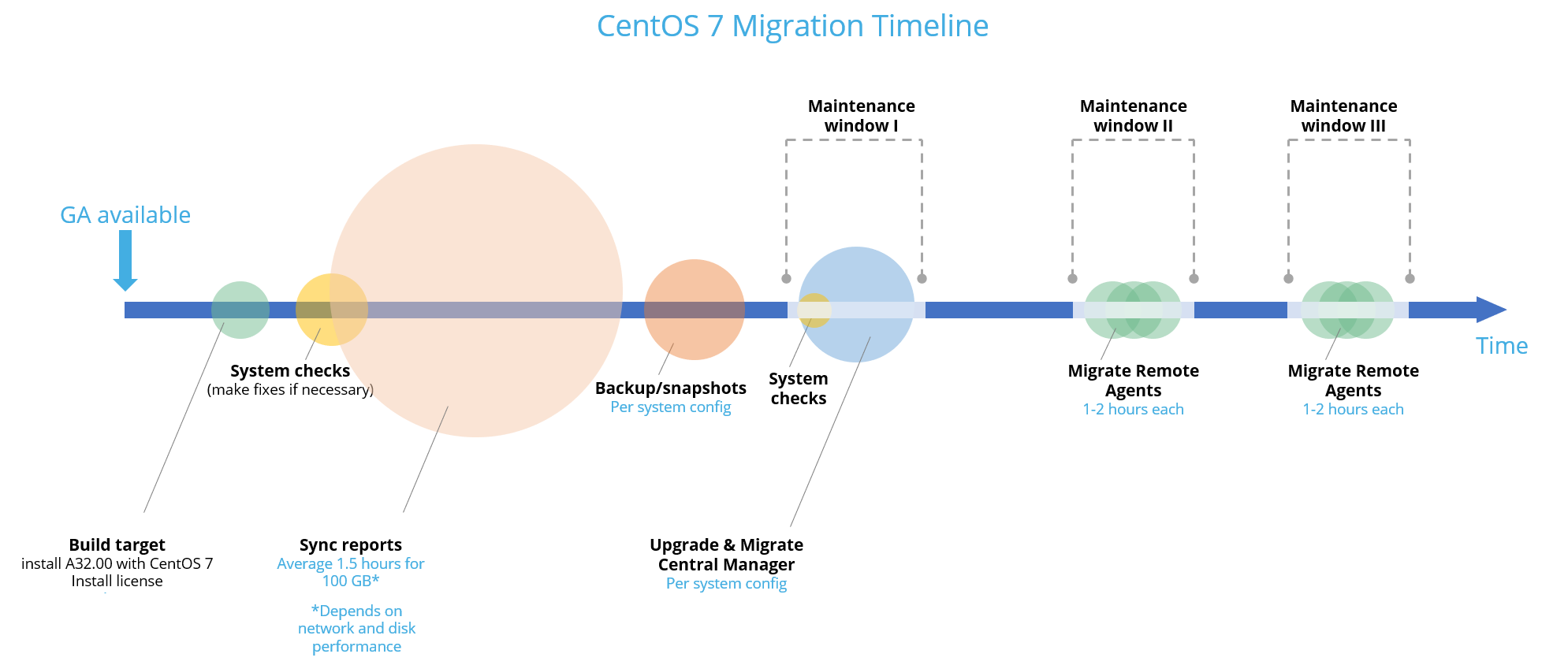
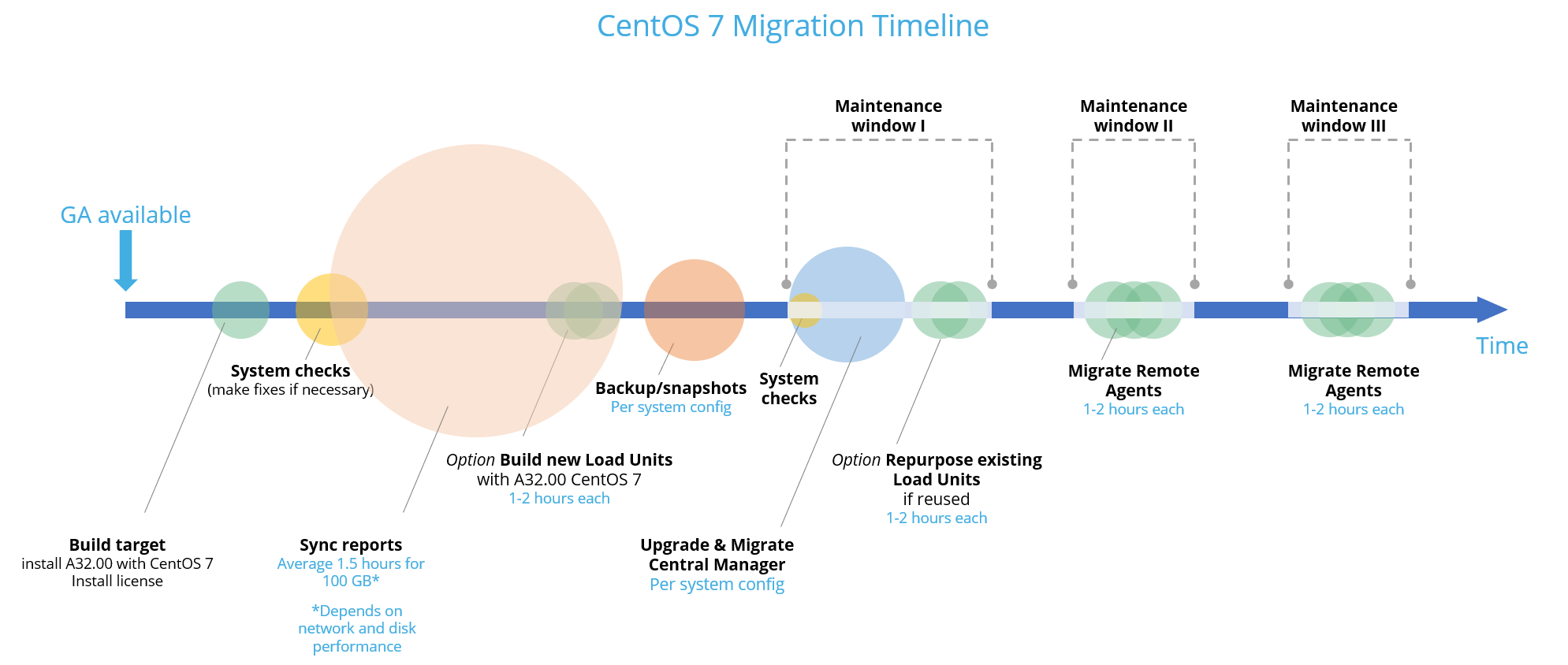
Central Manager + Geographic distributions (Remote Agents)
-
 Build your migration target
Build your migration target
Do the following:
- Choose your target type. See Choose your migration target appliance type.
-
Build the target machine according to target system requirements. See Migration target system requirements.
Important: Do not perform any hardening procedures that are not mentioned in Migration target system requirements. Doing so at this point may cause the migration to fail. For steps you can take once your system is successfully running A32.00, see ASMS system security.
-
Download upgrade packages from the Portal (Downloads > Software > AlgoSecSecurity Management Suite):
-
Select Upgrade (All Deployments) and specify A32.00 version with migration to CentOS 7.
-
Click Next. The Upgrade to ASMS A32.00 with Migration to CentOS 7 page appears.
-
Follow steps to download all upgrade packages for all node types at one time. Build numbers must be the same for all the packages you'll use, so downloading all at once ensures that, when you upgrade, you will have everything you need when you need it.
Tip: Save all packages to a secure location. You will need them later.
-
Step 1: Download upgrade package for Source Server: Click to download the ASMS A32.00 base package.
Note: If you have FIPS deployment, click I need the FIPS version. For more details, see Upgrade/migration steps.
Click Download Selected.
Note: The upgrade package consists of four build files:
- fireflow-3200.0.0-bbb.x86_64.run
- fa-3200.0.0-bbb.x86_64.run
For non-FIPS:
- algosec-appliance-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-3200.0.0-aaa-el7.x86_64.run
For FIPS:
- algosec-appliance-fips-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run
- Step 2: Download upgrade package for Target Server: If your Target is a new AlgoSec Hardware Appliance, you can use the base upgrade package you downloaded in step 1.
Otherwise, based on your Target Server deployment type, download the relevant upgrade package.
-
Step 3: Download upgrade packages for other nodes: If your your other nodes (Remote Agents, Load Distribution Units, HA/DR) are new AlgoSec Hardware Appliances, you can use the base upgrade package you downloaded in step 1.
Otherwise, depending on your nodes deployment type, download the relevant upgrade packages.
Tip: No need to download packages again if you already downloaded them in step 2.
-
-
-
On Target
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
For new appliances, follow steps in Deploy standalone appliances (not necessary for repurposed appliances).
-
For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
- Install the valid ASMS migration license on the target machine. See Migration target license . For instructions to install the license, see ASMS licensing.
- Verify the required ports are opened between source and target machine. See Required port connections. (In particular see the far right column, Central Manager (or Standalone Server) Migration).
-
Disable any NAT configuration between source and target machines.
-
 Run system checks
Run system checks
Do the following:
On Source
-
Perform source environment checks on the source server:
-
Check that required ASMS services are running. Go to the algosec_conf menu and enter option 17 Check services status. For details, see Test ASMS processes.
Note: Even if some services are not running, the upgrade process asks you confirm whether you would like to continue. We recommend contacting AlgoSec customer support to start these services before continuing.
- Last upgrade status must be successful.
- Last upgrade status must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
-
Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
- Last upgrade status, including remote nodes (RA/LDU), must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
-
- Verify that all system nodes are at same date and time. Nodes can be in different time zones, but they have to be at the same time relative to UTC.
- If you are not currently using FireFlow, make sure that the value of the FireFlow_configured parameter in /home/afa/.fa/config is set to no.
FireFlow_configured=no - For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
-
Follow the steps in the AlgoPedia article: CentOS 7 Migration | Preventive action for A32.0.
-
If you have configured an SSL certificate pass phrase, remove it now (recommended) or copy the ssl pass phrase file.
 To remove the SSL certificate pass phrase:
To remove the SSL certificate pass phrase:
-
On the CLI, enter the following script to print the pass phrase:
echo -e '#!/bin/bash\necho "Enter your SSL Passphrase here"' > /etc/httpd/conf.d/sslpassphrase
chmod 700 /etc/httpd/conf.d/sslpassphrase
-
Configure httpd to use the pass phrase script by entering the following:
-
Edit /etc/httpd/conf.d/ssl.conf
-
Change text from:
SSLPassPhraseDialog builtin
to:
SSLPassPhraseDialog exec:/etc/httpd/conf.d/sslpassphrase
-
-
Check that httpd starts without having to enter a pass phrase. Enter:
/etc/init.d/httpd restart
 To copy the SSL certificate pass phrase:
To copy the SSL certificate pass phrase:
-
Log in to Source as root user.
-
Run the commands:
PASSP=`grep SSLPassPhraseDialog /etc/httpd/conf.d/ssl.conf | grep -v builtin | cut -f2 -d\:` ; chmod a+x $PASSP
PFILE=`echo ${PASSP##*/}` ; echo $PFILE -
Copy the CLI printed output.
In this case, ssl-phrase.
-
Run the following replacing the actual Target IP:
rsync -rtu $PASSP <TARGET_IP>:/usr/libexec/ -
Enter password when prompted.
-
-
Log in to Target as root user and enter the following replacing the string you copied from step 1:
\cp -rpv /usr/libexec/httpd-ssl-pass-dialog{,.BACKUP_COPY} ; \cp -rpv /usr/libexec/<Copied string from step 1> /usr/libexec/httpd-ssl-pass-dialogFor Example, if the copied string is <ssl-phrase>, the command will be:
\cp -rpv /usr/libexec/ssl-phrase/usr/libexec/httpd-ssl-pass-dialog
-
Verification: Restart httpd and ensure httpd starts up:
service httpd restart
-
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Close ⌃-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
-
 Run system prerequisites
Run system prerequisites
Use the first part of the upgrade routine to run the automatic system prerequisites checks even without upgrading. If any of the prerequisite checks fail, the system notifies which items need to be fixed. After getting the system checks prerequisites results, stop before upgrading by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).Do the following:
On Source
-
Verify that your system is ready for the upgrade by running automatic prerequisite checks. checks are finisheddo not continue to the upgrade process:
-
Copy the upgrade package you saved previously to the /root/AlgoSec_Upgrade/ directory on the source server.
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
Note: Java11 is installed the first time option 8 is run to support prerequisite checks. It will not affect any of the existing system functionality.
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run on both the source and migration target machine. When the checks are finished manually stop the process by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).If you continue to upgrade at this point, you risk losing data.
-
-
-
 Fix prerequisite check errors
Fix prerequisite check errors
Since the next step, Sync Reports from Source to Target, is done on the Target, you can fix on the source the issues that are discovered during the automatic system prerequisites while the next step is running: Except for the following two issues. If either or both is discovered, fix them before proceeding:
Remote node [nodeIP], must be a standalone machine
For instructions, see Remote node must be a standalone machine The following ports are filtered from
local node to node x.x.x.x: [Port#, Port#]The following ports are filtered from
node x.x.x.x to local node: [Port#, Port#]For instructions, see Firewall(s) detected filtering traffic between source (x.x.x.x) and target (x.x.x.x) for ports: [ports] For instructions to resolve automatic system prerequisites checks issues, see Resolve automatic system prerequisites checks issues.
Close ⌃ -
 Sync reports from source to target
Sync reports from source to target
Important: If you use a NAS in your system, there is no need to sync reports since your reports data is already offloaded from the source.
Reports are pulled from the source to the target. The process runs in the background, which will save you a lot of downtime during the upgrade & migration process. If during the interim after time you sync reports and before you upgrade & migrate enough new reports accumulate, you may be prompted by the system to sync again before you upgrade & migrate.
Note: You can only sync reports from one server. If after syncing reports you choose to change to another server, only data from the most recent server synced will be retained.
Note: During the sync, to abort press Ctrl+D on the keyboard. Enter algosec_conf to return to the algosec_conf menu.
Do the following:
On Target
-
Make sure that the amount of free space of the /data/ folder on the new target machine is larger than the sum of the folder sizes of the following on the source:
-
/home/afa/algosec/firewalls/
-
/home/afa/algosec/groups/
-
/home/afa/algosec/matrices/
-
-
Go to the algosec_conf menu, and enter option 16 - Migrate ASMS units. Enter option 3 -Sync reports from peer node.
-
Enter the IP address and root password of the peer (the source) node. Reports are synced to the target node.
Warning: Make sure you enter the correct IP for the peer (source) node, otherwise data can be overwritten.
-
-
 Backup your system
Backup your system
Do the following:
On Source
-
Upgrade your system to the latest build version of either A30.00 or A30.10, if you haven't already. Download latest build from the AlgoSec portal.
Note: The latest build is the build available on the portal on the day you migrate. You may need to restore your system with this build so save the files to a secure location.
-
Perform a backup of the source server to an external or network drive. Make sure to include traffic logs and reports in your backup. See Backup and restore.
Additionally, for virtual and host-based appliances, when available, power-off the machine and take a snapshot (cold snapshot).
Important: If your system has a cluster (CM and/or RA), the order in which you take the snapshots is critical.
 To find out the order in which you should take the snapshots:
To find out the order in which you should take the snapshots:
-
Go the algosec_conf menu and run option 13 HA/DR Setup.
-
Run option 1. View cluster status details.
-
Take a snapshot first from the node without DB in its row and then take a snapshot of the node with DB in its row.
For example, if the results are:

Node 2. DR Primary doesn’t show the DB in its row, so its snapshot should be taken first.
Node 1. Primary shows the DB in its row, so its snapshot should be taken second.
-
-
-
 Migrate source server
Migrate source server
Note about custom scripts:
- Before migrating to CentOS 7, all custom scripts should be located in the folder: /usr/share/fireflow/local/etc/site/lib/. If you have customizations placed in other folders, move them to /usr/share/fireflow/local/etc/site/lib/. After the migration, you can return them to their previous locations.
- If you use custom scripts and other code that was especially made for you by the AlgoSec PS team, we recommend that you check with the AlgoSec before migrating your data to ensure that the codes migrate successfully.
Note: Communicate to your organization that users must not connect to the AlgoSec user interface during the upgrade process. Connections to the AlgoSec user interface during the data migration process can cause migration failure.
Note: During the migration process, any scheduled backup will be disabled.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Do the following:
On Source
-
If you are not already connected to the ASMS Administration interface (algosec_conf), connect now. For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
-
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run including a check for new reports that may need to be synced. If all checks pass, continue by entering y.
Note: If errors are discovered or new reports need to be synced, we recommend you stop now and follow the suggested steps. When done, run the upgrade again by going to the algosec_conf menu, and run option 8 - upgrade software.
- If you backed up your system in the previous section, press y to continue. Otherwise, we recommend you stop now and backup your system.
- When the upgrade finishes successfully, data migration from server to target starts automatically.
- During data migration, if there are any errors, the process will stop. See Upgrade/migration troubleshooting for instructions to address issues that occur. Once resolved, re-initiate the data migration process. From algosec_conf menu, run option 8 - upgrade software.
-
-
When data migration is completed, based on the appliance type of your source and target servers (see CentOS 7 migration target), either:
Repurpose the source machine for use as official machine Repurpose the source machine. See Install ASMS from a bootable flash drive.
Migrate data from target back to the repurposed machine. On the source, from the algosec_conf menu, run option 16 - Migrate ASMS units.
Target replaces source as official machine Use target as official machine and dispose of old source machine. -
If you have repurposed your source machine:On SourceFor FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
If your target replaces the source as the official machine: On target (Recommended) Reassign the IP address of the replaced source node to the target (the new Central Manager). See Basic configurations.
-
-
For a local syslog (on the Central Manager) and your target replaces the source as official machine:
-
On Target Reassign the IP address of the replaced source node to the new Central Manager (the target node). See Basic configurations.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new CM (or standalone server) IP.
-
- For external syslog-ng server:
- Upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
 If you use AutoDiscovery, migrate it now:
If you use AutoDiscovery, migrate it now:
Note: ASMS A32.00 connects to the new A32.00 AutoDiscovery server only, not to the old one.
The new A32.00 AutoDiscovery server is hosted on a dedicated Remote Agent node in ASMS. See AutoDiscovery server system requirements.
Do the following:
- Deploy the new AutoDiscovery server. See Deploy the AutoDiscovery server.
- Migrate data from the old AutoDiscovery server to the new one. See Migrate data from earlier AutoDiscovery versions.
- Redirect your Netflow target to the new AutoDiscovery server IP.
- Redefine user roles as part of ASMS. See Configure AutoDiscovery.
- Upgrade remote AutoDiscovery sensors, if exist, to A32.00. See Upgrade remote AutoDiscovery sensors.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the step in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the step in After the upgrade/migration.
-
 Migrate remote agents
Migrate remote agents
As part of the upgrade process of the Central Manager, Remote Agents are automatically upgraded to A32.00 while still running CentOS 6. These Remote Agents have full functionality when working with a Central Manager running A32.00 CentOS 7. This allows you the flexibility to migrate your Remote Agents to CentOS 7 now or in future maintenance windows.
Important: In a system using CentOS 7, in order to perform upgrades, all your system's nodes must be in CentOS 7.
Note: Remote Agents in High Availability clusters require licenses.
If you have a machine available to replace the Remote Agent that meets CentOS 7 migration requirements (see Upgrade/migration prerequisites), fresh install or repurpose the machine to A32.00 with CentOS 7 and then relocate devices to it from the old Remote Agent. If not, relocate the devices to the Central Manager, then repurpose or replace the existing Remote Agent and finally relocate the devices back from the Central Manager.
Do the following:
-
Relocate devices:
 If you have an available machine that meets CentOS 7 migration requirements to use as a new Remote Agent:
If you have an available machine that meets CentOS 7 migration requirements to use as a new Remote Agent:
-
Install A32.00 with CentOS7 on a new Remote Agent:
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
Add the new Remote Agent to the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- In the Architecture tab, add the new Remote Agent to the Geographic Distribution list.
-
Make sure to open the necessary port between each device and the remote Agent, depending on the protocol being used to connect to the device. See Manage devices.
-
Relocate devices from the original Remote Agent to the new one. See Relocate devices.
Note: Devices that are currently being monitored or analyzed will be skipped. Wait several minutes for the current monitor/analysis process to end and run the relocation process again.
Important: If the relocation fails and you receive the message:
Some devices were defined with an incorrect syslog host.
-
Delete the original Remote Agent from the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Delete the Remote Agent from the Geographic Distribution list.
- If your Remote Agent is in a cluster, rebuild cluster with a new or repurposed machine running A32.00 with CentOS 7. Both the RA and the RA cluster node require a license installed. See Build a cluster.
 If relocating devices to the Central Manager:
If relocating devices to the Central Manager:
-
Relocate devices to the Central Manager. See Relocate devices. The devices are grouped automatically and relocated to the Central Manager.
Note: Devices that are currently being monitored or analyzed will be skipped. Wait several minutes for the current monitor/analysis process to end and run the relocation process again.
-
Delete the original Remote Agent from the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Delete the Remote Agent from the Geographic Distribution list.
-
Install A32.00 with CentOS7 on new or repurposed Remote Agent:
Important: Make sure you have completed step a successfully before you do this step or data loss may occur.
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
Add the new Remote Agent to the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Add the Remote Agent to the Geographic Distribution list.
-
Make sure to open the necessary port between each device and the remote Agent, depending on the protocol being used to connect to the device. See Manage devices.
- Relocate devices group from CM to the new Remote Agent running CentOS 7. See Relocate devices.
Important: If the relocation fails and you receive the message:
Some devices were defined with an incorrect syslog host.
- If your Remote Agent is in a cluster, rebuild cluster with a new or repurposed machine running A32.00 with CentOS 7. Both the RA and the RA cluster node require a license installed. See Build a cluster.
-
-
Make sure that the date on the Remote Agent is set correctly. Machines can be in different time zones but they have to be at the same time relative to UTC.
Tip: We recommended you use an NTP server (use algosec_conf option 2 on the Remote Agent).
-
-
For a local syslog (on the new Remote Agent):
- Reassign the IP address of the original Remote Agent to the new Remote Agent to which devices have been relocated. Make sure you have deleted the original Remote Agent from the system before reassigning its IP to the target node. See To change the IP address of a Remote Agent.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new Remote Agent IP.
- For external syslog, upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
Central Manager with High Availability / Disaster Recovery cluster and Geographic distributions (Remote Agents)
-
 Build your migration target
Build your migration target
Do the following:
- Choose your target type. See Choose your migration target appliance type.
-
Build the target machine according to target system requirements. See Migration target system requirements.
Important: Do not perform any hardening procedures that are not mentioned in Migration target system requirements. Doing so at this point may cause the migration to fail. For steps you can take once your system is successfully running A32.00, see ASMS system security.
-
Download upgrade packages from the Portal (Downloads > Software > AlgoSecSecurity Management Suite):
-
Select Upgrade (All Deployments) and specify A32.00 version with migration to CentOS 7.
-
Click Next. The Upgrade to ASMS A32.00 with Migration to CentOS 7 page appears.
-
Follow steps to download all upgrade packages for all node types at one time. Build numbers must be the same for all the packages you'll use, so downloading all at once ensures that, when you upgrade, you will have everything you need when you need it.
Tip: Save all packages to a secure location. You will need them later.
-
Step 1: Download upgrade package for Source Server: Click to download the ASMS A32.00 base package.
Note: If you have FIPS deployment, click I need the FIPS version. For more details, see Upgrade/migration steps.
Click Download Selected.
Note: The upgrade package consists of four build files:
- fireflow-3200.0.0-bbb.x86_64.run
- fa-3200.0.0-bbb.x86_64.run
For non-FIPS:
- algosec-appliance-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-3200.0.0-aaa-el7.x86_64.run
For FIPS:
- algosec-appliance-fips-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run
- Step 2: Download upgrade package for Target Server: If your Target is a new AlgoSec Hardware Appliance, you can use the base upgrade package you downloaded in step 1.
Otherwise, based on your Target Server deployment type, download the relevant upgrade package.
-
Step 3: Download upgrade packages for other nodes: If your your other nodes (Remote Agents, Load Distribution Units, HA/DR) are new AlgoSec Hardware Appliances, you can use the base upgrade package you downloaded in step 1.
Otherwise, depending on your nodes deployment type, download the relevant upgrade packages.
Tip: No need to download packages again if you already downloaded them in step 2.
-
-
-
On Target
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
For new appliances, follow steps in Deploy standalone appliances (not necessary for repurposed appliances).
-
For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
- Install the valid ASMS migration license on the target machine. See Migration target license . For instructions to install the license, see ASMS licensing.
- Verify the required ports are opened between source and target machine. See Required port connections. (In particular see the far right column, Central Manager (or Standalone Server) Migration).
-
Disable any NAT configuration between source and target machines.
-
 Run system checks
Run system checks
Do the following:
On Source
-
Perform source environment checks on the source server:
-
Check that required ASMS services are running. Go to the algosec_conf menu and enter option 17 Check services status. For details, see Test ASMS processes.
Note: Even if some services are not running, the upgrade process asks you confirm whether you would like to continue. We recommend contacting AlgoSec customer support to start these services before continuing.
- Last upgrade status must be successful.
- Last upgrade status must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
-
Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
- Last upgrade status, including remote nodes (RA/LDU), must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
-
- Verify that all system nodes are at same date and time. Nodes can be in different time zones, but they have to be at the same time relative to UTC.
- If you are not currently using FireFlow, make sure that the value of the FireFlow_configured parameter in /home/afa/.fa/config is set to no.
FireFlow_configured=no - For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
-
Follow the steps in the AlgoPedia article: CentOS 7 Migration | Preventive action for A32.0.
-
If you have configured an SSL certificate pass phrase, remove it now (recommended) or copy the ssl pass phrase file.
 To remove the SSL certificate pass phrase:
To remove the SSL certificate pass phrase:
-
On the CLI, enter the following script to print the pass phrase:
echo -e '#!/bin/bash\necho "Enter your SSL Passphrase here"' > /etc/httpd/conf.d/sslpassphrase
chmod 700 /etc/httpd/conf.d/sslpassphrase
-
Configure httpd to use the pass phrase script by entering the following:
-
Edit /etc/httpd/conf.d/ssl.conf
-
Change text from:
SSLPassPhraseDialog builtin
to:
SSLPassPhraseDialog exec:/etc/httpd/conf.d/sslpassphrase
-
-
Check that httpd starts without having to enter a pass phrase. Enter:
/etc/init.d/httpd restart
 To copy the SSL certificate pass phrase:
To copy the SSL certificate pass phrase:
-
Log in to Source as root user.
-
Run the commands:
PASSP=`grep SSLPassPhraseDialog /etc/httpd/conf.d/ssl.conf | grep -v builtin | cut -f2 -d\:` ; chmod a+x $PASSP
PFILE=`echo ${PASSP##*/}` ; echo $PFILE -
Copy the CLI printed output.
In this case, ssl-phrase.
-
Run the following replacing the actual Target IP:
rsync -rtu $PASSP <TARGET_IP>:/usr/libexec/ -
Enter password when prompted.
-
-
Log in to Target as root user and enter the following replacing the string you copied from step 1:
\cp -rpv /usr/libexec/httpd-ssl-pass-dialog{,.BACKUP_COPY} ; \cp -rpv /usr/libexec/<Copied string from step 1> /usr/libexec/httpd-ssl-pass-dialogFor Example, if the copied string is <ssl-phrase>, the command will be:
\cp -rpv /usr/libexec/ssl-phrase/usr/libexec/httpd-ssl-pass-dialog
-
Verification: Restart httpd and ensure httpd starts up:
service httpd restart
-
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Close ⌃-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
-
 Run system prerequisites
Run system prerequisites
Use the first part of the upgrade routine to run the automatic system prerequisites checks even without upgrading. If any of the prerequisite checks fail, the system notifies which items need to be fixed. After getting the system checks prerequisites results, stop before upgrading by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).Do the following:
On Source
-
Verify that your system is ready for the upgrade by running automatic prerequisite checks. checks are finisheddo not continue to the upgrade process:
-
Copy the upgrade package you saved previously to the /root/AlgoSec_Upgrade/ directory on the source server.
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
Note: Java11 is installed the first time option 8 is run to support prerequisite checks. It will not affect any of the existing system functionality.
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run on both the source and migration target machine. When the checks are finished manually stop the process by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).If you continue to upgrade at this point, you risk losing data.
-
-
-
 Fix prerequisite check errors
Fix prerequisite check errors
Since the next step, Sync Reports from Source to Target, is done on the Target, you can fix on the source the issues that are discovered during the automatic system prerequisites while the next step is running: Except for the following two issues. If either or both is discovered, fix them before proceeding:
Remote node [nodeIP], must be a standalone machine
For instructions, see Remote node must be a standalone machine The following ports are filtered from
local node to node x.x.x.x: [Port#, Port#]The following ports are filtered from
node x.x.x.x to local node: [Port#, Port#]For instructions, see Firewall(s) detected filtering traffic between source (x.x.x.x) and target (x.x.x.x) for ports: [ports] For instructions to resolve automatic system prerequisites checks issues, see Resolve automatic system prerequisites checks issues.
Close ⌃ -
 Sync reports from source to target
Sync reports from source to target
Important: If you use a NAS in your system, there is no need to sync reports since your reports data is already offloaded from the source.
Reports are pulled from the source to the target. The process runs in the background, which will save you a lot of downtime during the upgrade & migration process. If during the interim after time you sync reports and before you upgrade & migrate enough new reports accumulate, you may be prompted by the system to sync again before you upgrade & migrate.
Note: You can only sync reports from one server. If after syncing reports you choose to change to another server, only data from the most recent server synced will be retained.
Note: During the sync, to abort press Ctrl+D on the keyboard. Enter algosec_conf to return to the algosec_conf menu.
Do the following:
On Target
-
Make sure that the amount of free space of the /data/ folder on the new target machine is larger than the sum of the folder sizes of the following on the source:
-
/home/afa/algosec/firewalls/
-
/home/afa/algosec/groups/
-
/home/afa/algosec/matrices/
-
-
Go to the algosec_conf menu, and enter option 16 - Migrate ASMS units. Enter option 3 -Sync reports from peer node.
-
Enter the IP address and root password of the peer (the source) node. Reports are synced to the target node.
Warning: Make sure you enter the correct IP for the peer (source) node, otherwise data can be overwritten.
-
-
 Backup your system
Backup your system
Do the following:
On Source
-
Upgrade your system to the latest build version of either A30.00 or A30.10, if you haven't already. Download latest build from the AlgoSec portal.
Note: The latest build is the build available on the portal on the day you migrate. You may need to restore your system with this build so save the files to a secure location.
-
Perform a backup of the source server to an external or network drive. Make sure to include traffic logs and reports in your backup. See Backup and restore.
Additionally, for virtual and host-based appliances, when available, power-off the machine and take a snapshot (cold snapshot).
Important: If your system has a cluster (CM and/or RA), the order in which you take the snapshots is critical.
 To find out the order in which you should take the snapshots:
To find out the order in which you should take the snapshots:
-
Go the algosec_conf menu and run option 13 HA/DR Setup.
-
Run option 1. View cluster status details.
-
Take a snapshot first from the node without DB in its row and then take a snapshot of the node with DB in its row.
For example, if the results are:

Node 2. DR Primary doesn’t show the DB in its row, so its snapshot should be taken first.
Node 1. Primary shows the DB in its row, so its snapshot should be taken second.
-
-
-
 Migrate source server
Migrate source server
Note about custom scripts:
- Before migrating to CentOS 7, all custom scripts should be located in the folder: /usr/share/fireflow/local/etc/site/lib/. If you have customizations placed in other folders, move them to /usr/share/fireflow/local/etc/site/lib/. After the migration, you can return them to their previous locations.
- If you use custom scripts and other code that was especially made for you by the AlgoSec PS team, we recommend that you check with the AlgoSec before migrating your data to ensure that the codes migrate successfully.
Note: Communicate to your organization that users must not connect to the AlgoSec user interface during the upgrade process. Connections to the AlgoSec user interface during the data migration process can cause migration failure.
Note: During the migration process, any scheduled backup will be disabled.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the procedure, clusters are automatically broken after being upgraded to A32.00 with CentOS 6.
Do the following:
On Source
-
If you are not already connected to the ASMS Administration interface (algosec_conf), connect now. For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
-
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run including a check for new reports that may need to be synced. If all checks pass, continue by entering y.
Note: If errors are discovered or new reports need to be synced, we recommend you stop now and follow the suggested steps. When done, run the upgrade again by going to the algosec_conf menu, and run option 8 - upgrade software.
- If you backed up your system in the previous section, press y to continue. Otherwise, we recommend you stop now and backup your system.
- When the upgrade finishes successfully, data migration from server to target starts automatically.
- During data migration, if there are any errors, the process will stop. See Upgrade/migration troubleshooting for instructions to address issues that occur. Once resolved, re-initiate the data migration process. From algosec_conf menu, run option 8 - upgrade software.
-
-
When data migration is completed, based on the appliance type of your source and target servers (see CentOS 7 migration target), either:
Repurpose the source machine for use as official machine Repurpose the source machine. See Install ASMS from a bootable flash drive.
Migrate data from target back to the repurposed machine. On the source, from the algosec_conf menu, run option 16 - Migrate ASMS units.
Target replaces source as official machine Use target as official machine and dispose of old source machine. -
If you have repurposed your source machine:On SourceFor FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
If your target replaces the source as the official machine: On target (Recommended) Reassign the IP address of the replaced source node to the target (the new Central Manager). See Basic configurations.
-
-
For a local syslog (on the Central Manager) and your target replaces the source as official machine:
-
On Target Reassign the IP address of the replaced source node to the new Central Manager (the target node). See Basic configurations.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new CM (or standalone server) IP.
-
- For external syslog-ng server:
- Upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
 If you use AutoDiscovery, migrate it now:
If you use AutoDiscovery, migrate it now:
Note: ASMS A32.00 connects to the new A32.00 AutoDiscovery server only, not to the old one.
The new A32.00 AutoDiscovery server is hosted on a dedicated Remote Agent node in ASMS. See AutoDiscovery server system requirements.
Do the following:
- Deploy the new AutoDiscovery server. See Deploy the AutoDiscovery server.
- Migrate data from the old AutoDiscovery server to the new one. See Migrate data from earlier AutoDiscovery versions.
- Redirect your Netflow target to the new AutoDiscovery server IP.
- Redefine user roles as part of ASMS. See Configure AutoDiscovery.
- Upgrade remote AutoDiscovery sensors, if exist, to A32.00. See Upgrade remote AutoDiscovery sensors.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the step in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the step in After the upgrade/migration.
-
 Migrate HA/DR cluster
Migrate HA/DR cluster
-
Install A32.00 with CentOS7 on a new or repurposed HA/DR machine:
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
- For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
- Build cluster with HA/DR machine. See Deploy clusters and distributed architectures.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
-
-
 Migrate remote agents
Migrate remote agents
As part of the upgrade process of the Central Manager, Remote Agents are automatically upgraded to A32.00 while still running CentOS 6. These Remote Agents have full functionality when working with a Central Manager running A32.00 CentOS 7. This allows you the flexibility to migrate your Remote Agents to CentOS 7 now or in future maintenance windows.
Important: In a system using CentOS 7, in order to perform upgrades, all your system's nodes must be in CentOS 7.
Note: Remote Agents in High Availability clusters require licenses.
If you have a machine available to replace the Remote Agent that meets CentOS 7 migration requirements (see Upgrade/migration prerequisites), fresh install or repurpose the machine to A32.00 with CentOS 7 and then relocate devices to it from the old Remote Agent. If not, relocate the devices to the Central Manager, then repurpose or replace the existing Remote Agent and finally relocate the devices back from the Central Manager.
Do the following:
-
Relocate devices:
 If you have an available machine that meets CentOS 7 migration requirements to use as a new Remote Agent:
If you have an available machine that meets CentOS 7 migration requirements to use as a new Remote Agent:
-
Install A32.00 with CentOS7 on a new Remote Agent:
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
Add the new Remote Agent to the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- In the Architecture tab, add the new Remote Agent to the Geographic Distribution list.
-
Make sure to open the necessary port between each device and the remote Agent, depending on the protocol being used to connect to the device. See Manage devices.
-
Relocate devices from the original Remote Agent to the new one. See Relocate devices.
Note: Devices that are currently being monitored or analyzed will be skipped. Wait several minutes for the current monitor/analysis process to end and run the relocation process again.
Important: If the relocation fails and you receive the message:
Some devices were defined with an incorrect syslog host.
-
Delete the original Remote Agent from the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Delete the Remote Agent from the Geographic Distribution list.
- If your Remote Agent is in a cluster, rebuild cluster with a new or repurposed machine running A32.00 with CentOS 7. Both the RA and the RA cluster node require a license installed. See Build a cluster.
 If relocating devices to the Central Manager:
If relocating devices to the Central Manager:
-
Relocate devices to the Central Manager. See Relocate devices. The devices are grouped automatically and relocated to the Central Manager.
Note: Devices that are currently being monitored or analyzed will be skipped. Wait several minutes for the current monitor/analysis process to end and run the relocation process again.
-
Delete the original Remote Agent from the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Delete the Remote Agent from the Geographic Distribution list.
-
Install A32.00 with CentOS7 on new or repurposed Remote Agent:
Important: Make sure you have completed step a successfully before you do this step or data loss may occur.
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
Add the new Remote Agent to the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Add the Remote Agent to the Geographic Distribution list.
-
Make sure to open the necessary port between each device and the remote Agent, depending on the protocol being used to connect to the device. See Manage devices.
- Relocate devices group from CM to the new Remote Agent running CentOS 7. See Relocate devices.
Important: If the relocation fails and you receive the message:
Some devices were defined with an incorrect syslog host.
- If your Remote Agent is in a cluster, rebuild cluster with a new or repurposed machine running A32.00 with CentOS 7. Both the RA and the RA cluster node require a license installed. See Build a cluster.
-
-
Make sure that the date on the Remote Agent is set correctly. Machines can be in different time zones but they have to be at the same time relative to UTC.
Tip: We recommended you use an NTP server (use algosec_conf option 2 on the Remote Agent).
-
-
For a local syslog (on the new Remote Agent):
- Reassign the IP address of the original Remote Agent to the new Remote Agent to which devices have been relocated. Make sure you have deleted the original Remote Agent from the system before reassigning its IP to the target node. See To change the IP address of a Remote Agent.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new Remote Agent IP.
- For external syslog, upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
Central Manager with High Availability / Disaster Recovery cluster and Load distributions
-
 Build your migration target
Build your migration target
Do the following:
- Choose your target type. See Choose your migration target appliance type.
-
Build the target machine according to target system requirements. See Migration target system requirements.
Important: Do not perform any hardening procedures that are not mentioned in Migration target system requirements. Doing so at this point may cause the migration to fail. For steps you can take once your system is successfully running A32.00, see ASMS system security.
-
Download upgrade packages from the Portal (Downloads > Software > AlgoSecSecurity Management Suite):
-
Select Upgrade (All Deployments) and specify A32.00 version with migration to CentOS 7.
-
Click Next. The Upgrade to ASMS A32.00 with Migration to CentOS 7 page appears.
-
Follow steps to download all upgrade packages for all node types at one time. Build numbers must be the same for all the packages you'll use, so downloading all at once ensures that, when you upgrade, you will have everything you need when you need it.
Tip: Save all packages to a secure location. You will need them later.
-
Step 1: Download upgrade package for Source Server: Click to download the ASMS A32.00 base package.
Note: If you have FIPS deployment, click I need the FIPS version. For more details, see Upgrade/migration steps.
Click Download Selected.
Note: The upgrade package consists of four build files:
- fireflow-3200.0.0-bbb.x86_64.run
- fa-3200.0.0-bbb.x86_64.run
For non-FIPS:
- algosec-appliance-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-3200.0.0-aaa-el7.x86_64.run
For FIPS:
- algosec-appliance-fips-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run
- Step 2: Download upgrade package for Target Server: If your Target is a new AlgoSec Hardware Appliance, you can use the base upgrade package you downloaded in step 1.
Otherwise, based on your Target Server deployment type, download the relevant upgrade package.
-
Step 3: Download upgrade packages for other nodes: If your your other nodes (Remote Agents, Load Distribution Units, HA/DR) are new AlgoSec Hardware Appliances, you can use the base upgrade package you downloaded in step 1.
Otherwise, depending on your nodes deployment type, download the relevant upgrade packages.
Tip: No need to download packages again if you already downloaded them in step 2.
-
-
-
On Target
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
For new appliances, follow steps in Deploy standalone appliances (not necessary for repurposed appliances).
-
For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
- Install the valid ASMS migration license on the target machine. See Migration target license . For instructions to install the license, see ASMS licensing.
- Verify the required ports are opened between source and target machine. See Required port connections. (In particular see the far right column, Central Manager (or Standalone Server) Migration).
-
Disable any NAT configuration between source and target machines.
-
 Run system checks
Run system checks
Do the following:
On Source
-
Perform source environment checks on the source server:
-
Check that required ASMS services are running. Go to the algosec_conf menu and enter option 17 Check services status. For details, see Test ASMS processes.
Note: Even if some services are not running, the upgrade process asks you confirm whether you would like to continue. We recommend contacting AlgoSec customer support to start these services before continuing.
- Last upgrade status must be successful.
- Last upgrade status must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
-
Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
- Last upgrade status, including remote nodes (RA/LDU), must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
-
- Verify that all system nodes are at same date and time. Nodes can be in different time zones, but they have to be at the same time relative to UTC.
- If you are not currently using FireFlow, make sure that the value of the FireFlow_configured parameter in /home/afa/.fa/config is set to no.
FireFlow_configured=no - For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
-
Follow the steps in the AlgoPedia article: CentOS 7 Migration | Preventive action for A32.0.
-
If you have configured an SSL certificate pass phrase, remove it now (recommended) or copy the ssl pass phrase file.
 To remove the SSL certificate pass phrase:
To remove the SSL certificate pass phrase:
-
On the CLI, enter the following script to print the pass phrase:
echo -e '#!/bin/bash\necho "Enter your SSL Passphrase here"' > /etc/httpd/conf.d/sslpassphrase
chmod 700 /etc/httpd/conf.d/sslpassphrase
-
Configure httpd to use the pass phrase script by entering the following:
-
Edit /etc/httpd/conf.d/ssl.conf
-
Change text from:
SSLPassPhraseDialog builtin
to:
SSLPassPhraseDialog exec:/etc/httpd/conf.d/sslpassphrase
-
-
Check that httpd starts without having to enter a pass phrase. Enter:
/etc/init.d/httpd restart
 To copy the SSL certificate pass phrase:
To copy the SSL certificate pass phrase:
-
Log in to Source as root user.
-
Run the commands:
PASSP=`grep SSLPassPhraseDialog /etc/httpd/conf.d/ssl.conf | grep -v builtin | cut -f2 -d\:` ; chmod a+x $PASSP
PFILE=`echo ${PASSP##*/}` ; echo $PFILE -
Copy the CLI printed output.
In this case, ssl-phrase.
-
Run the following replacing the actual Target IP:
rsync -rtu $PASSP <TARGET_IP>:/usr/libexec/ -
Enter password when prompted.
-
-
Log in to Target as root user and enter the following replacing the string you copied from step 1:
\cp -rpv /usr/libexec/httpd-ssl-pass-dialog{,.BACKUP_COPY} ; \cp -rpv /usr/libexec/<Copied string from step 1> /usr/libexec/httpd-ssl-pass-dialogFor Example, if the copied string is <ssl-phrase>, the command will be:
\cp -rpv /usr/libexec/ssl-phrase/usr/libexec/httpd-ssl-pass-dialog
-
Verification: Restart httpd and ensure httpd starts up:
service httpd restart
-
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Close ⌃-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
-
 Run system prerequisites
Run system prerequisites
Use the first part of the upgrade routine to run the automatic system prerequisites checks even without upgrading. If any of the prerequisite checks fail, the system notifies which items need to be fixed. After getting the system checks prerequisites results, stop before upgrading by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).Do the following:
On Source
-
Verify that your system is ready for the upgrade by running automatic prerequisite checks. checks are finisheddo not continue to the upgrade process:
-
Copy the upgrade package you saved previously to the /root/AlgoSec_Upgrade/ directory on the source server.
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
Note: Java11 is installed the first time option 8 is run to support prerequisite checks. It will not affect any of the existing system functionality.
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run on both the source and migration target machine. When the checks are finished manually stop the process by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).If you continue to upgrade at this point, you risk losing data.
-
-
-
 Fix prerequisite check errors
Fix prerequisite check errors
Since the next step, Sync Reports from Source to Target, is done on the Target, you can fix on the source the issues that are discovered during the automatic system prerequisites while the next step is running: Except for the following two issues. If either or both is discovered, fix them before proceeding:
Remote node [nodeIP], must be a standalone machine
For instructions, see Remote node must be a standalone machine The following ports are filtered from
local node to node x.x.x.x: [Port#, Port#]The following ports are filtered from
node x.x.x.x to local node: [Port#, Port#]For instructions, see Firewall(s) detected filtering traffic between source (x.x.x.x) and target (x.x.x.x) for ports: [ports] For instructions to resolve automatic system prerequisites checks issues, see Resolve automatic system prerequisites checks issues.
Close ⌃ -
 Sync reports from source to target
Sync reports from source to target
Important: If you use a NAS in your system, there is no need to sync reports since your reports data is already offloaded from the source.
Reports are pulled from the source to the target. The process runs in the background, which will save you a lot of downtime during the upgrade & migration process. If during the interim after time you sync reports and before you upgrade & migrate enough new reports accumulate, you may be prompted by the system to sync again before you upgrade & migrate.
Note: You can only sync reports from one server. If after syncing reports you choose to change to another server, only data from the most recent server synced will be retained.
Note: During the sync, to abort press Ctrl+D on the keyboard. Enter algosec_conf to return to the algosec_conf menu.
Do the following:
On Target
-
Make sure that the amount of free space of the /data/ folder on the new target machine is larger than the sum of the folder sizes of the following on the source:
-
/home/afa/algosec/firewalls/
-
/home/afa/algosec/groups/
-
/home/afa/algosec/matrices/
-
-
Go to the algosec_conf menu, and enter option 16 - Migrate ASMS units. Enter option 3 -Sync reports from peer node.
-
Enter the IP address and root password of the peer (the source) node. Reports are synced to the target node.
Warning: Make sure you enter the correct IP for the peer (source) node, otherwise data can be overwritten.
-
-
 Backup your system
Backup your system
Do the following:
On Source
-
Upgrade your system to the latest build version of either A30.00 or A30.10, if you haven't already. Download latest build from the AlgoSec portal.
Note: The latest build is the build available on the portal on the day you migrate. You may need to restore your system with this build so save the files to a secure location.
-
Perform a backup of the source server to an external or network drive. Make sure to include traffic logs and reports in your backup. See Backup and restore.
Additionally, for virtual and host-based appliances, when available, power-off the machine and take a snapshot (cold snapshot).
Important: If your system has a cluster (CM and/or RA), the order in which you take the snapshots is critical.
 To find out the order in which you should take the snapshots:
To find out the order in which you should take the snapshots:
-
Go the algosec_conf menu and run option 13 HA/DR Setup.
-
Run option 1. View cluster status details.
-
Take a snapshot first from the node without DB in its row and then take a snapshot of the node with DB in its row.
For example, if the results are:

Node 2. DR Primary doesn’t show the DB in its row, so its snapshot should be taken first.
Node 1. Primary shows the DB in its row, so its snapshot should be taken second.
-
-
-
 Migrate load distribution units
Migrate load distribution units
You can migrate your Load Distribution Units now to easily connect to them the Central Manager after it is migrated; or you can migrate them late and connect them to the Central Manager via the GUI.
Tip: If you choose the migrate your Load Units later, to connect to the new Central Manager see Add or edit Load Units.
-
Install A32.00 with CentOS7 on new or repurposed LDUs. See Supported deployments per architecture structure
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. During the server migration, you will be asked for LDU IPs to easily reconnect later.
-
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
-
 Migrate source to CentOS 7
Migrate source to CentOS 7
Note about custom scripts:
- Before migrating to CentOS 7, all custom scripts should be located in the folder: /usr/share/fireflow/local/etc/site/lib/. If you have customizations placed in other folders, move them to /usr/share/fireflow/local/etc/site/lib/. After the migration, you can return them to their previous locations.
- If you use custom scripts and other code that was especially made for you by the AlgoSec PS team, we recommend that you check with the AlgoSec before migrating your data to ensure that the codes migrate successfully.
Note: Communicate to your organization that users must not connect to the AlgoSec user interface during the migration process. Connections to the AlgoSec user interface during the data migration process can cause migration failure.
Note: During the migration process, any scheduled backup will be disabled.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Do the following:
-
If you are not already connected to the ASMS Administration interface (algosec_conf), connect now. For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
-
- Enter the IP address and root password of the target machine. Press <Enter>.
-
(optional) Provide new LDU IPs at this stage or you can configure them later. (If you changed LDU IPs earlier, you can provide them now and they will be automatically connected at the end of the upgrade/migration process). Otherwise, press <Enter> to skip through the prompts.
-
Prerequisite checks are run including a check for new reports that may need to be synced. If all checks pass, continue by entering y.
Note: If errors are discovered or new reports need to be synced, we recommend you stop now and follow the suggested steps. When done, run the upgrade again by going to the algosec_conf menu, and run option 8 - upgrade software.
- If you backed up your system in the previous section, press y to continue.
- When the upgrade finishes successfully, data migration from server to target starts automatically.
- During data migration, if there are any errors, the process will stop. See Upgrade/migration troubleshooting for instructions to address issues that occur. Once resolved, re-initiate the data migration process. From algosec_conf menu, run option 8 - upgrade software.
-
When data migration is completed, based on the appliance type of your source and target servers (see CentOS 7 migration target), either:
Repurpose the source machine for use as official machine Repurpose the source machine. See Install ASMS from a bootable flash drive.
Migrate data from target back to the repurposed machine. On the source, from the algosec_conf menu, run option 16 - Migrate ASMS units.
Target replaces source as official machine Use target as official machine and dispose of old source machine.
-
-
For a local syslog (on the Central Manager) and your target replaces the source as official machine:
-
On Target Reassign the IP address of the replaced source node to the new Central Manager (the target node). See Basic configurations.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new CM (or standalone server) IP.
-
- For external syslog-ng server:
- Upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
 If you use AutoDiscovery, migrate it now:
If you use AutoDiscovery, migrate it now:
Note: ASMS A32.00 connects to the new A32.00 AutoDiscovery server only, not to the old one.
The new A32.00 AutoDiscovery server is hosted on a dedicated Remote Agent node in ASMS. See AutoDiscovery server system requirements.
Do the following:
- Deploy the new AutoDiscovery server. See Deploy the AutoDiscovery server.
- Migrate data from the old AutoDiscovery server to the new one. See Migrate data from earlier AutoDiscovery versions.
- Redirect your Netflow target to the new AutoDiscovery server IP.
- Redefine user roles as part of ASMS. See Configure AutoDiscovery.
- Upgrade remote AutoDiscovery sensors, if exist, to A32.00. See Upgrade remote AutoDiscovery sensors.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
-
 Migrate HA/DR cluster
Migrate HA/DR cluster
-
Install A32.00 with CentOS7 on a new or repurposed HA/DR machine:
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
- For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
- Build cluster with HA/DR machine. See Deploy clusters and distributed architectures.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
-
Central Manager with High Availability / Disaster Recovery cluster, Geographic distributions (Remote Agents), and Load distributions
-
 Build your migration target
Build your migration target
Do the following:
- Choose your target type. See Choose your migration target appliance type.
-
Build the target machine according to target system requirements. See Migration target system requirements.
Important: Do not perform any hardening procedures that are not mentioned in Migration target system requirements. Doing so at this point may cause the migration to fail. For steps you can take once your system is successfully running A32.00, see ASMS system security.
-
Download upgrade packages from the Portal (Downloads > Software > AlgoSecSecurity Management Suite):
-
Select Upgrade (All Deployments) and specify A32.00 version with migration to CentOS 7.
-
Click Next. The Upgrade to ASMS A32.00 with Migration to CentOS 7 page appears.
-
Follow steps to download all upgrade packages for all node types at one time. Build numbers must be the same for all the packages you'll use, so downloading all at once ensures that, when you upgrade, you will have everything you need when you need it.
Tip: Save all packages to a secure location. You will need them later.
-
Step 1: Download upgrade package for Source Server: Click to download the ASMS A32.00 base package.
Note: If you have FIPS deployment, click I need the FIPS version. For more details, see Upgrade/migration steps.
Click Download Selected.
Note: The upgrade package consists of four build files:
- fireflow-3200.0.0-bbb.x86_64.run
- fa-3200.0.0-bbb.x86_64.run
For non-FIPS:
- algosec-appliance-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-3200.0.0-aaa-el7.x86_64.run
For FIPS:
- algosec-appliance-fips-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run
- Step 2: Download upgrade package for Target Server: If your Target is a new AlgoSec Hardware Appliance, you can use the base upgrade package you downloaded in step 1.
Otherwise, based on your Target Server deployment type, download the relevant upgrade package.
-
Step 3: Download upgrade packages for other nodes: If your your other nodes (Remote Agents, Load Distribution Units, HA/DR) are new AlgoSec Hardware Appliances, you can use the base upgrade package you downloaded in step 1.
Otherwise, depending on your nodes deployment type, download the relevant upgrade packages.
Tip: No need to download packages again if you already downloaded them in step 2.
-
-
-
On Target
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
For new appliances, follow steps in Deploy standalone appliances (not necessary for repurposed appliances).
-
For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
- Install the valid ASMS migration license on the target machine. See Migration target license . For instructions to install the license, see ASMS licensing.
- Verify the required ports are opened between source and target machine. See Required port connections. (In particular see the far right column, Central Manager (or Standalone Server) Migration).
-
Disable any NAT configuration between source and target machines.
-
 Run system checks
Run system checks
Do the following:
On Source
-
Perform source environment checks on the source server:
-
Check that required ASMS services are running. Go to the algosec_conf menu and enter option 17 Check services status. For details, see Test ASMS processes.
Note: Even if some services are not running, the upgrade process asks you confirm whether you would like to continue. We recommend contacting AlgoSec customer support to start these services before continuing.
- Last upgrade status must be successful.
- Last upgrade status must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
-
Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
- Last upgrade status, including remote nodes (RA/LDU), must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
-
- Verify that all system nodes are at same date and time. Nodes can be in different time zones, but they have to be at the same time relative to UTC.
- If you are not currently using FireFlow, make sure that the value of the FireFlow_configured parameter in /home/afa/.fa/config is set to no.
FireFlow_configured=no - For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
-
Follow the steps in the AlgoPedia article: CentOS 7 Migration | Preventive action for A32.0.
-
If you have configured an SSL certificate pass phrase, remove it now (recommended) or copy the ssl pass phrase file.
 To remove the SSL certificate pass phrase:
To remove the SSL certificate pass phrase:
-
On the CLI, enter the following script to print the pass phrase:
echo -e '#!/bin/bash\necho "Enter your SSL Passphrase here"' > /etc/httpd/conf.d/sslpassphrase
chmod 700 /etc/httpd/conf.d/sslpassphrase
-
Configure httpd to use the pass phrase script by entering the following:
-
Edit /etc/httpd/conf.d/ssl.conf
-
Change text from:
SSLPassPhraseDialog builtin
to:
SSLPassPhraseDialog exec:/etc/httpd/conf.d/sslpassphrase
-
-
Check that httpd starts without having to enter a pass phrase. Enter:
/etc/init.d/httpd restart
 To copy the SSL certificate pass phrase:
To copy the SSL certificate pass phrase:
-
Log in to Source as root user.
-
Run the commands:
PASSP=`grep SSLPassPhraseDialog /etc/httpd/conf.d/ssl.conf | grep -v builtin | cut -f2 -d\:` ; chmod a+x $PASSP
PFILE=`echo ${PASSP##*/}` ; echo $PFILE -
Copy the CLI printed output.
In this case, ssl-phrase.
-
Run the following replacing the actual Target IP:
rsync -rtu $PASSP <TARGET_IP>:/usr/libexec/ -
Enter password when prompted.
-
-
Log in to Target as root user and enter the following replacing the string you copied from step 1:
\cp -rpv /usr/libexec/httpd-ssl-pass-dialog{,.BACKUP_COPY} ; \cp -rpv /usr/libexec/<Copied string from step 1> /usr/libexec/httpd-ssl-pass-dialogFor Example, if the copied string is <ssl-phrase>, the command will be:
\cp -rpv /usr/libexec/ssl-phrase/usr/libexec/httpd-ssl-pass-dialog
-
Verification: Restart httpd and ensure httpd starts up:
service httpd restart
-
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Close ⌃-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
-
 Run system prerequisites
Run system prerequisites
Use the first part of the upgrade routine to run the automatic system prerequisites checks even without upgrading. If any of the prerequisite checks fail, the system notifies which items need to be fixed. After getting the system checks prerequisites results, stop before upgrading by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).Do the following:
On Source
-
Verify that your system is ready for the upgrade by running automatic prerequisite checks. checks are finisheddo not continue to the upgrade process:
-
Copy the upgrade package you saved previously to the /root/AlgoSec_Upgrade/ directory on the source server.
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
Note: Java11 is installed the first time option 8 is run to support prerequisite checks. It will not affect any of the existing system functionality.
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run on both the source and migration target machine. When the checks are finished manually stop the process by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).If you continue to upgrade at this point, you risk losing data.
-
-
-
 Fix prerequisite check errors
Fix prerequisite check errors
Since the next step, Sync Reports from Source to Target, is done on the Target, you can fix on the source the issues that are discovered during the automatic system prerequisites while the next step is running: Except for the following two issues. If either or both is discovered, fix them before proceeding:
Remote node [nodeIP], must be a standalone machine
For instructions, see Remote node must be a standalone machine The following ports are filtered from
local node to node x.x.x.x: [Port#, Port#]The following ports are filtered from
node x.x.x.x to local node: [Port#, Port#]For instructions, see Firewall(s) detected filtering traffic between source (x.x.x.x) and target (x.x.x.x) for ports: [ports] For instructions to resolve automatic system prerequisites checks issues, see Resolve automatic system prerequisites checks issues.
Close ⌃ -
 Sync reports from source to target
Sync reports from source to target
Important: If you use a NAS in your system, there is no need to sync reports since your reports data is already offloaded from the source.
Reports are pulled from the source to the target. The process runs in the background, which will save you a lot of downtime during the upgrade & migration process. If during the interim after time you sync reports and before you upgrade & migrate enough new reports accumulate, you may be prompted by the system to sync again before you upgrade & migrate.
Note: You can only sync reports from one server. If after syncing reports you choose to change to another server, only data from the most recent server synced will be retained.
Note: During the sync, to abort press Ctrl+D on the keyboard. Enter algosec_conf to return to the algosec_conf menu.
Do the following:
On Target
-
Make sure that the amount of free space of the /data/ folder on the new target machine is larger than the sum of the folder sizes of the following on the source:
-
/home/afa/algosec/firewalls/
-
/home/afa/algosec/groups/
-
/home/afa/algosec/matrices/
-
-
Go to the algosec_conf menu, and enter option 16 - Migrate ASMS units. Enter option 3 -Sync reports from peer node.
-
Enter the IP address and root password of the peer (the source) node. Reports are synced to the target node.
Warning: Make sure you enter the correct IP for the peer (source) node, otherwise data can be overwritten.
-
-
 Backup your system
Backup your system
Do the following:
On Source
-
Upgrade your system to the latest build version of either A30.00 or A30.10, if you haven't already. Download latest build from the AlgoSec portal.
Note: The latest build is the build available on the portal on the day you migrate. You may need to restore your system with this build so save the files to a secure location.
-
Perform a backup of the source server to an external or network drive. Make sure to include traffic logs and reports in your backup. See Backup and restore.
Additionally, for virtual and host-based appliances, when available, power-off the machine and take a snapshot (cold snapshot).
Important: If your system has a cluster (CM and/or RA), the order in which you take the snapshots is critical.
 To find out the order in which you should take the snapshots:
To find out the order in which you should take the snapshots:
-
Go the algosec_conf menu and run option 13 HA/DR Setup.
-
Run option 1. View cluster status details.
-
Take a snapshot first from the node without DB in its row and then take a snapshot of the node with DB in its row.
For example, if the results are:

Node 2. DR Primary doesn’t show the DB in its row, so its snapshot should be taken first.
Node 1. Primary shows the DB in its row, so its snapshot should be taken second.
-
-
-
 Migrate load distribution units
Migrate load distribution units
You can migrate your Load Distribution Units now to easily connect to them the Central Manager after it is migrated; or you can migrate them late and connect them to the Central Manager via the GUI.
Tip: If you choose the migrate your Load Units later, to connect to the new Central Manager see Add or edit Load Units.
-
Install A32.00 with CentOS7 on new or repurposed LDUs. See Supported deployments per architecture structure
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. During the server migration, you will be asked for LDU IPs to easily reconnect later.
-
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
-
 Migrate source to CentOS 7
Migrate source to CentOS 7
Note about custom scripts:
- Before migrating to CentOS 7, all custom scripts should be located in the folder: /usr/share/fireflow/local/etc/site/lib/. If you have customizations placed in other folders, move them to /usr/share/fireflow/local/etc/site/lib/. After the migration, you can return them to their previous locations.
- If you use custom scripts and other code that was especially made for you by the AlgoSec PS team, we recommend that you check with the AlgoSec before migrating your data to ensure that the codes migrate successfully.
Note: Communicate to your organization that users must not connect to the AlgoSec user interface during the migration process. Connections to the AlgoSec user interface during the data migration process can cause migration failure.
Note: During the migration process, any scheduled backup will be disabled.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Do the following:
-
If you are not already connected to the ASMS Administration interface (algosec_conf), connect now. For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
-
- Enter the IP address and root password of the target machine. Press <Enter>.
-
(optional) Provide new LDU IPs at this stage or you can configure them later. (If you changed LDU IPs earlier, you can provide them now and they will be automatically connected at the end of the upgrade/migration process). Otherwise, press <Enter> to skip through the prompts.
-
Prerequisite checks are run including a check for new reports that may need to be synced. If all checks pass, continue by entering y.
Note: If errors are discovered or new reports need to be synced, we recommend you stop now and follow the suggested steps. When done, run the upgrade again by going to the algosec_conf menu, and run option 8 - upgrade software.
- If you backed up your system in the previous section, press y to continue.
- When the upgrade finishes successfully, data migration from server to target starts automatically.
- During data migration, if there are any errors, the process will stop. See Upgrade/migration troubleshooting for instructions to address issues that occur. Once resolved, re-initiate the data migration process. From algosec_conf menu, run option 8 - upgrade software.
-
When data migration is completed, based on the appliance type of your source and target servers (see CentOS 7 migration target), either:
Repurpose the source machine for use as official machine Repurpose the source machine. See Install ASMS from a bootable flash drive.
Migrate data from target back to the repurposed machine. On the source, from the algosec_conf menu, run option 16 - Migrate ASMS units.
Target replaces source as official machine Use target as official machine and dispose of old source machine.
-
-
For a local syslog (on the Central Manager) and your target replaces the source as official machine:
-
On Target Reassign the IP address of the replaced source node to the new Central Manager (the target node). See Basic configurations.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new CM (or standalone server) IP.
-
- For external syslog-ng server:
- Upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
 If you use AutoDiscovery, migrate it now:
If you use AutoDiscovery, migrate it now:
Note: ASMS A32.00 connects to the new A32.00 AutoDiscovery server only, not to the old one.
The new A32.00 AutoDiscovery server is hosted on a dedicated Remote Agent node in ASMS. See AutoDiscovery server system requirements.
Do the following:
- Deploy the new AutoDiscovery server. See Deploy the AutoDiscovery server.
- Migrate data from the old AutoDiscovery server to the new one. See Migrate data from earlier AutoDiscovery versions.
- Redirect your Netflow target to the new AutoDiscovery server IP.
- Redefine user roles as part of ASMS. See Configure AutoDiscovery.
- Upgrade remote AutoDiscovery sensors, if exist, to A32.00. See Upgrade remote AutoDiscovery sensors.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
-
 Migrate HA/DR cluster
Migrate HA/DR cluster
-
Install A32.00 with CentOS7 on a new or repurposed HA/DR machine:
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
- For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
- Build cluster with HA/DR machine. See Deploy clusters and distributed architectures.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
-
-
 Migrate remote agents
Migrate remote agents
As part of the upgrade process of the Central Manager, Remote Agents are automatically upgraded to A32.00 while still running CentOS 6. These Remote Agents have full functionality when working with a Central Manager running A32.00 CentOS 7. This allows you the flexibility to migrate your Remote Agents to CentOS 7 now or in future maintenance windows.
Important: In a system using CentOS 7, in order to perform upgrades, all your system's nodes must be in CentOS 7.
Note: Remote Agents in High Availability clusters require licenses.
If you have a machine available to replace the Remote Agent that meets CentOS 7 migration requirements (see Upgrade/migration prerequisites), fresh install or repurpose the machine to A32.00 with CentOS 7 and then relocate devices to it from the old Remote Agent. If not, relocate the devices to the Central Manager, then repurpose or replace the existing Remote Agent and finally relocate the devices back from the Central Manager.
Do the following:
-
Relocate devices:
 If you have an available machine that meets CentOS 7 migration requirements to use as a new Remote Agent:
If you have an available machine that meets CentOS 7 migration requirements to use as a new Remote Agent:
-
Install A32.00 with CentOS7 on a new Remote Agent:
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
Add the new Remote Agent to the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- In the Architecture tab, add the new Remote Agent to the Geographic Distribution list.
-
Make sure to open the necessary port between each device and the remote Agent, depending on the protocol being used to connect to the device. See Manage devices.
-
Relocate devices from the original Remote Agent to the new one. See Relocate devices.
Note: Devices that are currently being monitored or analyzed will be skipped. Wait several minutes for the current monitor/analysis process to end and run the relocation process again.
Important: If the relocation fails and you receive the message:
Some devices were defined with an incorrect syslog host.
-
Delete the original Remote Agent from the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Delete the Remote Agent from the Geographic Distribution list.
- If your Remote Agent is in a cluster, rebuild cluster with a new or repurposed machine running A32.00 with CentOS 7. Both the RA and the RA cluster node require a license installed. See Build a cluster.
 If relocating devices to the Central Manager:
If relocating devices to the Central Manager:
-
Relocate devices to the Central Manager. See Relocate devices. The devices are grouped automatically and relocated to the Central Manager.
Note: Devices that are currently being monitored or analyzed will be skipped. Wait several minutes for the current monitor/analysis process to end and run the relocation process again.
-
Delete the original Remote Agent from the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Delete the Remote Agent from the Geographic Distribution list.
-
Install A32.00 with CentOS7 on new or repurposed Remote Agent:
Important: Make sure you have completed step a successfully before you do this step or data loss may occur.
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
Add the new Remote Agent to the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Add the Remote Agent to the Geographic Distribution list.
-
Make sure to open the necessary port between each device and the remote Agent, depending on the protocol being used to connect to the device. See Manage devices.
- Relocate devices group from CM to the new Remote Agent running CentOS 7. See Relocate devices.
Important: If the relocation fails and you receive the message:
Some devices were defined with an incorrect syslog host.
- If your Remote Agent is in a cluster, rebuild cluster with a new or repurposed machine running A32.00 with CentOS 7. Both the RA and the RA cluster node require a license installed. See Build a cluster.
-
-
Make sure that the date on the Remote Agent is set correctly. Machines can be in different time zones but they have to be at the same time relative to UTC.
Tip: We recommended you use an NTP server (use algosec_conf option 2 on the Remote Agent).
-
-
For a local syslog (on the new Remote Agent):
- Reassign the IP address of the original Remote Agent to the new Remote Agent to which devices have been relocated. Make sure you have deleted the original Remote Agent from the system before reassigning its IP to the target node. See To change the IP address of a Remote Agent.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new Remote Agent IP.
- For external syslog, upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
Central Manager with Geographic distributions (Remote Agents) and Load distributions
-
 Build your migration target
Build your migration target
Do the following:
- Choose your target type. See Choose your migration target appliance type.
-
Build the target machine according to target system requirements. See Migration target system requirements.
Important: Do not perform any hardening procedures that are not mentioned in Migration target system requirements. Doing so at this point may cause the migration to fail. For steps you can take once your system is successfully running A32.00, see ASMS system security.
-
Download upgrade packages from the Portal (Downloads > Software > AlgoSecSecurity Management Suite):
-
Select Upgrade (All Deployments) and specify A32.00 version with migration to CentOS 7.
-
Click Next. The Upgrade to ASMS A32.00 with Migration to CentOS 7 page appears.
-
Follow steps to download all upgrade packages for all node types at one time. Build numbers must be the same for all the packages you'll use, so downloading all at once ensures that, when you upgrade, you will have everything you need when you need it.
Tip: Save all packages to a secure location. You will need them later.
-
Step 1: Download upgrade package for Source Server: Click to download the ASMS A32.00 base package.
Note: If you have FIPS deployment, click I need the FIPS version. For more details, see Upgrade/migration steps.
Click Download Selected.
Note: The upgrade package consists of four build files:
- fireflow-3200.0.0-bbb.x86_64.run
- fa-3200.0.0-bbb.x86_64.run
For non-FIPS:
- algosec-appliance-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-3200.0.0-aaa-el7.x86_64.run
For FIPS:
- algosec-appliance-fips-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run
- Step 2: Download upgrade package for Target Server: If your Target is a new AlgoSec Hardware Appliance, you can use the base upgrade package you downloaded in step 1.
Otherwise, based on your Target Server deployment type, download the relevant upgrade package.
-
Step 3: Download upgrade packages for other nodes: If your your other nodes (Remote Agents, Load Distribution Units, HA/DR) are new AlgoSec Hardware Appliances, you can use the base upgrade package you downloaded in step 1.
Otherwise, depending on your nodes deployment type, download the relevant upgrade packages.
Tip: No need to download packages again if you already downloaded them in step 2.
-
-
-
On Target
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
For new appliances, follow steps in Deploy standalone appliances (not necessary for repurposed appliances).
-
For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
- Install the valid ASMS migration license on the target machine. See Migration target license . For instructions to install the license, see ASMS licensing.
- Verify the required ports are opened between source and target machine. See Required port connections. (In particular see the far right column, Central Manager (or Standalone Server) Migration).
-
Disable any NAT configuration between source and target machines.
-
 Run system checks
Run system checks
Do the following:
On Source
-
Perform source environment checks on the source server:
-
Check that required ASMS services are running. Go to the algosec_conf menu and enter option 17 Check services status. For details, see Test ASMS processes.
Note: Even if some services are not running, the upgrade process asks you confirm whether you would like to continue. We recommend contacting AlgoSec customer support to start these services before continuing.
- Last upgrade status must be successful.
- Last upgrade status must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
-
Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
- Last upgrade status, including remote nodes (RA/LDU), must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
-
- Verify that all system nodes are at same date and time. Nodes can be in different time zones, but they have to be at the same time relative to UTC.
- If you are not currently using FireFlow, make sure that the value of the FireFlow_configured parameter in /home/afa/.fa/config is set to no.
FireFlow_configured=no - For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
-
Follow the steps in the AlgoPedia article: CentOS 7 Migration | Preventive action for A32.0.
-
If you have configured an SSL certificate pass phrase, remove it now (recommended) or copy the ssl pass phrase file.
 To remove the SSL certificate pass phrase:
To remove the SSL certificate pass phrase:
-
On the CLI, enter the following script to print the pass phrase:
echo -e '#!/bin/bash\necho "Enter your SSL Passphrase here"' > /etc/httpd/conf.d/sslpassphrase
chmod 700 /etc/httpd/conf.d/sslpassphrase
-
Configure httpd to use the pass phrase script by entering the following:
-
Edit /etc/httpd/conf.d/ssl.conf
-
Change text from:
SSLPassPhraseDialog builtin
to:
SSLPassPhraseDialog exec:/etc/httpd/conf.d/sslpassphrase
-
-
Check that httpd starts without having to enter a pass phrase. Enter:
/etc/init.d/httpd restart
 To copy the SSL certificate pass phrase:
To copy the SSL certificate pass phrase:
-
Log in to Source as root user.
-
Run the commands:
PASSP=`grep SSLPassPhraseDialog /etc/httpd/conf.d/ssl.conf | grep -v builtin | cut -f2 -d\:` ; chmod a+x $PASSP
PFILE=`echo ${PASSP##*/}` ; echo $PFILE -
Copy the CLI printed output.
In this case, ssl-phrase.
-
Run the following replacing the actual Target IP:
rsync -rtu $PASSP <TARGET_IP>:/usr/libexec/ -
Enter password when prompted.
-
-
Log in to Target as root user and enter the following replacing the string you copied from step 1:
\cp -rpv /usr/libexec/httpd-ssl-pass-dialog{,.BACKUP_COPY} ; \cp -rpv /usr/libexec/<Copied string from step 1> /usr/libexec/httpd-ssl-pass-dialogFor Example, if the copied string is <ssl-phrase>, the command will be:
\cp -rpv /usr/libexec/ssl-phrase/usr/libexec/httpd-ssl-pass-dialog
-
Verification: Restart httpd and ensure httpd starts up:
service httpd restart
-
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Close ⌃-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
-
 Run system prerequisites
Run system prerequisites
Use the first part of the upgrade routine to run the automatic system prerequisites checks even without upgrading. If any of the prerequisite checks fail, the system notifies which items need to be fixed. After getting the system checks prerequisites results, stop before upgrading by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).Do the following:
On Source
-
Verify that your system is ready for the upgrade by running automatic prerequisite checks. checks are finisheddo not continue to the upgrade process:
-
Copy the upgrade package you saved previously to the /root/AlgoSec_Upgrade/ directory on the source server.
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
Note: Java11 is installed the first time option 8 is run to support prerequisite checks. It will not affect any of the existing system functionality.
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run on both the source and migration target machine. When the checks are finished manually stop the process by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).If you continue to upgrade at this point, you risk losing data.
-
-
-
 Fix prerequisite check errors
Fix prerequisite check errors
Since the next step, Sync Reports from Source to Target, is done on the Target, you can fix on the source the issues that are discovered during the automatic system prerequisites while the next step is running: Except for the following two issues. If either or both is discovered, fix them before proceeding:
Remote node [nodeIP], must be a standalone machine
For instructions, see Remote node must be a standalone machine The following ports are filtered from
local node to node x.x.x.x: [Port#, Port#]The following ports are filtered from
node x.x.x.x to local node: [Port#, Port#]For instructions, see Firewall(s) detected filtering traffic between source (x.x.x.x) and target (x.x.x.x) for ports: [ports] For instructions to resolve automatic system prerequisites checks issues, see Resolve automatic system prerequisites checks issues.
Close ⌃ -
 Sync reports from source to target
Sync reports from source to target
Important: If you use a NAS in your system, there is no need to sync reports since your reports data is already offloaded from the source.
Reports are pulled from the source to the target. The process runs in the background, which will save you a lot of downtime during the upgrade & migration process. If during the interim after time you sync reports and before you upgrade & migrate enough new reports accumulate, you may be prompted by the system to sync again before you upgrade & migrate.
Note: You can only sync reports from one server. If after syncing reports you choose to change to another server, only data from the most recent server synced will be retained.
Note: During the sync, to abort press Ctrl+D on the keyboard. Enter algosec_conf to return to the algosec_conf menu.
Do the following:
On Target
-
Make sure that the amount of free space of the /data/ folder on the new target machine is larger than the sum of the folder sizes of the following on the source:
-
/home/afa/algosec/firewalls/
-
/home/afa/algosec/groups/
-
/home/afa/algosec/matrices/
-
-
Go to the algosec_conf menu, and enter option 16 - Migrate ASMS units. Enter option 3 -Sync reports from peer node.
-
Enter the IP address and root password of the peer (the source) node. Reports are synced to the target node.
Warning: Make sure you enter the correct IP for the peer (source) node, otherwise data can be overwritten.
-
-
 Backup your system
Backup your system
Do the following:
On Source
-
Upgrade your system to the latest build version of either A30.00 or A30.10, if you haven't already. Download latest build from the AlgoSec portal.
Note: The latest build is the build available on the portal on the day you migrate. You may need to restore your system with this build so save the files to a secure location.
-
Perform a backup of the source server to an external or network drive. Make sure to include traffic logs and reports in your backup. See Backup and restore.
Additionally, for virtual and host-based appliances, when available, power-off the machine and take a snapshot (cold snapshot).
Important: If your system has a cluster (CM and/or RA), the order in which you take the snapshots is critical.
 To find out the order in which you should take the snapshots:
To find out the order in which you should take the snapshots:
-
Go the algosec_conf menu and run option 13 HA/DR Setup.
-
Run option 1. View cluster status details.
-
Take a snapshot first from the node without DB in its row and then take a snapshot of the node with DB in its row.
For example, if the results are:

Node 2. DR Primary doesn’t show the DB in its row, so its snapshot should be taken first.
Node 1. Primary shows the DB in its row, so its snapshot should be taken second.
-
-
-
 Migrate load distribution units
Migrate load distribution units
You can migrate your Load Distribution Units now to easily connect to them the Central Manager after it is migrated; or you can migrate them late and connect them to the Central Manager via the GUI.
Tip: If you choose the migrate your Load Units later, to connect to the new Central Manager see Add or edit Load Units.
-
Install A32.00 with CentOS7 on new or repurposed LDUs. See Supported deployments per architecture structure
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. During the server migration, you will be asked for LDU IPs to easily reconnect later.
-
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
-
 Migrate source to CentOS 7
Migrate source to CentOS 7
Note about custom scripts:
- Before migrating to CentOS 7, all custom scripts should be located in the folder: /usr/share/fireflow/local/etc/site/lib/. If you have customizations placed in other folders, move them to /usr/share/fireflow/local/etc/site/lib/. After the migration, you can return them to their previous locations.
- If you use custom scripts and other code that was especially made for you by the AlgoSec PS team, we recommend that you check with the AlgoSec before migrating your data to ensure that the codes migrate successfully.
Note: Communicate to your organization that users must not connect to the AlgoSec user interface during the migration process. Connections to the AlgoSec user interface during the data migration process can cause migration failure.
Note: During the migration process, any scheduled backup will be disabled.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Do the following:
-
If you are not already connected to the ASMS Administration interface (algosec_conf), connect now. For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
-
- Enter the IP address and root password of the target machine. Press <Enter>.
-
(optional) Provide new LDU IPs at this stage or you can configure them later. (If you changed LDU IPs earlier, you can provide them now and they will be automatically connected at the end of the upgrade/migration process). Otherwise, press <Enter> to skip through the prompts.
-
Prerequisite checks are run including a check for new reports that may need to be synced. If all checks pass, continue by entering y.
Note: If errors are discovered or new reports need to be synced, we recommend you stop now and follow the suggested steps. When done, run the upgrade again by going to the algosec_conf menu, and run option 8 - upgrade software.
- If you backed up your system in the previous section, press y to continue.
- When the upgrade finishes successfully, data migration from server to target starts automatically.
- During data migration, if there are any errors, the process will stop. See Upgrade/migration troubleshooting for instructions to address issues that occur. Once resolved, re-initiate the data migration process. From algosec_conf menu, run option 8 - upgrade software.
-
When data migration is completed, based on the appliance type of your source and target servers (see CentOS 7 migration target), either:
Repurpose the source machine for use as official machine Repurpose the source machine. See Install ASMS from a bootable flash drive.
Migrate data from target back to the repurposed machine. On the source, from the algosec_conf menu, run option 16 - Migrate ASMS units.
Target replaces source as official machine Use target as official machine and dispose of old source machine.
-
-
For a local syslog (on the Central Manager) and your target replaces the source as official machine:
-
On Target Reassign the IP address of the replaced source node to the new Central Manager (the target node). See Basic configurations.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new CM (or standalone server) IP.
-
- For external syslog-ng server:
- Upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
 If you use AutoDiscovery, migrate it now:
If you use AutoDiscovery, migrate it now:
Note: ASMS A32.00 connects to the new A32.00 AutoDiscovery server only, not to the old one.
The new A32.00 AutoDiscovery server is hosted on a dedicated Remote Agent node in ASMS. See AutoDiscovery server system requirements.
Do the following:
- Deploy the new AutoDiscovery server. See Deploy the AutoDiscovery server.
- Migrate data from the old AutoDiscovery server to the new one. See Migrate data from earlier AutoDiscovery versions.
- Redirect your Netflow target to the new AutoDiscovery server IP.
- Redefine user roles as part of ASMS. See Configure AutoDiscovery.
- Upgrade remote AutoDiscovery sensors, if exist, to A32.00. See Upgrade remote AutoDiscovery sensors.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
-
 Migrate remote agents
Migrate remote agents
As part of the upgrade process of the Central Manager, Remote Agents are automatically upgraded to A32.00 while still running CentOS 6. These Remote Agents have full functionality when working with a Central Manager running A32.00 CentOS 7. This allows you the flexibility to migrate your Remote Agents to CentOS 7 now or in future maintenance windows.
Important: In a system using CentOS 7, in order to perform upgrades, all your system's nodes must be in CentOS 7.
Note: Remote Agents in High Availability clusters require licenses.
If you have a machine available to replace the Remote Agent that meets CentOS 7 migration requirements (see Upgrade/migration prerequisites), fresh install or repurpose the machine to A32.00 with CentOS 7 and then relocate devices to it from the old Remote Agent. If not, relocate the devices to the Central Manager, then repurpose or replace the existing Remote Agent and finally relocate the devices back from the Central Manager.
Do the following:
-
Relocate devices:
 If you have an available machine that meets CentOS 7 migration requirements to use as a new Remote Agent:
If you have an available machine that meets CentOS 7 migration requirements to use as a new Remote Agent:
-
Install A32.00 with CentOS7 on a new Remote Agent:
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
Add the new Remote Agent to the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- In the Architecture tab, add the new Remote Agent to the Geographic Distribution list.
-
Make sure to open the necessary port between each device and the remote Agent, depending on the protocol being used to connect to the device. See Manage devices.
-
Relocate devices from the original Remote Agent to the new one. See Relocate devices.
Note: Devices that are currently being monitored or analyzed will be skipped. Wait several minutes for the current monitor/analysis process to end and run the relocation process again.
Important: If the relocation fails and you receive the message:
Some devices were defined with an incorrect syslog host.
-
Delete the original Remote Agent from the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Delete the Remote Agent from the Geographic Distribution list.
- If your Remote Agent is in a cluster, rebuild cluster with a new or repurposed machine running A32.00 with CentOS 7. Both the RA and the RA cluster node require a license installed. See Build a cluster.
 If relocating devices to the Central Manager:
If relocating devices to the Central Manager:
-
Relocate devices to the Central Manager. See Relocate devices. The devices are grouped automatically and relocated to the Central Manager.
Note: Devices that are currently being monitored or analyzed will be skipped. Wait several minutes for the current monitor/analysis process to end and run the relocation process again.
-
Delete the original Remote Agent from the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Delete the Remote Agent from the Geographic Distribution list.
-
Install A32.00 with CentOS7 on new or repurposed Remote Agent:
Important: Make sure you have completed step a successfully before you do this step or data loss may occur.
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
Add the new Remote Agent to the architecture:
- In AlgoSec Firewall Analyzer, go to the Administration page.
- Click the Architecture tab.
- Add the Remote Agent to the Geographic Distribution list.
-
Make sure to open the necessary port between each device and the remote Agent, depending on the protocol being used to connect to the device. See Manage devices.
- Relocate devices group from CM to the new Remote Agent running CentOS 7. See Relocate devices.
Important: If the relocation fails and you receive the message:
Some devices were defined with an incorrect syslog host.
- If your Remote Agent is in a cluster, rebuild cluster with a new or repurposed machine running A32.00 with CentOS 7. Both the RA and the RA cluster node require a license installed. See Build a cluster.
-
-
Make sure that the date on the Remote Agent is set correctly. Machines can be in different time zones but they have to be at the same time relative to UTC.
Tip: We recommended you use an NTP server (use algosec_conf option 2 on the Remote Agent).
-
-
For a local syslog (on the new Remote Agent):
- Reassign the IP address of the original Remote Agent to the new Remote Agent to which devices have been relocated. Make sure you have deleted the original Remote Agent from the system before reassigning its IP to the target node. See To change the IP address of a Remote Agent.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new Remote Agent IP.
- For external syslog, upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
Central Manager with Load distributions
-
 Build your migration target
Build your migration target
Do the following:
- Choose your target type. See Choose your migration target appliance type.
-
Build the target machine according to target system requirements. See Migration target system requirements.
Important: Do not perform any hardening procedures that are not mentioned in Migration target system requirements. Doing so at this point may cause the migration to fail. For steps you can take once your system is successfully running A32.00, see ASMS system security.
-
Download upgrade packages from the Portal (Downloads > Software > AlgoSecSecurity Management Suite):
-
Select Upgrade (All Deployments) and specify A32.00 version with migration to CentOS 7.
-
Click Next. The Upgrade to ASMS A32.00 with Migration to CentOS 7 page appears.
-
Follow steps to download all upgrade packages for all node types at one time. Build numbers must be the same for all the packages you'll use, so downloading all at once ensures that, when you upgrade, you will have everything you need when you need it.
Tip: Save all packages to a secure location. You will need them later.
-
Step 1: Download upgrade package for Source Server: Click to download the ASMS A32.00 base package.
Note: If you have FIPS deployment, click I need the FIPS version. For more details, see Upgrade/migration steps.
Click Download Selected.
Note: The upgrade package consists of four build files:
- fireflow-3200.0.0-bbb.x86_64.run
- fa-3200.0.0-bbb.x86_64.run
For non-FIPS:
- algosec-appliance-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-3200.0.0-aaa-el7.x86_64.run
For FIPS:
- algosec-appliance-fips-3200.0.0-aaa-el6.x86_64.run
- algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run
- Step 2: Download upgrade package for Target Server: If your Target is a new AlgoSec Hardware Appliance, you can use the base upgrade package you downloaded in step 1.
Otherwise, based on your Target Server deployment type, download the relevant upgrade package.
-
Step 3: Download upgrade packages for other nodes: If your your other nodes (Remote Agents, Load Distribution Units, HA/DR) are new AlgoSec Hardware Appliances, you can use the base upgrade package you downloaded in step 1.
Otherwise, depending on your nodes deployment type, download the relevant upgrade packages.
Tip: No need to download packages again if you already downloaded them in step 2.
-
-
-
On Target
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. -
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
For new appliances, follow steps in Deploy standalone appliances (not necessary for repurposed appliances).
-
For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
- Install the valid ASMS migration license on the target machine. See Migration target license . For instructions to install the license, see ASMS licensing.
- Verify the required ports are opened between source and target machine. See Required port connections. (In particular see the far right column, Central Manager (or Standalone Server) Migration).
-
Disable any NAT configuration between source and target machines.
-
 Run system checks
Run system checks
Do the following:
On Source
-
Perform source environment checks on the source server:
-
Check that required ASMS services are running. Go to the algosec_conf menu and enter option 17 Check services status. For details, see Test ASMS processes.
Note: Even if some services are not running, the upgrade process asks you confirm whether you would like to continue. We recommend contacting AlgoSec customer support to start these services before continuing.
- Last upgrade status must be successful.
- Last upgrade status must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
- Check that all Remote Agents are reachable. See Access the AFA Administration area.
- Last upgrade status, including Remote Agents, must be successful.
-
Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all Load Distribution Units are reachable. See Access the AFA Administration area.
- Last upgrade status, including Load Distribution Units, must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
- Last upgrade status, including remote nodes (RA/LDU), must be successful.
- Check that all remote nodes (RA/LDU) are reachable. See Access the AFA Administration area.
-
- Verify that all system nodes are at same date and time. Nodes can be in different time zones, but they have to be at the same time relative to UTC.
- If you are not currently using FireFlow, make sure that the value of the FireFlow_configured parameter in /home/afa/.fa/config is set to no.
FireFlow_configured=no - For virtual appliances: verify that the newest VMware Tools package version is installed and up-to-date. See Best practices for your AlgoSec VMware Deployment .
-
Follow the steps in the AlgoPedia article: CentOS 7 Migration | Preventive action for A32.0.
-
If you have configured an SSL certificate pass phrase, remove it now (recommended) or copy the ssl pass phrase file.
 To remove the SSL certificate pass phrase:
To remove the SSL certificate pass phrase:
-
On the CLI, enter the following script to print the pass phrase:
echo -e '#!/bin/bash\necho "Enter your SSL Passphrase here"' > /etc/httpd/conf.d/sslpassphrase
chmod 700 /etc/httpd/conf.d/sslpassphrase
-
Configure httpd to use the pass phrase script by entering the following:
-
Edit /etc/httpd/conf.d/ssl.conf
-
Change text from:
SSLPassPhraseDialog builtin
to:
SSLPassPhraseDialog exec:/etc/httpd/conf.d/sslpassphrase
-
-
Check that httpd starts without having to enter a pass phrase. Enter:
/etc/init.d/httpd restart
 To copy the SSL certificate pass phrase:
To copy the SSL certificate pass phrase:
-
Log in to Source as root user.
-
Run the commands:
PASSP=`grep SSLPassPhraseDialog /etc/httpd/conf.d/ssl.conf | grep -v builtin | cut -f2 -d\:` ; chmod a+x $PASSP
PFILE=`echo ${PASSP##*/}` ; echo $PFILE -
Copy the CLI printed output.
In this case, ssl-phrase.
-
Run the following replacing the actual Target IP:
rsync -rtu $PASSP <TARGET_IP>:/usr/libexec/ -
Enter password when prompted.
-
-
Log in to Target as root user and enter the following replacing the string you copied from step 1:
\cp -rpv /usr/libexec/httpd-ssl-pass-dialog{,.BACKUP_COPY} ; \cp -rpv /usr/libexec/<Copied string from step 1> /usr/libexec/httpd-ssl-pass-dialogFor Example, if the copied string is <ssl-phrase>, the command will be:
\cp -rpv /usr/libexec/ssl-phrase/usr/libexec/httpd-ssl-pass-dialog
-
Verification: Restart httpd and ensure httpd starts up:
service httpd restart
-
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Close ⌃-
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
Make sure that HA/DR clusters are synced:
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 13 - HA/DR Setup. The cluster status is displayed.
Note: If the cluster is syncing, wait a few moments.
-
-
 Run system prerequisites
Run system prerequisites
Use the first part of the upgrade routine to run the automatic system prerequisites checks even without upgrading. If any of the prerequisite checks fail, the system notifies which items need to be fixed. After getting the system checks prerequisites results, stop before upgrading by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).Do the following:
On Source
-
Verify that your system is ready for the upgrade by running automatic prerequisite checks. checks are finisheddo not continue to the upgrade process:
-
Copy the upgrade package you saved previously to the /root/AlgoSec_Upgrade/ directory on the source server.
- Connect to the ASMS Administration interface (algosec_conf). For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
Note: Java11 is installed the first time option 8 is run to support prerequisite checks. It will not affect any of the existing system functionality.
-
Enter the IP address and root password of the target machine.
-
Prerequisite checks are run on both the source and migration target machine. When the checks are finished manually stop the process by entering n at the prompt:
Do you want to continue with the upgrade? (y/n).If you continue to upgrade at this point, you risk losing data.
-
-
-
 Fix prerequisite check errors
Fix prerequisite check errors
Since the next step, Sync Reports from Source to Target, is done on the Target, you can fix on the source the issues that are discovered during the automatic system prerequisites while the next step is running: Except for the following two issues. If either or both is discovered, fix them before proceeding:
Remote node [nodeIP], must be a standalone machine
For instructions, see Remote node must be a standalone machine The following ports are filtered from
local node to node x.x.x.x: [Port#, Port#]The following ports are filtered from
node x.x.x.x to local node: [Port#, Port#]For instructions, see Firewall(s) detected filtering traffic between source (x.x.x.x) and target (x.x.x.x) for ports: [ports] For instructions to resolve automatic system prerequisites checks issues, see Resolve automatic system prerequisites checks issues.
Close ⌃ -
 Sync reports from source to target
Sync reports from source to target
Important: If you use a NAS in your system, there is no need to sync reports since your reports data is already offloaded from the source.
Reports are pulled from the source to the target. The process runs in the background, which will save you a lot of downtime during the upgrade & migration process. If during the interim after time you sync reports and before you upgrade & migrate enough new reports accumulate, you may be prompted by the system to sync again before you upgrade & migrate.
Note: You can only sync reports from one server. If after syncing reports you choose to change to another server, only data from the most recent server synced will be retained.
Note: During the sync, to abort press Ctrl+D on the keyboard. Enter algosec_conf to return to the algosec_conf menu.
Do the following:
On Target
-
Make sure that the amount of free space of the /data/ folder on the new target machine is larger than the sum of the folder sizes of the following on the source:
-
/home/afa/algosec/firewalls/
-
/home/afa/algosec/groups/
-
/home/afa/algosec/matrices/
-
-
Go to the algosec_conf menu, and enter option 16 - Migrate ASMS units. Enter option 3 -Sync reports from peer node.
-
Enter the IP address and root password of the peer (the source) node. Reports are synced to the target node.
Warning: Make sure you enter the correct IP for the peer (source) node, otherwise data can be overwritten.
-
-
 Backup your system
Backup your system
Do the following:
On Source
-
Upgrade your system to the latest build version of either A30.00 or A30.10, if you haven't already. Download latest build from the AlgoSec portal.
Note: The latest build is the build available on the portal on the day you migrate. You may need to restore your system with this build so save the files to a secure location.
-
Perform a backup of the source server to an external or network drive. Make sure to include traffic logs and reports in your backup. See Backup and restore.
Additionally, for virtual and host-based appliances, when available, power-off the machine and take a snapshot (cold snapshot).
Important: If your system has a cluster (CM and/or RA), the order in which you take the snapshots is critical.
 To find out the order in which you should take the snapshots:
To find out the order in which you should take the snapshots:
-
Go the algosec_conf menu and run option 13 HA/DR Setup.
-
Run option 1. View cluster status details.
-
Take a snapshot first from the node without DB in its row and then take a snapshot of the node with DB in its row.
For example, if the results are:

Node 2. DR Primary doesn’t show the DB in its row, so its snapshot should be taken first.
Node 1. Primary shows the DB in its row, so its snapshot should be taken second.
-
-
-
 Migrate load distribution units
Migrate load distribution units
You can migrate your Load Distribution Units now to easily connect to them the Central Manager after it is migrated; or you can migrate them late and connect them to the Central Manager via the GUI.
Tip: If you choose the migrate your Load Units later, to connect to the new Central Manager see Add or edit Load Units.
-
Install A32.00 with CentOS7 on new or repurposed LDUs. See Supported deployments per architecture structure
For AlgoSec hardware appliances: -
If your appliance is loaded with ASMS A32.00: Install the base upgrade package you downloaded for the source server.
-
If your appliance is not loaded with ASMS A32.00 (that is, it is loaded with A30.10 or A32.10 or above), either:
-
Load the Repurposed AlgoSec Hardware Appliance image to a flash drive and install in the target machine. See Install ASMS from a bootable flash drive. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
install the Repurposed AlgoSec Hardware Appliance image on the target machine via iLO. See Install ASMS with iLO 5. Then, update the build by installing the ASMS base upgrade package to the same build as the packages you downloaded in step 3.
-
For virtual and host based appliances: Install the ASMS software package for A32.00 based on deployment type. During the server migration, you will be asked for LDU IPs to easily reconnect later.
-
-
For FIPS, install the FIPS build algosec-appliance-fips-3200.0.0-aaa-el7.x86_64.run. Restart the machine.
-
-
 Migrate source to CentOS 7
Migrate source to CentOS 7
Note about custom scripts:
- Before migrating to CentOS 7, all custom scripts should be located in the folder: /usr/share/fireflow/local/etc/site/lib/. If you have customizations placed in other folders, move them to /usr/share/fireflow/local/etc/site/lib/. After the migration, you can return them to their previous locations.
- If you use custom scripts and other code that was especially made for you by the AlgoSec PS team, we recommend that you check with the AlgoSec before migrating your data to ensure that the codes migrate successfully.
Note: Communicate to your organization that users must not connect to the AlgoSec user interface during the migration process. Connections to the AlgoSec user interface during the data migration process can cause migration failure.
Note: During the migration process, any scheduled backup will be disabled.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Important: If you want to use your HA/DR node as a fallback, break the cluster before running the following procedure. During the following procedure, clusters are automatically broken and Load Distribution Units are disconnected after being upgraded to A32.00.
Do the following:
-
If you are not already connected to the ASMS Administration interface (algosec_conf), connect now. For details, see Connect to and Utilize the Administration Interface.
-
In the Administration interface main menu, run option 8 - Upgrade software.
-
- Enter the IP address and root password of the target machine. Press <Enter>.
-
(optional) Provide new LDU IPs at this stage or you can configure them later. (If you changed LDU IPs earlier, you can provide them now and they will be automatically connected at the end of the upgrade/migration process). Otherwise, press <Enter> to skip through the prompts.
-
Prerequisite checks are run including a check for new reports that may need to be synced. If all checks pass, continue by entering y.
Note: If errors are discovered or new reports need to be synced, we recommend you stop now and follow the suggested steps. When done, run the upgrade again by going to the algosec_conf menu, and run option 8 - upgrade software.
- If you backed up your system in the previous section, press y to continue.
- When the upgrade finishes successfully, data migration from server to target starts automatically.
- During data migration, if there are any errors, the process will stop. See Upgrade/migration troubleshooting for instructions to address issues that occur. Once resolved, re-initiate the data migration process. From algosec_conf menu, run option 8 - upgrade software.
-
When data migration is completed, based on the appliance type of your source and target servers (see CentOS 7 migration target), either:
Repurpose the source machine for use as official machine Repurpose the source machine. See Install ASMS from a bootable flash drive.
Migrate data from target back to the repurposed machine. On the source, from the algosec_conf menu, run option 16 - Migrate ASMS units.
Target replaces source as official machine Use target as official machine and dispose of old source machine.
-
-
For a local syslog (on the Central Manager) and your target replaces the source as official machine:
-
On Target Reassign the IP address of the replaced source node to the new Central Manager (the target node). See Basic configurations.
Note: If you do not reassign the IP, on each and every device (each firewall), redirect audit logs/traffic logs to new CM (or standalone server) IP.
-
- For external syslog-ng server:
- Upgrade Java to version 11. See Upgrade external syslog server to Java 11.
-
-
 If you use AutoDiscovery, migrate it now:
If you use AutoDiscovery, migrate it now:
Note: ASMS A32.00 connects to the new A32.00 AutoDiscovery server only, not to the old one.
The new A32.00 AutoDiscovery server is hosted on a dedicated Remote Agent node in ASMS. See AutoDiscovery server system requirements.
Do the following:
- Deploy the new AutoDiscovery server. See Deploy the AutoDiscovery server.
- Migrate data from the old AutoDiscovery server to the new one. See Migrate data from earlier AutoDiscovery versions.
- Redirect your Netflow target to the new AutoDiscovery server IP.
- Redefine user roles as part of ASMS. See Configure AutoDiscovery.
- Upgrade remote AutoDiscovery sensors, if exist, to A32.00. See Upgrade remote AutoDiscovery sensors.
At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
Close ⌃At this point, If you plan to upgrade/migrate your Remote Agents in future maintenance windows, before running your system, follow the steps in After the upgrade/migration.
â Next steps: