Configure advanced AppViz properties
This topic describes the advanced configuration properties available in the AppViz.
 Manage AppViz advanced configuration properties
Manage AppViz advanced configuration properties
AppViz advanced configuration properties are managed by AppViz Advanced Configuration APIs.
 Access and edit the user.properties file
Access and edit the user.properties file
The user.properties AppViz configuration file is located on the AppViz server, at /home/bflow/config/user.properties.
Do the following:
- Open a terminal and log in to the AppViz server as user root.
- Browse to an open /home/bflow/config/user.properties for editing.
-
Add or edit configuration parameters as needed. If the parameter is missing, add the parameter name and value on a new line.
For details, see Advanced AppViz property reference.
- When you're finished, save the file and restart AppViz. For more details, see Restart AppViz.
Advanced AppViz property reference
This section describes the advanced AppViz properties available
Integer. The number of advance search results initially displayed on an advanced search results page.
For example, the following sets the number of advanced search results initially displayed to 15:
advanced-search.results.page_size=15
String. Use to define partially routed traffic as Allowed (the default flow behavior defines partially routed traffic as Blocked). To do this set as follows:
String. afa.query.pass_fip_results=SameZone,Routed,PartiallyRouted
To define partially routed traffic as Allowed, also set the parameter:
afa.tsq.allow_partial_nonblocked_fip_result=true
Boolean. Use to remove duplicate objects during AFA object sync.
Supported values:
-
True (default): Remove duplicate objects during AFA object sync.
-
false: Do not remove duplicate objects during AFA object sync.
Boolean. Defines how the object update on device process works: bind endpoint to devices using the endpoint object or the device ID.
Note: This setting is used to enhance performance. If exceptions occur during the sync process, set to false.
true (default): Use endpoint object.
false: Use device ID.
For example,
afa.sync.device_batch_binder.through_objects=true
Specifies the priority order for device duplication, where the first listed device has the highest priority and the last listed device has the lowest priority. Device IDs should be comma-separated and can be any number.
Example Usage:
afa.sync.duplication.device_priority=device1,device2,device3
Default Value: BLANK (no value)
For more information, see Managing Same Name Different Content (SNDC) Objects in application flows.
Determines whether to update both Device and Non-Device Endpoints with the same name based on the priority device endpoint. This property only takes true or false as values and is effective only when afa.sync.duplication.device_priority is defined.
Example Usage:
afa.sync.duplication.device_priority.update_device_endpoints=true
Default Value: false
For more information, see Managing Same Name Different Content (SNDC) Objects in application flows.
Binary. Use to define partially routed traffic as Allowed (the default flow behavior defines partially routed traffic as Blocked.)
afa.tsq.allow_partial_nonblocked_fip_result=true
Supported values:
-
True: Partially routed traffic is defined as Allowed.
-
false (default): Partially routed traffic is defined as Blocked.
To define partially routed traffic as Allowed, also set the parameter:
afa.query.pass_fip_results=SameZone,Routed,PartiallyRouted
String. Specifies the device group to use when running connectivity tests across all applications.
Note: To run application-specific Traffic Simulation queries on a targeted group of devices—improving the accuracy of connectivity checks—define the device group in the Device Group field under the application's General Information section. See Application dashboard.
If empty, the query runs on ALL_FIREWALLS including all devices the user has permission to access.:
afa.tsq.custom_group=Group1
Default value: ALL_FIREWALLS
 ai.blacklisted.applications
ai.blacklisted.applications
Comma-separated list. Defines the application names that should be excluded from AI Discovery in AppViz. Any applications whose names appear in this list will not be discovered or displayed after discovery. This can include any invalid names that need to be omitted.
For example, the following blacklists the application names any and NOT_FOUND:
ai.blacklisted.applications=any,NOT_FOUND
 ai.app.discovery.source
ai.app.discovery.source
-
AFA: Use data from AFA device policy tables
-
AFF: Use data from FireFlow tickets
Default value: AFF
For example:
ai.app.discovery.source=AFA
 ai.used.custom.fields.in.cr
ai.used.custom.fields.in.cr
For example:
ai.used.custom.fields.in.cr=subject,comment,application,source,destination,service,custom1
 application.default.expiration.period.configuration.in.months
application.default.expiration.period.configuration.in.months
Specifies the expiration period (in months) after the latest recertification date. This property accepts valid JSON with a key defaultPeriodInMonths and the value can range from 1 to 36.
Default Value: {"defaultPeriodInMonths":12}
Example usage:
application.default.expiration.period.configuration.in.months={"defaultPeriodInMonths":12}
Integer. Defines the number of recent applications displayed in the applications menu.
application.recent.page_size=15
Default value: 10
Integer. Defines the number of application search results shown by default.
application.search.page_size=100
Default value: 100
String. By default, API username is called "api_access". Use to edit the API username.
Boolean. Determines whether AppViz change request handling is disabled, including all change request creation and all change request-related tabs.
Supported values:
- True: Change requests are disabled from AppViz.
- False (default): Change requests are enabled in AppViz.
Comma-separated list. Defines the FireFlow change request statuses that AppViz status changes will be triggered for.
By default, pending statuses for objects and applications in AppViz transition to their next status once FireFlow change requests reach the reconcile, pending match, or resolved statuses.
For example, the following sets the AppViz status to change when the FireFlow change request reaches the pending match, matched or resolved status:
changerequest.status.resolved=pending match,matched,resolved
Determines whether to enable AppViz connectivity checks for flows and applications, the Refresh Connectivity and Run Connectivity buttons, and scheduled connectivity checks.
- true (default): Enable connectivity checks, related buttons, and indicators.
- false: Disable connectivity checks, related buttons, and indicators.
Integer. Determines the maximum number of flows combined per application during a discovery process.
Default: 50
For example, the following sets the default value to 60 flows:
discovery.max_flows_per_application=60
Tip: The larger the number of maximum flows per application, the more specific each flow will be. The smaller the maximum number of flows per application, the more AppViz will optimize and combine flows.
String. Defines the minimum percentage of the IP addresses required to be found in a specific CIDR, for the CIDR to be suggested as a source/destination value.
This is relevant for the optimization process performed during discovery from traffic logs.
|
Supported values |
Supported values include:
Default: 0.3 |
Default: 10
endpoint.search.page_size=100
Default: 100
Boolean. Determines whether AppViz opens change requests in FireFlow for specific device objects by adding the device name to the object in the source/destination value.
Supported values:
- True: AppViz appends the device name to the object in the source/destination.
- False: AppViz does not append the device name to the object.
Note: This feature must be used together with the Set($StoreFirewallSuffixInHostGroup, '1')FireFlow command.
Boolean. Determines whether AppViz passes the names or content of the network objects when opening change requests in FireFlow.
Supported values:
- True. AppViz passes the content of the network objects.
- False (default): AppViz passes the network object name.
The value determines whether AppViz compacts the IP addresses before opening a Change Request in order to minimize the number of actions the Change Request needs to execute.
For example:
fireflow.ranges.compact=true
Boolean. Determines whether AppViz passes the names or content of the service objects when opening change requests in FireFlow.
Supported values:
- True:. AppViz passes the content of the service objects.
- False (default): AppViz passes the service object name.
Boolean. Determines whether AppViz differentiates between traffic that is explicitly allowed by a rule and traffic that is allowed because it is unprotected or unfiltered.
Supported values:
- True:. AppViz differentiates between explicitly allowed traffic and unprotected/unfiltered traffic.
- False (default): AppViz does not differentiate between allowed traffic types.
For example, you may want to enable this feature when using micro-management within subnets.
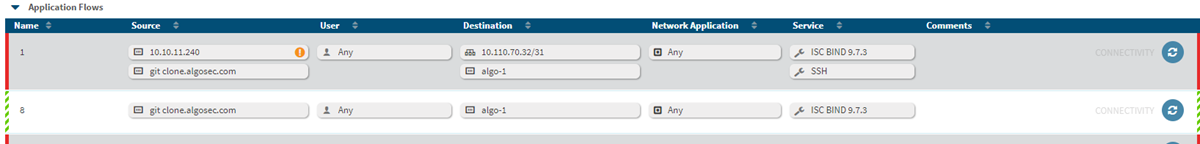
flow.connectivity.display_unprotected_flows=true
When configured, AppViz indicates this in the FLOWS tab as follows:
- All allowed flows appear with a green connectivity indicator.
- All unprotected flows appear with a striped indicator.
For example:
Additionally, this information is available in:
| Flow exports / API responses |
When AppViz provides connectivity information about flows, the values will specify whether the flow is "allowed" (protected) or "unprotected". Note: By default, AppViz does not include connectivity information in flow exports. For details, see flow.connectivity.export and Discover applications. |
| Application search abilities |
When performing an advanced search for applications By Connectivity, you will have the option to specify whether to search for applications with allowed flows that are protected or allowed flows that are unprotected. For more details, see Business applications. Note: Unprotected flow detection has no impact on application connectivity status, only flow connectivity status. An application whose flows are all allowed (protected or unprotected) will always have the connectivity status Allowed. |
Boolean. Determines whether flow connectivity data is exported together with an application's flows.
-
True: Connectivity data is exported together with the flows.
-
False (default): No connectivity data is exported.
When configured , exported connectivity data includes any of the following values:
- Allowed
- Blocked
- Partially blocked
- No connectivity information
- Unprotected.
Note: Unprotected appears only when AppViz is configured to detect unprotected flows.
Otherwise, all allowed traffic is assigned the Allowed value. For details, see flow.connectivity.display_unprotected_flows .
String. Determines the delimiter used in CSV import files.
Default value: , (comma)
For example, change this to a colon if needed:
import.delimiter=:
String. Defines the encoding used for imported files.
Default value: UTF-8
String. Determines the order of preference used when optimizing network objects from different sources.
During discovery, if more than one network object is found with the same name, AppViz selects the object to use based on origin preference configured.
| Supported values |
Source values include: |
| Default value |
Imported, BusinessFlow, Device |
For example, the following sets the priority sequence to BusinessFlow, Imported, Device :
network_entity.origin.order=BusinessFlow,Imported,Device
Note: Network objects that originate from the same place cannot have the same name, except for device objects. If two device objects with the same name (but different content) exist, the CSV file validation will fail.
If two device objects defined on different devices have the same name and the same content, AppViz will treat them as one object and validation will succeed.
Boolean. Determines whether AppViz is enabled to define device object definitions on the device using AppViz.
Supported values:
- True (default):Enable AppViz to define device object definitions on the device.
- False: Disable the ability for AppViz to define device object definitions on the device.
String. Determines the permissions granted by default to All Users.
Multiple values separated with commas.
For example, the following sets the initial permissions for all users to create applications and view all applications:
permissions.initial=ROLE_CREATE_APPLICATION,ROLE_VIEW_ALL_APPLICATION
For more details, see AppViz permission reference.
Default values:
| All users |
Default permissions for all users include:
|
 Privileged users Privileged users |
Privileged users have additional permissions to update risk information by default. See permissions.initial.afa_user for defining additional parameters. |
| Administrators |
Administrator users receive all permissions by default. |
 permissions.initial.afa_user
permissions.initial.afa_user
Determines the permissions granted by default to Privileged users.
For example, the following sets the initial permissions for Privileged users to view risk information:
permissions.initial.afa_user=ROLE_VIEW_RISK
For more details, see AppViz permission reference.
Determines whether risk checks are run automatically when a pending revision becomes active.
- True (default): Enable automatic risk checks.
- False: Disable automatic risk checks.
Tip: Use together with connectivity.enable to enable automatic data refreshes.
 saved.search.change.request
saved.search.change.request
This user property specifies the FireFlow saved search filter that determines which change requests will be evaluated by AI Discovery when set to use FireFlow as the data source (as set by the user property ai.app.discovery.source).
Default: [_1] Resolved Change Requests (this set AI Discovery to return only resolved change requests).
For example, say there is another saved search filter in FireFlownamed Resolved Change Requests from last 6 months, which returns only resolved change requests from past 6 months. The following configuration sets AI Discovery to use that saved search when returning results.
saved.search.change.request=Resolved Change Requests from last 6 months
A semi-colon delimited list of networks, in CIDR format. Defines the internal/private zone networks.
Default value: 10.0.0.0/8;172.16.0.0/12;92.168.0.0/16
For example, the following sets the internal zone to 172.16.0.0/12 and 92.168.0.0/16:
security_zones.default_internal_network_ranges=172.16.0.0/12;192.168.0.0/16
Defines the number of services displayed.
service.recent.page_size=10
Default 10.
Defines the number of service search results displayed.
service.search.page_size=100
Default 100
String. Determines ownership of shared flows, which are general or partial flows that may be relevant to many applications.
Note: Shared flows specify only a source or destination, leaving the remaining field only with a placeholder value. When an application subscribes to another application's shared flows, the subscribing application specifies a value for the placeholder.
Supported values include:
| sharingApplication (Default) |
Determines that the application with the shared flows is defined as the flow owner. Editing a shared flow or a subscribed flow creates an application draft for the application with the shared flow. |
| combined |
Determines that ownership is shared across several applications.
The application with the shared flow and the application with the subscribed flow will both reflect the risks, connectivity, etc., derived from the subscribed flow. Note: When a change is pending for traffic relevant to a shared or subscribed flow, the flows cannot be edited, deleted or added in any application. |
For more details, see Application flows.
Integer. Determines the maximum upload size, in MB.
For example:
upload.max_size=100
AppViz permission reference
|
Permission name |
Permission to... |
|---|---|
| ROLE_APPLY_DRAFT | Apply application drafts. |
| ROLE_CREATE_APPLICATION | Create a new application. |
| ROLE_CREATE_TAGS | Create tags. |
| ROLE_CREATE_SHARED_FLOWS | Create a shared flow. |
| ROLE_EDIT_ALL_APPLICATION | Edit all applications. |
| ROLE_EDIT_APPLICATION_INFORMATION | Edit application custom fields, tags, and contacts. |
| ROLE_EDIT_NETWORK_OBJECTS | Edit network objects. |
| ROLE_EDIT_SERVICE_OBJECTS | Edit service objects. |
| ROLE_SYNC_OBJECT | Run an update process for a device object. |
| ROLE_UPDATE_CONNECTIVITY | Update connectivity. |
| ROLE_UPDATE_RISK | Update risk information. |
| ROLE_VIEW_ACTIVITY_LOG | View activity log information for applications and network objects. |
| ROLE_VIEW_ALL_APPLICATION | View all applications. |
| ROLE_VIEW_CHANGE_REQUESTS | View change request information for applications, network objects, and service objects. |
| ROLE_VIEW_CONNECTIVITY | View connectivity. |
| ROLE_VIEW_RISK | View risk information. |
| ROLE_VIEW_VULNERABILITY | View vulnerability information for applications. |