Group report pages
This topic describes the pages available in group reports, most of which are very similar to device reports.
For more details, see View AFA group data, View AFA device data, and Device report pages.
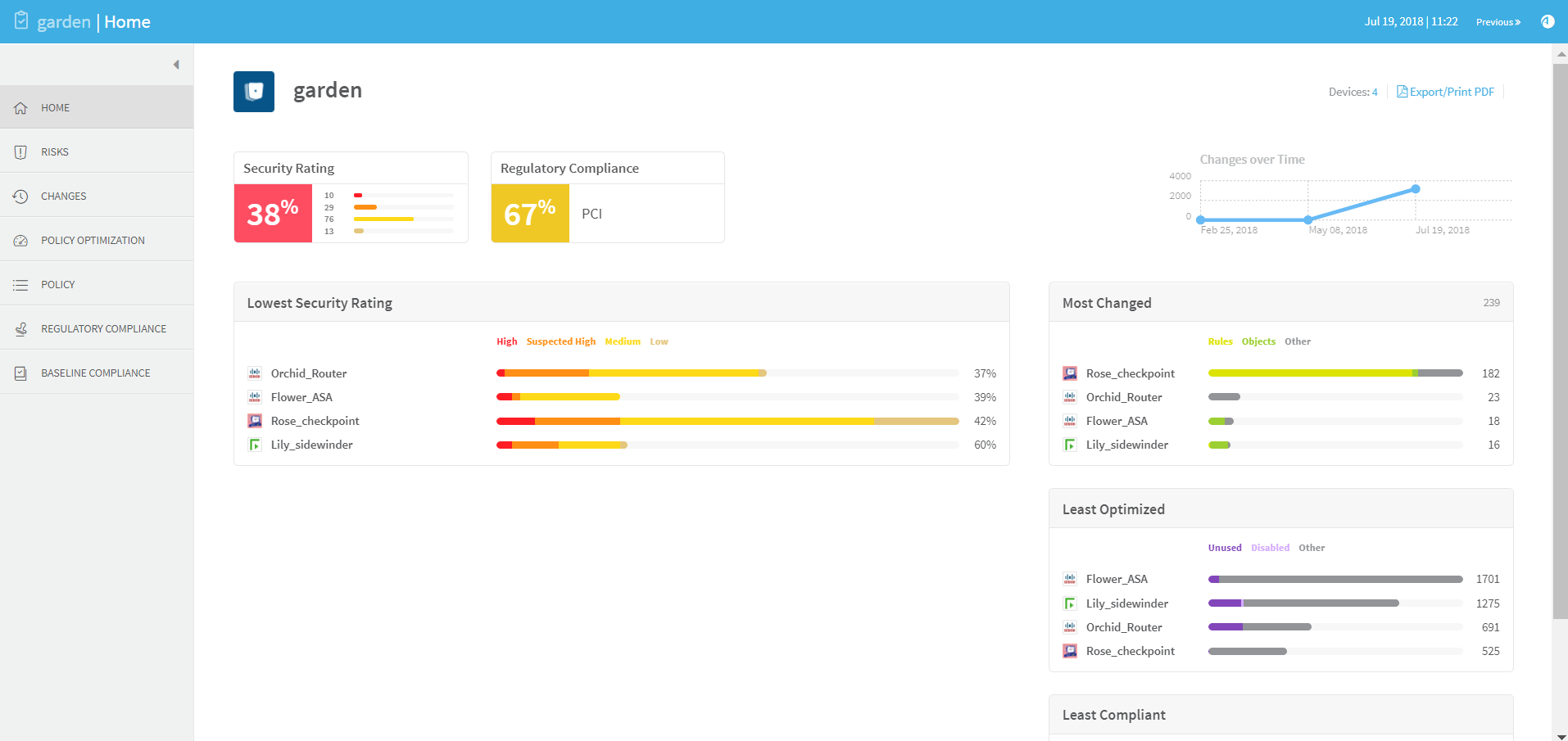
HOME page
The Home page provides an overview of the group report. The page's content depends on your AFA modules.
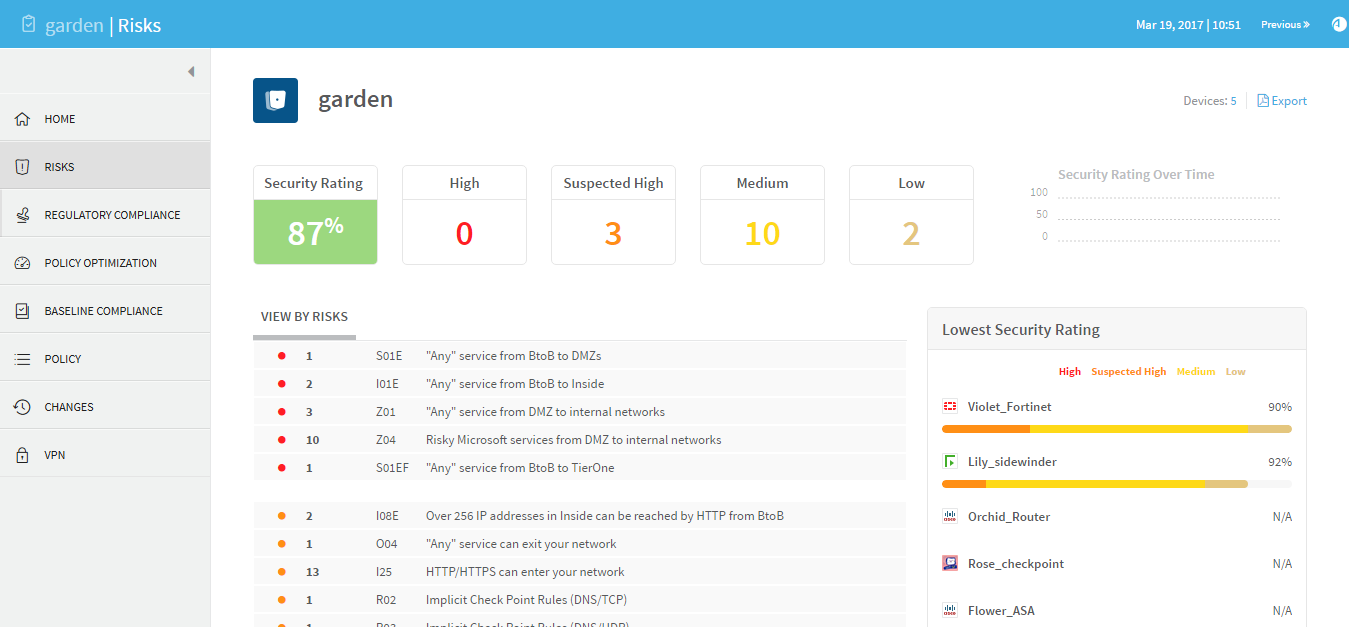
RISKS page
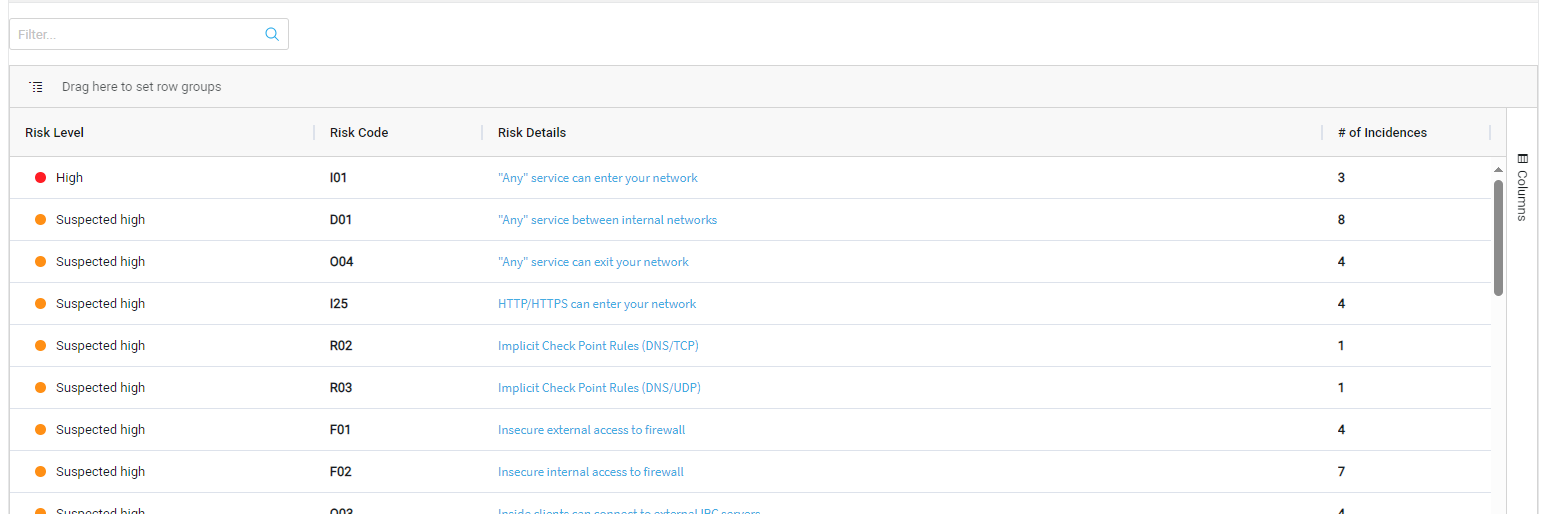
The Risks page summarizes all risk analysis findings by providing the following:
- The security rating for the group.
The security rating indicates the group's degree of compliance with security standards. A security rating of 100% indicates full compliance.
- The total number of risks in each severity category, not counting duplicates.
- A graph displaying the security rating trend.
- A list of all the group's risks, in decreasing order of severity.
The list includes a brief summary of each threat: the risk, its trigger count (the number of times it was detected), and a brief description. The New label indicates risks that were not present in the previous report.
- The ability to easily drill down to specific rules and groups.
- A visual representation of the risks per device, with each device's security rating.
To access an individual device's report, in the Lowest Security Rating area, click on the device's name.
For further information about the Risks page, see RISKS page.
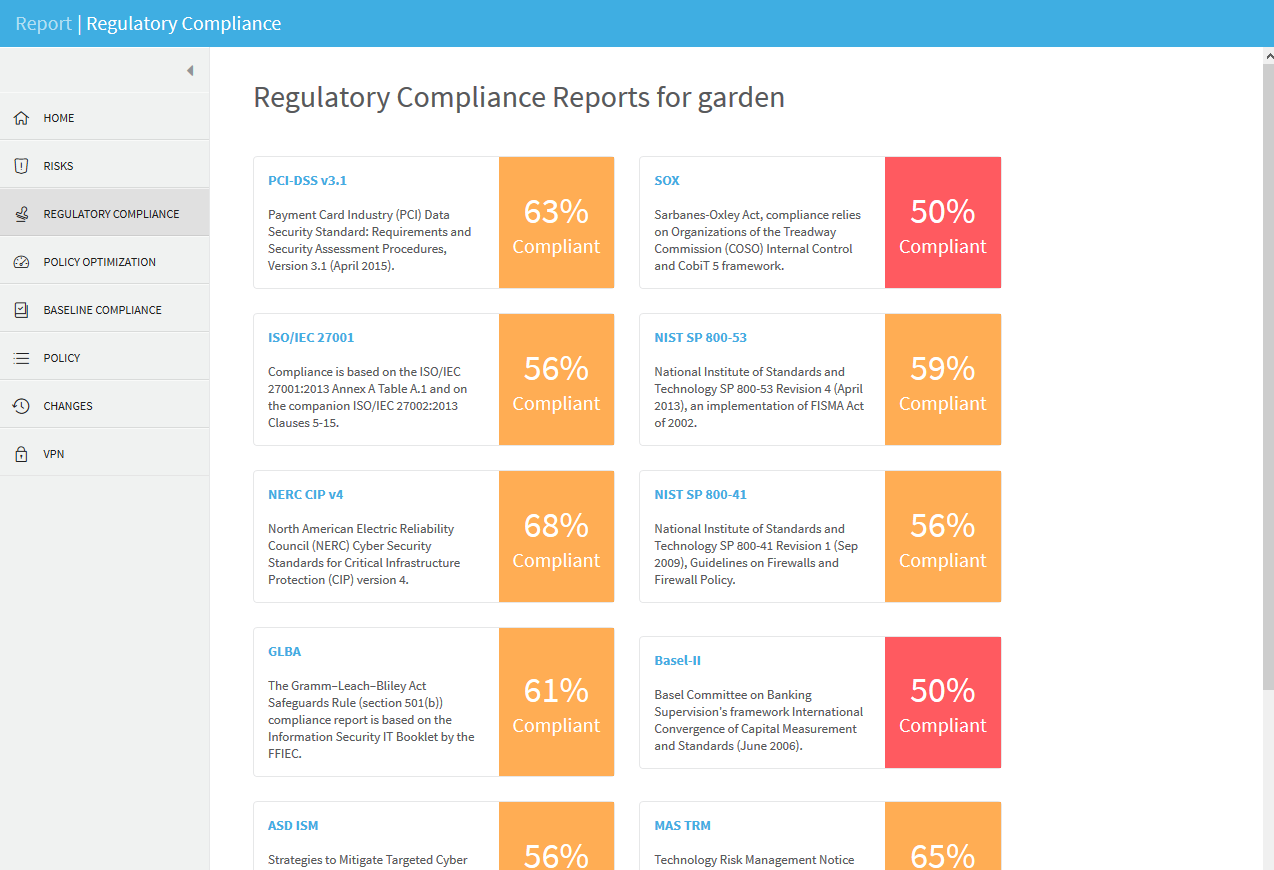
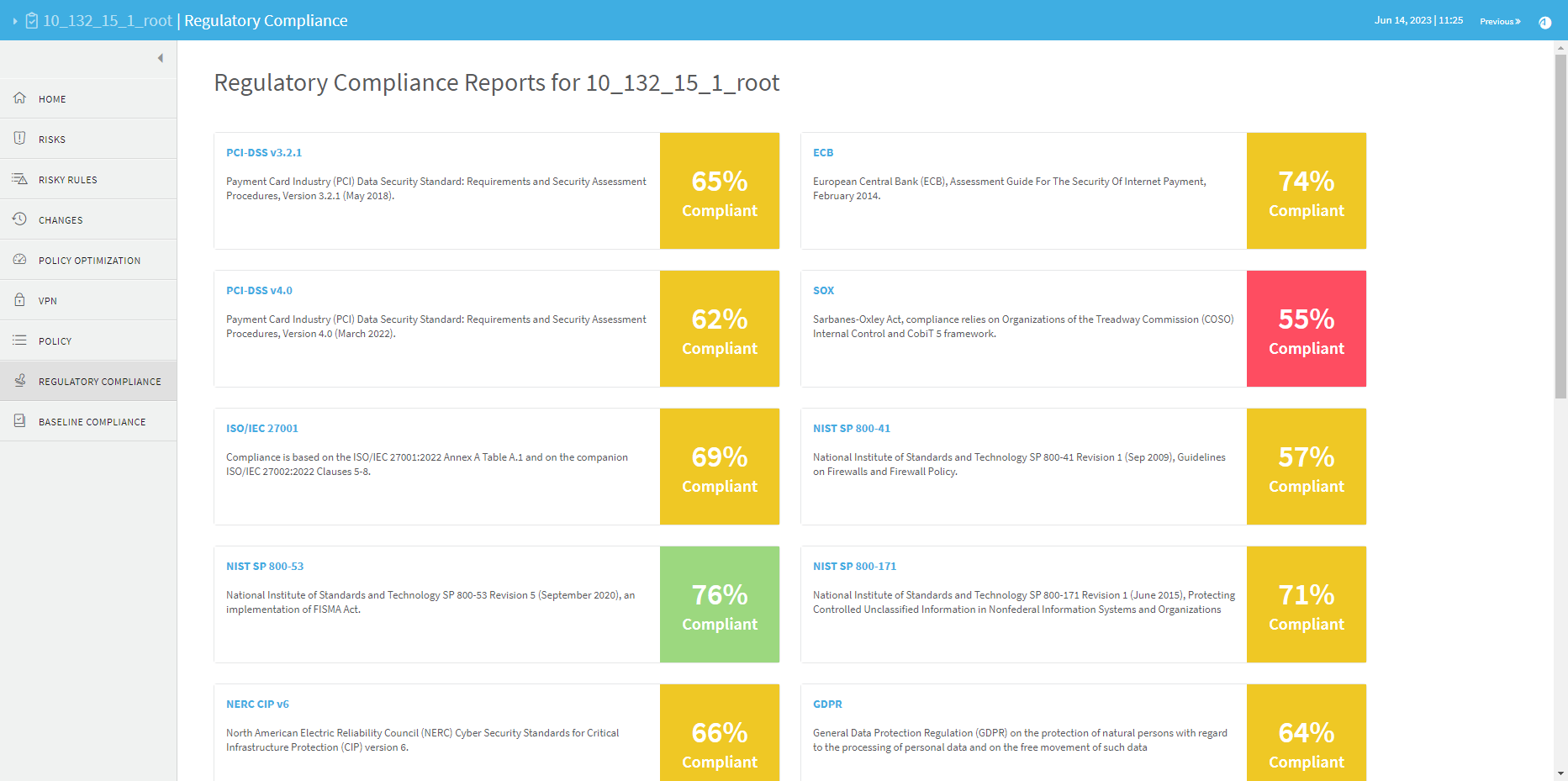
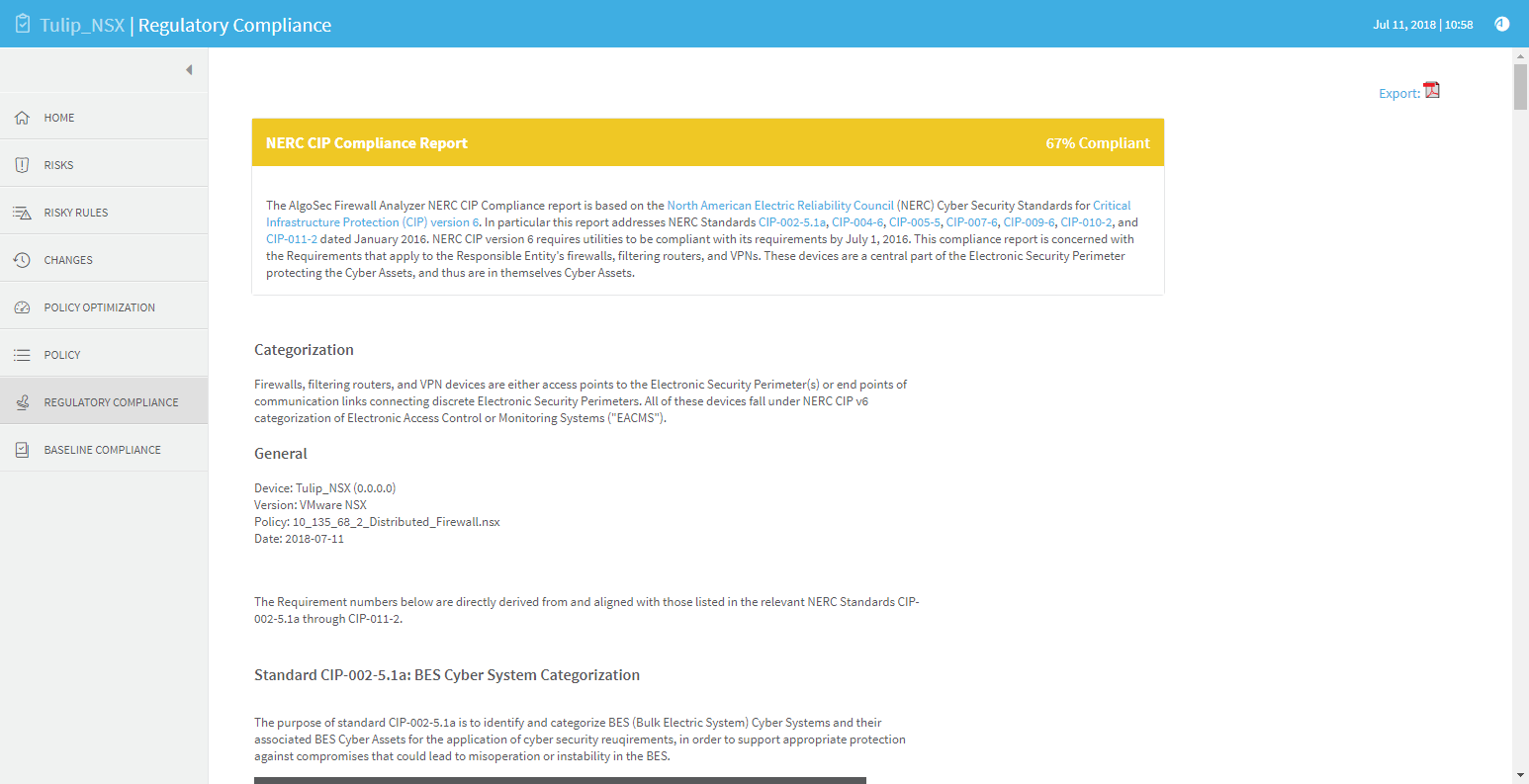
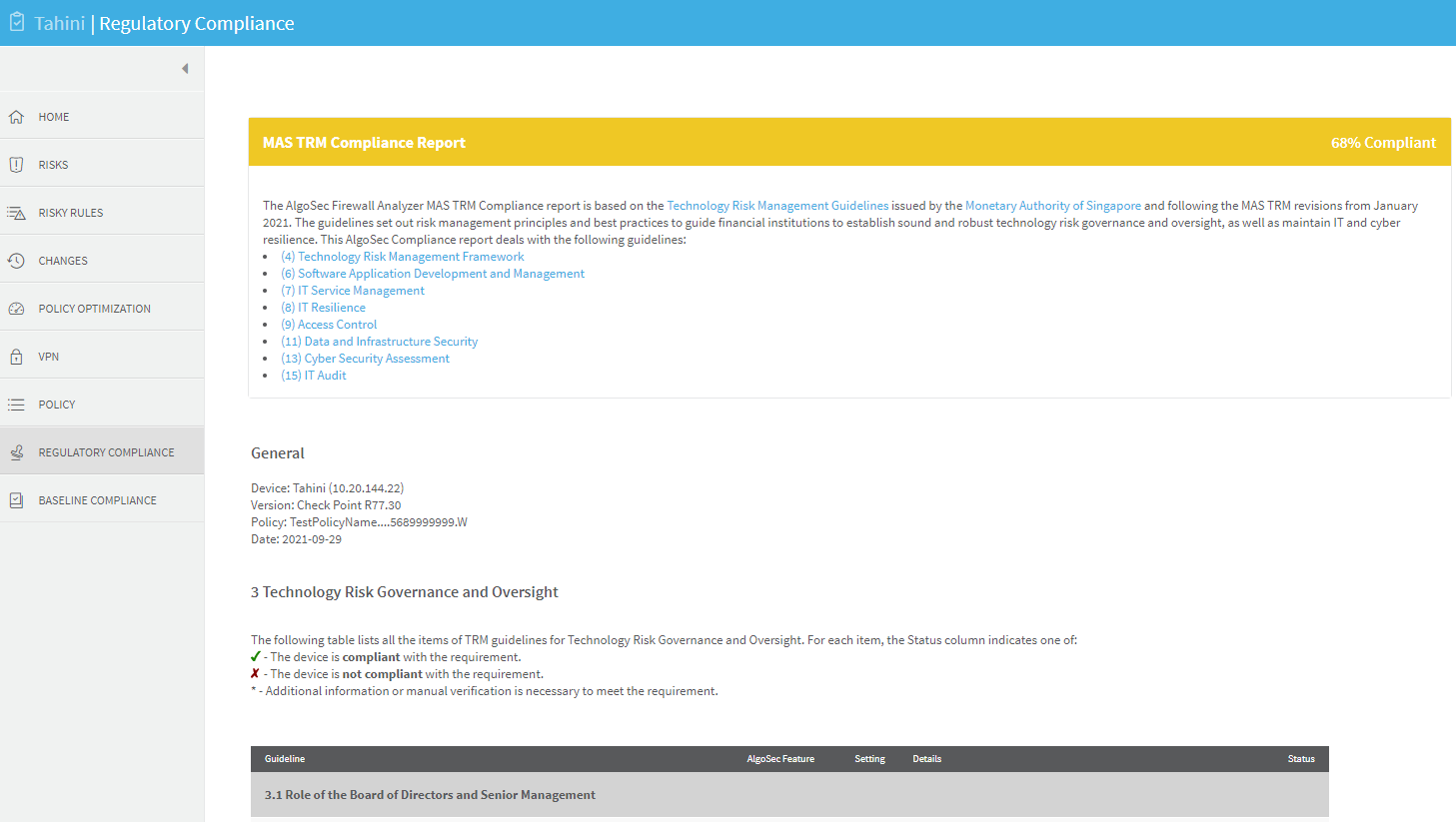
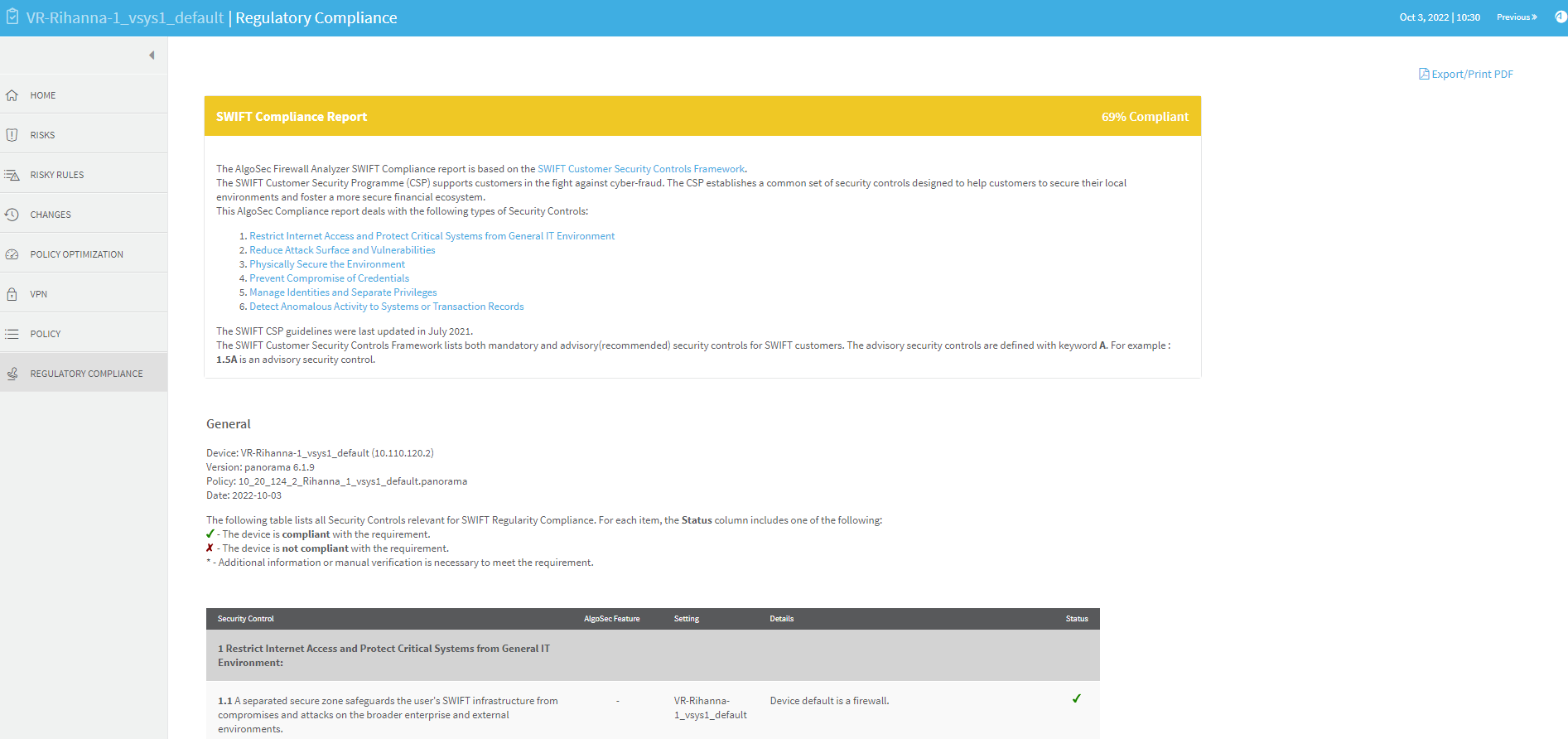
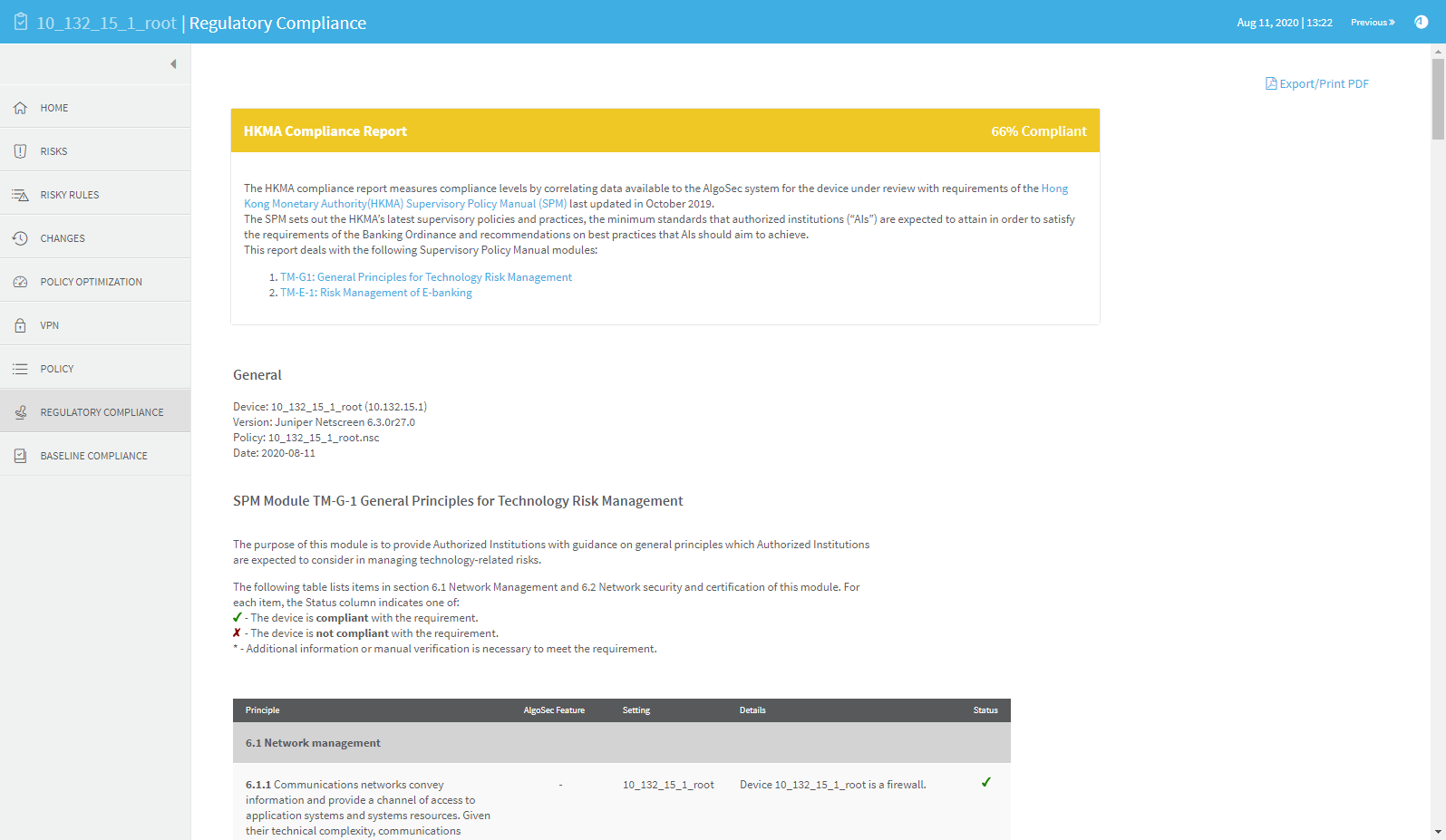
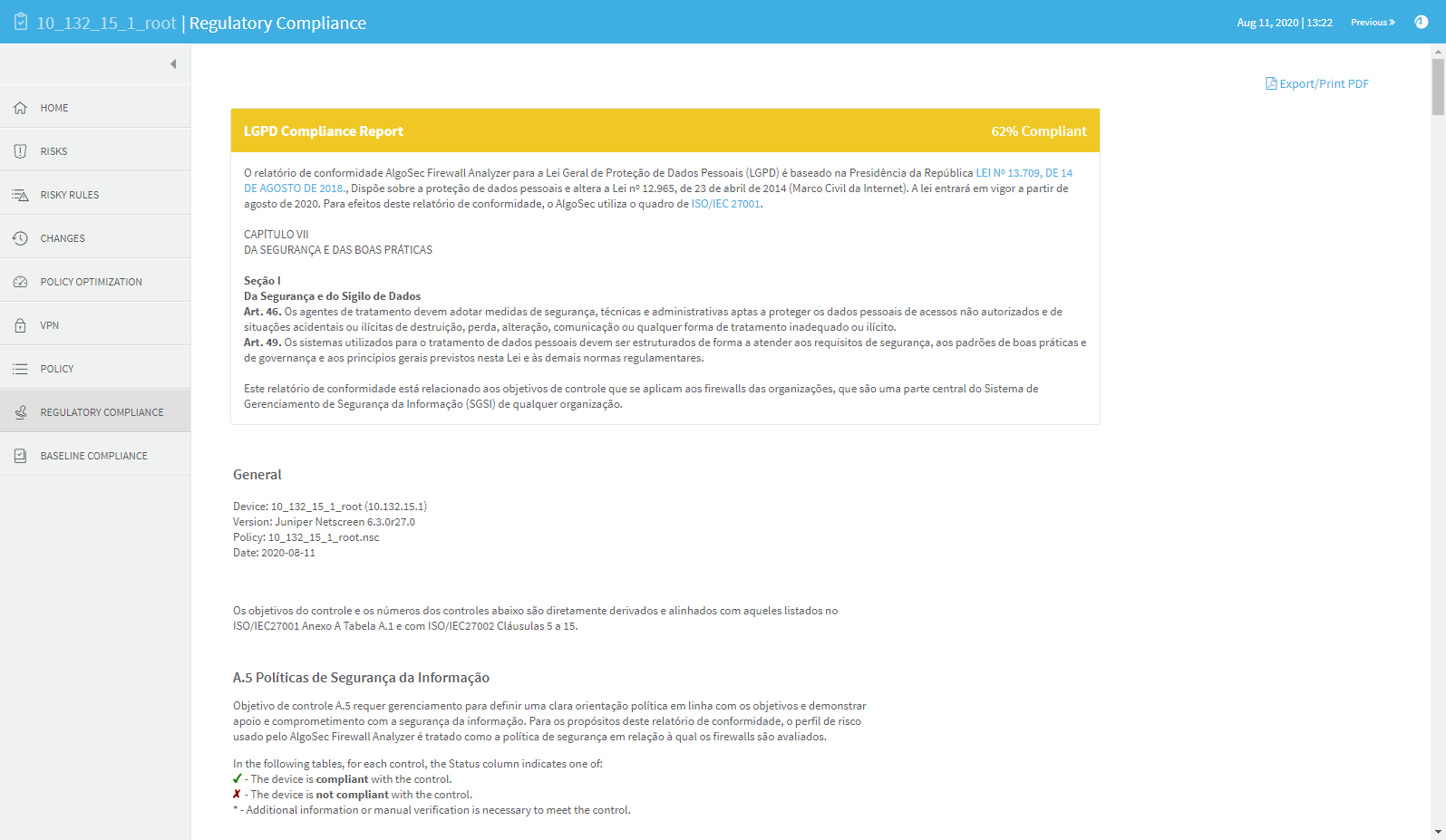
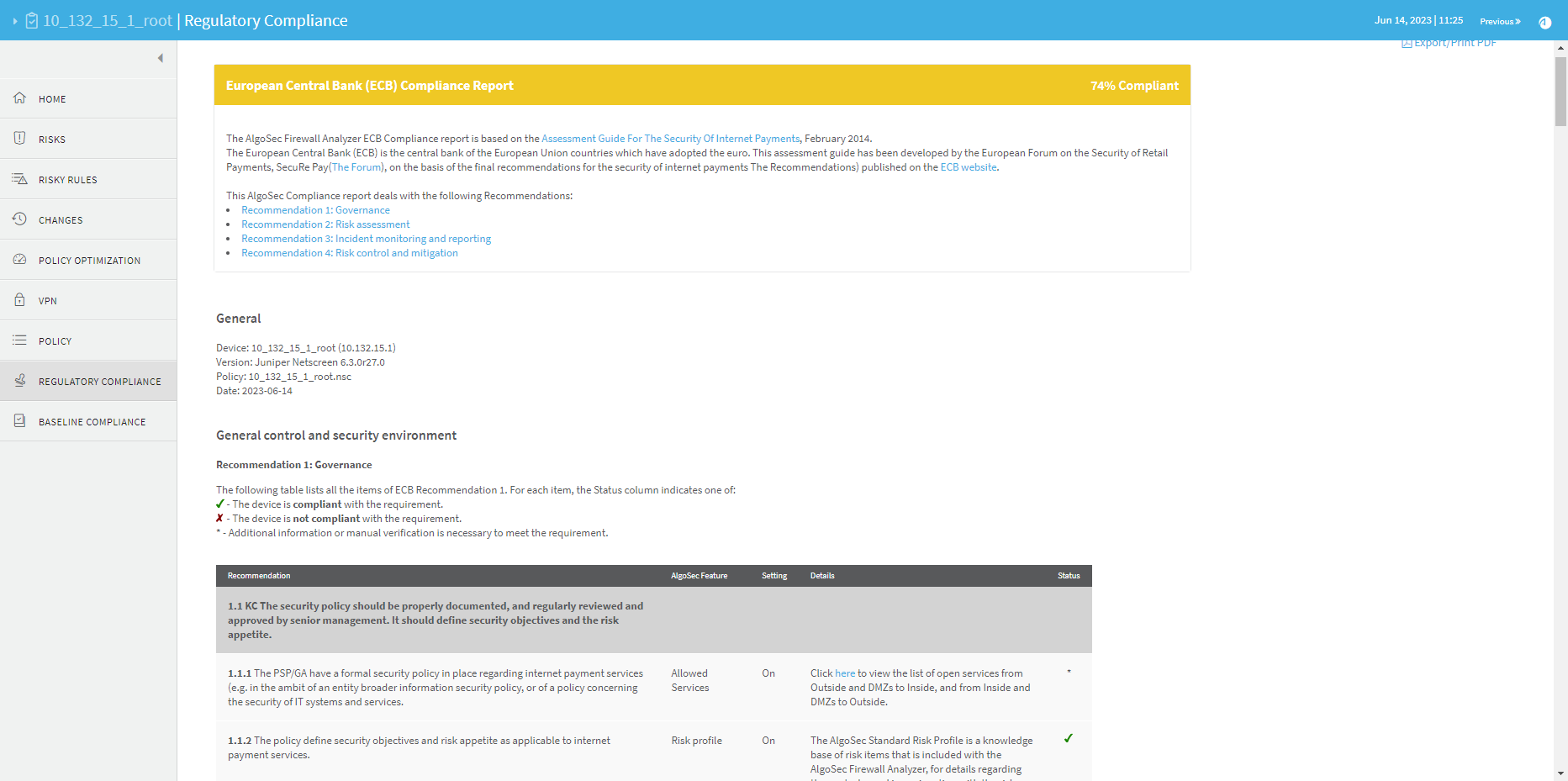
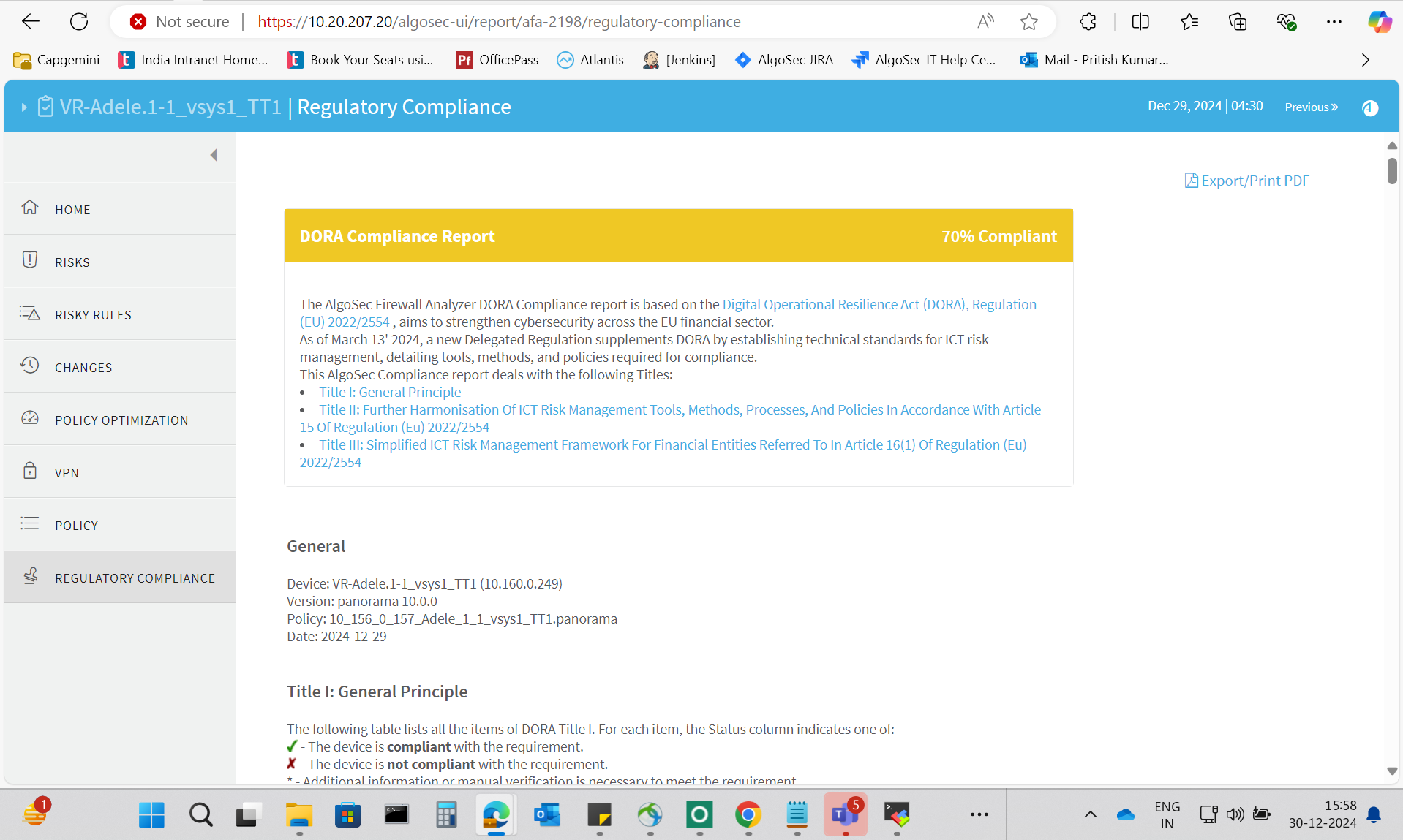
REGULATORY COMPLIANCE page
The Regulatory Compliance page includes aggregated compliance reports for the entire group.
To view a report, click the desired report's name.
The REGULATORY COMPLIANCE page includes a number of reports that describe how compliant your security policy is to specific regulatory standards.
To customize the Regulatory Compliance page, see Customize the regulatory compliance report.
Running these compliance reports will help you identify non-compliant items that require adjustment. Each report follows the reporting requirements of its standard. The reports can save you hours of work, especially when you need to prepare periodic compliance review.
The Regulatory Compliance page provides the following regulatory compliance reports:
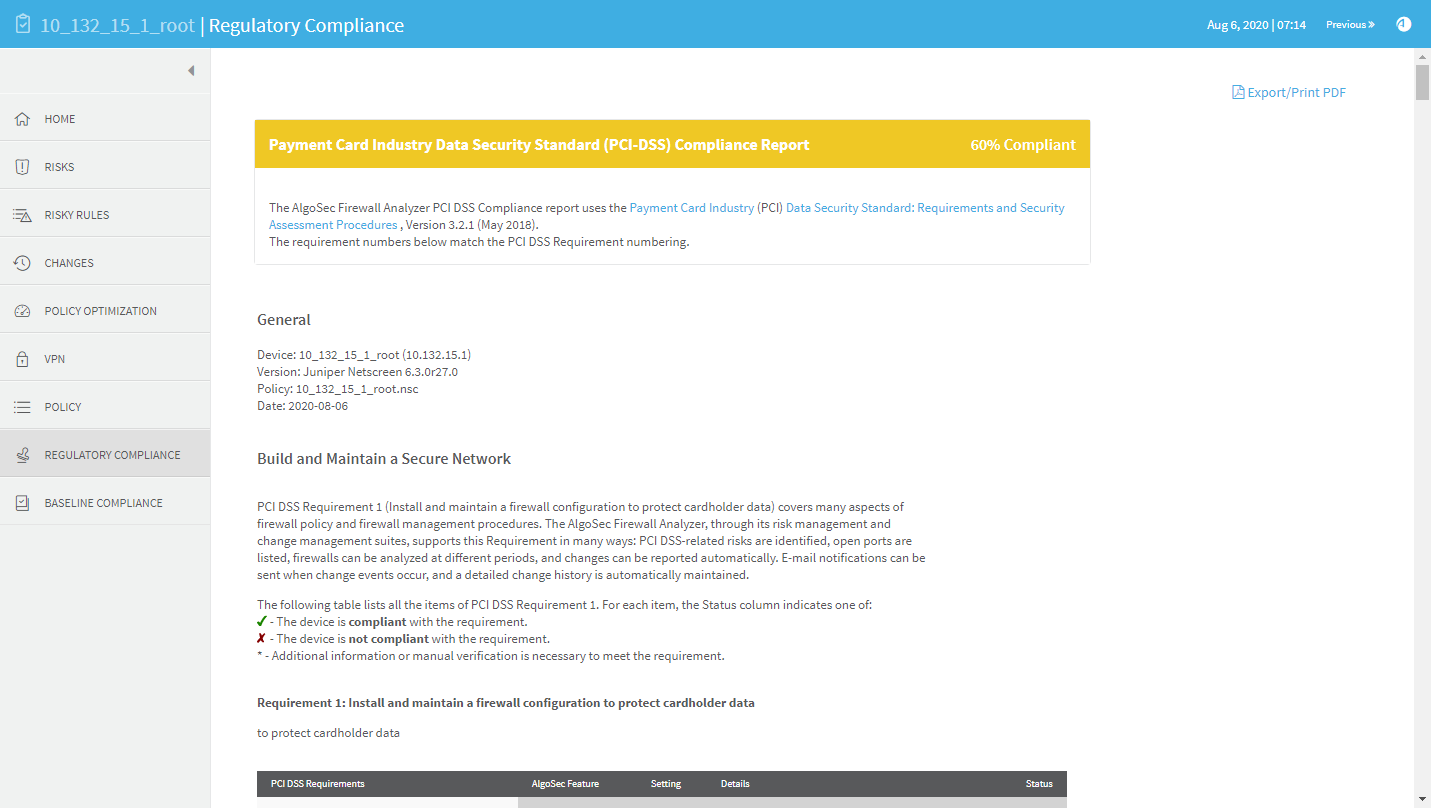
The Payment Card Industry Data Security Standard (PCI DSS) report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the PCI DSS audit procedures. Using this report can save you hours of work when you need to prepare your annual or quarterly PCI DSS compliance report.
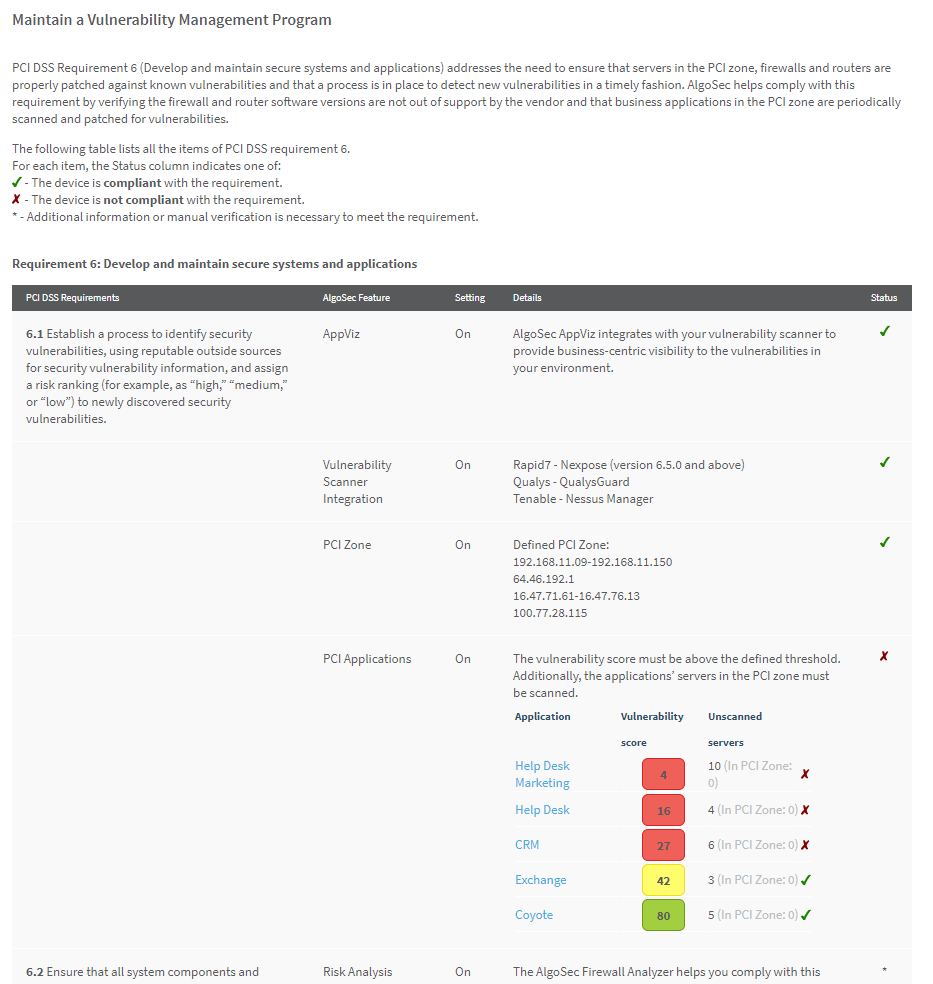
If AppViz is being used with a vulnerability scanner, this report can be configured to display the vulnerability of PCI applications. Requirement 6.1 specifies whether AppViz is being used and whether vulnerability scanner integration is enabled. If you configure the PCI zone and a vulnerability threshold in AFA, the requirement additionally specifies the servers in the PCI zone and the vulnerability assessment for all AppViz applications which intersect the PCI zone.
PCI DSS v4.0 includes many new and revised requirements. It supports the use of different technologies, such as cloud, by introducing more flexibility to the wording of requirements.
The ISO/IEC 27001 report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the ISO/IEC 27001:2022 International Standard "Information technology - Security techniques - Information security management systems - Requirements" and of the companion ISO/IEC 27002:2022 "Code of practice for information security management" International Standard.
The NERC Standards for Critical Infrastructure Protection (NERC CIP) report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the NERC Standards CIP-002-2, CIP-003-2, CIP-004-2, CIP-005-2, and CIP-007-2. Compliance with these requirements is required of all NERC-registered entities by June 30, 2010. The report addresses the requirements that apply to devices, filtering routers, and VPNs.
Note: By default, NERC version 4 is displayed. It is possible to configure AFA to simultaneously display version 3 and 4. Contact AlgoSec support for assistance.
The requirement numbers listed in the report are aligned with those specified in the relevant NERC Standards.
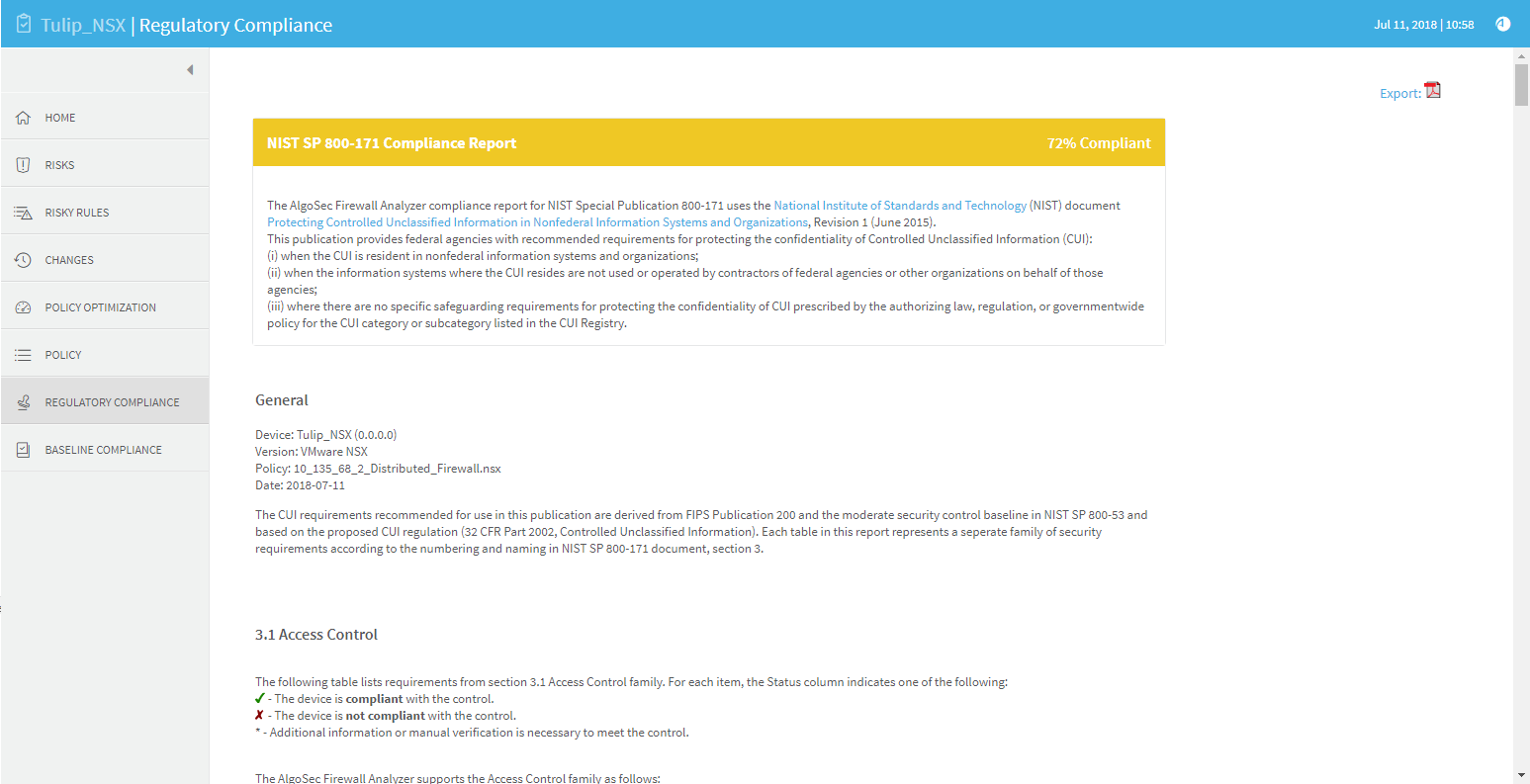
The NIST Special Publication 800-171 report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the National Institute of Standards and Technology (NIST) document Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations, Revision 1 (June 2015).
This publication provides federal agencies with recommended requirements for protecting the confidentiality of Controlled Unclassified Information (CUI):
(i) when the CUI is resident in non-federal information systems and organizations;
(ii) when the information systems where the CUI resides are not used or operated by contractors of federal agencies or other organizations on behalf of federal agencies;
(iii) where there are no specific safeguarding requirements for protecting the confidentiality of CUI prescribed by the authorizing law, regulation, or government wide policy for the CUI category or subcategory listed in the CUI Registry.
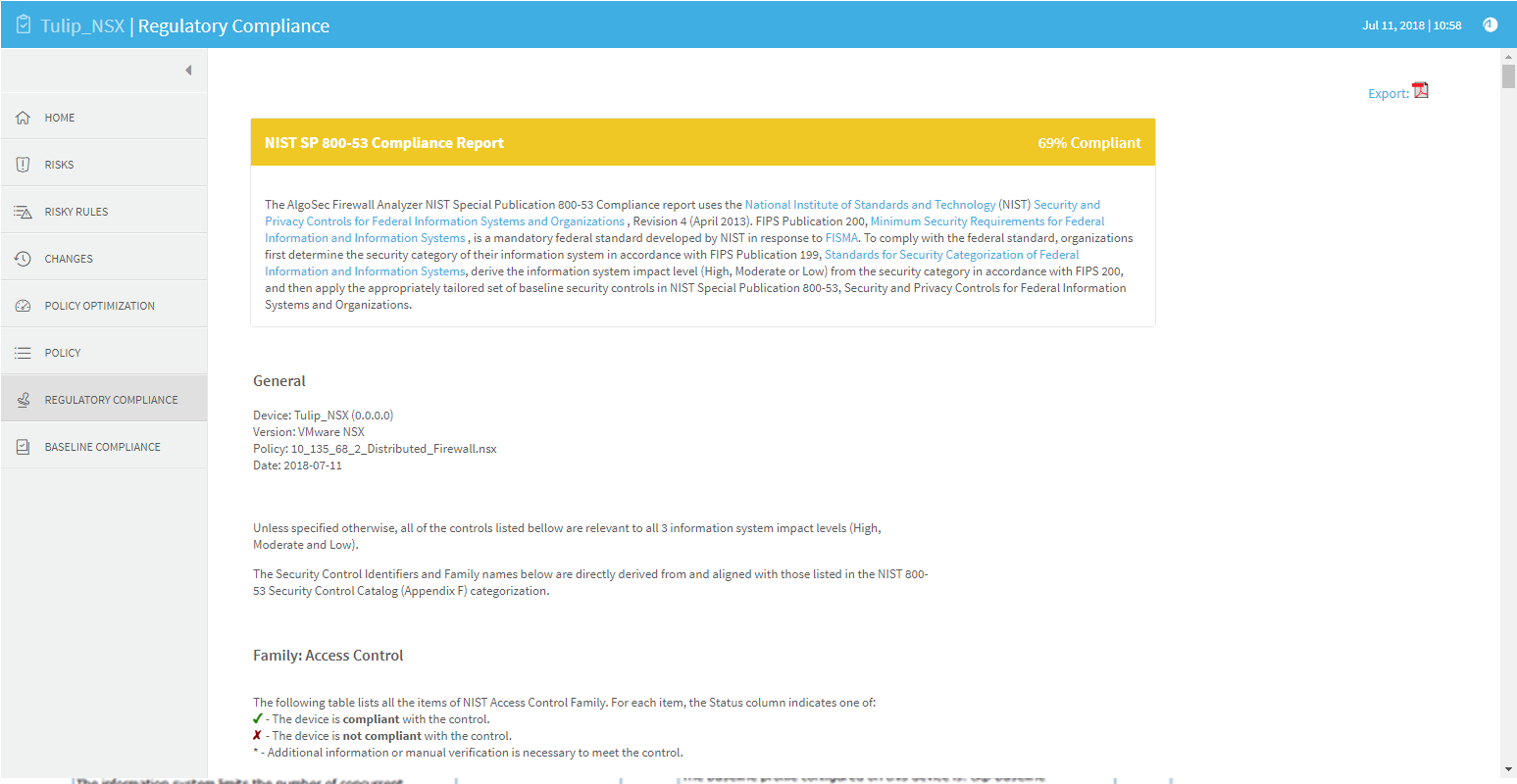
The NIST Special Publication 800-53 report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the National Institute of Standards and Technology (NIST) Security and Privacy Controls for Federal Information Systems and Organizations , Revision 4 (April 2013). FIPS Publication 200, Minimum Security Requirements for Federal Information and Information Systems , is a mandatory federal standard developed by NIST in response to FISMA. To comply with the federal standard, organizations first determine the security category of their information system in accordance with FIPS Publication 199, Standards for Security Categorization of Federal Information and Information Systems, derive the information system impact level (High, Moderate or Low) from the security category in accordance with FIPS 200, and then apply the appropriately tailored set of baseline security controls in NIST Special Publication 800-53, Security and Privacy Controls for Federal Information Systems and Organizations.
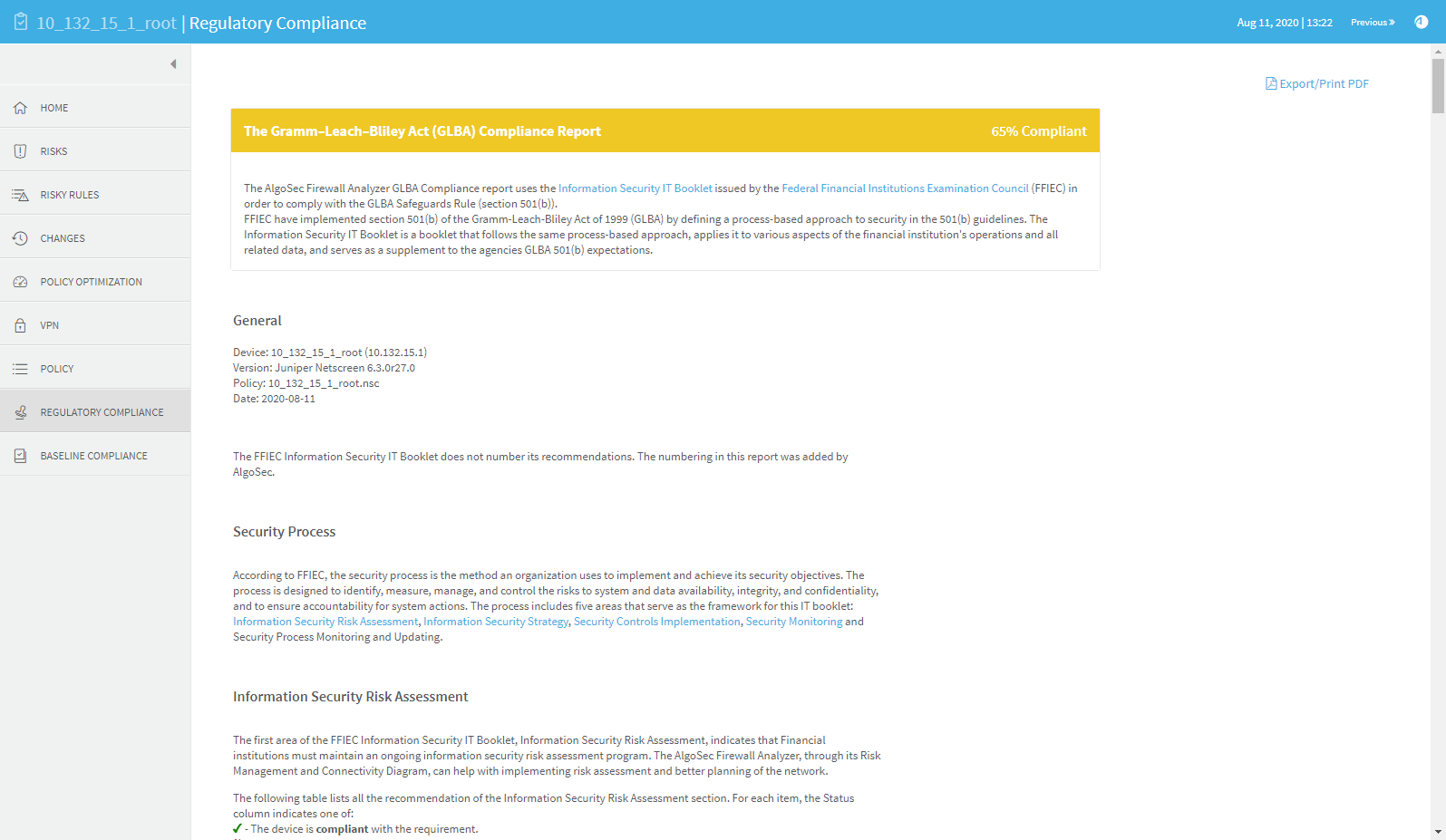
The Gramm–Leach–Bliley Act (GLBA) report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the Information Security IT Booklet issued by the Federal Financial Institutions Examination Council (FFIEC) in order to comply with the GLBA Safeguards Rule (section 501(b)).
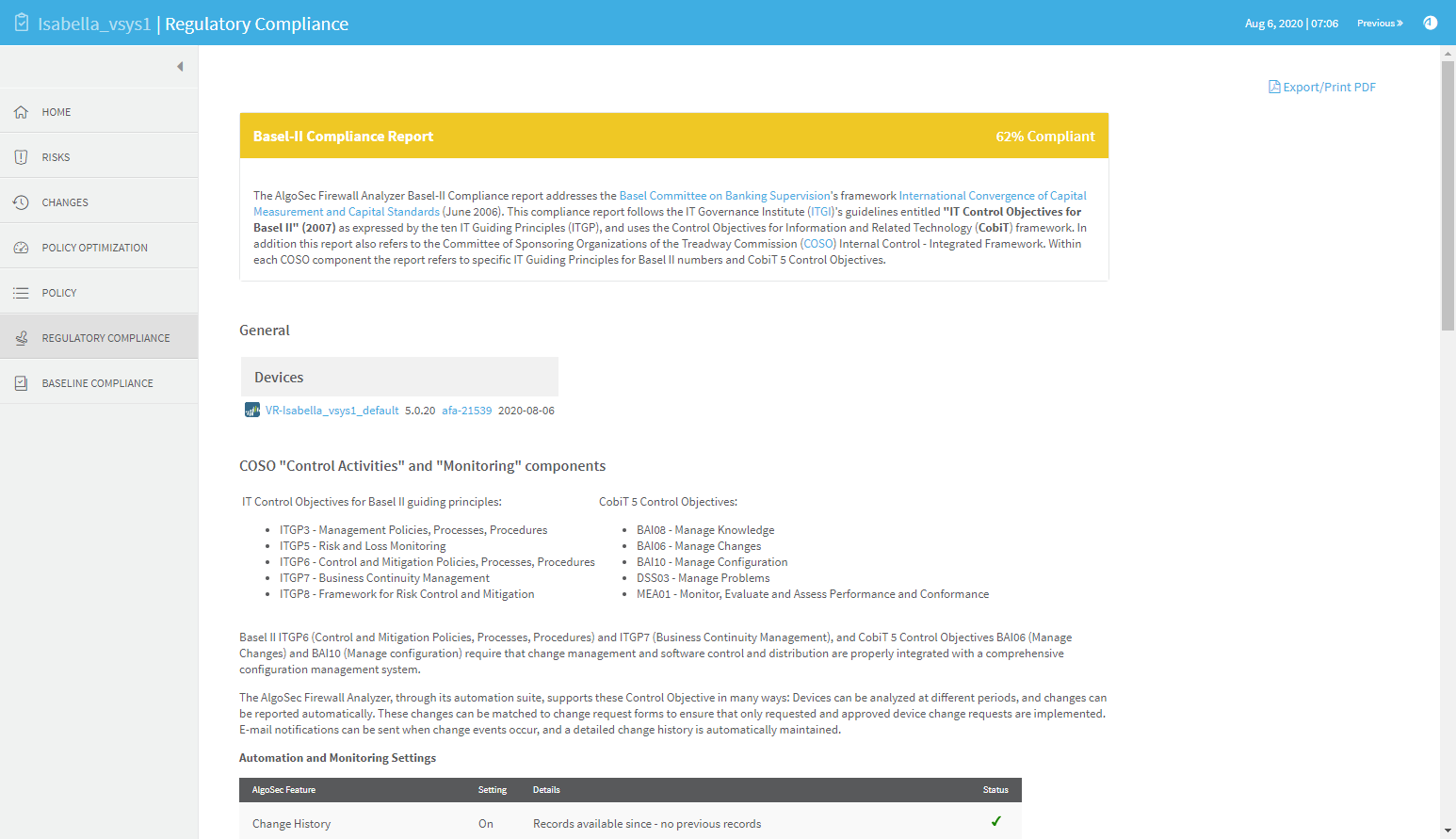
The Basel-II report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the Basel Committee on Banking Supervision's framework International Convergence of Capital Measurement and Capital Standards (June 2006). It follows the IT Governance Institute (ITGI)'s guidelines entitled "IT Control Objectives for Basel II" (2007) as expressed by the ten IT Guiding Principles (ITGP), and uses the Control Objectives for Information and Related Technology (CobiT) framework. In addition this report also refers to the Committee of Sponsoring Organizations of the Treadway Commission (COSO) Internal Control - Integrated Framework. Within each COSO component the report refers to specific IT Guiding Principles for Basel II numbers and CobiT 5 Control Objectives.
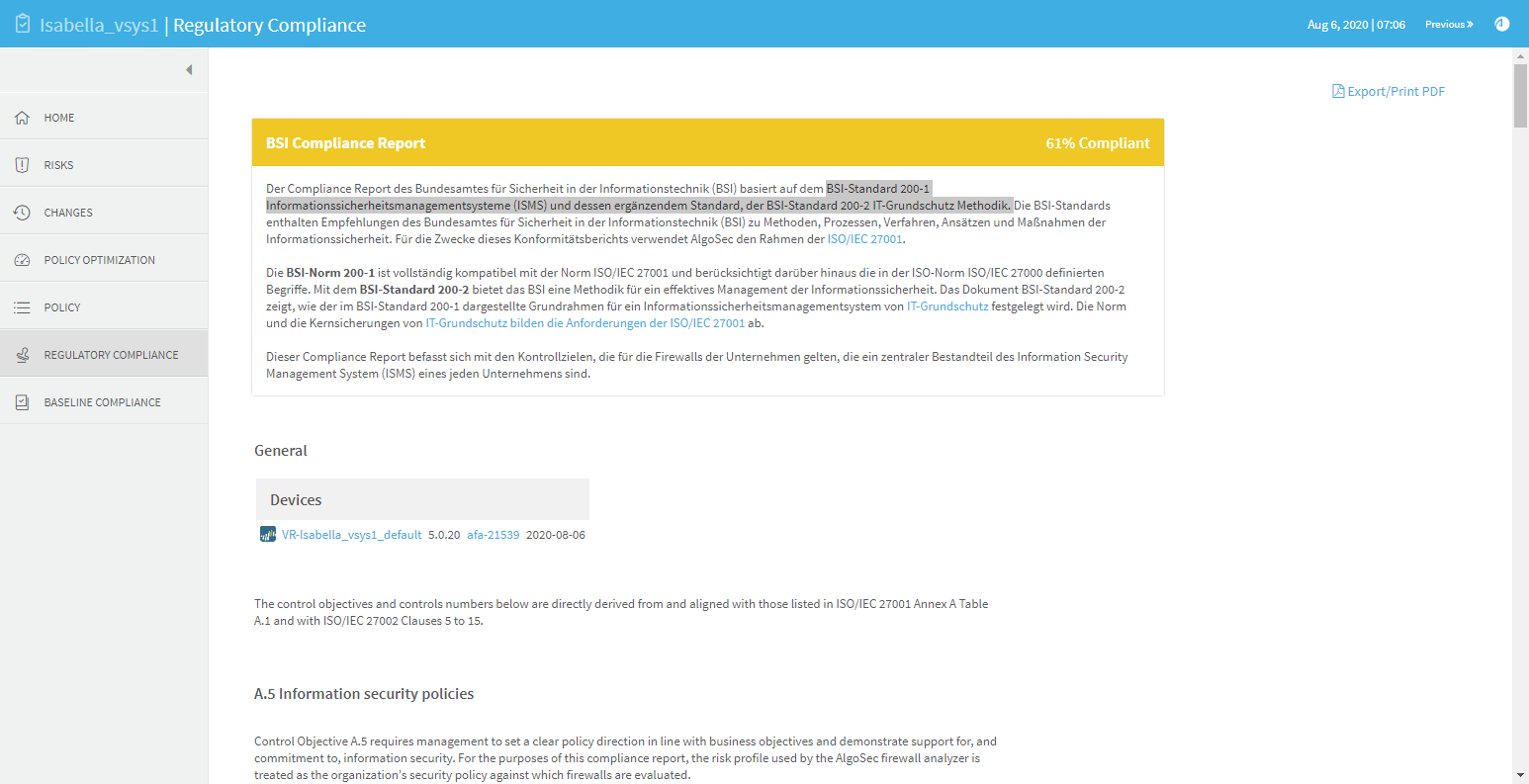
The BSI 200 report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the BSI standard 200-1 information security management systems (ISMS) and its supplementary standard, the BSI standard 200-2 IT-Grundschutz methodology (BSI-Standard 200-1 Informationssicherheitsmanagementsysteme (ISMS) und dessen ergänzendem Standard, der BSI-Standard 200-2 IT-Grundschutz Methodik).
Like the AlgoSec Sarbanes-Oxley report, the Financial Instruments and Exchange Law (Japan) report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the CobiT 5 control objectives, in the Japanese language. Use this report to learn how well you are doing, and to present to your auditors as needed.
Note: If you see the titles of the risk items in English it means that you are using the English language pack.
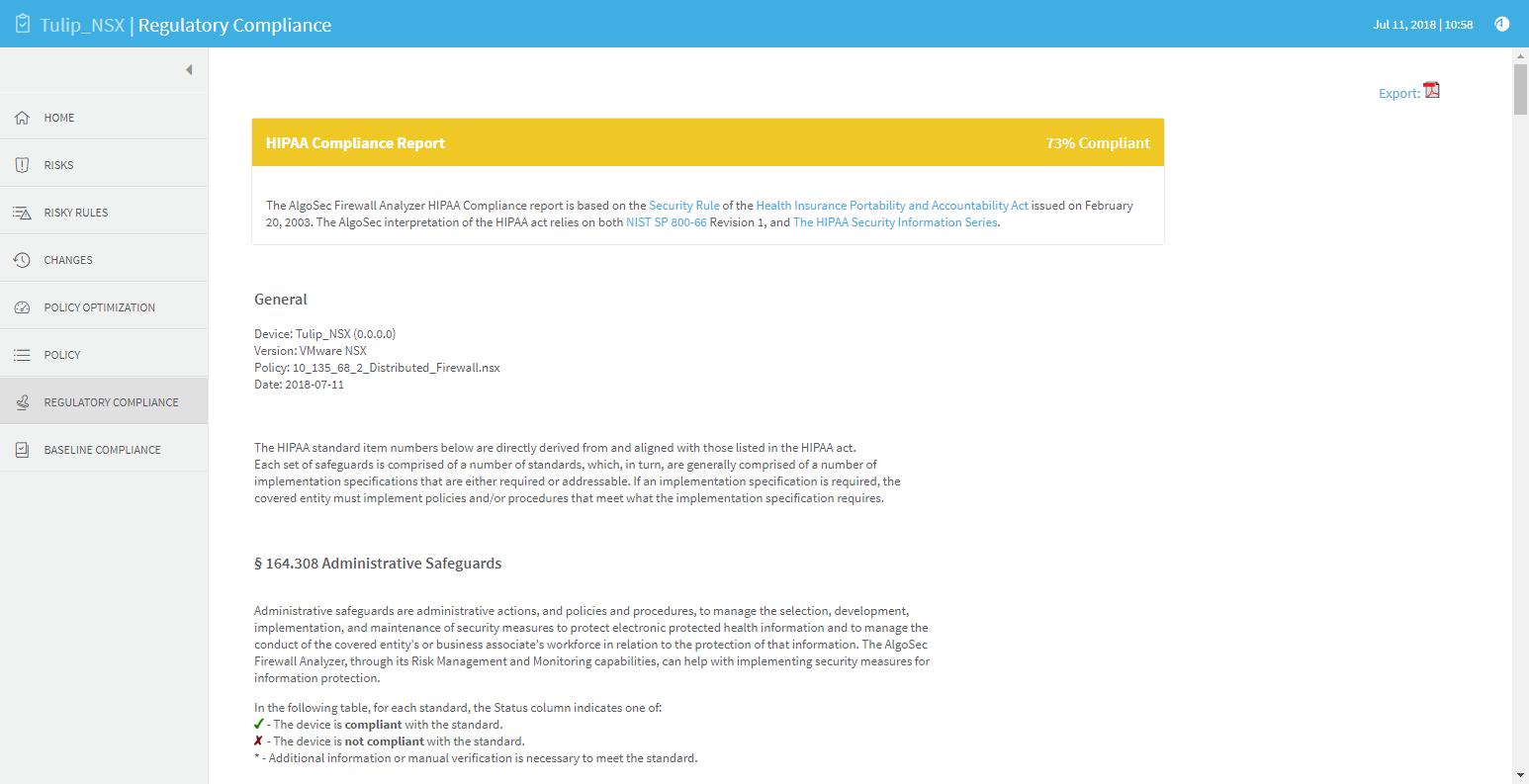
The HIPAA report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the Security Rule of the Health Insurance Portability and Accountability Act issued on February 20, 2003. The AlgoSec interpretation of the HIPAA act relies on both NIST SP 800-66 Revision 1, and The HIPAA Security Information Series.
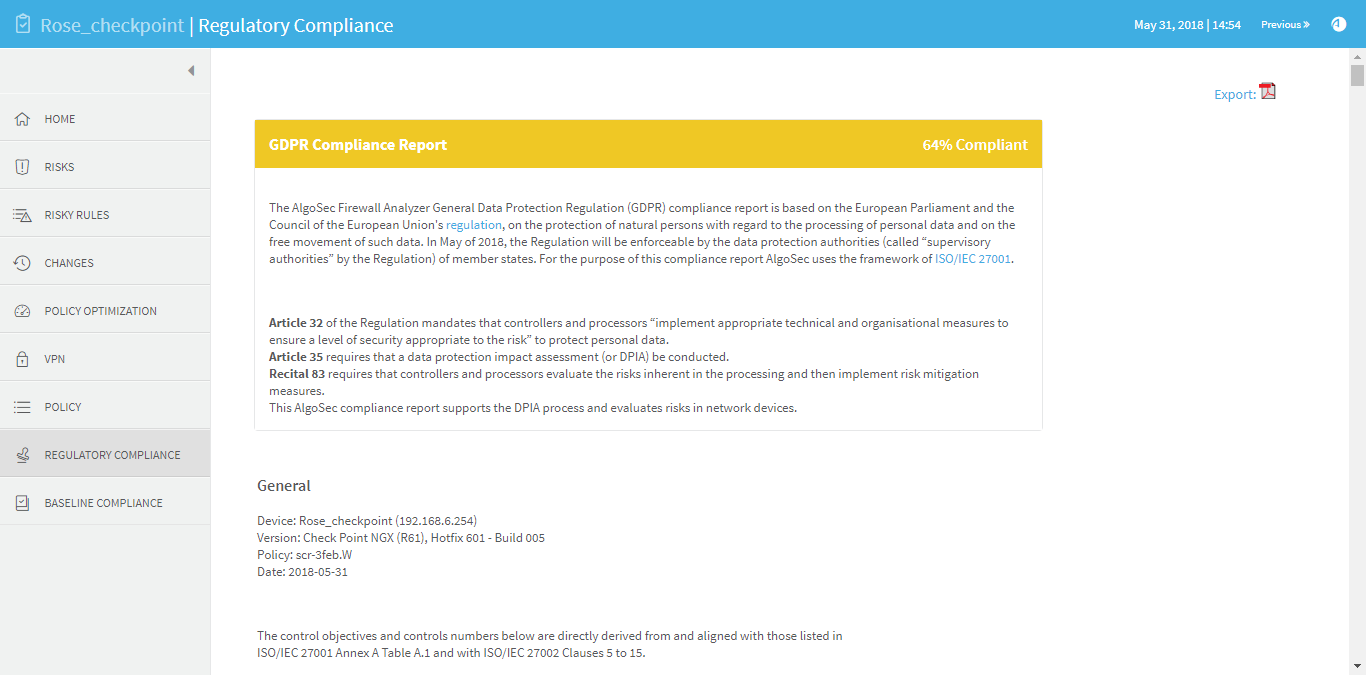
The General Data Protection Regulation (GDPR) report measures compliance levels by correlating data available to the AlgoSec system for the device under review with requirements of the European Parliament and the Council of the European Union's regulation, on the protection of natural persons with regard to the processing of personal data and on the free movement of such data. For the purpose of this compliance report, AlgoSec uses the framework of ISO/IEC 27001.
The AlgoSec Firewall Analyzer ECB Compliance report is based on the Assessment Guide For The Security Of Internet Payments, February 2014.
The European Central Bank (ECB) is the central bank of the European Union countries which have adopted the euro. This assessment guide has been developed by the European Forum on the Security of Retail Payments, SecuRe Pay (The Forum), on the basis of the final recommendations for the security of internet payments
The DORA compliance report measures compliance levels by correlating data available to the AlgoSec system for the device under review with the operational and cybersecurity requirements set forth in the Digital Operational Resilience Act of 13 March 2024. DORA applies across all European Union (EU) member states, ensuring a harmonized approach to operational resilience in the financial sector.
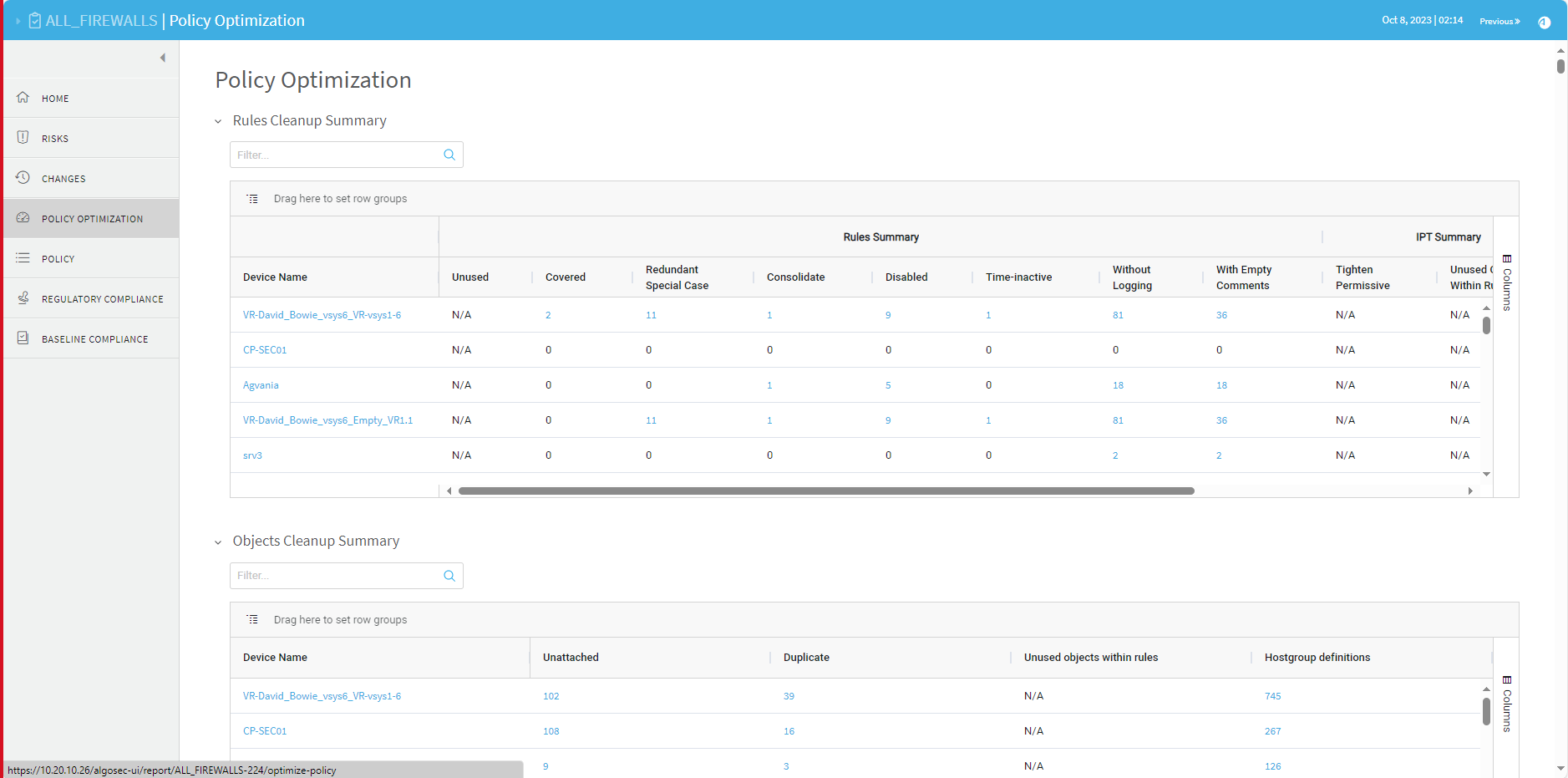
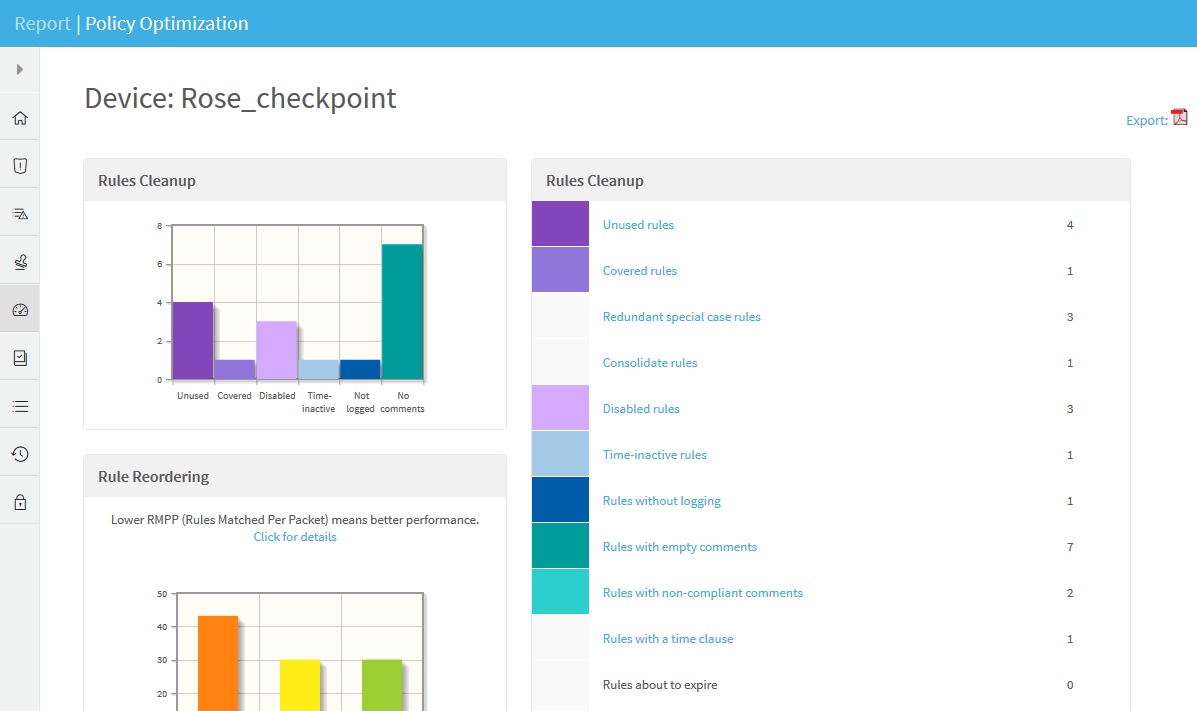
POLICY OPTIMIZATION page
The Policy Optimization page enables you to optimize your policy, by identifying inefficient rules and objects. The top of the page displays Rules Cleanup Summary and Objects Cleanup Summary tables with details on all relevant devices.
Click on a number in the summary tables to view the corresponding report in a new browser tab.
-
To filter
-
Based on data contained in all columns:
-
Type in the Filter field.
-
Use spaces to add additional filters (for example, filter1 filter2 filter3).
-
-
Based on data in one column:

-
Hover over the column header of the column to filter.
-
Click
 to bring up the filter popup dialog.
to bring up the filter popup dialog. -
Use the drop-down to select the filter operation (contains, not contains, starts with, ends with, etc.).
-
Enter the text to filter by the filter details.
-
-
-
To modify the table
-
Sort by column
-
Click the column header of the column you want to sort. Each click toggles between low to high, high to low, and default sorting.
-
-
Rearrange columns
-
Option 1
-
Drag column headers to move the column.
-
-
Option 2
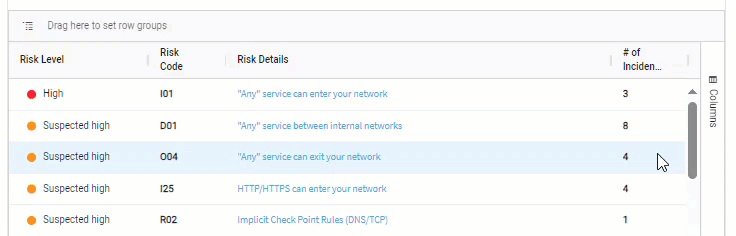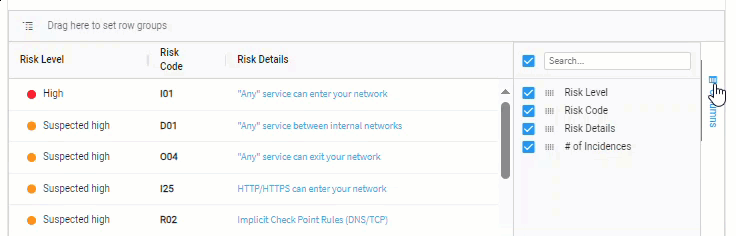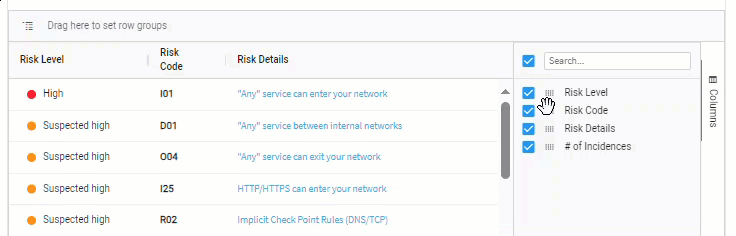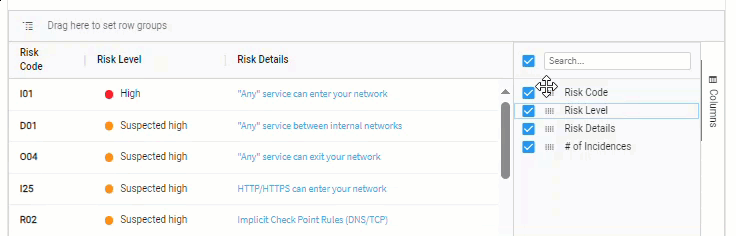
-
Click on Columns, located on the far right of the list.
-
Drag
 next to the column names to rearrange their order in the list.
next to the column names to rearrange their order in the list.
-
-
-
Pin columns
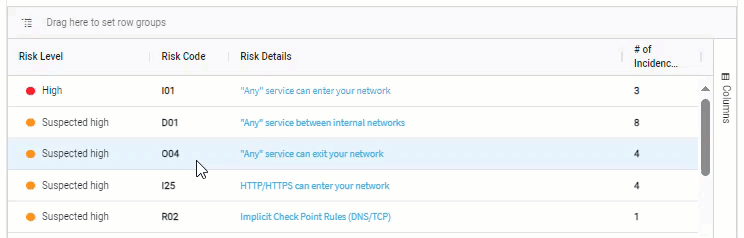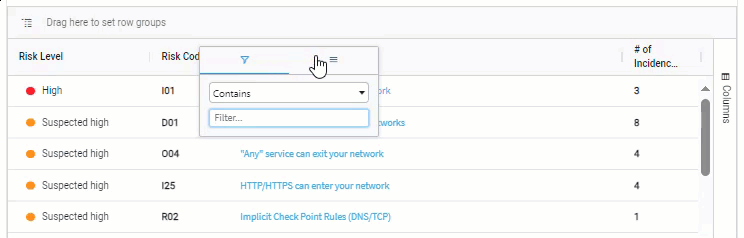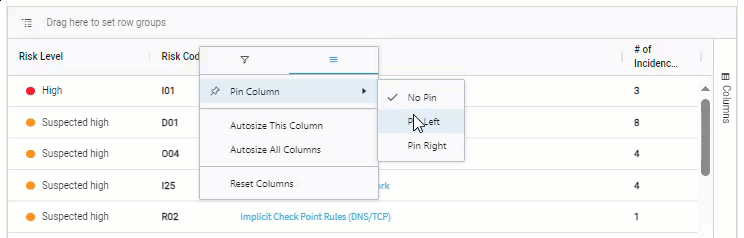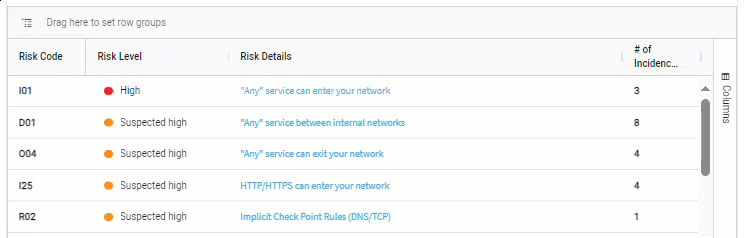
-
Hover over the column header of the column to pin.
-
Click
 to bring up the filter popup dialog.
to bring up the filter popup dialog. -
On the popup, click
 to show column options.
to show column options. -
Hover over Pin Column to display the pin options.
-
Click on one of the pin options: No Pin, Pin Left, or Pin Right.
-
-
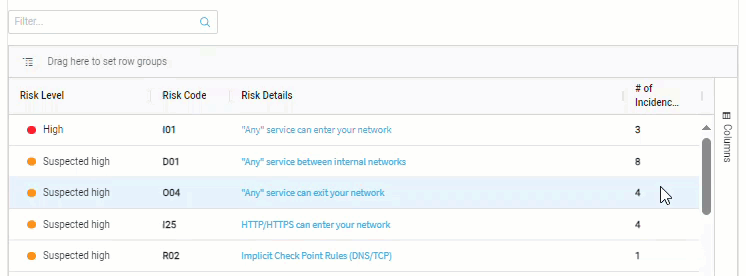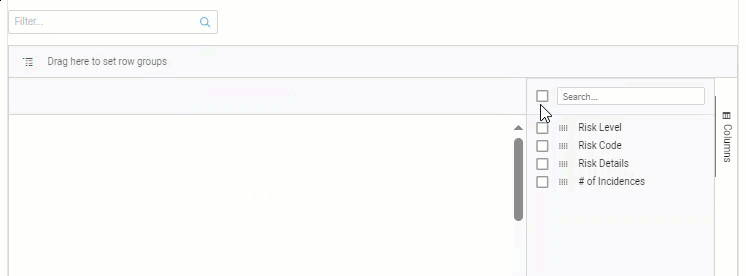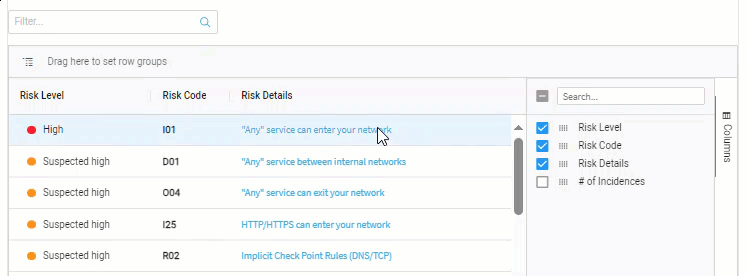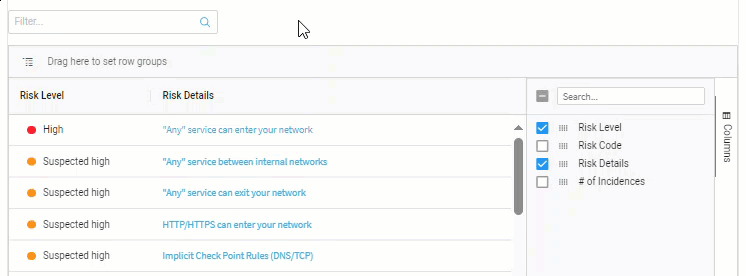
Show / hide columns
-
Click on Columns, located on the far right of the list.
-
Use the checkboxes beside each column name to select which columns to show / hide.
-
Click the checkbox next to the column search field to show / hide all of the columns.
Note: You can also hide columns by clicking on a column header and dragging it outside of the list.
-
-
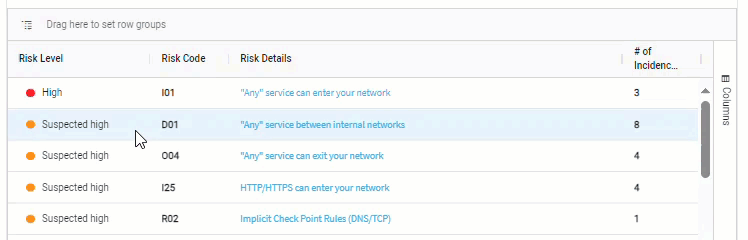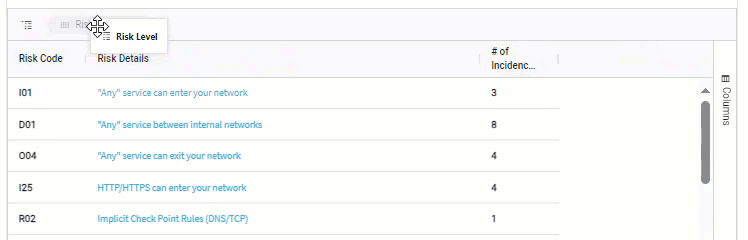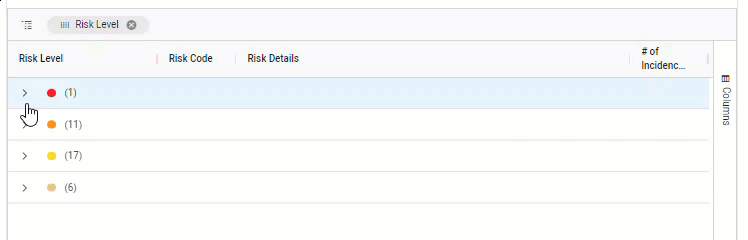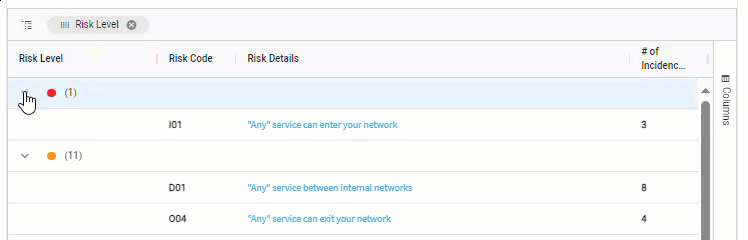
Group by column.
For example, when data includes risk severity, you can group by the severity column to see the total number of risks at each severity level.
-
Option 1
-
Drag column headers into the Drag here to set row groups section.
-
-
Option 2
-
Hover over the column header of the column you want to group.
-
Click
 to bring up the filter popup dialog.
to bring up the filter popup dialog. -
Click to group / ungroup by the column.
-
-
Option 3
-
Click on Columns, located on the far right of the list.
-
Right click on the name of the column header.
-
Click to group / ungroup by the column.
-
-
-
Policy optimization for each device in the group appears below the summary tables.
For more information on using this page, see POLICY OPTIMIZATION page.
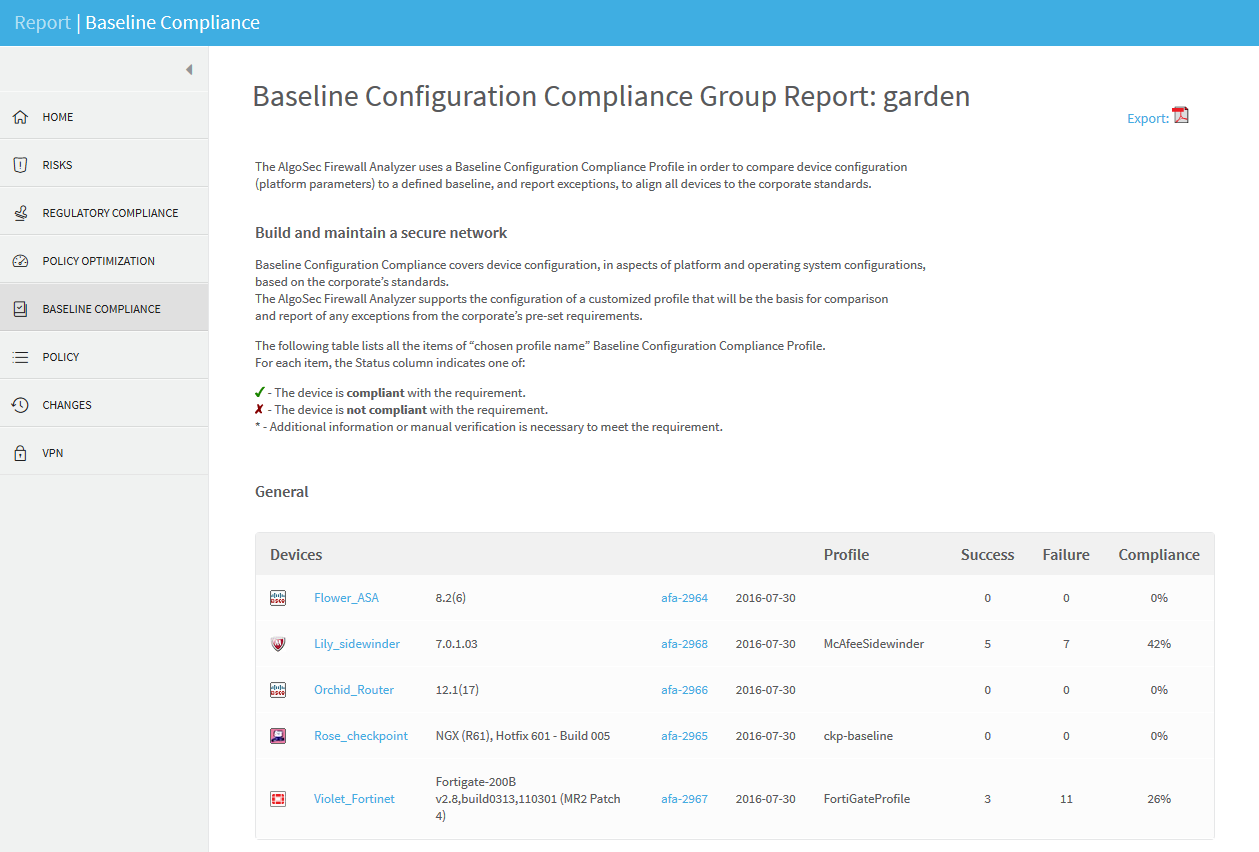
BASELINE COMPLIANCE page
The Baseline Compliance page includes aggregated baseline compliance reports for the entire group.
For further information, see BASELINE COMPLIANCE page)
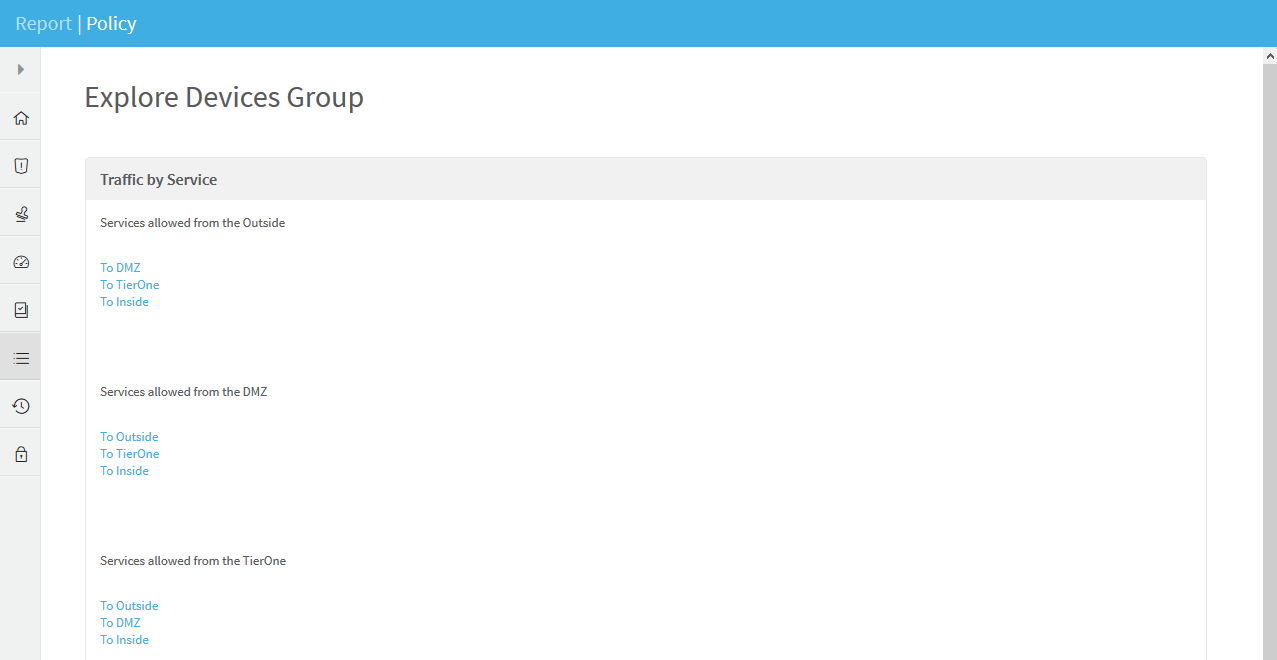
POLICY page
The Policy page enables you to drill down into various aspects of your policy.
For further information, see POLICY Page.
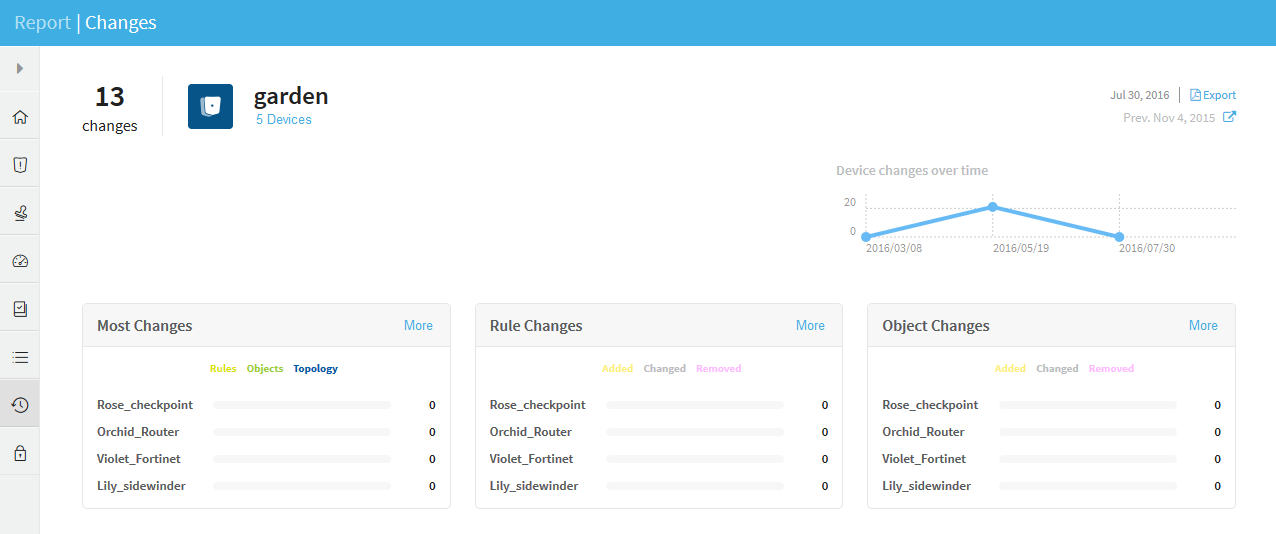
CHANGES page
The Changes page provides detailed information about changes to the devices in the group, over the whole history of AFA reports for the group.
For further information, see CHANGES page.