Onboard Kubernetes Security
This topic explains onboarding options for your AWS Kubernetes clusters.
Cloud App Analyzer provides agentless discovery and detection of vulnerabilities, compliance, and configuration risks for Kubernetes components.
Note: Onboarding Azure and GCP Kubernetes clusters is performed automatically.
As part of the onboarding AWS wizard, there are two onboarding methods you can choose from to enable scanning of your AWS Kubernetes clusters:
Manual onboarding
Do the following:
-
Add permissions per cluster manually. Follows steps based on your cluster authentication mode:
When EKS API Mode is Enabled
-
Create a new access entry with access policy:
-
AWS IAM principal: Prevasio role ARN
-
Access policy: AmazonEKSViewPolicy
-
-
Download the following file: EKS API Roles YAML.
-
In the downloaded file, replace the string <prevasio assumed role arn> with:
arn:aws:sts::{account_id}:assumed-role/{prevasio_role_name}/AssumedRoleSession
-
Set account_id to AWS account ID (this is the onboarded to account_id).
-
Set prevasio_role_name to Prevasio IAM role name
-
-
Apply the edited file to the cluster.
When Only ConfigMap Mode is Enabled
Do the following:
-
Download the following script: ConfigMap Permissions Script
-
Before you run the script:
-
Ensure you are the creator of the cluster and have network access to it.
-
Install eksctl.
-
Set the following parameters in the script:
-
CLUSTER_NAME
-
CLUSTER_REGION
-
PREVASIO_ROLE_ARN
-
-
If you are not running in AWS CloudShell:
-
Install aws-cli
-
Install kubectl
-
-
-
Run the script.
-
-
Set public network configurations, if required
Note: Private Networks: Clusters won't be scanned.
For Public Networks: If the cluster has a restricted allowlist, add CIDR blocks to the allowlist:
Region
CIDR blocks
Prod US
3.230.68.171/32
Prod ME
15.185.85.1/32
16.24.29.104/32
16.24.42.118/32
Prod ANZ
13.238.234.53/32
52.65.218.87/32
54.153.142.211/32
Prod EMEA 3.69.134.56/32 52.29.118.194/32 52.59.98.60/32 Prod UAE 3.28.25.184/32 3.29.200.208/32 51.112.98.9/32 Prod IND 13.234.15.109/32 3.108.144.76/32 3.109.35.125/32
Automatic onboarding
Important:
-
Cloud App Analyzer automatic onboarding supports clusters with platform version 1.23 and higher. Read more.
-
Cloud App Analyzer automatic onboarding supports only clusters with public network access for any IP 0.0.0.0/0
When you choose to enable the automatic discovery and scanning of your Kubernetes cluster, if the current cluster authentication mode is ConfigMap, Cloud App Analyzer changes it to EKS API and ConfigMap.
Note:
-
Once EKS API and ConfigMap cluster authentication method is enabled, it cannot be disabled.
-
ConfigMap cluster authentication method is now deprecated. Read more.
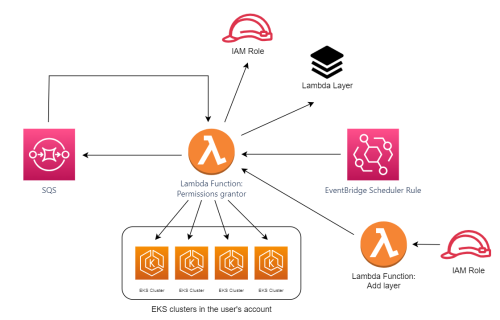
In addition, Cloud App Analyzer automatically creates additional resources in your account to establish the new permissions in each cluster.
Alongside the lambda function, the following resources are deployed:
-
Lambda Function (Permissions grantor): Grants required permissions in each cluster.
-
Lambda Function (Add Layer): Adds a layer to the permissions grantor lambda.
-
IAM roles: Dedicated roles for the lambdas with a custom policy attached. The permissions that the IAM roles use are listed below in Lambda required for automatic solution
-
SQS: If the lambda changes the access mode of the cluster, the cluster will be in an 'updated' status for several seconds/minutes after being updated. Consequently, it won't be available for connecting to add the required permissions. If clusters are updated, the lambda triggers itself with a delay of several minutes to add the permissions to the updated clusters.
-
EventBridge Scheduler rule: The lambda runs each day, discovering and adding permissions to new clusters.
Note: To see the list of Cluster roles that Cloud App Analyzer creates, see ClusterRole Permissions.
Lambda required for automatic solution
AlgoSec provides an automatic solution to create the required permissions for scanning a cluster.
As part of this solution, several resources are created:
| Type | Permission | Role | Component | Justification | |
|---|---|---|---|---|---|
| CNS | CAA | ||||
|
ec2:DescribeRegions (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ |
For Kubernetes Cluster scan: Lambda permission to list all the enabled regions in the account to identify clusters in these regions. |
||
|
eks:ListAccessEntries (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ |
For Kubernetes Cluster scan: Lambda permission to verify if the access entry for the Cloud App Analyzer role already exists. |
||
|
eks:ListAccessPolicies (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ |
For Kubernetes Cluster scan: Lambda permission to retrieve the available access policies. |
||
|
eks:ListClusters (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ |
For Kubernetes Cluster scan: Lambda permission to list all clusters to add the required permissions to each of them. |
||
|
eks:DescribeCluster (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ |
For Kubernetes Cluster scan: Lambda permission to retrieve the current cluster authentication mode configuration. If the mode is 'ConfigMap' only, change it to 'EKS API and ConfigMap'. |
||
|
eks:CreateAccessEntry (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ | For Kubernetes Cluster scan: Lambda permission to create an access entry for the Cloud App Analyzer role with viewer permissions. | ||
|
eks:AssociateAccessPolicy (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ | For Kubernetes Cluster scan: Lambda permission to assign the AmazonEKSClusterAdminPolicy to the lambda role access entry to add RBAC roles to the cluster. | ||
|
eks:DeleteAccessEntry (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ |
For Kubernetes Cluster scan: Lambda permission to delete the access entry for the lambda role after adding the permissions. |
||
|
eks:UpdateClusterConfig (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ |
For Kubernetes Cluster scan: Lambda permission to change the cluster authentication mode to 'EKS API and ConfigMap' if it is currently 'ConfigMap' only. |
||
Additionally, the AWSLambdaBasicExecutionRole built-in policy is assigned.
The following are the required Add Layer Lambda Function role permissions:
| Permission | Role | Component | Justification | Permission | |
|---|---|---|---|---|---|
| CNS | CAA | ||||
| s3:GetObject
(optional - for Kubernetes Cluster scan)3 |
IAM | ✔ | For Kubernetes Cluster scan: Permission to get the layer zip from Cloud App Analyzer public S3 bucket | ||
|
lambda:PublishLayerVersion (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ | For Kubernetes Cluster scan: Permission to publish a new layer version | ||
|
lambda:GetLayerVersion (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ | For Kubernetes Cluster scan: Permission to publish a new layer version | ||
|
lambda:UpdateFunctionConfiguration (optional - for Kubernetes Cluster scan)3 |
IAM | ✔ | For Kubernetes Cluster scan: Permission to attach the layer to the permissions grantor lambda function | ||