Onboard Azure Subscriptions to Cloud Network Security
This topic describes how to onboard Azure subscriptions toAppViz Cloud Network Security.
For details about permissions required, see Permissions required for Azure subscriptions.
You can choose from the following four onboarding methods to add new Azure subscriptions, management groups, and tenant root groups:
-
With script - Uses scripts to onboard Azure resources. Changes to subscriptions, management groups, and tenant root groups after onboarding are automatically synced.
-
No script - Onboard Azure resources without using scripts. Changes to subscriptions, management groups, and tenant root groups after onboarding are automatically synced.
-
API (single account) - Onboard a single subscription. Changes to the subscription after onboarding are not synced.
-
Terraform - Leverage Terraform, the infrastructure-as-code solution, for onboarding your Azure subscriptions into AppViz. Changes to subscriptions, management groups, and tenant root groups after onboarding are automatically synced.
Note: Any changes to Azure subscriptions, managed groups, or tenant root groups after onboarding will automatically sync with AppViz once every hour.
Note: For more information about the Azure onboarding script, see Cloud Network Security Azure Onboarding Script.
Access the Onboarding wizard
Do the following:
-
In the AppViz
 Settings area, click
Settings area, click  ONBOARDING.
ONBOARDING.On the Onboarding Managment page that opens, click +Onboard.
-
If you are onboarding your first account, click the New Cloud Account button on the welcome page.
-
Otherwise, click the
 Microsoft Azure button and click Next.
Microsoft Azure button and click Next.The Azure Onboarding wizard appears.
-
Select your preferred method to onboard using the Select Onboarding Method dropdown.
*Automatically syncs changes to subscriptions, management groups, and tenant root groups from Azure to AppViz after onboarding. Onboarding Method Description Automatic sync* With script Uses scripts to onboard Azure resources Yes No script Onboard Azure resources without using scripts Yes API (single account) Onboard a single subscription via API No Terraform Onboard Azure resources using Terraform Yes -
Onboard Azure resources using your preferred method:
 To onboard Azure resources | With script
Close ⌃
To onboard Azure resources | With script
Close ⌃Do the following:
-
Make sure you can access the Azure console as a user with Application Administrator OR Application Developer role.
-
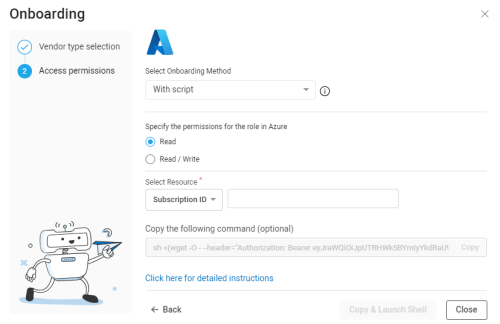
In the Onboarding wizard for Azure, from the Select Onboarding Method dropdown, select With script to select the onboarding method using scripts.
-
Select which level of permissions are required for the role in Azure.
Note: AlgoSec only needs READ permissions to provide support for your AWS security policy management. This requirement ensures you can still receive complete security analysis and recommendations while granting the minimal level of access.
Write permissions can optionally be added for advanced policy change capabilities.
Note about permissions: Read access to the account is the minimum permission required to manage Azure Network Security Groups (NSGs). This enables AppViz visibility for Vnets, subnets, Azure VMs, network flow logs, tags, and routing tables.
-
Select Read to fully support your Azure security policy management, security analysis and recommendations. For more information, see Onboard Azure Subscriptions to Cloud Network Security.
-
(Optional) Select Read/Write for additional advanced policy change capabilities for Azure NSGs. This requires the following permissions:
-
Base Read permissions, as described in Onboard Azure Subscriptions to Cloud Network Security,
-
Additional Write permissions, outlined in .
-
-
-
Select the Azure resource type:
Important: To run the script, the user must possess the necessary permissions for creating a service principal on the selected resource.
-
Enter the Subscription ID or Management Group of the Azure resource to onboard.
Note: When Tenant Root Group is the Azure resource type, no additional information is required.
The Cloud Shell command field is automatically populated based on the resource type and ID / Name.
-
Complete the onboarding using one of the following methods:
-
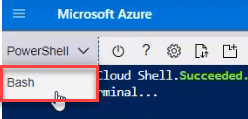
To open a Cloud Shell session directly from the AppViz interface, click
 .
. Note: The Cloud Shell link is copied automatically to you clipboard.
The Azure editor opens in a new browser tab.
-
(Alternative method) If you don't want to open a Cloud Shell session directly from the AppViz interface, you can run bash locally using a proxy:
-
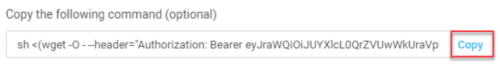
Click Copy to copy the Cloud Shell command.
Note: The command generates an unreadable script. Expand the example below to see the readable version of the script:
 Example of CloudFlare script
CopyClose ⌃
Example of CloudFlare script
CopyClose ⌃#!/bin/bash
#Algosec's multi-tenant application
APP_ID='<ALGOSEC_ONBOARDING_APP_ID>'
#Algosec's onboarding URL
CF_ONBOARDING_URL='https://<HOST>/cloudflow/api/admin/v1/onboarding/azure'
#Target resource
TARGET_RESOURCE='<AZURE_TARGET_RESOURCE>'
out=$(az account show)
az_tenant=$(echo "$out" | jq -r '.tenantId')
echo "Preparing to onboard the target resource [$TARGET_RESOURCE] of [$az_tenant] tenant"
echo "Onboard Algosec AZ-AD Application"
out=$(az ad sp create --id $APP_ID 2>/dev/null)
#Roles
roles=(<AZURE_ROLES>)
for role in "${roles[@]}"; do
echo "Assign a role to the [$TARGET_RESOURCE]: [$role]"
out=$(az role assignment create --role "$role" --assignee $APP_ID --scope $TARGET_RESOURCE)
if [ $? -ne 0 ]; then
echo "ERROR: The target resource [$TARGET_RESOURCE] wasn't found or the user has no permission to work with it"
echo "The onboarding process has failed — please ensure you have the required permissions"
exit 1
fi
done
response=$(curl -X POST "$CF_ONBOARDING_URL" \
-H "Content-Type: application/json" \
-H "Accept: application/json" \
-H "Authorization: $TOKEN" \
--silent \
-d '{ "azure_tenant":"'$az_tenant'" }')
status=$(echo $response | jq -r '.status')
message=$(echo $response | jq -r '.message')
if [ "$status" == 200 ]; then
echo "The onboarding process is finished: $message"
echo "Press CTRL+D to close the terminal session"
else
echo "ERROR: The onboarding process has failed: $message"
fi
-
Paste and run the script in your alternative shell to complete onboarding the subscription(s).
-
-
-
In AppViz, click Close to close the onboarding wizard.
Note: It may take up to an hour for Azure to sync with AppViz.
 To onboard Azure resources | No script
Close ⌃
To onboard Azure resources | No script
Close ⌃You can onboard Azure subscriptions, managed groups, or tenant root groups without using a script if your system does not support using scripts.
Do the following:
-
Make sure you can access the Azure console as a user with Application Administrator OR Application Developer role.
-
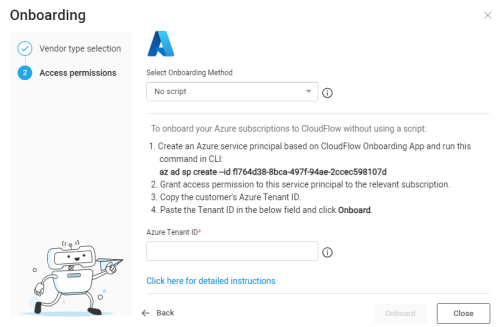
From the Azure CLI, create an Azure service principal based on the AppViz Azure multi-tenant application. You can do this with the following command:
az ad sp create --id 'f1764d38-8bca-497f-94ae-2ccec598107d'
The Azure service principal is created.
The next steps explain how to grant access permission to the service principal to a subscription or management group.
-
Navigate to the Azure console and select either the subscription or management group you want to assign role permissions.
-
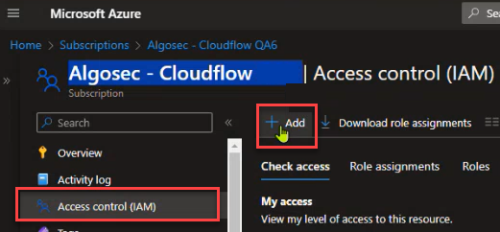
Click Access control (IAM) from the left menu, and then click +Add.
-
From the dropdown, select Add role assignment.
The Add role assignment page appears.
-
Choose the role (permission) you want to grant to the service principal to work with the subscription:
-
Reader: Enable read access only
-
Contributor: Enable read/write access
-
-
(Optional) To allow AppViz to collect NSG Flow logs, grant the service principal the additional roles:
-
Network Contributor
-
Storage Account Contributor
-
-
Click Next.
The Member tab appears.
-
Click Select members. From the Select members popup search for and select CloudFlow Onboarding - prod.
CloudFlow Onboarding - prod will move to the Selected members section of the popup.
-
Click Select.
The Service Principal is assigned to the specific subscription and role.
-
Click Review + assign.
The Review + assign screen appears where the user can review the assignment.
-
Click Review + assign once more to finalize the assignment and allow AppViz to access the Azure subscription.
-
Navigate to Azure Active Directory > Properties > Tenant ID
-
Click on the copy icon to copy Tenant ID associated with the subscription or management group.
-
From the AppViz Azure Onboarding wizard, from the Select Onboarding Method, select No script.
-
Paste the ID into the Azure Tenant ID field.
-
Click Onboard to complete the onboarding process.
 To onboard Azure resources | API (for single account)
To onboard Azure resources | API (for single account)
You can use API calls to add a single Azure subscription to AppViz.
Note: Any changes to a subscription after onboarding are not synced with AppViz. To delete one or more subscriptions, see Offboard Azure subscriptions from AppViz.
Do the following:
-
Go to the page Add a cloud account.
-
Click on the tab For an Azure subscription.
The instructions for onboarding an Azure subscription using API appears.
-
Follow the instructions on the page.
 To onboard Azure resources | Terraform
Close ⌃
To onboard Azure resources | Terraform
Close ⌃You can leverage Terraform, the infrastructure-as-code solution, as another option for onboarding your Azure subscriptions into AppViz.
Do the following:
Integrate the code below into your Terraform toolkit. Make the following parameter value replacements in the Locals section:
Parameter Description Notes cf_auth_url
URL to authorize AppViz
-
For US use:
https://app.algosec.com/api/algosaas/auth/v1/access-keys/login
-
For EMEA use:
https://api.platform.eu.app.algosec.com/api/algosaas/auth/v1/access-keys/login
-
For ANZ use:
https://api.platform.anz.app.algosec.com/api/algosaas/auth/v1/access-keys/login
-
For ME use:
https://api.platform.me.app.algosec.com/api/algosaas/auth/v1/access-keys/login
-
For UAE use:
https://api.platform.uae.app.algosec.com/api/algosaas/auth/v1/access-keys/login
-
For IND use:
https://api.platform.ind.app.algosec.com/api/algosaas/auth/v1/access-keys/login
cf_url
URL to onboard Azure
-
For US use:
https://api.cloudflow.us.app.algosec.com/cloudflow/api/admin/v1/onboarding/azure
-
For EMEA use:
https://api.cloudflow.eu.app.algosec.com/cloudflow/api/admin/v1/onboarding/azure
-
For ANZ use:
https://api.cloudflow.anz.app.algosec.com/cloudflow/api/admin/v1/onboarding/azure
-
For ME use:
https://api.cloudflow.me.app.algosec.com/cloudflow/api/admin/v1/onboarding/aws/api
-
For UAE use:
https://api.cloudflow.uae.app.algosec.com/cloudflow/api/admin/v1/onboarding/aws/api
-
For IND use:
https://api.cloudflow.ind.app.algosec.com/cloudflow/api/admin/v1/onboarding/aws/api
tenantId
Your AppViz Tenant ID
clientId
Client ID
This is part of Access Key details. In AppViz, go to Access Management > API ACCESS tab. Create a new API Access Key or use an existing one. See here. clientSecret
Client Secret of the API Access Key
This is part of Access Key details. In AppViz, go to Access Management > API ACCESS tab. Create a new API Access Key or use an existing one. See here. subscriptionId Azure subscription to be onboarded Copylocals {
cfAuthUrl = "https://stage.app.algosec.com/api/algosaas/auth/v1/access-keys/login"
cfUrl = "https://api.cloudflow.stage.app.algosec.com/cloudflow/api/admin/v1/onboarding/azure"
tenantId = "xxxxxxxxxxxxxxxxxxxxxxxxx"
clientId = "xxxxxxxxxxxxxxxxxxxxxxxxx"
clientSecret = "xxxxxxxxxxxxxxxxxxxxxxxxx"
subscriptionId = "xxxxxxxxxxxxxxxxxxxxxxxxx"
}
provider "azurerm" {
subscription_id = local.subscriptionId
features {}
}
data "azurerm_client_config" "current" {
}
resource "azuread_service_principal" "cloudflow" {
app_role_assignment_required = false
client_id = "b3719212-f07b-46a1-b8eb-bef56d387570"
owners = [data.azurerm_client_config.current.object_id]
}
resource "azuread_application" "cloudflow" {
display_name= "Algosec CloudFLow Onboarding"
}
data "http" "cf_auth" {
url = local.cfAuthUrl
method = "POST"
# Optional request headers
request_headers = {
Accept = "application/json"
}
request_body = jsonencode({ tenantId : local.tenantId, clientId : local.clientId, clientSecret : local.clientSecret })
lifecycle {
postcondition {
condition = contains([200, 201, 204], self.status_code)
error_message = "Authorization failed"
}
}
}
locals {
auth_response = jsondecode(data.http.cf_auth.response_body)
auth_token = local.auth_response.access_token
}
data "http" "cf_onboard_account" {
url = local.cfUrl
method = "POST"
# Optional request headers
request_headers = {
Accept = "application/json"
Authorization = "Bearer ${local.auth_token}"
}
request_body = jsonencode({
azure_tenant : data.azurerm_client_config.current.tenant_id,
event: {
RequestType: "Create"
}
})
lifecycle {
postcondition {
condition = contains([200, 201, 204], self.status_code)
error_message = "Authorization failed"
}
}
}
######################################################################
# Print the created data to console
output "onboard_status" {
value = data.http.cf_onboard_account.status_code
} -
Enable Azure flow logs
For each Azure device where flow logs are enabled in your connected subscription, AppViz automatically collects flow logs.
The flow logs provide all the details needed to display rule usage data on the risk trigger and network policy pages. On the Network policy pages, AppViz users can clean up old or unused NSG / Azure Firewall policy rules, supported by the display of this data. For more details, see Last used and Clean Up Policies.
To enable Azure Firewall flow logging, do the following:
-
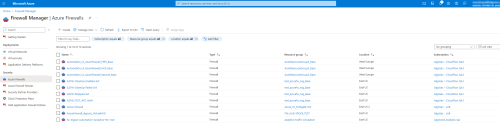
In the Microsoft Azure portal, select Azure Firewalls.
The Azure Firewall page appears with a list of Azure Firewall instances that span different Azure regions and subscriptions.
-
From the list, click on the firewall that you want to enable flow logging and select Diagnostic Settings.
The list of configured diagnostic settings appears.
-
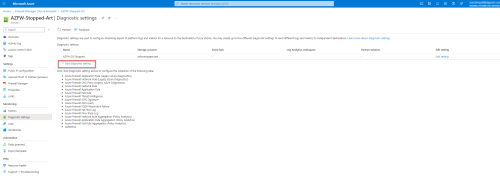
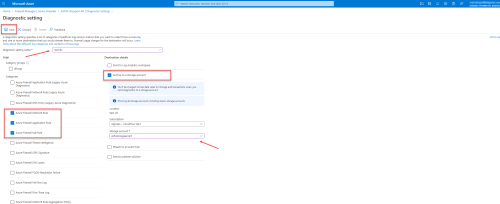
Click + Add diagnostic setting.
The page to add diagnostic settings appears.
-
Enter a Diagnostic setting name.
-
Under Categories, check the following rules to collect log data:
-
Azure Firewall Network Rule
-
Azure Firewall Application Rule
-
Azure Firewall NAT Rule
Note: If any of these categories are not checked, AppViz displays "Flow logs disabled" when showing details related to flow logs. For more details, see Last used and Clean Up Policies.
-
-
Under Destination details, check Archive to a storage account and use the Storage Account dropdown to select the account where the traffic log data is saved.
Note: We recommend using a storage account located in the same subscription as the Azure firewall.
-
Click Save.
Azure Firewall flow logs will now be saved to the storage account and automatically appear in AppViz after the next data collection cycle.
Note: It may take up to one hour for log flow data to begin appearing in AppViz.
-
-
Repeat these steps for each firewall you want to enable flow logging.
Note: NSG flow logs collection will not start unless the following prerequisite tasks have been completed:
-
Enable NSG flow logging.
-
Configure the required permissions on the AppViz ActiveDirectory application using the PowerShell script.
-
Configure NSG flow logs and Diagnostic Settings to enable AppViz to collect, retrieve and analyze flow logs.
-
Run traffic through the subject NSG(s) so that NSG flow logs will be created.
Note: After enabling flow logging, review Configure the Storage Account Firewall (Optional) and decide if it is relevant to the subject subscription.
To enable flow logging, do one of the following:
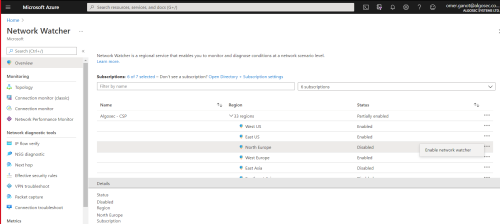
Configure Network Watcher
- Select the subscription containing the NSG you wish to enable.
- Expand the regions button
- Select on the region for which traffic should be collected by clicking it.
The Enable network watcher pop-up is displayed. - Click the Enable network watcher pop-up.
The status of the region changes to enabled.
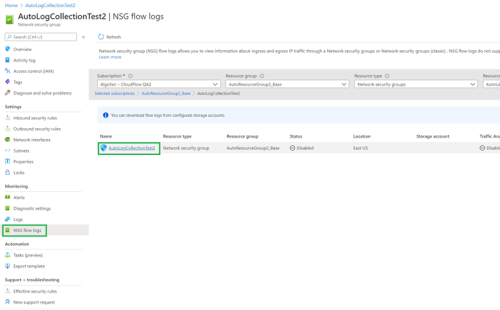
Enable NSG Flow Logs for a specific storage account
To enable NSG flow logs for a specific storage account, follow the steps of Alternative 1 or Alternative 2.
-
Browse to the relevant NSG and select the NSG flow logs in the left navigation.
-
Click the NSG link in the main workspace.
-
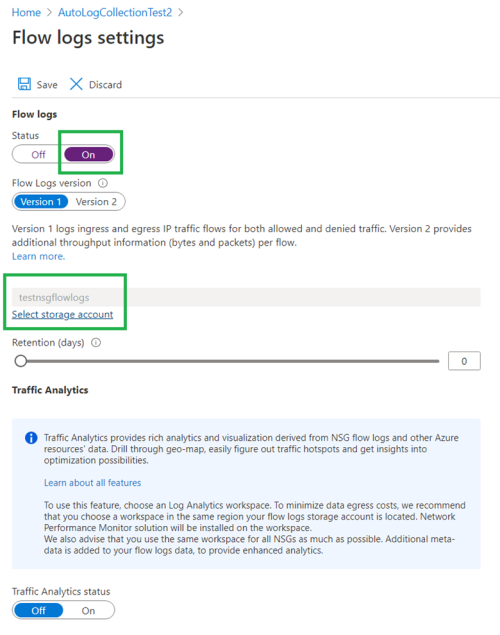
Set the Flow logs status to On and select click on the Select storage account link to select the required storage account.
Alternative 2
This alternative procedure will accomplish the same outcome as Alternative 1.
-
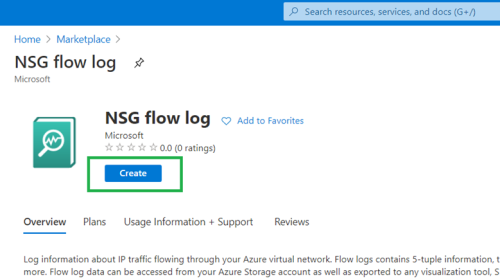
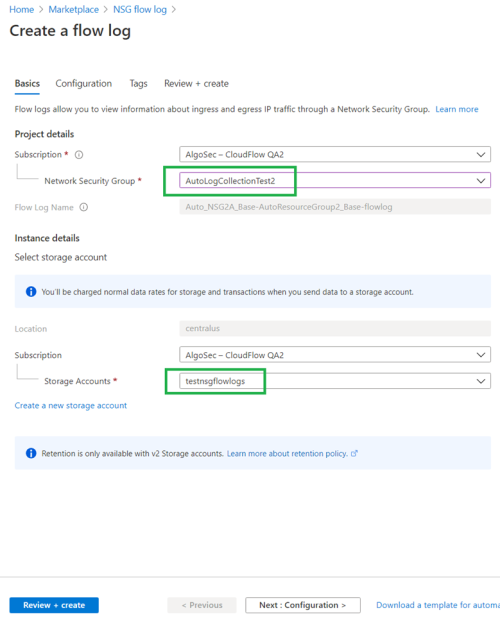
Visit the Azure Marketplace and select “NSG flow logs”.
-
Enter the relevant NSG and storage account details.
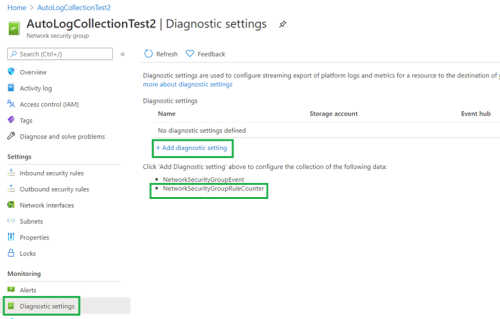
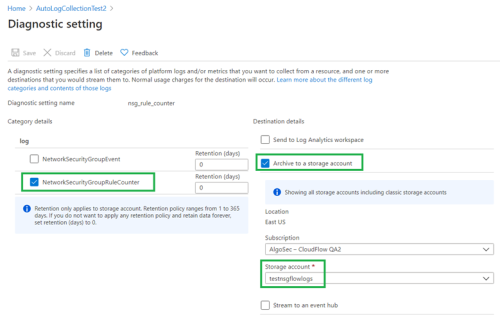
Add Diagnostic Setting
Every NSG with a flow log must also have the diagnostic setting NetworkSecurityGroupRuleCounter added for it.
To add it:
-
Browse to the subject NSG and click on the Add diagnostic settings in the left navigation.
-
Click Add diagnostic setting in the main Diagnostic settings workspace that is displayed.
-
Select the NetworkSecurityGroupRuleCounter option.
-
Select the same storage account as you selected when you configured the NSG Flow Logging.
Configure Storage account firewall (optional)
Review if the following additional configuration is relevant for the subject subscription:
Close ⌃This procedure describes how to enable flow logging for multiple Azure NSGs using a PowerShell script provided by AppViz.
Note: Although the script is recommended for enabling flow logging for multiple NSGs, it can also be used to enable flow logging for a single NSG.
Do the following:
-
In your Azure subscription, register the microsoft.Insights resource provider. Do the following:
-
Manually create a CSV file that lists the flow logging details, and save it to a local directory.
The script that you will download in step 3 will ask for the path to the CSV file and will enable flow logging on all NSGs in each subscription you list in the CSV file.The CSV file must have the following headers (horizontally):
Subscription The Azure subscription ID. Region The region for your Azure subscription. Storage The Azure storage blob where your flow logs are stored.  Example
Example
The following table shows a sample CSV file to use when enabling flow logging on multiple NSGs. The AppViz script will enable flow logging for all NSGs on each subscription listed.
Close ⌃Subscription Region Storage 1c2d1333-1234-4665-aaaa-bc22ccc42323 eastus /subscriptions/1c2d1333-1234-4665-aaaa-bc22ccc42323/resourceGroups/AutoDcExclusive_
RgA_Base/providers/Microsoft.Storage/
storageAccounts/EastUS_SA1c2d1333-1234-4665-aaaa-bc22ccc42323 centralus /subscriptions/1c2d1333-1234-4665-aaaa-bc22ccc42323/resourceGroups/AutoDcExclusive_
RgA_Base/providers/Microsoft.Storage/
storageAccounts/CentralUS_SA88855544-abab-4665-8fdf-bc22ccc42c06 eastus /subscriptions/88855544-abab-4665-8fdf-bc22ccc42c06/resourceGroups/2c06_RG1/providers/
Microsoft.Storage/storageAccounts/EastUS_SA -
On the AppVizAdd New Azure Subscription page
- Click the PowerShell script upload/download icon (bottom task bar)
- Select the upload option
- Browse to and select AppViz's enableNsgFlowLogs.ps1 script.
Note: For users logged into AppViz, this script is available at https://cloudflow.algosec.com/cloudflow/assets/files/enableNsgFlowLogs.ps1.
-
Run the enableNsgFlowLogs.ps1 script. When prompted, enter the path to the CSV file you created in step 2.
As the script runs, it enables flow logging for all NSGs in each Azure subscription you listed in the CSV file, and provides the following feedback:
- Details about the results for each subscription, as the script runs through them
- Summary of all actions performed, once the script has run on all subscriptions listed
-
If you want to manage the retention policy, follow Microsoft's Azure Storage lifecycle management
 instructions.
instructions.
Configure Storage account firewall (Optional)
Review if the following additional configuration is relevant for the subject subscription:
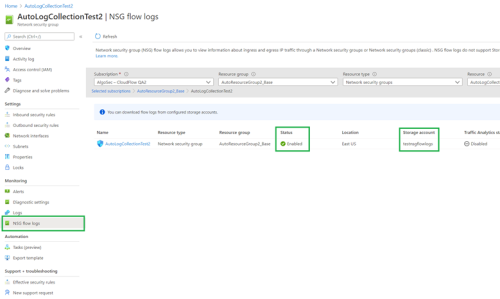
Close ⌃For previously configured NSG flow logs, it is essential to verify that the required Diagnostic settings have been made.
The status Enabled seen in the this image shows you that NSG flow logs have been successfully configured for the NSG named in the same row.
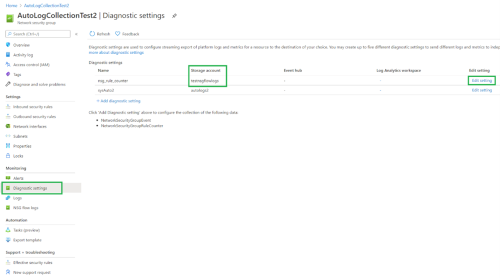
Check if the diagnostic setting has been configured by looking for indications such as those in the following image. If the diagnostic setting has not been configured, be sure to follow the procedure for Adding diagnostic setting, above.
Close ⌃For Azure NSG
AppViz administrators can configure the frequency at which logs are collected, or entirely enable or disable the feature, via API.
Modify the following parameters as needed:
|
TRAFFIC_LOG_FREQUENCY_PERIOD_MINUTES |
Determines the frequency, in minutes, at which AppViz collects traffic logs from Azure NSGs. Value: Integer Default: 60 |
| ENABLE_TRAFFIC_LOGS |
Determines whether traffic log collection is enabled for Azure NSGs. Disabling this parameter will cause AppViz to display Flow logs disabled in the Last used column on the risk trigger details pages, even when flow logging is enabled in the Azure NSG itself. Value: Boolean Default: Enabled |
| INACTIVE_RULE_PERIOD |
Determines the number of days for which AppViz checks for flow logs. Default = 30 NSG rules where flow logs are enabled but no hits are found during the period defined by this parameter are considered as unused. In the Last used column, these rules will be marked as No traffic logged. For details, see Last used. |
To modify any of these parameters, contact AlgoSec support.
Close ⌃If the subscription being configured includes a storage account from which NSG logs will be collected, network access may require configuration.
Do the following:
-
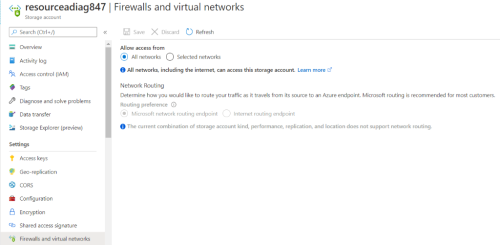
Determine if the storage account's firewall can be configured to allow:
-
Access from all networks, or
-
Access only from selected networks
-
-
If you select allowing access from All networks, the default setting, no further configuration is required.
-
If you select allowing access from Selected networks, to enable AppViz to collect NSG flow logs from the storage account:
-
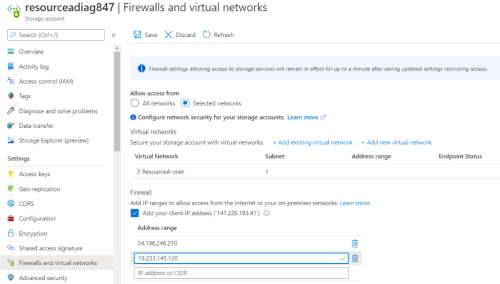
Copy the Current AppViz service IPs for your region, listed below:
US region
18.209.205.33
23.21.89.217
52.21.25.44
EU region 3.124.48.17
3.66.94.197
52.29.166.50
ANZ region
13.237.219.32
3.24.141.128
52.62.160.212
ME region
157.241.75.15
16.24.37.180
16.24.41.212
UAE region
51.112.135.86
51.112.113.39
51.112.73.196
IND region
35.154.132.171
15.206.226.212
13.234.86.181
-
Add these AppViz service IPs to the Firewall-Address range configuration as shown at the bottom of the figure below.
-
Offboard Azure subscriptions from AppViz
You can offboard Azure subscriptions from AppViz with the following methods:
Do the following:
From the Azure Cloudshell run the following command:
az ad sp delete --id 'f1764d38-8bca-497f-94ae-2ccec598107d'
Note: You need proper permissions to run "az ad sp delete".
For more details on using Azure Cloudshell to offboard a subscription, see az ad sp delete.
Note: Removed subscriptions will automatically sync with AppViz once every hour.
Do the following:
-
In AppViz, hover over the
 SETTINGS icon at the bottom left of the screen. After the panel expands, click
SETTINGS icon at the bottom left of the screen. After the panel expands, click  ONBOARDING. The ONBOARDING MANAGEMENT page is displayed, with a table showing details for each account defined in AppViz.
ONBOARDING. The ONBOARDING MANAGEMENT page is displayed, with a table showing details for each account defined in AppViz. -
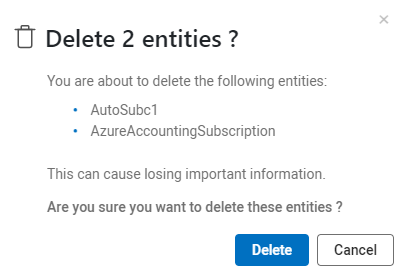
Select the checkbox to the left of the subscriptions(s) you want to delete. You can click on the checkbox in the column header to select all vendors.
-
Click Delete.
A confirmation window appears.
-
Click Delete again to delete the selected subscription(s).







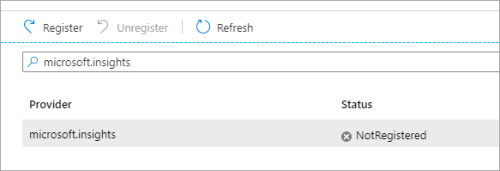
 Register button and wait for the registration to complete.
Register button and wait for the registration to complete.