AppViz (SaaS) - ASMS integration

This topic describes how to create a connection between the AlgoSec SaaS environment and ASMS.
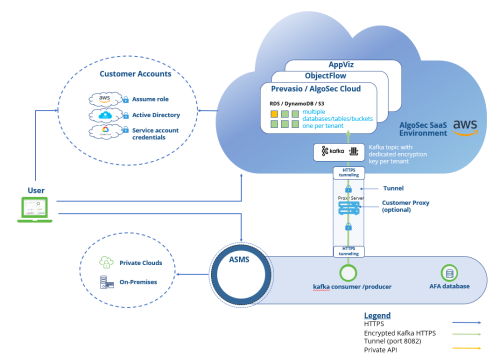
About the HTTPS tunnel
When you integrate AlgoSec SaaS solutions ObjectFlow, AppViz (SaaS), and AppViz (SaaS) with ASMS, by default the HTTPS tunnel automatically starts to route traffic from ASMS to AlgoSec SaaS environment. The tunnel encapsulates traffic and encrypts it with the Public Key certificate mechanism.
Note: The HTTPS tunnel can run with or without a customer proxy server. If you have configured a proxy server in ASMS (see Define a proxy server) the HTTPS tunnel automatically routes traffic through it.
If you are using a proxy server, the Proxy Content Inspection should be disabled to avoid redundant encryption and resulting degradation of the connection.
The following diagram illustrates the HTTPS tunnel architecture:
Note: If you choose to remove the tunnel, ASMS-AlgoSec SaaS secure communication takes place over TLS, using port TCP/9094. For steps to remove the tunnel, see To remove the HTTPS tunnel
For instruction on troubleshooting tunnel connectivity problems, see Troubleshoot AlgoSec SaaS HTTPS tunnel.
Prerequisites
Supported ASMS versions: Can be integrated with ASMS A32.20 and above.
If you are connecting between ASMS and the AlgoSec SaaS environment :
-
Via the HTTPS tunnel:
-
Allow outgoing HTTP traffic on port 8082 towards the Kafka hosts.
-
To ensure successful traffic flow from your customer network to the AlgoSec SaaS services (traffic directed through the HTTP tunnel on port 8082), confirm that your edge router uses static IPs only.
-
-
Without the tunnel:
-
Allow ASMS-AlgoSec SaaS secure communication takes place over TLS, using port TCP/9094.
-
-
Note: When ASMS-AlgoSec SaaS secure communication takes place over TLS, using port TCP/9094, make sure that your connectivity between ASMS and the relevant Kafka host is open.
Connect AppViz (SaaS) to ASMS
This procedure describes how the Admin role can create a
Note: The following steps are relevant both for existing customers of other AlgoSec SaaS solutions and for customers connecting ASMS to AlgoSec SaaS Services for the first time.
Note: ASMS-AlgoSec SaaS integration supports integrating a single ASMS host (i.e. production, testing or Beta) to each AlgoSec SaaS tenant. If you need to change the ASMS host integrated to AlgoSec SaaS, follow Offboard AlgoSec SaaS (AlgoSec Cloud, ObjectFlow, AppViz) from ASMS and then reconnect AppViz (SaaS) to ASMS. If you are also using other AlgoSec SaaS applications, reconnect as well.
Do the following:
-
Connect to Kafka destination hosts:
-
WIth HTTPS tunnel: Allow outgoing HTTP traffic on port 8082 towards the Kafka hosts.
-
Without tunnel: Allow outgoing TLS traffic on port TCP/9094 towards the Kafka hosts.
US region:
-
kafka1.us.algocare.algosec.com
-
kafka2.us.algocare.algosec.com
-
kafka3.us.algocare.algosec.com
EU region:
-
kafka1.eu.algocare.algosec.com
-
kafka2.eu.algocare.algosec.com
-
kafka3.eu.algocare.algosec.com
ANZ region:
-
kafka1.anz.algocare.algosec.com
-
kafka2.anz.algocare.algosec.com
-
kafka3.anz.algocare.algosec.com
ME region:
-
kafka1.me.algocare.algosec.com
-
kafka2.me.algocare.algosec.com
-
kafka3.me.algocare.algosec.com
UAE region
-
kafka1.uae.algocare.algosec.com
-
kafka2.uae.algocare.algosec.com
-
kafka3.uae.algocare.algosec.com
IND region
-
kafka1.ind.algocare.algosec.com
-
kafka2.ind.algocare.algosec.com
-
kafka3.ind.algocare.algosec.com
SGP region
-
kafka1.sgp.algocare.algosec.com
-
kafka2.sgp.algocare.algosec.com
-
kafka3.sgp.algocare.algosec.com
Important: In order to maintain the security of your ASMS instance, AppViz (SaaS) is barred from establishing inbound connections to the ASMS host. AppViz (SaaS)-ASMS integration communication is always initiated by ASMS.
-
-
Start in AppViz (SaaS), and click the Settings
 icon at the bottom left of your screen.
icon at the bottom left of your screen. -
Select ASMS INTEGRATION.
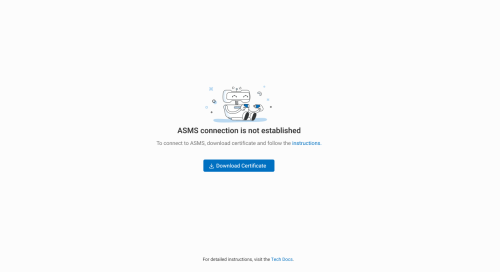
The ASMS Integration screen appears
-
Click
 Download Certificate.
Download Certificate.Note the downloaded file's name (AlgoSec_Cloud_trust_establish_data-{tenant ID}.zip) and location for use in Step 5, below.
-
Upload the trust file (AlgoSec_Cloud_trust_establish_data-{tenant ID}.zip) to the ASMS upgrade directory (/root/AlgoSec_Upgrade).
-
Log in to your ASMS machine with username root.
Note: More details regarding the algosec_conf utility can be found in Connect to the Administration interface in the ASMSDocumentation.
-
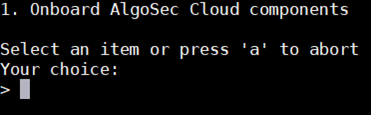
Enter 14 to select option 14. Product and Cloud Configuration from the algosec_conf menu that is displayed .
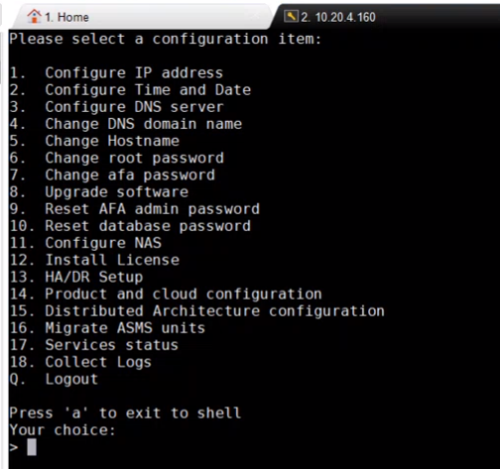
-
Enter 3 to select 3. Cloud Integration from the configuration items submenu.
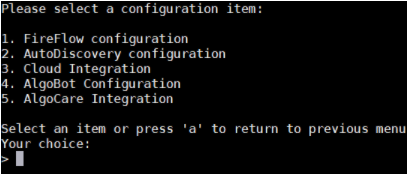
-
Enter 1 to select 1. Onboard AlgoSec Cloud components.
-
When prompted for the path of the configuration file, enter: /root/AlgoSec_Upgrade/AlgoSec_Cloud_trust_establish_data-{tenant ID}.zip
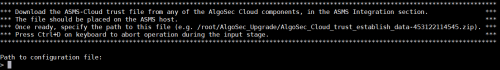
A message will indicate the success or failure of the ASMS-AppViz (SaaS) integration.
Offboard AlgoSec SaaS (AlgoSec Cloud, ObjectFlow, AppViz) from ASMS
To manually offboard (remove the trust between the subject ASMS machine and the target SaaS tenant):
Do the following:
-
Login via SSH to the target ASMS machine as user root
-
Recommended: Backup the folder: /home/afa/.fa/kafka
-
Remove the tunnel:
-
In the algosec_conf main menu, enter 14 Product and cloud configuration.
-
Enter 3 Cloud Integration.
-
Enter 2 HTTPS tunnel Configuration.
-
Enter 2 Remove HTTPS tunnel.
-
Confirm by entering y. The tunnel is removed.
-
-
Delete the folder: /home/afa/.fa/kafka
-
Open the file: /home/afa/.fa/config and remove the following parameters:
-
Kafka_Tenant_Region
-
Kafka_Tenant_Environment
-
Cloud_Tenant_Id
-
APPVIZCLOUD_ENABLED
Save your changes.
-
-
Run the following command:
service ms-cloudflow-broker restart
To remove the HTTPS tunnel
If you do choose to remove the tunnel, ASMS-AlgoSec SaaS secure communication takes place over TLS, using port TCP/9094.
Note: When ASMS-AlgoSec SaaS secure communication takes place over TLS, using port TCP/9094, make sure that your connectivity between ASMS and the relevant Kafka host is open.
In the algosec_conf main menu, enter 14 Product and cloud configuration.
Enter 3 Cloud Integration.
Enter 3 HTTPS tunnel Configuration.
Enter 2 Remove HTTPS tunnel.
Confirm by entering y. The tunnel is removed.