Attack Path Analysis (AWS)
Attack Path Analysis is a capability within Application Discovery that identifies when AWS services can potentially be remotely compromised due to a combination of misconfigurations and known exploitable vulnerabilities or malware.
Attack Path Analysis helps you understand when a workload is exposed and the potential path an attack could make in order to steal data or take control of the application.
It provides:
-
High-confidence detection of potential attack conditions
-
Clear visibility into how an attacker could reach and steal secrets, PII, customer records etc., or take control of an application.
-
Insight into the blast radius based on IAM permissions
-
Actionable guidance for remediation
This makes Attack Path Analysis an essential component of application-level risk assessment in AWS environments.
An attack path is constructed by using several patterns. For example, one of the patterns dictates that in order for an attack to be successful, the following conditions must be met:
-
Unrestricted Security Group: The EC2 instance is exposed through a security group allowing inbound access from anywhere (for example, 0.0.0.0/0).
-
Public Reachability: The instance resides in a public subnet or otherwise accepts external traffic.
-
Exploitable Weakness: The instance has a known exploitable vulnerability or malware. (Exposure alone is not enough—there must be something to exploit.)
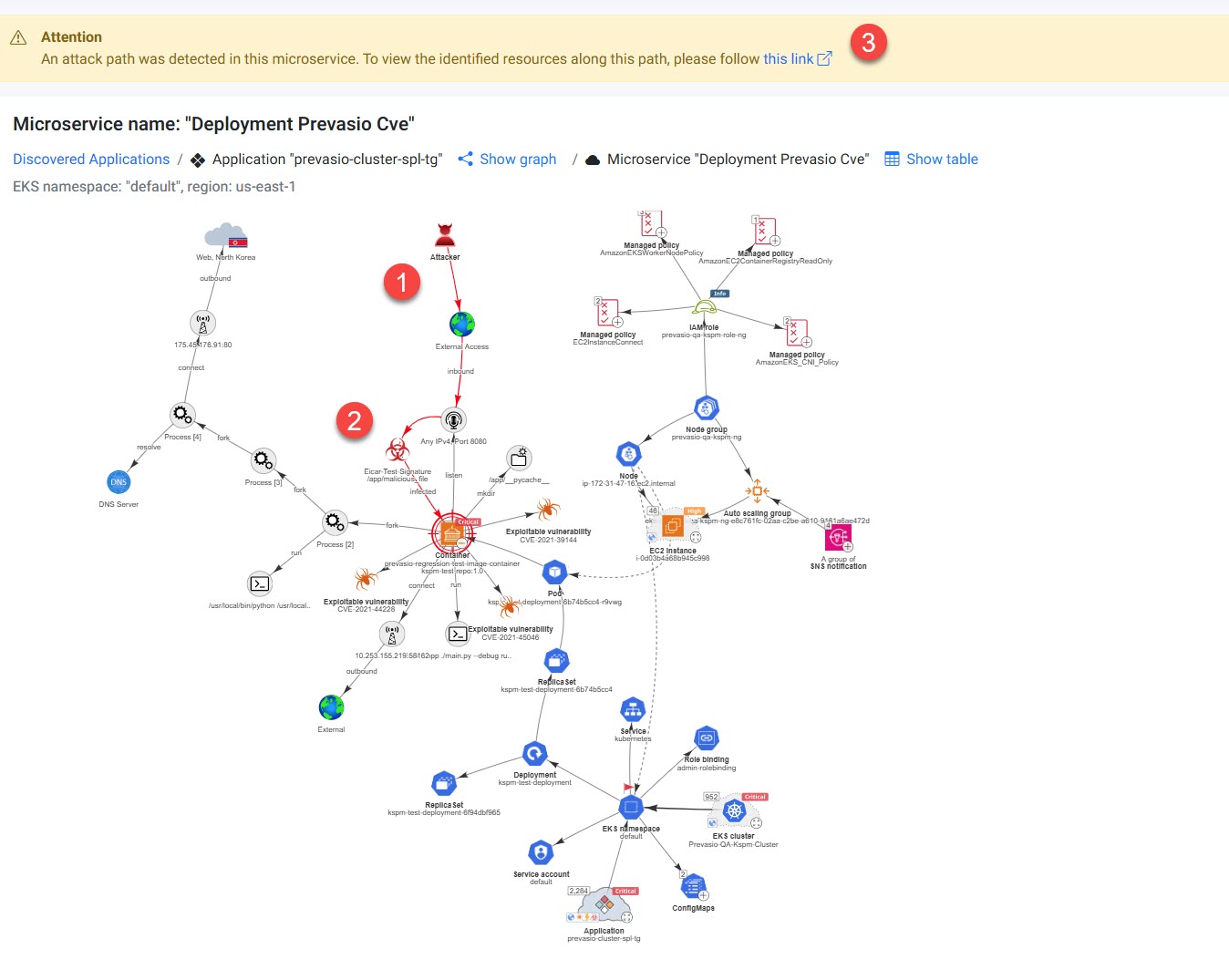
When required conditions align, ACE determines that a remote attacker could compromise the application and potentially take control of it. An Attack Path Detected alert appears at the top of the microservice graph to guide further investigation.
Viewing an Attack Path in the UI
When an attack path is found:
-
The graph displays the attack path overlay
-
The Findings icon appears on the affected application
-
A warning banner appears at the top of the microservice graph.

-
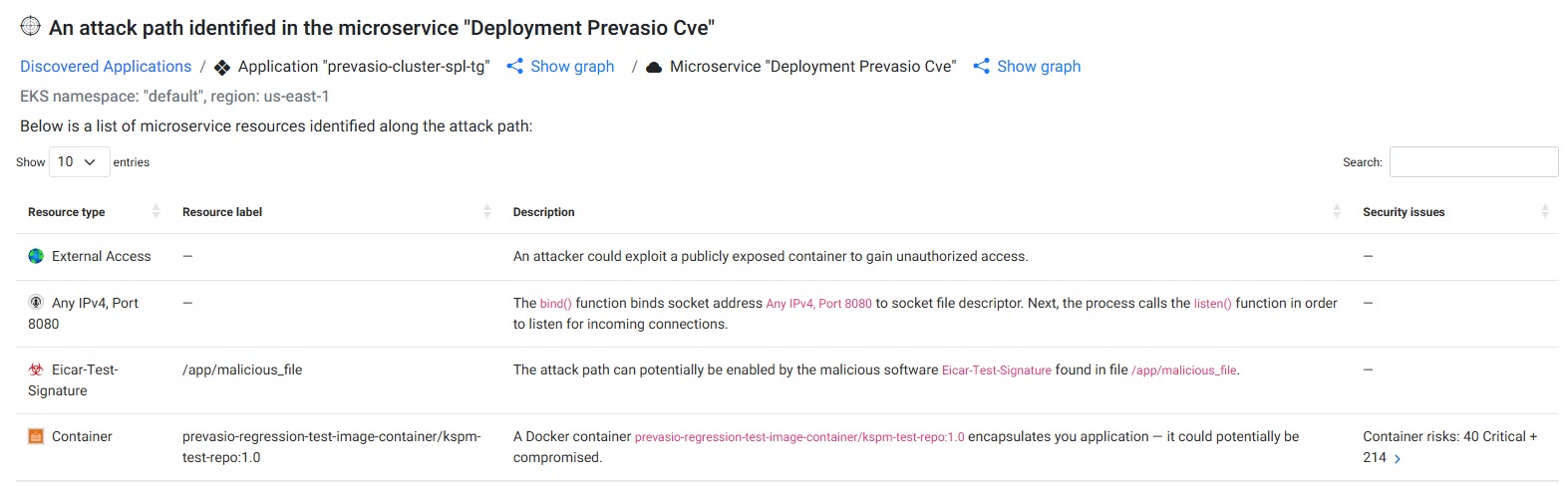
Clicking the link on the warning banner opens a dedicated Attack Path page lists each step in order, helping you understand how the attack could unfold.
The table shows all nodes involved in the attack path (excluding the attacker’s node), providing clear remediation guidance.
Understanding What an Attack Path Means
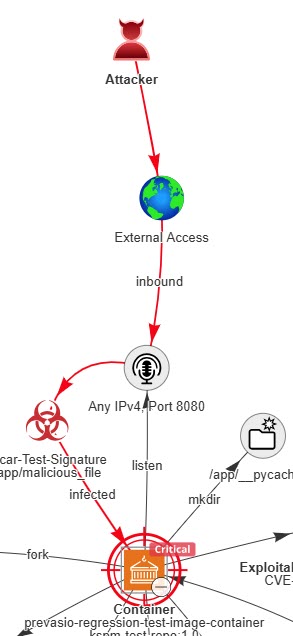
An attack path shows how a real attacker could progress from external access to AWS service impact.
Part 1: Compromise
If an attacker can reach an EC2 instance through a misconfigured security group and the instance has exploitable vulnerabilities or malware, ACE identifies it as a compromise point. A successful exploit could let the attacker run code with the same permissions the instance already has and get access to the data
Part 2: IAM Permissions Impact
If the instance uses an IAM role, ACE evaluates what that role can access.
If it grants permissions to critical AWS services, such as DynamoDB, S3, RDS/Aurora, Lambda, ECS, ECR, Cognito, or Bedrock, the attack path extends to those services.
If the instance has minimal or no permissions, the attack path stops at the instance itself.
The attack path always ends at the highest-impact service the attacker could reach through the compromised instance.
Remediating an Attack Path
Because attack paths represent potentially exploitable risks, remediation should be prioritized.
Common fixes include:
-
Restricting overly permissive security groups
-
Moving workloads out of public subnets
-
Patching vulnerabilities
-
Removing malware
-
Adjusting IAM roles to least-privilege access
Once corrected, the attack path will disappear after the next discovery scan.