AFA REST web services
Note: To view vulnerability data in AFA device reports, you must either have vulnerability scanners configured in AppViz, or import your vulnerability data manually.
For more details, see Manage vulnerability assessment scanners and Import vulnerability data.
Base URL
There are two types of base URLs and corresponding authentication method:
-
The base URL for most requests is:
https:://<algosec_server>/afa/api/v1where <algosec_server> is the AFA server URL. Most of these APIs are shown in swagger.
Authentication is through a cookie session. For example:
curl --cookie "PHPSESSID=g4mgnv4cno9ivt7rclmhmejj27" https://<IP:Port>/afa/api/v1/security_zones/get_profiles_list
For the value of the PHPSESSID parameter in the request cookie, use the sessionID value received in the login response. See Log in to ASMS .
-
The base URL for the remaining requests is:
https://<algosec_server>/fa/server
where <algosec_server> is the AFA server URL. These APIs are not shown in swagger.
Authentication is through a URL parameter (except for Log in to ASMS ). For example:
curl -H "Accept:application/json" -k " https://192.168.3.76/fa/server/rules/read?session=c69bcc3e6832149642b32e6f269c82c0&entity=admin
For the value of the session parameter in the request, use the sessionID value received in the login response. See Log in to ASMS .
Note: For each request, the documentation specifies the base URL and authentication method.
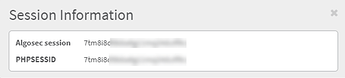
Tip: If you want to authenticate APIs and aren’t sure what your username/password is (for example, when you use SSO to log in), to quickly access your AlgoSec Session and PHP Session IDs:
Hover your mouse anywhere on the AFA home page and type ‘session!’. A popup with the session details will appear.
Swagger
The AlgoSec Firewall Analyzer RESTful API includes Swagger support, enabling you to execute simplified API request calls and access full lists of request parameters.
To access Swagger API documentation:
- In the toolbar, click your username and click API Documentation.
-
From the dropdown at the top-right, select one of the following definition options:
AlgoSec_Firewall_Analyzer Controls most central AFA API requests, such as object or device requests
--Vulnerabilities Controls AFA API requests related to vulnerabilites.
--Policy_Optimization Controls AFA APIs related to network rules. --Issues_Center Controls AFA APIs related to the ASMS Issues Center --Map Control AFA APIs related to the ASMS network map.
Syntax rules
Keep in mind the following syntax rules as you work with the APIs
-
Comma separated multiple items in lists: Lists can be identified by square brackets []. Each item in lists that are comma-separated need to be enclosed in quotes (" "). For example,
"service": [
"http","https"
]
Note: In the example above, "service": ["http,https"] is incorrect syntax.
AFA REST API reference
The following table lists the REST APIs supported for AFA. For more details, see EntitiesResponse type and AFA search rule fields.