What's new in A30.10
The AlgoSec Security Management Suite brings business-driven intelligent automation and orchestration of security changes, visibility and control for application connectivity and security, and an enterprise-grade platform and SaaS service.
This topic describes new features available in AlgoSec Security Management Suite version A30.10.
AppViz and AppChange
ASMS A30.10 brings full productization of the AlgoSec AppViz and AppChange add-ons, available over AFA and FireFlow , respectively.
The AppViz and AppChange add-ons replace the functionality previously provided by BusinessFlow. These plugins are installed with and accessed from within AFA and FireFlow but are licensed separately.
Users with AppViz will see the additional AppViz menu item at the bottom of the main menu on the left.
Users licensed for AppChange will also have following additional features available:
- The Change Requests tab, to manage FireFlow change requests from AppViz
- The Resolve button, to resolve FireFlow change requests automatically from AppViz
- The Apply Changes button, to apply changes as specified in the FireFlow change request from AppViz
- The Projects menu, to manage AppViz projects with FireFlow change requests
For more details, see Welcome to AppViz.
Additionally, ASMS A30.10 enhancements for AppViz include the following:
Enterprise-grade and openness
ASMSA30.10 provides the following updates for enterprise-grade features:
Tip: You may want to migrate your Central Manager or relocate devices if you are moving your data centers to a new location or to the cloud, moving to a new set of upgraded appliances, or if you're adding additional appliances to your system.
For an example, see Use case scenario: Migrating an entire ASMS system.
Central Manager migration
ASMS A30.10 enables system administrators to migrate an ASMS Central Manager to another appliance via the algosec_conf CLI menu.
This support includes migrations to a virtual appliance, AlgoSec hardware appliance, or an AWS/Azure instance.
For more details, see Migrate the Central Manager.
Device relocation between nodes
ASMS A30.10 also enables system administrators on distributed architectures to relocate devices using the algosec_conf CLI menu or new REST APIs.
Relocate the devices as needed using the following architectural options:
- From the ASMS Central Manager to Remote Agents
- From Remote Agents to the ASMS Central Manager
- Between different Remote Agents
For details, see Relocate devices.
ASMS open APIs
ASMS’s REST APIs now includes enhanced Swagger support, enabling you to execute API request calls and access lists of request parameters directly from Swagger.
Access the ASMS interactive Swagger APIs from AFA, FireFlow, or AppViz. Click your username at the top-right corner of your screen and select API Documentation. Alternatively, log in to ASMS and navigate to https://<ASMS IP address>/algosec/swagger/swagger-ui.html.
In Swagger, select the spec for the APIs you want to view from the drop-down at the top-right.
For an example, click to play:
For details, see ASMS API reference.
Reporting tool updates
ASMS A30.10 introduces new graphs and dashboards in the AlgoSec Reporting Tool (ART), which have an executive focus. Additionally, A30.10 enables you to navigate between dashboards using the new AlgoSec Navigation pane, located at the top of the page. For example, the following image shows a sample Executive – Workload dashboard, with the AlgoSec Navigation pane highlighted with several more dashboard options.
Click the play the following video, which reviews a few dashboards provided out-of-the-box by AlgoSec.
For more details, see AlgoSec Reporting Tool.
Cloud and hybrid-cloud
AlgoSec CloudFlow provides instant visibility, risk detection, and mitigation for cloud misconfigurations, and also simplifies network security policies with central management and cleanup capabilities.
CloudFlow’s central management features provide instant visibility and risk assessment, helping you to enforce company and regulatory policies, as well as pro-actively detect misconfigurations in the cloud.
In A30.10, we’ve integrated CloudFlow access with ASMS, enabling CloudFlow users to open their tenants directly from the top-left menu.
In ASMS, click the top-left dropdown menu and then click CloudFlow. The CloudFlow login page opens in a separate tab.
Recent CloudFlow enhancements include support for AWS SG and Azure NSG network risks, as well as streamlined risk trigger remediation.
For more details, see Try CloudFlow and the CloudFlow Release Notes.
Devices and automation
ASMS A30.10 brings the following enhancements and updates for device and automation support:
- One-armed service chaining
- Enhancements for Juniper Space Security Director
- FireFlow support for F5 AFM devices
- Maximized traffic workflow optimization
One-armed service chaining
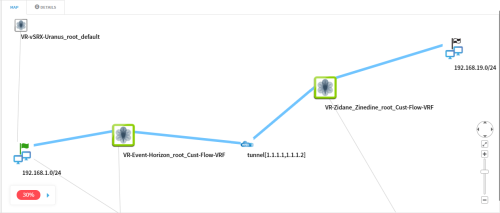
AFA now supports one-armed setup for devices running in Service Chaining modes, where traffic flows in both directions on the same firewall interface. This additional support is provided for single-device queries and risk analysis.
For example, if you have a Check Point CloudGuard device running in a one-armed topology and part of a Cisco ACI Service Graph, AFA now displays that traffic correctly as exiting and entering on the same interface.
AFA now provides support for one-armed configurations for the following device types:
- Check Point CloudGuard
- Cisco Firepower
- Fortinet
- Palo Alto firewalls managed by Panorama
For more details, see Add Check Point devices, Add Cisco devices, and Add Palo Alto Networks devices.
Enhancements for Juniper Space Security Director
ASMS A30.10 provides the following updates for Juniper Space and SRX firewalls managed by Juniper Space:
For more details, see Junos Space Security Director devices in AFA.
FireFlow support for F5 AFM devices
FireFlow now supports work order recommendations on traffic workflows for F5 AFM devices, which FireFlow users can follow and implement manually on their devices.
Tip: If you are using an LTM-only device, use the BIG-IP LTM Only option to add your device to AFA.
For more details, see Add F5 BIG-IP load balancers.
Maximized traffic workflow optimization
In A30.00, FireFlow work orders always recommended creating new contracts for ACI-related change requests.
In A30.10, FireFlow checks to see if there is an existing contract that can be modified to accommodate the requested traffic instead of creating a new contract. This helps cater for new change requests while avoiding a policy bloat.
Additionally, the new CiscoACICreateNewFiltersOnCommonTenant FireFlow configuration parameter enables
FireFlow administrators to determine whether to create new filter objects on the user tenant or the common tenant.
For more details, see Traffic change workflow, Edit work orders, and Work order parameters.
Cisco partnership enhancements
ASMS A30.10 continues to strengthen the partnership between AlgoSec and Cisco, with the following enhancements:
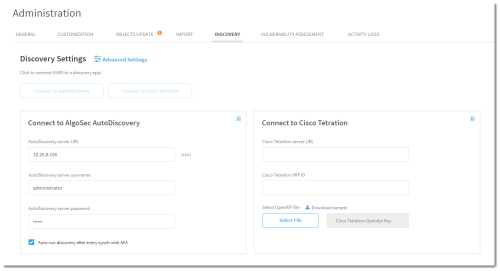
Note: A30.10 also brings enhanced support for discovering flows via Cisco Tetration servers. For more details, see Discovery wizards for AutoDiscovery and Cisco Tetration.
Cisco Firepower baseline compliance reports
ASMS now provides Baseline Compliance reporting for Cisco Firepower devices.
AFA Administrators can select a specific baseline profile, either the one provided by AlgoSec out-of-thebox, a modified version, or they can create their own custom profile.
Note: AlgoSec's baselines for Cisco products, such as Firepower devices, are based on the CIS guidelines and other sources for best practices.
For more details, see BASELINE COMPLIANCE page and Customize baseline configuration profiles.
Cisco ASA enhancements for drop traffic requests
For drop traffic requests that result in changes on Cisco ASA devices, FireFlow’s default recommendation is now to simplify or remove existing rules instead of adding additional deny rules to your policy.
These updated recommendations help keep your policy clean, avoiding complexity and future complications.
Recommendations are updated both for requests originating from FireFlow users, or from AppViz users with AppChange enabled.
For more details, see Cisco ASA firewalls in AFA and Traffic change workflow.
Enhanced support for Cisco ACI
ASMS A30.10 provides the following enhancements for Cisco ACI support:
For more details, see Cisco Application Centric Infrastructure (ACI) devices in AFA.