Release Notes
This topic lists both latest features now available in Cloud Network Security and Cloud App Analyzer, and important documentation updates.
Note: In our technical documentation, we use the term "Azure Native Firewall" to refer to Azure Firewall (Policy-based) devices, distinguishing it from Azure Firewall (Classic).
- Cloud Network Security (CNS)
- Cloud App Analyzer (CAA)
CNS February 2026 Update
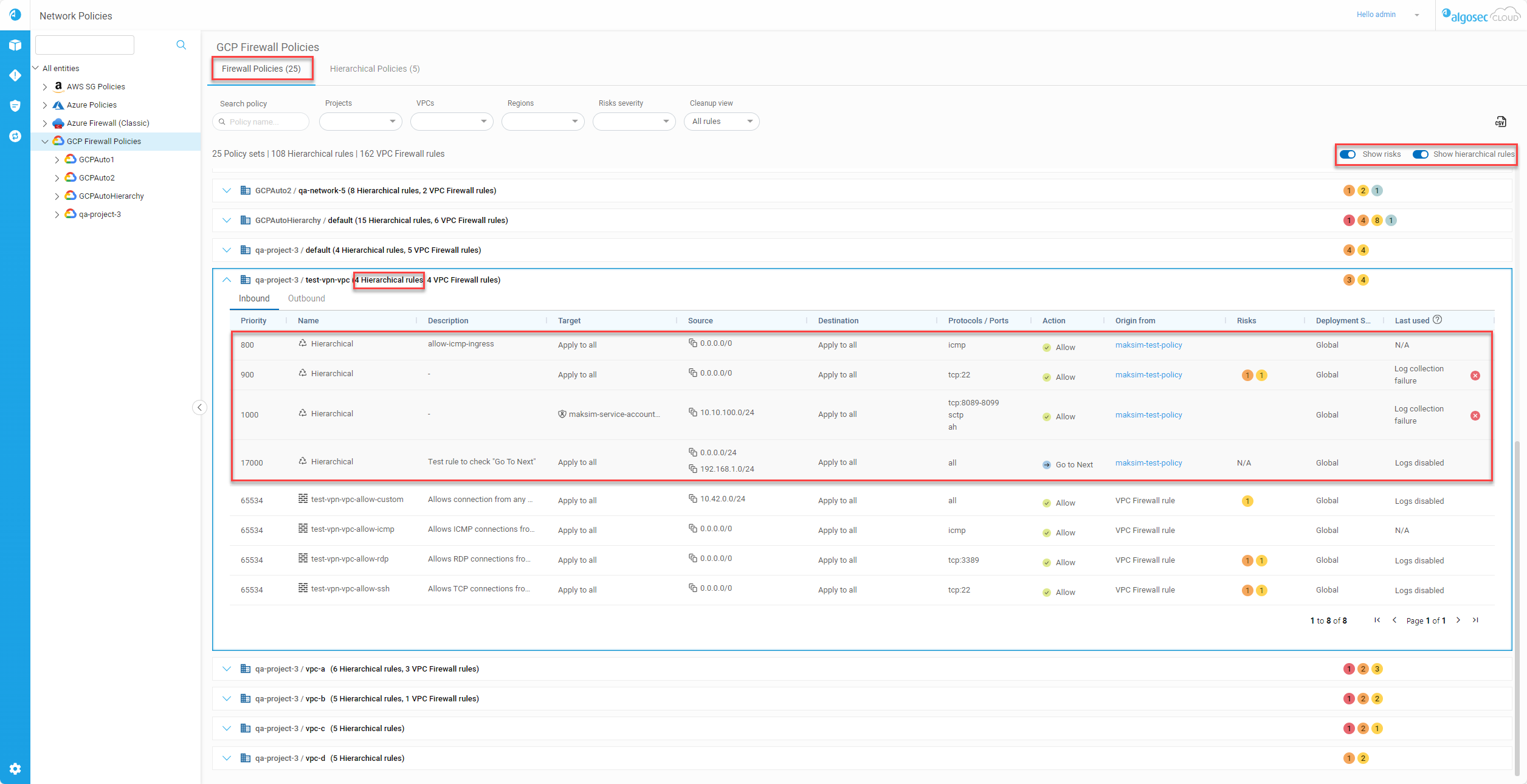
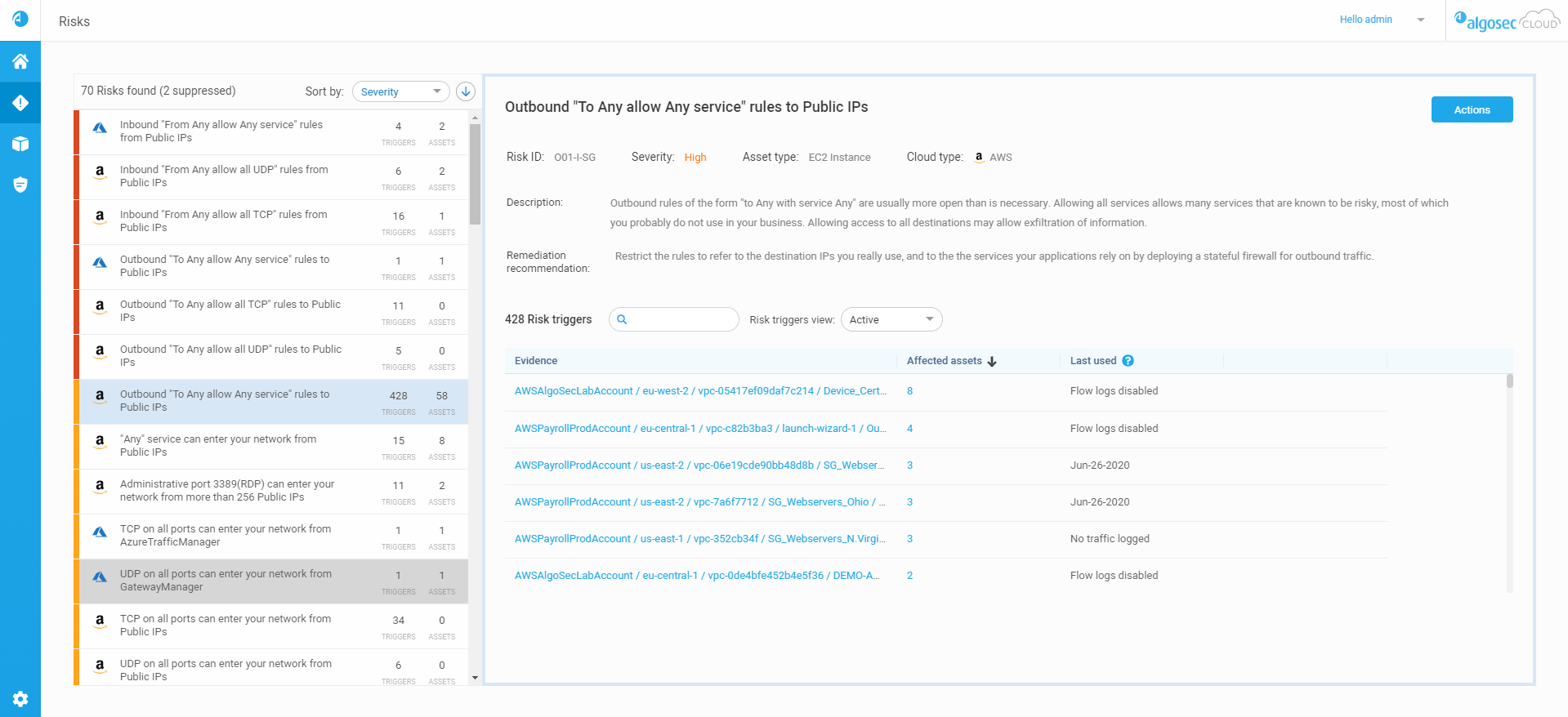
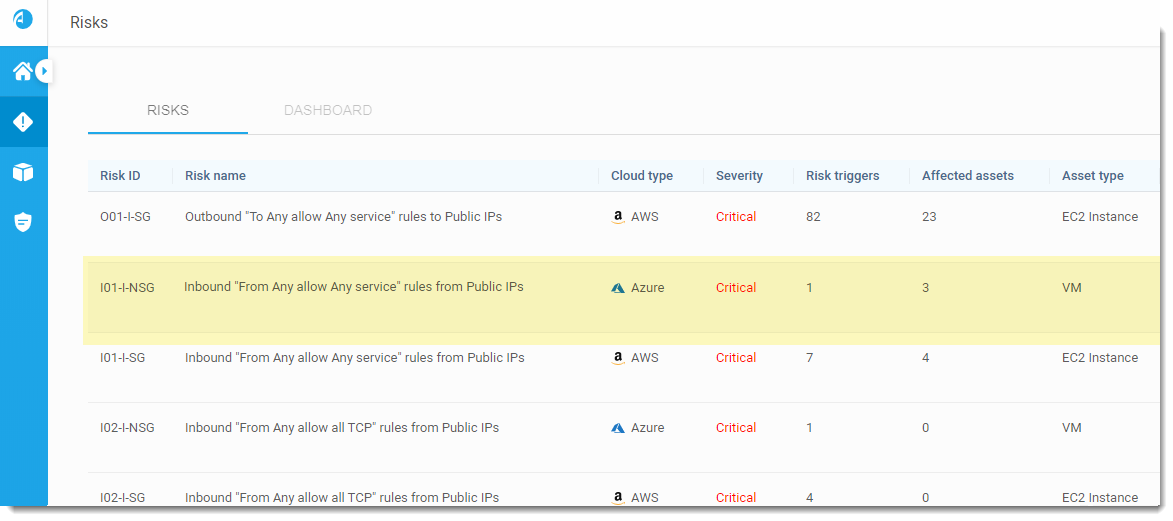
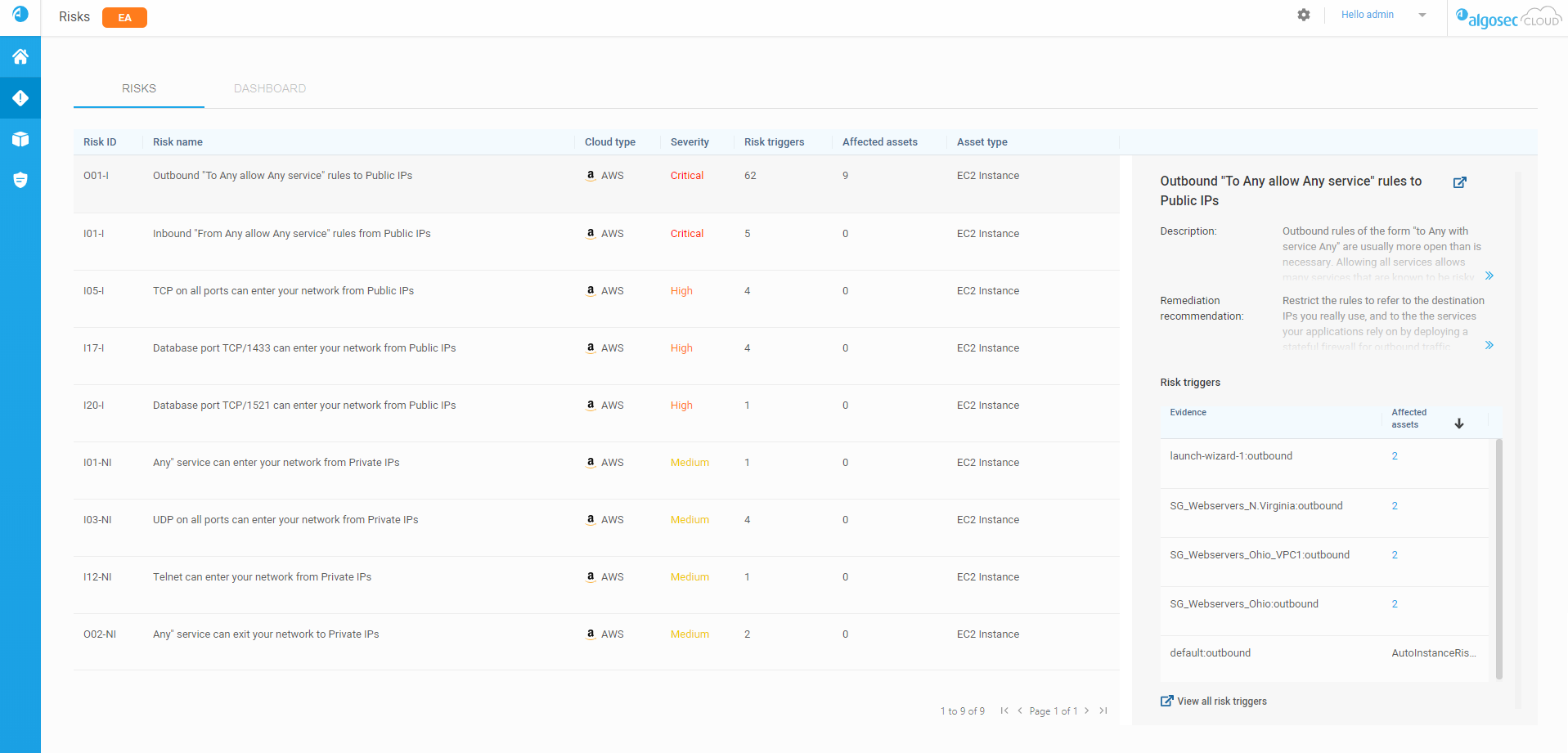
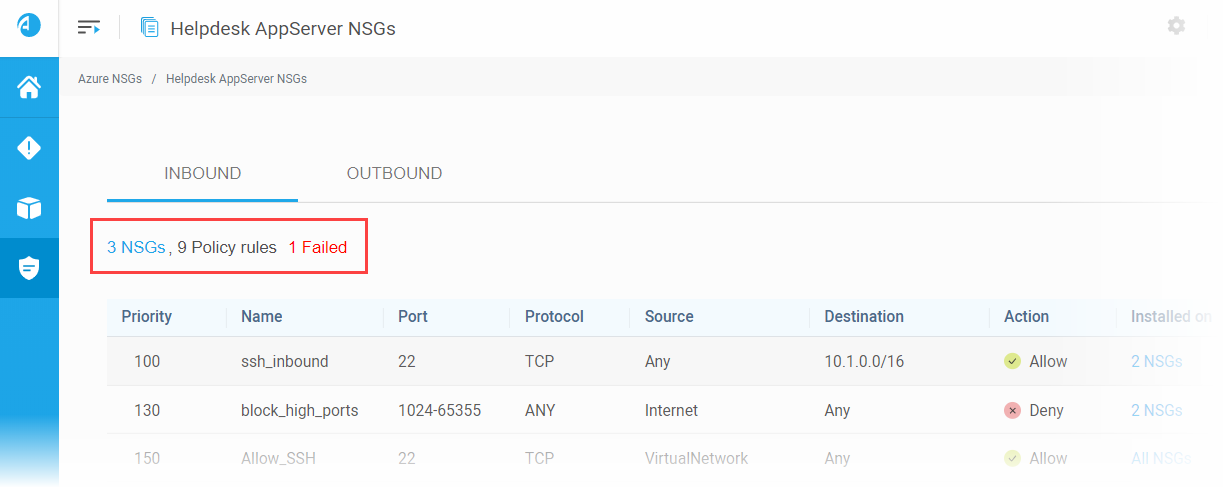
Findings column enhancement | Internet access issues detected during VM scans
The Findings column in the Virtual Machine tab now includes internet access–related issues detected during Cloud App Analyzer VM scans, making these findings visible directly within Cloud Network Security. You can now also generate a VM report that includes, for each VM, internet access information alongside networking issues and other VM-related findings.
This feature is currently available for AWS only.
For more details, see The Virtual Machines tab. (Released 25-Feb-2026)
Regenerate Onboarding API Access Keys
You can now regenerate the Onboarding API Access Key used for cloud onboarding at any time, helping you respond quickly to compromised credentials or meet key rotation requirements.
After regenerating the key, update your cloud configuration to ensure AlgoSec continues communicating with your cloud accounts.
Step-by-step instructions are provided for AWS, Azure, and Google Cloud. See Regenerating the Onboarding API Access Key. (Released 25-Feb-2026)
ACE now supports Azure ExpressRoute in the ASMS network topology map (currently in Early Availability), giving you clearer visibility into your hybrid connectivity by showing ExpressRoute circuits and peerings directly in the topology view. To enable it, an ASMS administrator must turn on the relevant EA flag. Required Azure permissions must also be configured. Available only when ACE is integrated with ASMS, and supported on ASMS 33.10 (latest hotfix) and higher. See:Permissions for Azure ExpressRoute for Cloud Network Security and Azure ExpressRoute in ASMS Map. (Released 5-Feb-2026)
CNS December 2025 Update
Exclude Risks using Trusted Networks
You can now define a network or IP range as trusted within your security policy. Rules whose source or destination contains only these trusted networks will not trigger risks. For more details, see Global Trusted Host Groups (Trusted Networks). (Released 15-Dec-2025)
CNS November 2025 Update
AWS Security Group Rule IDs now appear in the exported risk CSV reports and policy CSV reports.
Enable the following permission to use AWS Security Group Rule IDs:
-
ec2:DescribeSecurityGroupRules
For details on permissions, see AWS Permissions and Justifications. (Released 11-Nov-2025)
CNS October 2025 Update
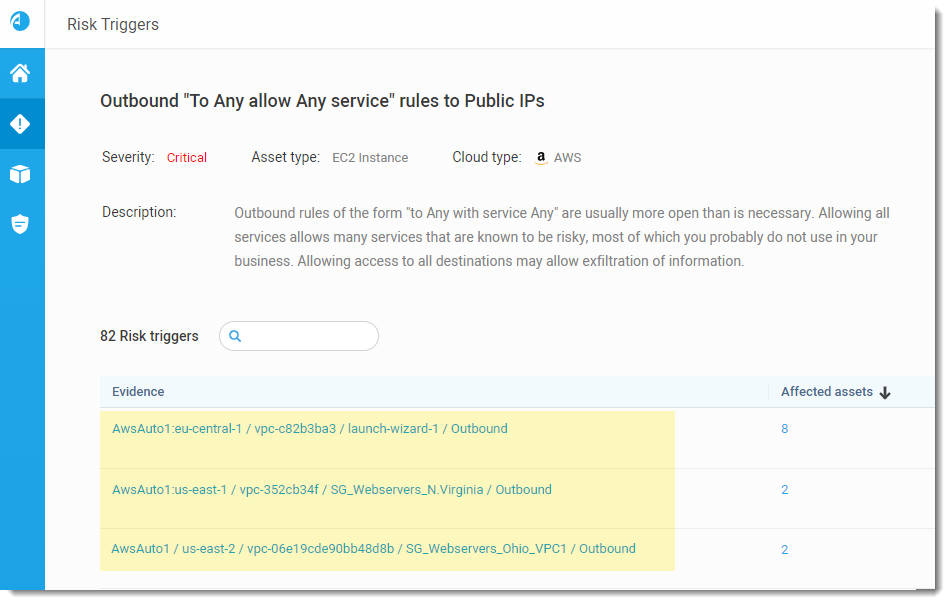
Define Risks for All Traffic Allowing a Specific Service
You can now define risks for any traffic that allows a specific service—for example, any rule permitting SFTP (TCP/22). For details, see Define Risks for All Traffic Allowing a Specific Service. (Released 29-Oct-2025)
ACE now lets you review account onboarding activities. For details, see Track User Activities. (Released 28-Oct-2025)
Export virtual machine report to a CSV file
We’ve added a new export option. You can now generate a CSV report that combines virtual machine data across all your accounts. See each virtual machine’s network details, including IPs, protection policy, tags, network risks, and any detected threats tied to its application. For details, see Export virtual machines to CSV. (Released 15-Oct-2025)
CNS September 2025 Update
Quick access to Compliance and Application pages
Now you can use the left-side navigation menu in Cloud Network Security to quickly access the following pages:
-
Compliance: Click to see the detected compliance risks across your AWS, Azure, and GCP accounts
-
Application Discovery: Click to identify applications and their component microservices within your AWS and Azure environments
For more details, see Getting Around Cloud Network Security. (Released 15-September-2025)
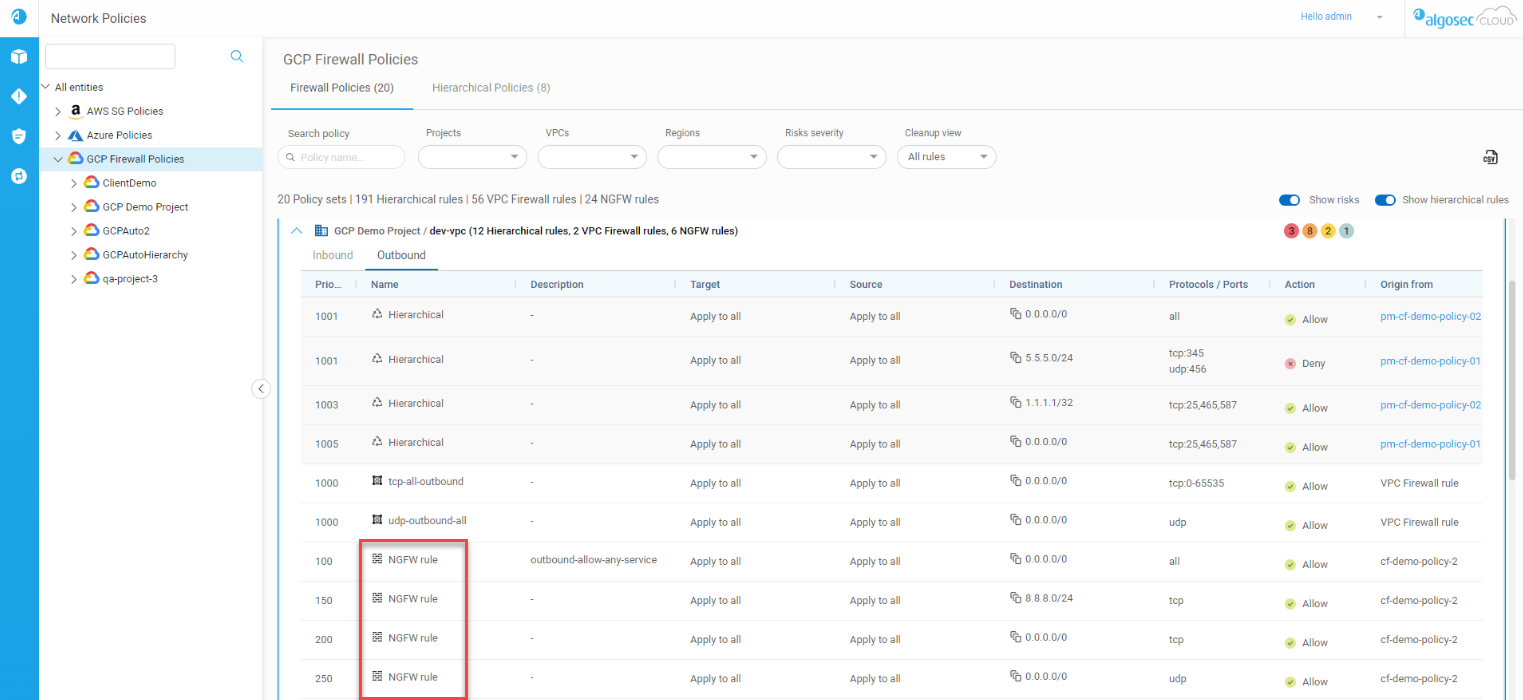
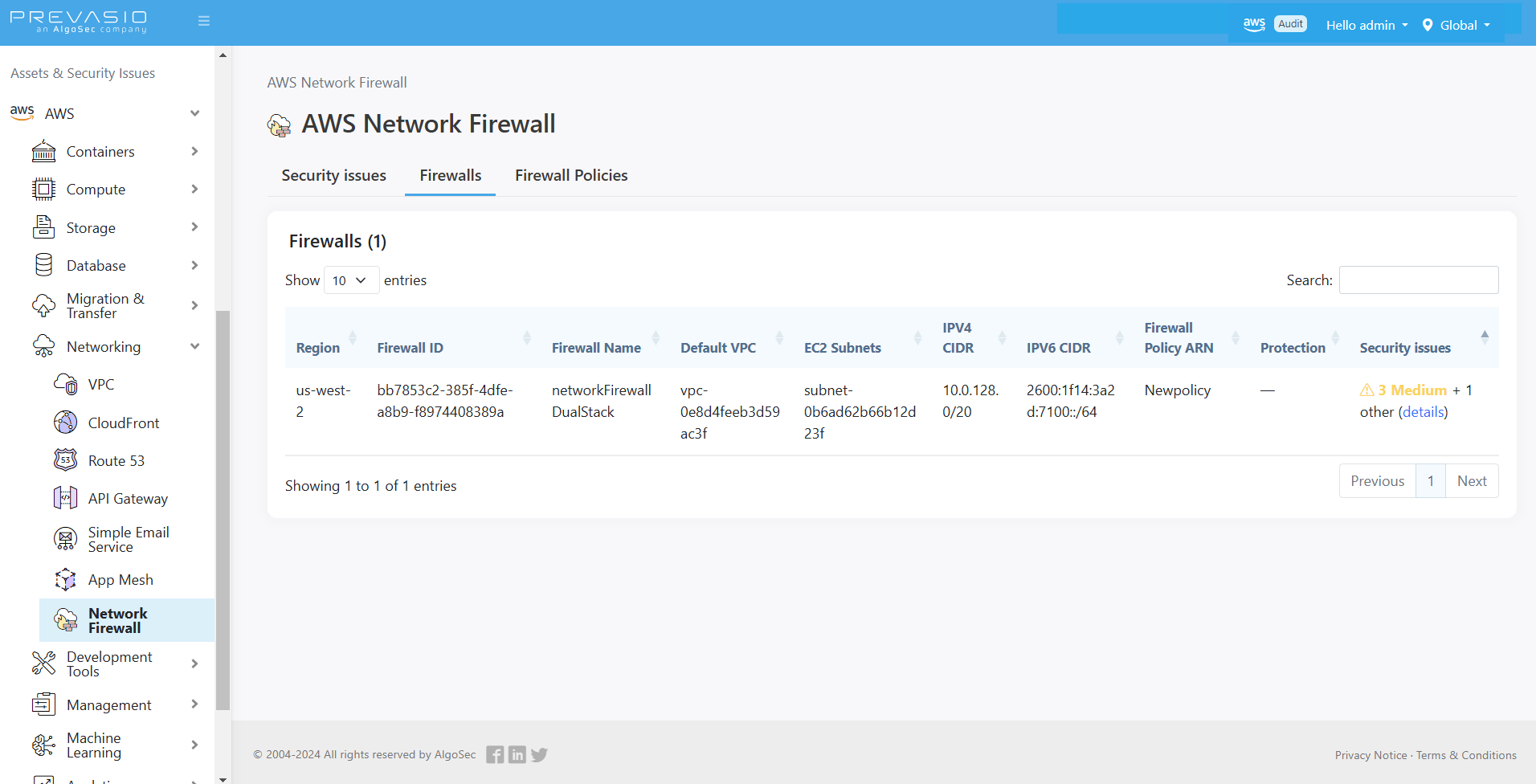
AWS Native Firewall policy visibility support
Now AlgoSec supports policy visibility for AWS Native Firewall. On a single pane of glass, you can see and review all the AWS firewall policies that you created and all the firewalls across all your AWS accounts. For each firewall, you can see the VPC the firewall is installed on, and the networking information including the availability zones and attached subnets. For details, see Work with Policies.
Enable the following permissions to use AWS Native Firewalls:
-
network-firewall:DescribeFirewall
-
network-firewall:ListFirewalls
-
network-firewall:DescribeFirewallPolicy
-
network-firewall:ListFirewallPolicies
-
network-firewall:DescribeRuleGroup
-
network-firewall:ListRuleGroups
For details on permissions, see Permissions for AWS Native Firewall. (Released 1-Sep-2025)
CNS August 2025 Update
Enhanced topology for AWS transit gateway
For ASMS A33.10: This optional permission supports enhanced topology for AWS transit gateway:
-
ec2:DescribeTransitGatewayVpcAttachments
For details on permissions, see Permissions Required for AWS Accounts. (Released 14-Aug-2025)
The New Findings column | Security Issues found during VM Scan
In addition to the network findings, the new Findings column in the Virtual Machine tab now also displays all the issues related to malware, exploitable vulnerabilities, and open ports detected during Cloud App Analyzer's VM Scan right inside Cloud Network Security. Click on an icon to see detailed information in Cloud App Analyzer. This feature is currently only available for AWS. For more details, see The Virtual Machines tab. (Released 7-Aug-2025)
CNS July 2025 Update
AWS Gateway Load Balancer Updated Permissions
For ASMS A33.10 support of AWS Gateway Load Balancers we have added the following read permissions requirements:
-
ec2:DescribeVpcEndpoints
-
ec2:DescribeVpcEndpointServiceConfigurations
For details on permissions, see Permissions Required for AWS Accounts. (Released 30-July-2025)
New AWS Permission for Enhanced Support of Transit Gateway (for ASMS A33.10+)
For customers using ASMS A33.10+, we have added a new AWS permission requirement ec2:GetTransitGatewayRouteTableAssociations to support the Network Topology Map, Traffic Simulation Queries, and support in FireFlow. This permission allows ASMS to list Transit Gateway route table associations and retrieve their corresponding attachments, improving the accuracy of connectivity insights across AWS environments. Also important when AWS Load Balancer is connected to transit gateway. See Permissions Required for AWS Accounts.
We have added support for GCP LB. Customers who have not used scripts for onboarding their GCP Projects need to add the following permissions:
-
compute.networkEndpointGroups.list
-
compute.backendServices.list
-
compute.healthChecks.list
-
compute.instanceGroups.list
-
compute.targetInstances.list
-
compute.targetPools.list
For details on permissions, see Permissions Required for Google Cloud Projects . (Released 1-July-2025)
CNS May 2025 Update
AWS Gateway Load Balancer Support
ASMS A33.10 displays AWS Gateway Load Balancers in the tree and network topology map.
Additional permissions are required for this feature to work correctly:
-
elasticloadbalancing:DescribeTargetGroups
-
elasticloadbalancing:DescribeTargetHealth
-
elasticloadbalancing:DescribeListeners
-
elasticloadbalancing:DescribeLoadBalancers
For details on permissions, see Permissions Required for AWS Accounts. (Released 14-May-2025)
Monitor VPC / VNet internet access
Now ACE helps you identify unwanted connections to the internet.
We've added the Internet Access column to the Accounts tab and VPC / VNet tab, which displays whether a VPC / VNet can access the internet from one of the private subnets defined on it. This analysis considers all the routing and policies defined on the path to the internet. For details, see The Accounts Tab and The VPCs / VNets Tab. (Released 7-May-2025)
CNS April 2025 Update
AWS participant accounts | Flow log collection
AlgoSec Cloud now supports displaying unused rule information for shared VPCs of a participant account. We support flow logs defined in the owner account on the VPC level or on the Subnet level. For more details, see Enable VPC flow logging for S3. (Released 15-Apr-2025)
View applications and microservices used by virtual machines
You can now easily access the application and related findings for each AWS EC2 instance and Azure virtual machine. Click on the link in the new Application Graph column of the Virtual Machine tab to open the application dependency graph where you can review microservices and findings related to the virtual machine. For more details, see The Virtual Machine Tab. (Released 9-Apr-2025)
Track Public IPs on the Account Overview page
You can now see a summary of all the Public IPs that are defined on each account / subscription / project. This can assist you to identify Public IP misconfiguration. Drill down to see on which VNet / VPC the Public IP address is defined or check in the Virtual Machine tab where this Public IP is configured. For more details, see The Accounts Tab. (Released 9-April-25)
CNS March 2025 Update
Assign accounts to custom risk profiles
AlgoSec now supports customized risk definitions on a per-account basis. Admins can upload multiple customized risk profiles to ACE Cloud Network Security and choose which profiles will generate the risks for each account. For more details, see Manage risk profiles. (Released 31-March-2025)
CNS January 2025 Update
We've added a new VPCs / VNets tab to the Overview page that lets you see an aggregated view of all your AWS VPCs, Google Cloud VPCs and Azure VNets from multiple accounts. Easily identify VPCs / VNets that have low security ratings, risky virtual machines, critical risks, and other vital information to better manage your cloud security. Use the filters to focus on a subset of VPCs / VNets, for example to find virtual machines with public addresses. For more details, see VPCs / VNets tab . (Released 23-Jan-2025)
CNS December 2024 Update
New APIs to download scheduled reports
AlgoSec can now automatically create scheduled Policy and Risk CSV reports via APIs. The report can be used for status archiving purposes and for business integration (BI). See Export risk and risk trigger details and Export Policies. (Released 17-December-2024)
Export risk details to a CSV file
You can now export all your Azure NSG, Azure Native Firewall, and Google Cloud risks to a CSV report—expanding on the existing capability to export risk details for AWS. The CSV report includes detailed information about the risks, the affected virtual machines, the tags associated with them, and information about the associated network interfaces. This allows for easy sharing with relevant stakeholders, further analysis and using it in external business intelligence (BI) systems. For details, see Export risk and risk trigger details. (Released 10-December-2024)
CNS November 2024 Update
Google Cloud Network Firewall Policy | Secure tag keys
Cloud Network Security now collects Network Firewall Policy secure tag keys. This information is used for Google Cloud Traffic Simulations.
The following additional permission is required for this feature to work correctly:
-
resourcemanager.tagKeys.list
For details on permissions, see Permissions required for Google Cloud. (Released 12-November-2024)
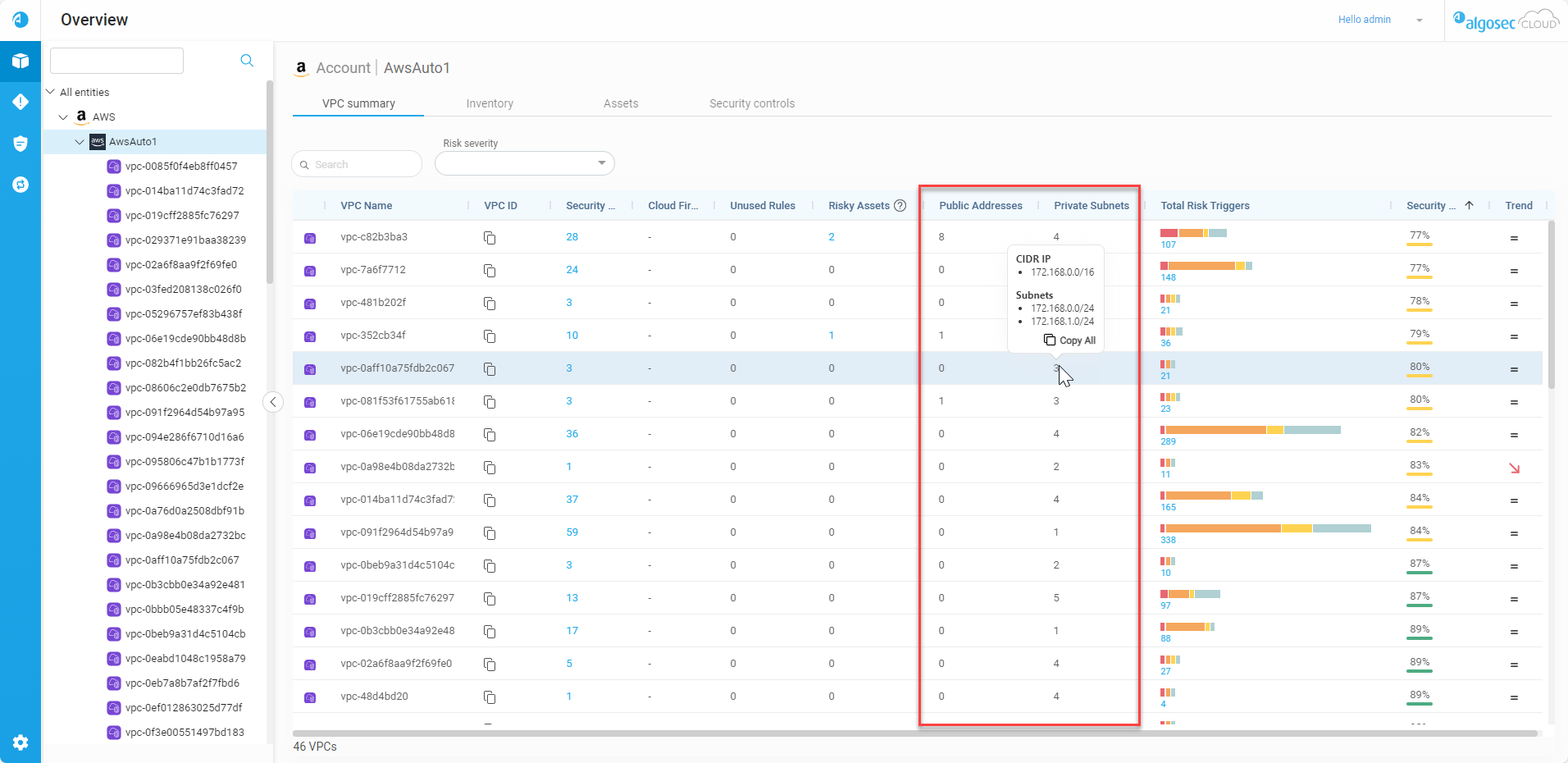
VPC Summary | See Public IPs and Private Subnets
Now you can see the public IP addresses and private subnets associated with all interfaces in Azure VNets and AWS/Google Cloud VPCs. For more details, see The Account Summary Tab. (Released 12-November-2024)
Extended export to PDF and CSV capabilities
Now you can export detected risks, scan results, history of pull requests and applications, to PDF and CSV files. (Released 26-Nov-2024)
CNS October 2024 Update
Google Cloud Network Firewall policy visibility
Cloud Network Security now displays Google Cloud Network Firewall policies for each VPC in the Firewall Policies Tab.
Note: Additional permissions is required for this feature to work correctly:
-
compute.regionFirewallPolicies.list
(this replaces the obsolete permission compute.regionNetworkFirewallPolicies.list)
For details on permissions, see Permissions required for Google Cloud.
For details see Network policies. (Released 23-October-2024)
Additional permissions required to onboard GCP via Terraform, API and No Script
Additional permissions are required to onboard GCP via Terraform, API and No Script:
-
compute.interconnectAttachments.list
-
compute.interconnects.list
For details on permissions, see Permissions required for Google Cloud (Released 23-October-2024)
CNS September 2024 Update
Export AWS risk details to a CSV file
AlgoSec Cloud now lets you export a snapshot of risks and risk trigger information for easy sharing with relevant stakeholders and further analysis. As part of this feature, self-referencing rules are now indicated in the Comments column of the exported file. For details, see Export risk and risk trigger details. (Released 10-September-2024)
CNS August 2024 Update
New AlgoSec Cloud deployment locations for UAE and IND regions
We're excited to announce the addition of a new ACE deployment location for our valued users in the UAE and IND regions. ACE is now hosted on the following AWS availability zones:
-
IND: ap-south-1 (Mumbai)
-
UAE: me-central-1 (UAE)
-
ME: me-south-1 (Bahrain )
-
US: us-east-1 (N. Virginia)
-
EMEA: eu-central-1 (Frankfurt)
-
ANZ : ap-southeast-2 (Sydney)
See Logging in and out. (Released 5-August-2024)
CNS July 2024 Update
View risk triggers associated with virtual machines
Now you can easily identify all the risk triggers associated with a virtual machine in one convenient location, and then follow up to investigate the rule which is the root cause of the risk. For more details, see View risk triggers associated with a virtual machine. (Released 22-July-2024)
How to offboard cloud resources
We've updated the documentation to provide clear instruction on how you can offboard your AWS, Azure, and Google Cloud resources. For details see:
(Released 5-July-2024)
CNS June 2024 Update
CSV reports | See risk details for exported policies
When you export a policy CSV report, by default the report now includes the associated risks for each rule. (Released 25-June-2024)
CNS May 2024 Update
Enhanced User Management with SSO Group Mapping!
Create groups of users based on their job roles, departments, or other criteria in your identity provider. Then In AlgoSec Cloud, you can associate these SSO groups to user roles and set their permissions. See SSO Group mapping and management. (Released 29-May-2024)
Rebranding Update: CloudFlow is now called AlgoSec Cloud
We're excited to share that CloudFlow has a new name – AlgoSec Cloud! This name change reflects our evolving brand identity, and is already aligned in our latest marketing initiatives.
Now you can download a detailed policy report that includes security network policies and their corresponding rules in a convenient CSV format. Perform in-depth analysis of your security landscape and share insights with relevant stakeholders. For more details, see Export policies details to a CSV file. (Released 6-May-2024)
CNS April 2024 Update
Azure Native Firewall | Network Zone Definitions
Now you can define network zones Internal, DMZ and External in the customized risk profile excel, improving risk assessments and risk accuracy. See User-Defined Network Zone Definitions: Enhanced Risk Accuracy. (Released 11-April-2024)
Manage notifications about risk & policy changes and ASMS connectivity on the new Notifications page. You can set notifications to be sent via email and Microsoft Teams to selected users ensuring they receive only the notifications that are most relevant to them. For more details, see Configure ACE Notifications. (Released 10-April-2024)
Now you can customize a risk report by selecting specific risks to include, focusing only on the areas that matter most to you. We've also provided the option in the report to only show the number of affected assets without listing them all by name. For more details, see Export risk and risk trigger details. (Released 4-April-2024)
CNS March 2024 Update
For each risk, ACE now displays a detection date so you can quickly understand what risks were recently added to your environment and take immediate actions to fix them. (Released 26-March-2024)
-
The new Detected on column shows the date ACE first detected a risk trigger for a rule. For more details, see Risk triggers.
-
Filter risks by their detection date using the Detection date filter. Select a predefined or custom date range. For more details, see Search and filter risks.
New ACE deployment location for Middle East (ME) region
We're excited to announce the addition of a new ACE deployment location for our valued users in the Middle East region. ACE is now hosted on the following AWS availability zones:
-
ME: me-south-1 (Bahrain )
-
US: us-east-1 (N. Virginia)
-
EMEA: eu-central-1 (Frankfurt)
-
ANZ : ap-southeast-2 (Sydney).
See Logging in and out. (Released 19-March-2024)
See when accounts were onboarded to ACE
On the Onboarding page, you can now see the date when each account was successfully onboarded to ACE. (Accounts onboarded before this feature was introduced will show N/A.) For more details about the new Onboarding Date column, see -+6. (Released 12-March-2024)
See the date/time when data collection of onboarded accounts last completed successfully
ACE now makes it easy to see when the last successful data collection occurred. The column "Last Successful Update" on the Onboarding page shows the most recent date and time that data, necessary for calculating risks and other important information about your onboarded resources, was gathered. If an error occurred during the update process  appears in the Status column. Hover over the status error icon to see details about the error as well as the last update attempt. For more details, see Onboarding Management. (Released 12-March-2024)
appears in the Status column. Hover over the status error icon to see details about the error as well as the last update attempt. For more details, see Onboarding Management. (Released 12-March-2024)
Filter risks according to virtual networks on the risk page
Now you can see which risks are associated with specified virtual networks. See Risk filters. (Released 12-March-2024)
We have updated login URLs:
-
For US-based users: http://us.app.algosec.com/prevasio
-
For ANZ-based users: http://anz.app.algosec.com/prevasio
See Logging In and Out. (Released 06-March-2024)
CNS February 2024 Update
Azure Native Firewall support for Last Used rule information and unused rules
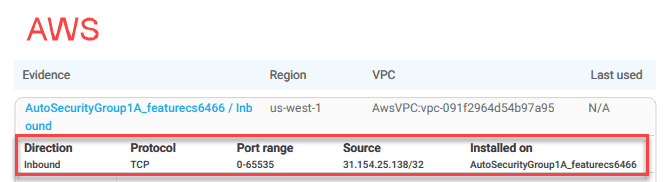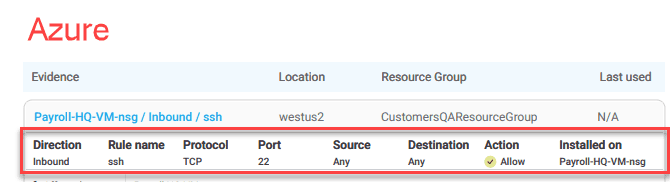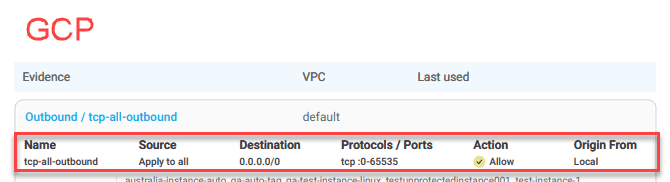
ACE now supports Azure Native Firewall log data to track the last usage of firewall rules, allowing users to identify unused rules and generate reports on them. For details, see Filter displayed policies, Export risk trigger details, and Enable Azure resource logs for traffic analysis. (Released 12-March-2024)
View Azure ACR CD mitigation scan history
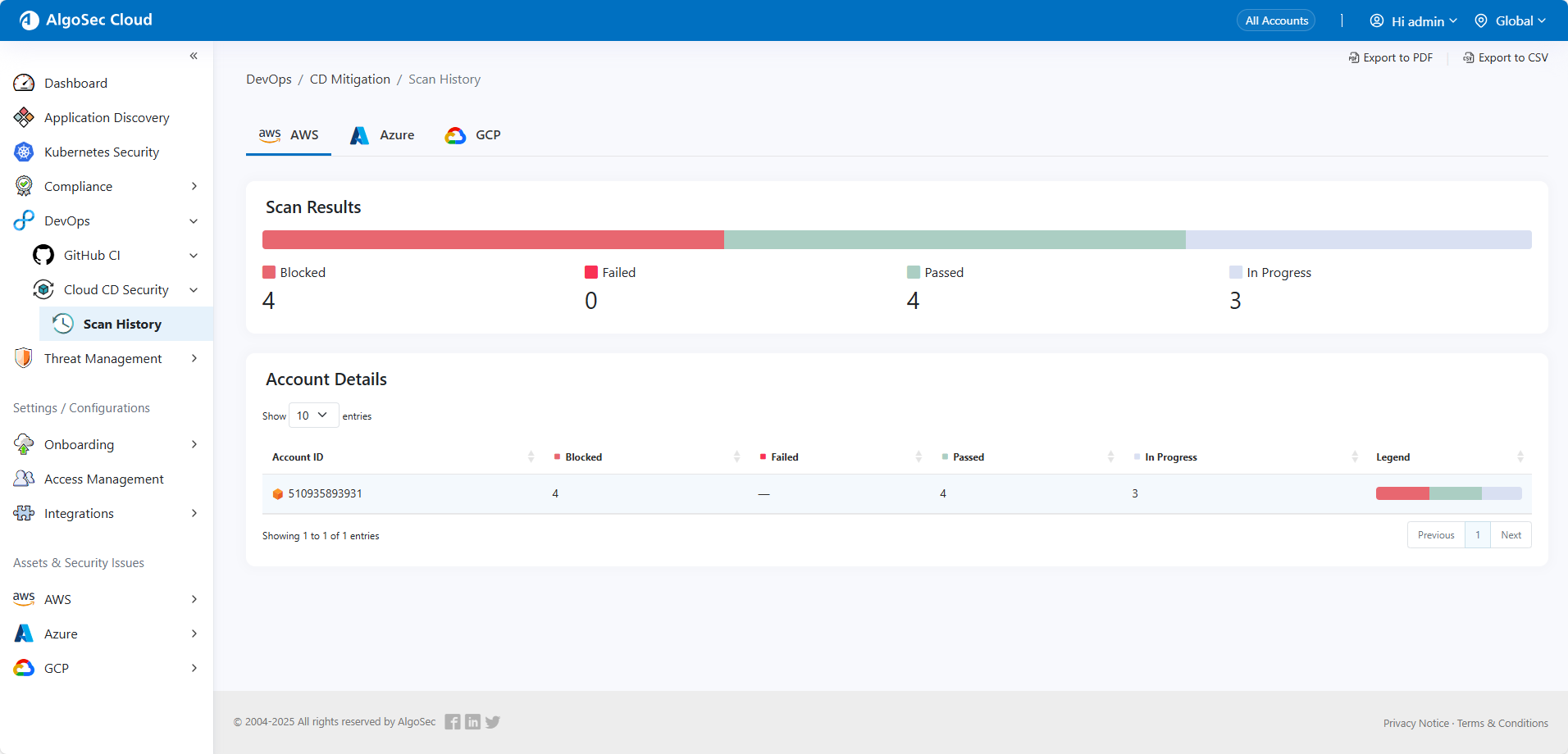
The ECR CD Mitigation Scan History Page provides a provides a scan log of each deployment of an image in the CR . You can view a summary of all scan history or drill down for details of each Azure Subscription. See Enable Threat Management on Azure ACR. (Released 28-February-2024)
View Configuration and Compliance Risk Trends
We've enhanced the dashboard for single accounts of all CSP (Cloud Service Provider) types. This update features a high-level analytic risk trend graph. This graph displays both regressions and progress in resolving configuration and compliance issues for the account and can be filtered according to severity level and time frame. Additionally, the update introduces a summary of the latest cloud security assessment scan data for the selected cloud account.
These enhancements enable security administrators to gain a holistic view of the current security status and historical trends streamlining the process of identifying vulnerabilities and understanding security patterns over time.
See View Configuration and Compliance Risk Trends. (Released 19-February-2024)
CNS January 2024 Update
Risks severity filter for Azure Native Firewall
We've added the Risks severity filter for Azure Native Firewall. This filter allows the display of only those policies in the list that contain rules with the selected severity level. See Filter displayed policies. (Released 29-January-2024)
Onboard Google Cloud resources from multiple organizations.
You can now onboard resources to ACE from multiple organizations in Google Cloud. To ensure a smooth onboarding process, make sure that project IDs should be unique across different organizations. For more details, see Onboard Google Cloud Projects to Cloud Network Security. (Released 29-January-2024)
New onboarding methods for Google Cloud, Azure and AWS
Four methods for onboarding Google Cloud and Azure resources are now available in the onboarding wizard. You can choose from With Script, No Script (ideal for environments that do not support scripts), API, or Terraform methods, via a drop-down menu. For AWS, there are now three available methods to choose from: With Script, API, or Terraform. For more details, see:
-
For Google Cloud: Onboard Google Cloud Projects to Cloud Network Security
-
For Azure: Onboard Azure Subscriptions
(Released 29-January-2024)
Improved dashboard to explore and identify Account and Virtual Network issues
The dashboard on the Accounts Summary tab now offers expanded functionality. When you select an account in the Account Summary tab, you can see all the virtual networks in the account and pinpoint the virtual networks that are at the root cause of network issues. You can also drill down into the virtual networks to explore further and gain a deeper understanding .
In the Account Summary page, we added two additional columns: Security policies and Cloud firewalls. These columns allow you to gauge the total number of security policies in each account. In addition, for Azure subscriptions you can review the number of Azure Native Firewalls under each.
We also added summary pages for each virtual network.
For more details, see Review Account Status. (Released 17-January-2024)
Enhanced Networking Risk Management in Cloud App Analyzer
Introducing the AlgoSec Best Practices compliance standard: Cloud App Analyzer now enables you to deep dive into networking risks with advanced capabilities for identifying and analyzing networking misconfiguration, a feature that distinctly positions us ahead of competitors in the cloud security space. We've added a fourth compliance standard, AlgoSec Best Practices, specifically designed for network risk violations. This internally developed standard elevates our compliance and risk assessment to new heights, offering a more comprehensive analysis and improved adherence to compliance standards. See Manage Networking Risks in Cloud App Analyzer. (Released 17-January-2024)
CNS December 2023 Update
Risk trigger indicators for individual Azure Native Firewall policies
ACE now delivers enhanced insights regarding the number of risk triggers detected in Azure Native Firewall policies. Besides showing the risk trigger totals for each policy, you can now see the breakdown of these numbers at the rule collection group and individual rule levels. Clicking on any of these indicators opens a popup with detailed information on the risk triggers. For more information, see View risks details at the policy level. (Released 26-December-2023)
You can now easily access your Account ID directly fromACE. This is ideal if you're managing multiple accounts. It also simplifies the process of referencing an Account ID for support queries. To view and copy your account ID, just click on your username located at the top right corner of the screen to open the drop down. See View your Account (Tenant) ID. (Released 26-December-2023)
Export Azure Native Firewall Risk Report to PDF
Now you can export risk reports for Azure Native Firewalls in PDF format. The report contains detailed information about risks and risk triggers found on Azure Native Firewall devices based on the filters selected by the user requesting the report. See Export risk and risk trigger details. (Released 14-December-2023)
CNS November 2023 Update
Onboarding Azure resources without scripts
We've updated the onboarding wizard to include an option to onboard Azure subscriptions, management groups, and tenant root groups without using scripts. This is useful if your environment does not support scripts. For more details, see Onboard Azure Subscriptions. (Released 28-November-2023)
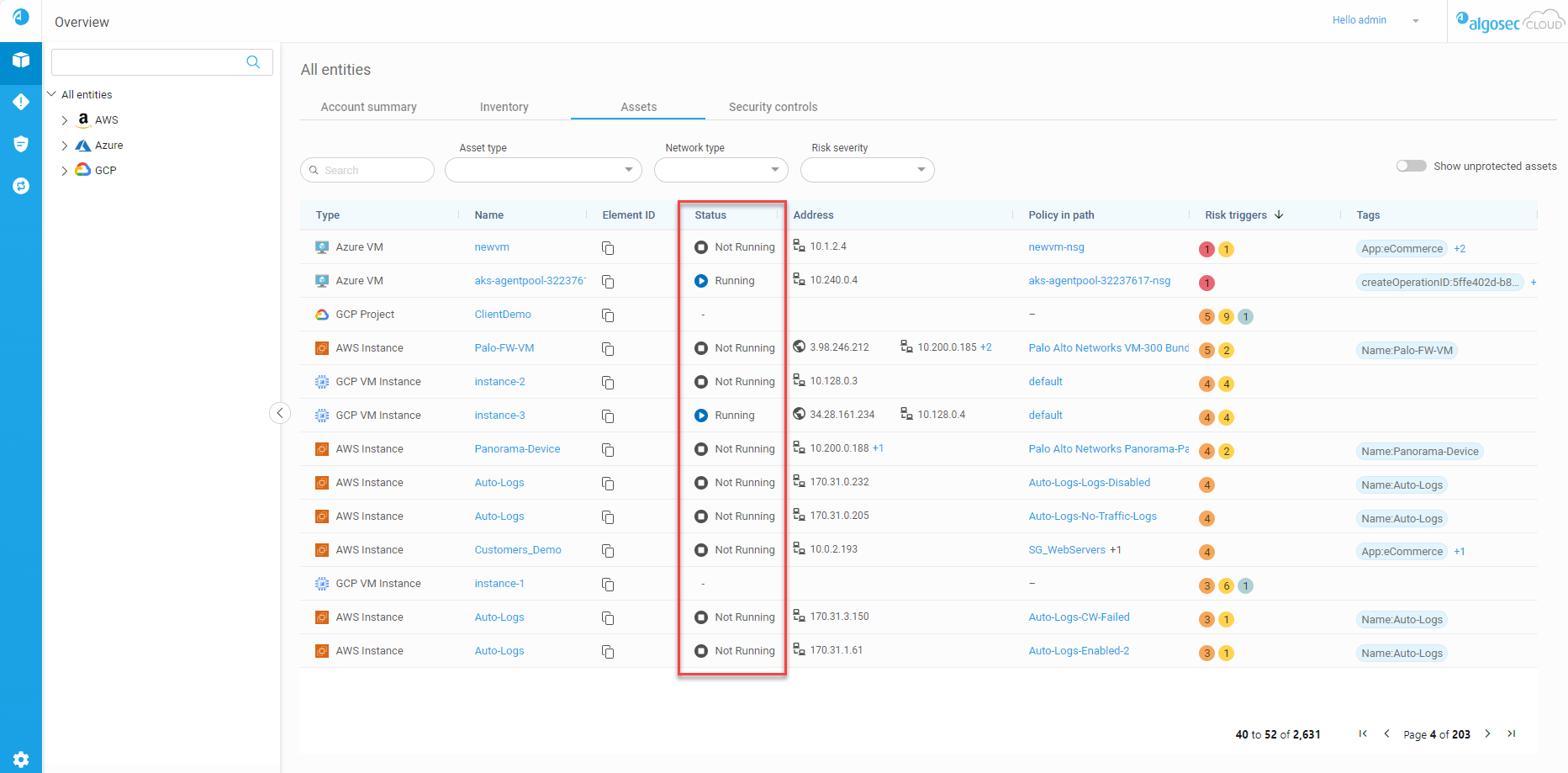
You can now see the status of your onboarded virtual machines and instances. Located in the Assets tab of the Overview page, the new Status column indicates whether or not the VM operating system and applications are running. See The Assets Tab. (Released 14-November-2023)
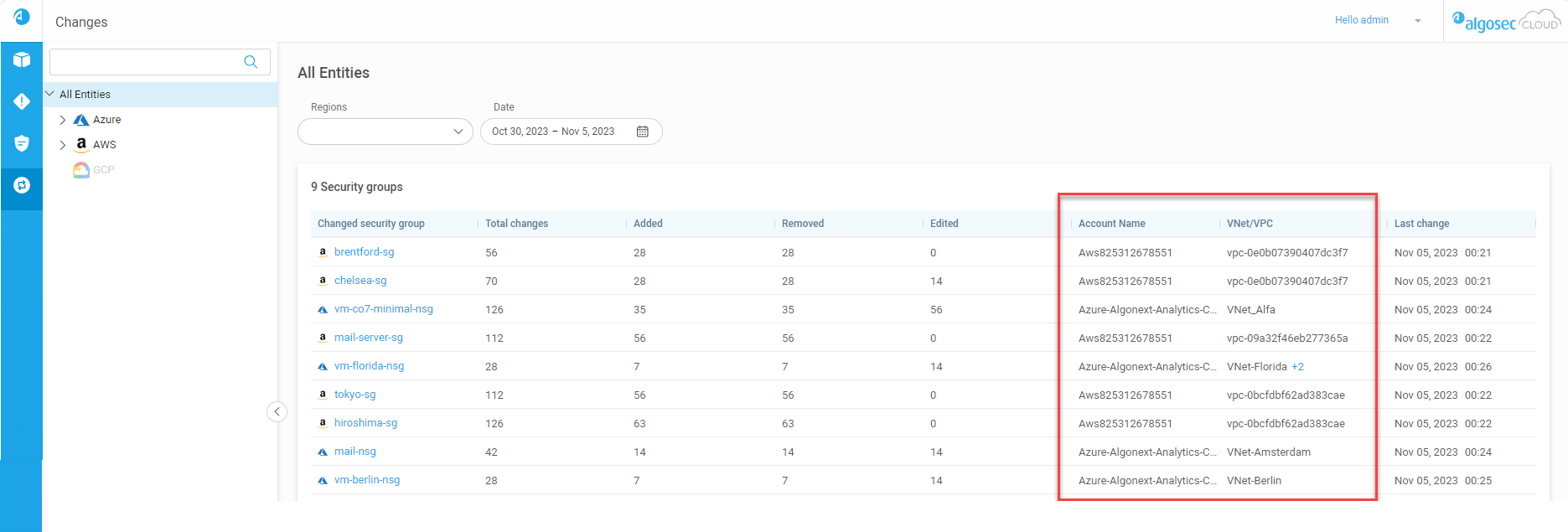
New columns on the Changes page: Account Name and Virtual Network
The Changes page now has two new columns, providing additional information for Azure and AWS about the changed security groups:
-
Account Name: The name of the subscription / account
-
VNet / VPC: The virtual network where the change was detected
For more information, see Changed Security Groups list. (Released 2-November-2023)
To streamline yourACE experience, we've removed the Home page. (Released 2-November-2023)
View ECR CD mitigation scan history
The ECR CD Mitigation Scan History Page provides a provides a scan log of each deployment of an image in the ECR repository. You can view a summary of all scan history or drill down for details of each AWS account. See Enable Threat Management on AWS ECR . (Released 29-November-2023)
Manage threats in your CI/CD pipelines
Cloud App Analyzer's Mitigation Rules are integral to the GitHub CI and the AWS ECR CD pipelines. Mitigation rules assess container images for high-risk flags. Cloud App Analyzer static scans cover malware, vulnerabilities, and dynamic scans check behavior analysis (IPs, Domains, Countries, Open Ports).
Default Mitigation Rules, sourced from government and other public databases and updated daily, include artifact items with risk severity. You can set minimum risk levels for blocking pull requests (GitHub CI) and locking repositories (AWS ECR CD). For instance, a medium-risk IP won't block a pull request if the minimum risk is set to high. Conversely, with a medium risk-setting, the same IP would trigger a block. You can also create custom block- and allow-lists. See Threat Management. (Released 16-November-2023)
CNS October 2023 Update
Export an Unused Rules Report to a CSV file
Now you can export an Unused Rules Report based on selected entities in the tree and filters (Vendor, Account, VNet/VPC, etc.), making it easy to share. See Export Policies. (Released 11-October-2023)
New Cloud App Analyzer deployment location for ANZ region
We're excited to announce the addition of a new Cloud App Analyzer deployment location for our valued users in the Asia Pacific region. We are already in the process of onboarding the first customer located in Australia. Cloud App Analyzer is now hosted on the following AWS availability zones and next in line is the EMEA availability zone as well.
-
ANZ : ap-southeast-2 (Sydney).
-
US: us-east-1 (N. Virginia)
See Logging In and Out. (Released 26-October-2023)
Extended insights for Docker container scans
We've enhanced Cloud App Analyzer CI/CD Container Security by displaying the list of your open Pull Requests right in Cloud App Analyzer. The list provides a structured view of the scan details for each open pull request, to help quickly assess and manage your security findings. Also, you can now access a full report of Docker container scans, directly from the Scan Summary comments in GitHub or from within Cloud App Analyzer, in the Pull Requests list. See Cloud App Analyzer CI/CD Container Security. (Released 22-October-2023)
Manage Your AWS ECR Repositories
Now you can integrate Cloud App Analyzer with AWS to manage ECR repositories. Automatically detect when new images are pushed to your repositories. Modify the permissions of your repositories, giving you the ability to block any pull operation for the location where the image resides. See Enable Threat Management on AWS ECR . (Released 12-October-2023)
CNS September 2023 Update
Get information to build your own account summary dashboard
ACE's new Get Account Summary Information API provides you with the data you need to build your own account summary dashboards, including information about risks and their severity, unused rules, risky assets, risks security rating, and trend. See Get account summary information API. (Released 27-September-2023)
Cloud App Analyzer CI/CD Container Security
Cloud App Analyzer CI/CD Container Security solution is an extensible security plugin platform that provides an automated scan for Docker containers. Cloud App Analyzer will build, simulate runtime, and scan the image statically and dynamically for security risks. This is integrated into the user's GitHub repository CI process. See Cloud App Analyzer CI/CD Container Security. (Released 19-September-2023)
CNS August 2023 Update
Google Cloud Project auto onboarding
With the new Google Cloud Project auto onboarding process, ACE continually syncs with your Google Cloud Projects. Any subsequent changes such as adding or removing projects are automatically reflected in ACE. See Onboard Google Cloud resources using your preferred method. (Released 22-August-2023)
CNS July 2023 Update
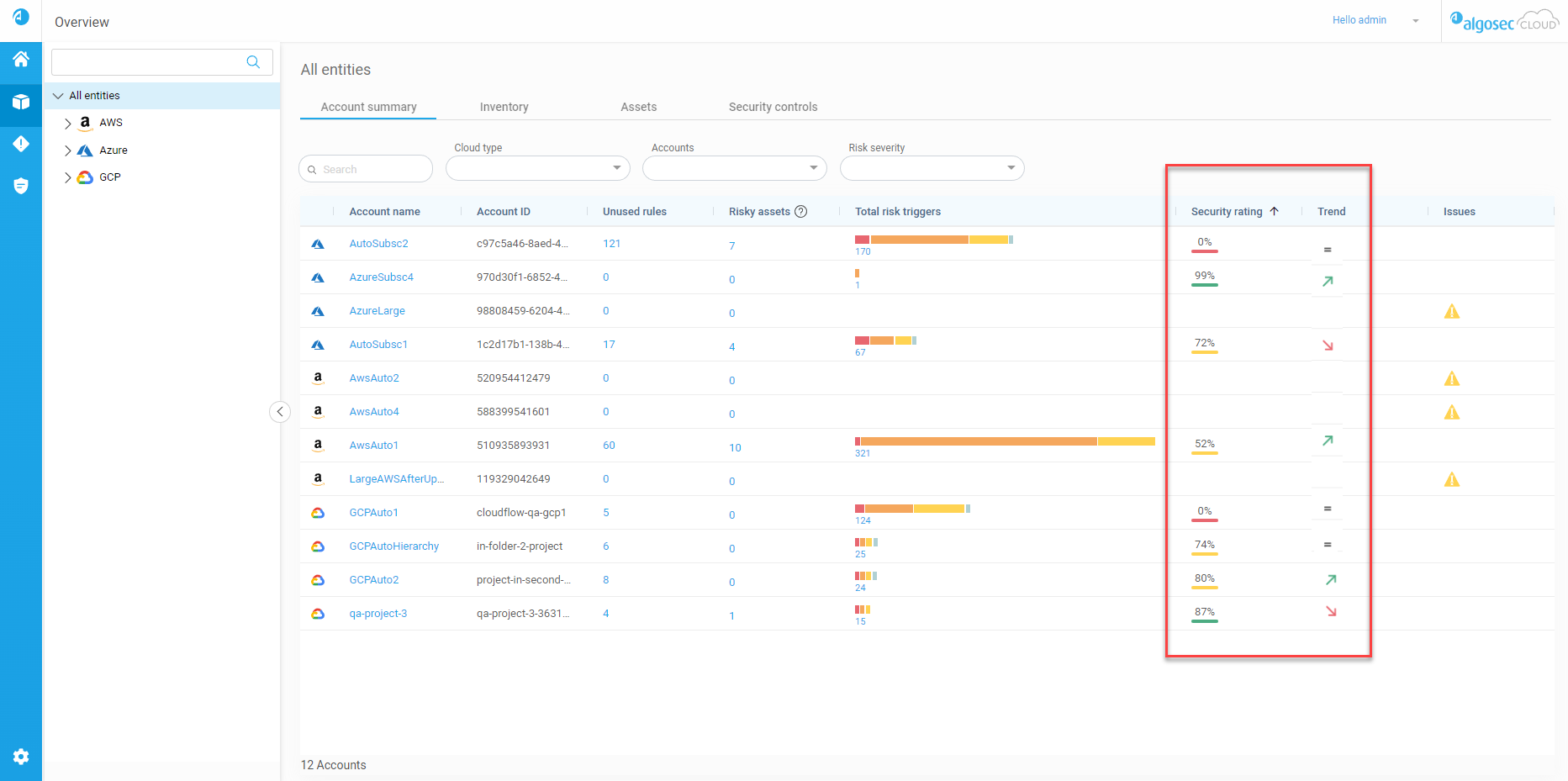
Accounts | New security rating and trend indicators
The Account Summary now includes a security rating, which shows the network security compliance level of the account. The trend indicator shows any changes in the security rating over time. See Review Account Status. (Released 31-July-2023)
On the Network Policy page, now you can click the risk severity level indicators on policies to get a detailed list of all the risk triggers associated with the policy. See The Account Summary tab. (Released 31-July-2023)
The new User Activity tab provides administrators with a convenient way to check users' adherence to established protocols and assists in the prevention and detection of fraudulent activities. Review key information such as who initiated an activity and when. For more details, see Track User Activities (Released 19-July-2023)
View Google Cloud Project unused rules
Now on the Overview page, for each project you can see the number of Google Cloud Project rules not being used. This information can assist in cleaning the policies and reducing the attack surface. Click on the number to open the Network Policies page and get the unused rules report. See Review Account Status. (Released 4-July-2023)
CNS June 2023 Update
Identify public-facing assets with risks
We've made it easier for you to spot potential issues with your assets. On the Account Summary tab, you'll now see the Risky Assets column which shows you how many of your assets with public IPs have critical or high risks. It's a quick way to identify what risks you should handle first. For more details, see The Account Summary tab. (Released 20-June-2023)
See the number of risk triggers per asset
Now on the Overview page's Assets tab, you can see the number of risk triggers associated with each asset. This allows you to quickly understand each asset's risk exposure and then take corrective steps. For more details, see The Assets tab. (Released 14-June-2023)
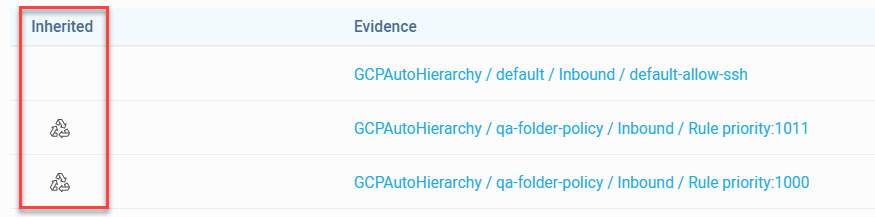
Affected Assets for Hierarchical (Inherited) Policies
ACE now displays affected assets for detected risks on all rules, including hierarchical (inherited) rules. See View rule risks & affected assets. (Released 5-June-2023)
With the new Azure onboarding process, ACE continually syncs with your Azure subscriptions. Any subsequent changes such as adding or removing subscriptions are automatically reflected in ACE. See To onboard Azure resources | With script. (Released 5-June-2023)
ACE now provides admins with a detailed explanation of account data collection failure. To learn more, see Access the Onboarding Management page. (Released 5-June-2023)
CNS May 2023 Update
Azure Native Firewall risk information
Now on the ACE Risks page, you can view Azure Native Firewall (Managed with Policies) risk information and see recommended remediation. For more info see Work with Risks. (Released 23-May-2023)
The Assets tab has a new column, Address, which displays the public and private IP address of the asset. For more info, see The Assets tab. (Released 11-May-2023)
CNS April 2023 Update
Google Cloud Project Policy Cleanup
ACE now tracks rule usage for onboarded Google Cloud Project so you can indentify unused rules for both hierarchical (inherited) rules and firewall policy rules. For more info, see Clean Up Policies. (Released 10-April-2023)
Important: Existing customers will need to add the permission Onboard Google Cloud Projects to Cloud Network Security in Google Cloud Project.
CNS March 2023 Update
-
Account Summary tab: Get a comprehensive view of your accounts
-
See all rules protecting the Google Cloud Project VPC in one place
In the new Risk Profile page, you can manage which risk profile ACE uses to calculate risks to your onboarded accounts and assets. For more details, see Manage risk profiles. (Released 22-March-2023)
Account Summary tab: Get a comprehensive view of your accounts
The renamed Overview page (previously known as Inventory) gives you a comprehensive view of your network resources. The Account Summary tab, gives you a detailed summary of all onboarded accounts, including potential risk indicators based on the activated risk profile. For more details, see Overview page tabs (Released 16-March-2023)
See all rules protecting the Google Cloud Project VPC in one place
Now you can see all the rules protecting the Google Cloud Project VPC in one place in the Network Policies tab. View VPC firewall rules and the hierarchical (inherited) rules used by that firewall. Hierarchical (inherited) rules are located above the VPC firewall rules and are distinguished by grey rows. For more details see Flattened Hierarchical View of Google Cloud Policies. (Released 1-March-2023)
CNS February 2023 Update
We've revamped the AWS onboarding process. During onboarding, ACE connects with your AWS StackSets and automatically syncs all accounts (Stacks) at once. Any subsequent changes made to StackSets in AWS such as addition or removal of accounts are automatically reflected in ACE. See Onboard AWS Accounts to Cloud Network Security. (Released 14-February-2023)
The new Changes page in ACE gives details on rule changes made on your on-boarded AWS accounts and Azure subscriptions. We will be rolling out this feature to our customers in phases during Q1 and Q2 2023, so if you still don't see it, you will soon! See View Changes History. (First released 19-November-2022)
CNS January 2023 Update
In ACE Settings, we've renamed the Accounts page to Onboarding Management and given it a UI facelift. For more details see Manage Onboarded Accounts. (Released 27-January-2023)
Official support for OKTA for SSO
AlgoSec SaaS applications now officially support OKTA as an SSO provider. See Manage Single Sign-On (SSO). (Released 27-January-2023)
IaC (Infrastructure-as-Code) Connectivity Risk Analysis
AlgoSec’s IaC Connectivity Risk Analysis solution is an extensible security plug in platform that checks code for potential vulnerabilities before any commits are made to a repository. Using it, you can accelerate application delivery taking a proactive, preventive, and collaborative approach within your CI/CD pipeline. Developers have clear visibility into risks right in the source control applications and are given clear remediation steps without a need to move to different applications or wait for security admin to manually review and approve that the code is risk free. See IaC Connectivity Risk Analysis. (Released 1-January-2023)
CNS November 2022 Update
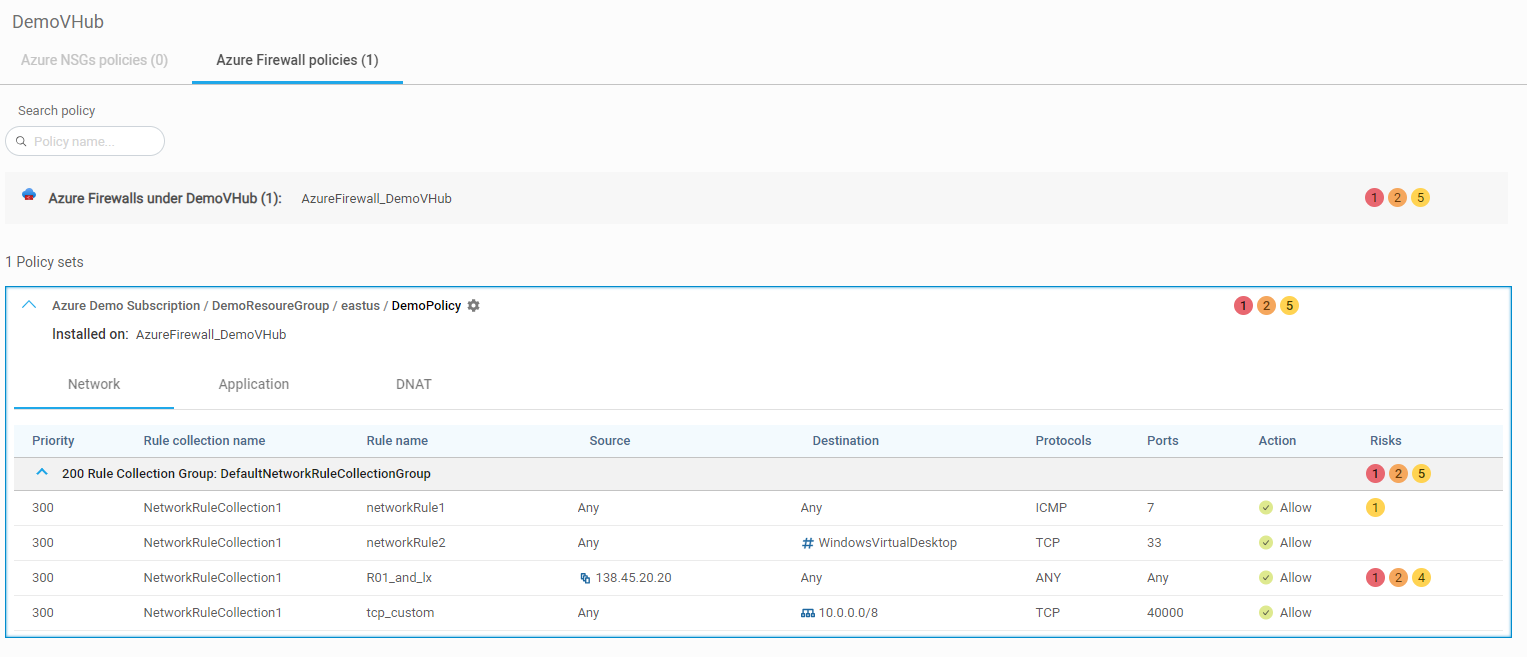
Azure Native Firewall policies
Important: Make sure you update your Azure permissions.
ACE now shows information about your Azure Native Firewall (Managed with Policies) and its network, application, and NAT rules. See Filter displayed policies. (Released 28-November-2022).
We've added new filters to the Network Policies page. Each vendor has its own unique set of filters which you can use to refine the policies displayed. See Vendor-specific filters. (Released 9-November-2022)
CNS October 2022 Update
- Documentation Enhancement: Azure, AWS, Google Cloud Project required permissions
-
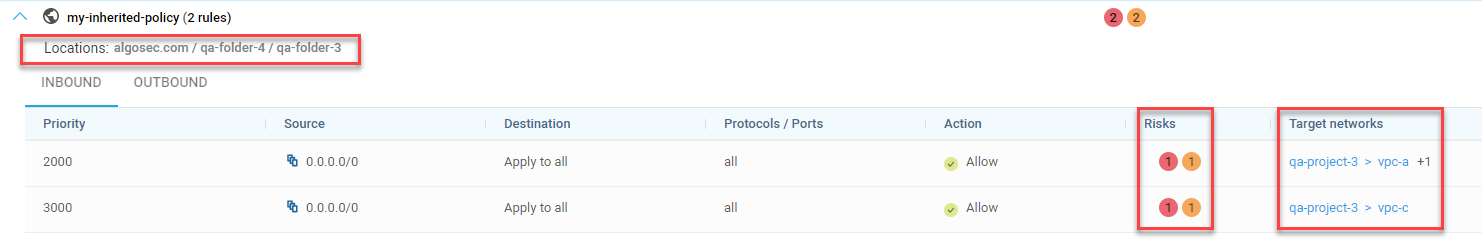
Google Cloud Project Inherited Policies Visibility and Risks
Documentation Enhancement: Azure, AWS, Google Cloud Project required permissions
You asked for it, we delivered. We’ve added a list of permissions for Azure, AWS, and Google Cloud Project. Have a look here: Azure, AWS, and Google Cloud Project. (Released 24-October-2022)
Google Cloud Project Inherited Policies Visibility and Risks
Important: Make sure you update your Google Cloud Project permissions.
ACE now displays Google Cloud Project Inherited policies:
-
On the Network Policies page, you can view details such as the folder where the inherited policy is defined, its calculated risks, and which target networks use the inherited policies.
-
On the Risks page, there is a new column indicating the risks found in rules in inherited policies.
(Released 24-October-2022)
CNS August 2022 Update
You can now log in to ACE SSO-enabled tenants with a single click. To set up SSO on a tenant, see Manage Single Sign-On (SSO). (Released 22-August-2022)
The new Protected by column on the ASSETS tab of the Inventory page helps you to understand the protection each of your VMs has and to identify unprotected assets. See Review Account Status. (Released 10-August-2022)
CNS July 2022 Update
ACE's Network Policies page added a tree structure so you can quickly navigate between cloud vendors and drill down into individual VPCs/VNets. See Manage Network Policies. (Released 18-July-2022)
The new Severity filter allows you to also filter risks by risk severity. (Released 14-July-2022)
We’ve added a new topic explaining how to work with tags in ACE. On the Risks page, filtering based on tags can focus your risk analysis and remediation specifically on the risks identified by the selected tags. A common use case for tags is to identify all assets related to applications. See Work with Tags. (Released 6-July-2022)
Minimum permissions for roles that are not Azure-built-in roles
We've added a new section detailing minimum permissions for roles that are not Azure built in roles. See Onboard Azure Subscriptions. (Released 6-June-2022)
CNS June 2022 Update
When the connection with ASMS is established, ACE by default automatically starts to collect risks from the ASMS Standard Risk Profile. You can also use a custom profile instead of the ASMS Standard Risk Profile. See Calculate risks. (Released 6-June-2022)
Cloud secure communication over HTTP tunnel connection from ASMS in A32.10
Starting from the June 6 HF of ASMS A32.10 (build A32.10.380-180), AlgoSec Cloud secure communication takes place over TLS, which by ASMS default is transported over an HTTP tunnel. The traffic that is encapsulated is encrypted with the Public Key certificate mechanism. The HTTP tunnel can run with or without a customer proxy server. See ASMS-AlgoSec SaaS trust and communication. (Released 6-June-2022)
Cross account flow logs for S3 bucket
You now can create cross account flow logs for your S3 (Simple Storage Service) bucket in AWS. See Enable VPC flow logging for S3. (Released 13 June-2022)
CNS May 2022 Update
Cloud secure communication over HTTP tunnel connection from ASMS in A32.20
New to ASMS A32.20, ASMS-AlgoSec Cloud secure communication takes place over TLS, which by ASMS default is transported over an HTTP tunnel. The traffic that is encapsulated is encrypted with the Public Key certificate mechanism. The HTTP tunnel can run with or without a customer proxy server. See ASMS-AlgoSec SaaS trust and communication. (Released 2-May-2022)
CNS April 2022 Update
Custom Roles or System Roles can be assigned to users
Custom roles define accounts as managed, read-only or with no permission for the users to which these roles are assigned. This lets administrators control which accounts users can see or manage. Like system roles, multiple custom roles can be applied to one user. However custom roles and system roles cannot be applied to the same user. See Custom Roles (Released 22-Apr-2022)
CNS March 2022 Update
The total number of policies risks and risks per rule of each severity level are displayed for policies listed in the Network Policy tab. (Released 14-Mar-2022)
Google Cloud Project Network Risks Support
Google Cloud Project Risks are now displayed on the ACE Risks page, providing complete visibility and access to risks across all your on-boarded Google Cloud Project accounts. See Work with Risks. (Released 7-Mar-2022)
Updated AlgoSec Cloud Services Security Practices
We've added new information. See AlgoSec SaaS Services Security Practices (Released 1-Mar-2022)
CNS February 2022 Update
List of minimum required Azure Permissions
This list of limited permissions will simplify onboarding Azure subscriptions. See Onboard Azure Subscriptions (Released 17-Feb-2022)
CNS January 2022 Update
Third-party software components
A list of third-party software components used in AlgoSec cloud applications is now available on the portal Documentation Resources page (under AlgoSec Cloud Documentation). (Released 6-Jan-2022)
CNS December 2021 Update
Reset Password from the ACE Access Management UI
A ACE Admin can reset a user's password. See Reset Password. (Released 22-Nov-2021)
All ACE users can create Risks Reports. Risks Report presents a snapshot of risks and risk triggers found at a specific time based on the filters selected by the user requesting the report. See Export risk and risk trigger details and Work with Risks. (Released 27-Dec-2021)
CNS October 2021 Update
ACE's October 2021 update provides the following new features:
Manage API Access Keys from the ACE Access Management UI
ACEsupports managing access keys for use with AlgoSec APIs. See Manage API Access Keys. (Released 18-Oct-2021)
Support for running Admin and Risks APIs from the API Documentation
To access the ACE APIs, click on this link: api-docs.algosec.com or the link:  at the top of the ACE online documentation landing page. (Released 18-Oct-2021)
at the top of the ACE online documentation landing page. (Released 18-Oct-2021)
CNS August 2021 Update
ACE's August 2021 update provides the following new feature:
ACE now supports three built-in user roles. For details, see Manage User Roles. (Released 11-Aug-2021)
For a selected risk, export the details of the associated risk triggers. For details, see Export risk and risk trigger details. (Released 11-Aug-2021)
CNS June 2021 Update
ACE's June 2021 update provides the following new feature and bug fixes:
Initial Support for Google Cloud
ACEnow supports Google Cloud in preview mode - Onboarding Google Cloud Projects and Inventory. For details, see Onboard Google Cloud Projects to Cloud Network Security. (Released 21-Jun-2021)
-
AWS accounts data collection status is displayed as “Failure” when one or more regions in the target account are disabled. ACE now skips disabled regions. (SUP-14932, 9-Jun-2021)
-
The network policies interface may be unusable when the system is onboarded with a large number of cloud accounts. The relevant DB queries have been enhanced and the underlying infrastructure was scaled-up to accommodate for large accounts. (SUP-14896, 31-May-2021)
-
The network policies interface may be unusable when the system is onboarded with a large number of cloud accounts. The relevant DB queries have been enhanced to accommodate for large accounts. (SUP-14519, 1-May-2021)
CNS April 2021 Update
ACE's April 2021 update provides the following improvement:
Multi-factor Authentication (MFA) enforcement option
ACE now provides the option of setting Multi-factor Authentication (MFA) enforcement for secure user login. For details see Logging In and Out and Manage Users. (Released 12-Apr-2021)
CNS March 2021 Update
ACE's March 2021 update provides the following improvement:
In addition to the ability to filter risks for cloud types, accounts and regions, you can now focus your risk analysis and remediation on specific categories of risks identified by tags (key/value combinations) applied to the cloud platform assets.
Customers can leverage this capability to focus on analyzing and remediating risks related to specific applications. For example, the tag filter App: eCommerce can be used to review all the risks related to the eCommerce application. See Work with Risks (Released 15-Mar-2021)
CNS February 2021 update
ACE's February 2021 update provides the following improvement:
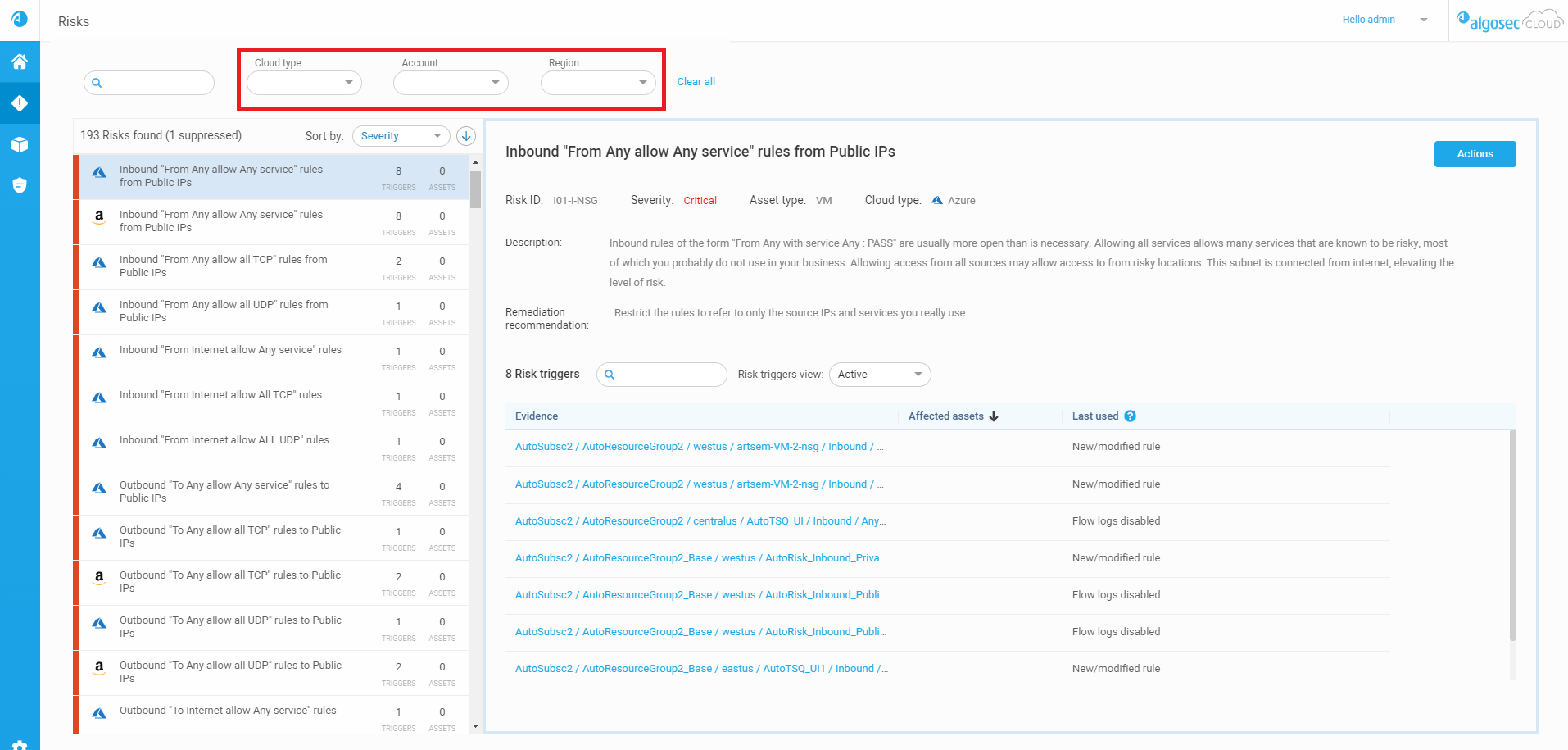
Easily focus on your risks and risk triggers of interest using the Cloud type, Account and Region filters at the top of the Risks page. Each of these optional filters can accommodate multiple values. You can quickly shorten the list of available filter values by typing in the filter field. See Risk filters (Released 9-Feb-2021)
CNS January 2021 update
ACE's January 2021 update provides the following improvement:
The risks page has been redesigned to provide a better and easier user experience. The complete list of risks and all details for the selected risk, including all risk trigger details, are accessible from one page. This avoids generation of multiple tabs and the need for browsing between those tabs. For details see Work with Risks (Released 4-Jan-2021)
CNS December 2020 update
ACE's December 2020 update provides the following new features and bug fix:
You are now able to establish trust between ACE and ASMS. This integration allows hybrid functionality such as Check connectivity over the hybrid network. For details about establishing this trust, see ACE - ASMS Integration. (Released 28-Dec-2020)
Check Connectivity for the Hybrid Network
You are now able to run a connectivity check (traffic simulation query) on an Azure NSG rule to observe how traffic is routed and whether it is allowed across your entire hybrid network (i.e. across NSGs, firewalls routers etc., deployed on cloud and/or on-prem). For details see Check connectivity for the hybrid network (Released 28-Dec-2020)
Data collection failure for Azure subscriptions having a large number of storage accounts. Excessive data collection requests resulted in Azure API rate limiting. Relevant API call has been enhanced to collect the same data in fewer requests. (SUP-12908, 7-December-2020, SUP-13120, 28-December-2020)
Note: Although this seems identical to the release note (regarding SUP-11388 and SUP-12111) below, the customer Azure setup in each case was different and the solutions are different.
CNS November 2020 update
ACE's November 2020 update provides the following new and improved features:
AWS VPC Flow Logs Collection from CloudWatch
ACE is now able to collect AWS VPC Flow Logs from CloudWatch (in addition to the existing ability to do the same from S3 buckets).
This provides better flexibility for customers that wish to enjoy ACE rule cleanup and rule usage capabilities with logs stored on CloudWatch.
For more details, refer to VPC Flow Logs. (Released 16-Nov-2020)
Suppressing risks and risk triggers
Risks and risk triggers can now be suppressed (i.e. acknowledged) to ensure a shorter risks list and avoid reviewing risks and risk triggers you trust and consider as “noise”.
For more details, refer to Suppress/Activate risks and risk triggers. (Released 9-Nov-2020)
New individual admin users can now be added and managed from the ACE interface. For more details, refer to Manage Users. (Released 2-Nov-2020)
CNS October 2020 update
ACE's October 2020 update provides the following issue resolution:
Resolved/Optimized:
Data collection failure for Azure subscriptions having a large number of storage accounts. Excessive data collection requests resulted in Azure API rate limiting. The relevant API call has been enhanced to collect the same data in fewer requests. (SUP-12111, 5-Oct-2020)
Note: Although this seems identical to the release note (regarding SUP-11388, 14-Sep-2020) below, the customer Azure setup in each case was different and the solutions are different.
CNS September 2020 updates
ACE's September 2020 update includes several resolved issues:
Resolved:
- Rule usage was not shown for AWS Security Groups policy rules when VPC Flow Logs were sent for both CloudWatch and S3. (CloudWatch is not supported by ACE). Now, the sending of CloudWatch VPC Flow Logs does not negatively affect the ACE rule usage display, which is based on S3 log data. (SUP-11782, 14-Sep-2020)
- For large AWS accounts with a large number of Security Groups, not all the security groups were displayed on the AWS SGs network policies interface. (CS-2980, 14-Sep-2020)
- When using the Azure subscription PowerShell setup script, the "Contributor" role may be assigned to a different subscription from the one the user selected.
Note: The issue originates from a recent change Azure did in the relevant API.(CS-2969, 14-Sep-2020)
Resolved/Optimized:
- Data collection failure for Azure subscriptions having a large number of storage accounts. Excessive data collection requests resulted in Azure API rate limiting. The relevant API call has been enhanced to collect the same data in fewer requests. (SUP-11388, 14-Sep-2020)
CNS July 2020 updates
ACE's July 2020 update provides the following enhancements and bug fix:
- Improved Azure risk triggers/affected assets calculations
- New option facilitates NSG resource logs collection permissions
- Azure Scale Sets support
- Bug fix
Improved Azure risk triggers/affected assets calculations
Azure NSG risk triggers and affected assets calculations have been improved. For details, see Work with Risks.
New option facilitates NSG resource logs collection permissions
An option has been added in the Azure subscription PowerShell setup script. The option assigns roles required for NSG resource logs collection.
ACE now collects Azure Virtual Machine Scale Sets configurations.
The VM parts of Scale Set data are
- displayed as VM records in the Inventory section
- taken into consideration in risk calculation, and
- displayed as affected assets in the Risk interface.
The flickering of Inventory Asset and Security Control lists in high-magnitude zoom or on large screens has been eliminated.
CNS June 2020 updates
ACE's June 2020 update provides the following enhancements:
- New login screen
- AWS SG rules cleanup support
- Unused rules on-the-fly analysis time modification
- ICMP support for Azure NSG rules
- Policy rule count
A new login screen has been introduced, allowing the user to submit all the login credentials in one screen.
During first-time login, Admin users can now provide their email. This enables them to reset their password at any time, using the Forgot Password button.
Cloud security groups are constantly adjusted, and can bloat rapidly. This makes cloud security groups difficult to maintain, and increases potential risk.
When viewing AWS SG policies , ACE now provides a Cleanup view that enables you to show unused rules only.
For example:
Use this Cleanup view when optimizing your network policies by removing rules that may no longer be required because they are no longer in use.
For more details, see Clean Up Policies.
Note: To view last used data for AWS SGs, you must have flow logs enabled for each relevant SG. For more details, see Enable AWS VPC flow logging.
Unused rules on-the-fly analysis time modification
In the both the AWS SGs policies page and the Azure NSGs policies page, the analysis time criteria for unused rules can be changed on-the-fly. A rule's last-used column shows the last-used date or "no traffic logged".
Note: This requires flow logging / resource logging to be enabled for the relevant AWS VPCs and/or the relevant Azure NSGs.
ICMP support for Azure NSG rules
The ICMP protocol is now supported for Azure NSG rules.
As of June 2020 Azure does not enforce ICMP sub-types (even if the user configured a source or destination port along the ICMP protocol.)
Policy rule counts are displayed on policy pages. They indicate the number of rules per policy or group of policies, or the number of rules filtered or searched (i.e. all, unused, and filtered by search criteria).
CNS April 2020 updates
ACE's April 2020 update provides the following enhancements:
Enhanced central policy management
ACE's NETWORK POLICIES area has been redesigned to provide a smoother flow for viewing and editing your network policies.
Main user interface updates include the following:
-
Policy tree and unified policy management
The NETWORK POLICY tree now displays only AWS SG policies, Azure NSG policies, and Azure Firewall (classic). Click an item to view and manage all policies for the selected type on a single page.
For example:
On the page for each type, ACE displays both policies with only one security control, such as a single AWS Security Group, and policies with multiple, similar, security controls.
-
All security controls are automatically part of a policies
Each individual security control is now assigned to a default policies . Search for similar security controls to merge them as needed.
For example:
Note: Since each policy now has a default policies , you no longer need to create a new policies from scratch. Instead, merge similar policies to create a new, central policies .
For more details and updated instructions for viewing, editing, merging, and dissolving policies , see Merge policies .
Cloud security groups are constantly adjusted, and can bloat rapidly. This makes cloud security groups difficult to maintain, and increases potential risk.
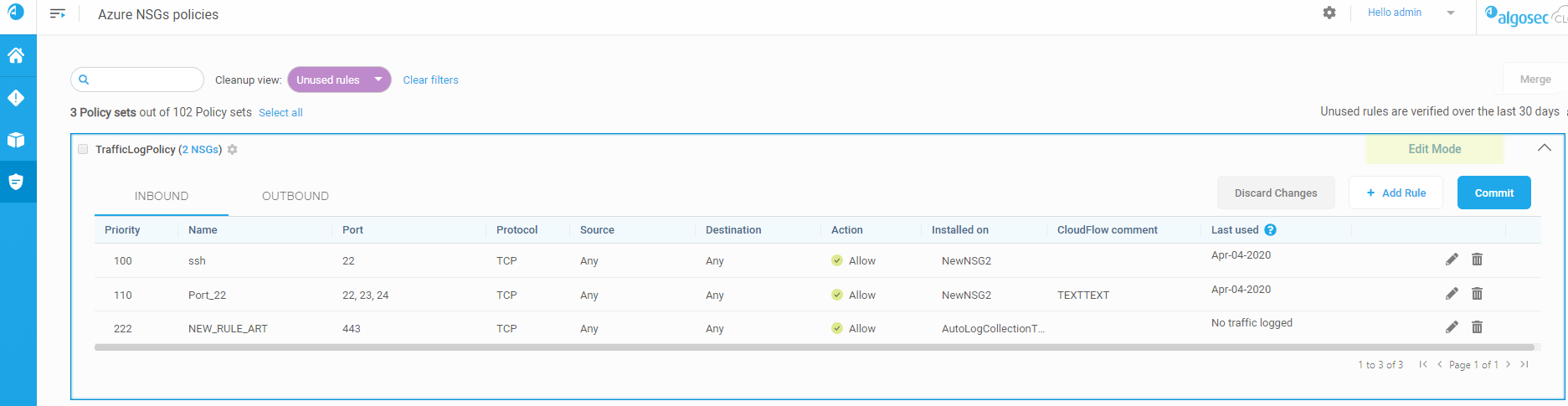
When viewing Azure NSG policies , ACE now provides a Cleanup view that enables you to show unused rules only.
For example:
Use this Cleanup view when optimizing your network policies by removing rules that may no longer be required because they are no longer in use.
For more details, see Clean Up Policies.
Note: To view last used data for Azure NSGs, you must have flow logs enabled for each relevant NSG. For more details, see Enable Azure resource logs for traffic analysis.
CNS March 2020 updates
ACE's March 2020 update provides the following updates:
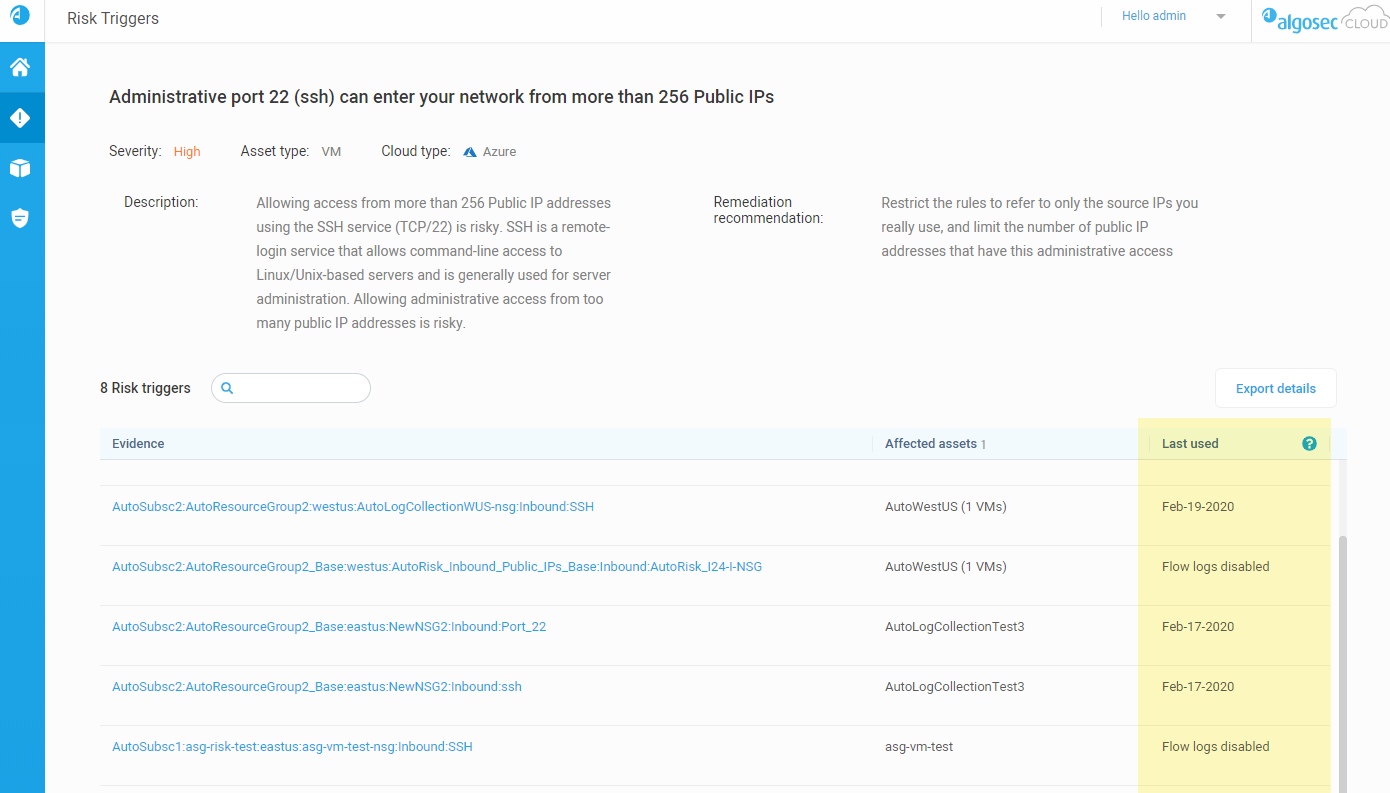
Last used rule data for Azure NSG risks
ACE now enables you to view the last date a specific rule was used on the risk triggers details page, for Azure NSGs. This data is based on your NSG resource logs, and helps you to clean up your NSG network policies by identifying rules that have little or no use.
We recommend removing rules that are not in use to keep your policies clean and simple.
The last used column displays one of the following values:
- A date, which is the last date that a rule was used, or triggered. ACE analyzes rule usage in the last 30 days only
- No traffic logged, if the rule was not used at all during the last 30 days
- Flow logs disabled, if resource logs are not enabled for the relevant NSG
In order to display rule usage data, you must enable resource logging for your NSG. You can do this for each NSG manually in the Azure console, or for multiple NSGs using a script provided by ACE.
ACE will automatically start to collect resource log data for any NSG with resource logging enabled, even if it was added to ACE at an earlier time.
Tip: We recommend that you enable resource logs whenever provisioning a new NSG on your subscription, and even configuring your system to automatically enable resource logs when provisioning a new NSG.
For more details, see Enable Azure resource logs for traffic analysis.
Azure NSG risk enhancements
ACE's risk analysis now supports Azure NSG rules with Service tags or Application security groups (ASGs).
For more details, see Work with Risks.
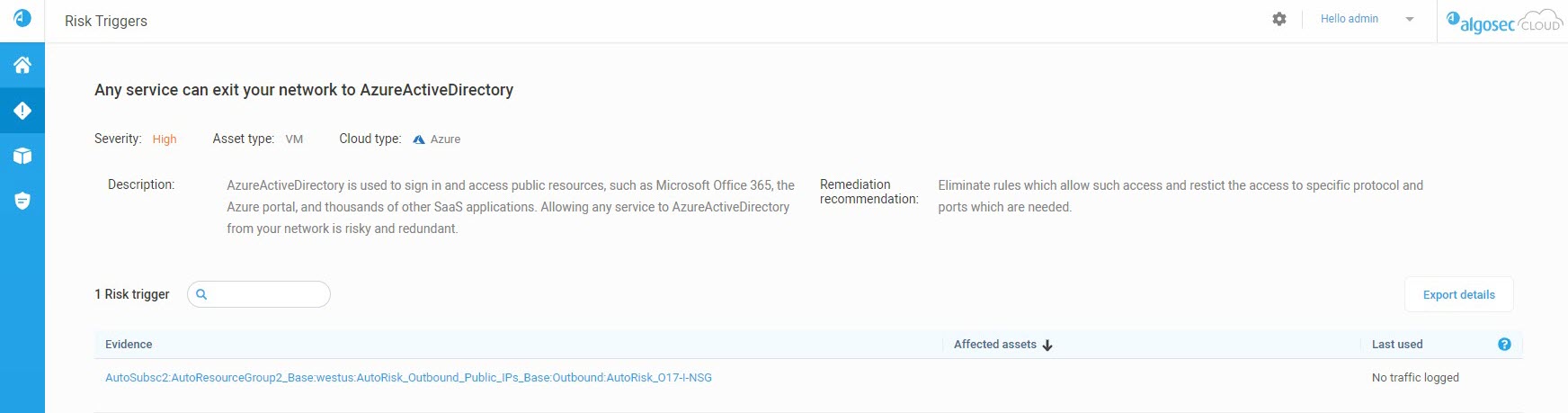
Service tag support
In addition to detecting risks for Azure rules with Service tag values, ACE has specific risks for Service tag definitions.
For example, the following image shows a risk that is triggered for any Azure rule or NSG where the destination is selected as the ActiveDirectory service tag, and the destination port is any:
ASG support
ACE detects network risks for rules consisting of Azure ASGs by identifying the ASG network content and calculating risks accordingly.
CNS January 2020 updates
ACE's January 2020 update provides the following updates:
Azure NSG network risks
ACE now supports risks detected in Azure NSGs.
For example, in the ACE RISKS area, view both AWS SG and Azure NSG risks and their full details.
For more details, see Work with Risks and Onboard Azure Subscriptions.
Streamlined risk trigger remediation
Risk trigger details pages now also include hyperlinks directly to the relevant policies for each trigger item.
Click a link in the Evidence column to jump to the relevant policy.
A new tab is opened to display the policies . There, the relevant rule is highlighted and you can edit the policy to make any changes needed.
For example, modify or remove the offending rule to avoid allowing risky traffic.
For more details, see View risks and risk details and Policy details.
CNS Earlier updates
Click through the following to read ACE's release notes from earlier releases:
The November 2019 update includes the following features and enhancements:
- View all network policies per type
- Edit a policies name, description, and members, or dissolve a set
- Unassigned security controls
- Export risk triggers to CSV
- Add cloud provider accounts as read-only
- Azure NSG and SG Description fields
View all network policies per type
ACE now provides a high-level view of all network policies of a specific type, either Azure Firewall (classic), Azure NSGs, or AWS SGs.
In the Network Policies navigation tree, click a parent node to view all sets of the selected type. For example:
The selected type of policies is displayed in a grid. For example:
For more details, see Manage Network Policies.
Edit a policies name, description, and members, or dissolve a set
The policies grid that displays all sets of a specific type enables you to drill down to each set, as well as edit high level details or dissolve a set altogether.
For example:
Note: Dissolving a set only removes that set from ACE, and lists related security controls as unassigned. Policy rules in each member policy are left intact.
For more details, see Work with Policies and Unassigned security controls.
If you have accounts managed by ACE with security controls that are not assigned to a ACE policies , ACE now highlights these controls in the NETWORK POLICIES navigation tree.
Click a set of unassigned firewalls, NSGs, or SGs to display the list and assign items to either a new or an existing policies .
For example:
For more details, see Manage Network Policies.
Now you can export a list of risk triggers detected by ACE. This enables you to access essential details such as public IP addresses, and enables further analysis and easy sharing.
The downloaded CSV file includes a full list of triggers for the selected risk, all affected assets, and the relevant private and public IP addresses.
In a Risk Triggers page, click Export details to download your CSV file.
For example:
For more details, see Work with Risks.
Add cloud provider accounts as read-only
You may want to add cloud accounts or subscriptions to ACE for read-only analysis purposes, without enabling any changes to be made from ACE.
Now you can do this by determining read-only permissions for both AWS and Azure.
Determine read-only or read/write permissions when adding the account to ACE. For more details, the updated procedures in Onboard Azure Subscriptions and Onboard AWS Accounts to Cloud Network Security.
Azure NSG and SG Description fields
In Azure NSG and SG rules, the field that was previously labeled Description has been renamed to ACE Comment.
We renamed this field to clarify that this comment is based in ACE only. Your Azure Description field value remains unchanged, regardless of the updates you make in ACE.
For example:
For more details, see Manage Network Policies and Field Reference per Rule Type.
The October 2019 update includes the addition of the RISKS module to ACE.
Note: The RISKS module is supported in Early Availability mode, and currently includes only network risks triggered by AWS security groups.
Click the  RISKS item from the menu on the left to display a list of all the security risks detected in your ACE accounts.
RISKS item from the menu on the left to display a list of all the security risks detected in your ACE accounts.
Risks are displayed in a grid that provides an overview of your risk data. Click a specific row to show more details about the selected risk on the right.
For more details, see Work with Risks.
September 2019 updates include the following:
- AWS S3 buckets displayed in the inventory
- View asset and security control details
- Azure Firewall (classic) service tag support
- AWS Security Group ICMP support
- Performance enhancements
AWS S3 buckets displayed in the inventory
The ACE dashboard now shows AWS S3 buckets in the AWS > ASSETS area and on the ASSETS tab.
For example:
For more details, see Review Account Status and Onboard AWS Accounts to Cloud Network Security.
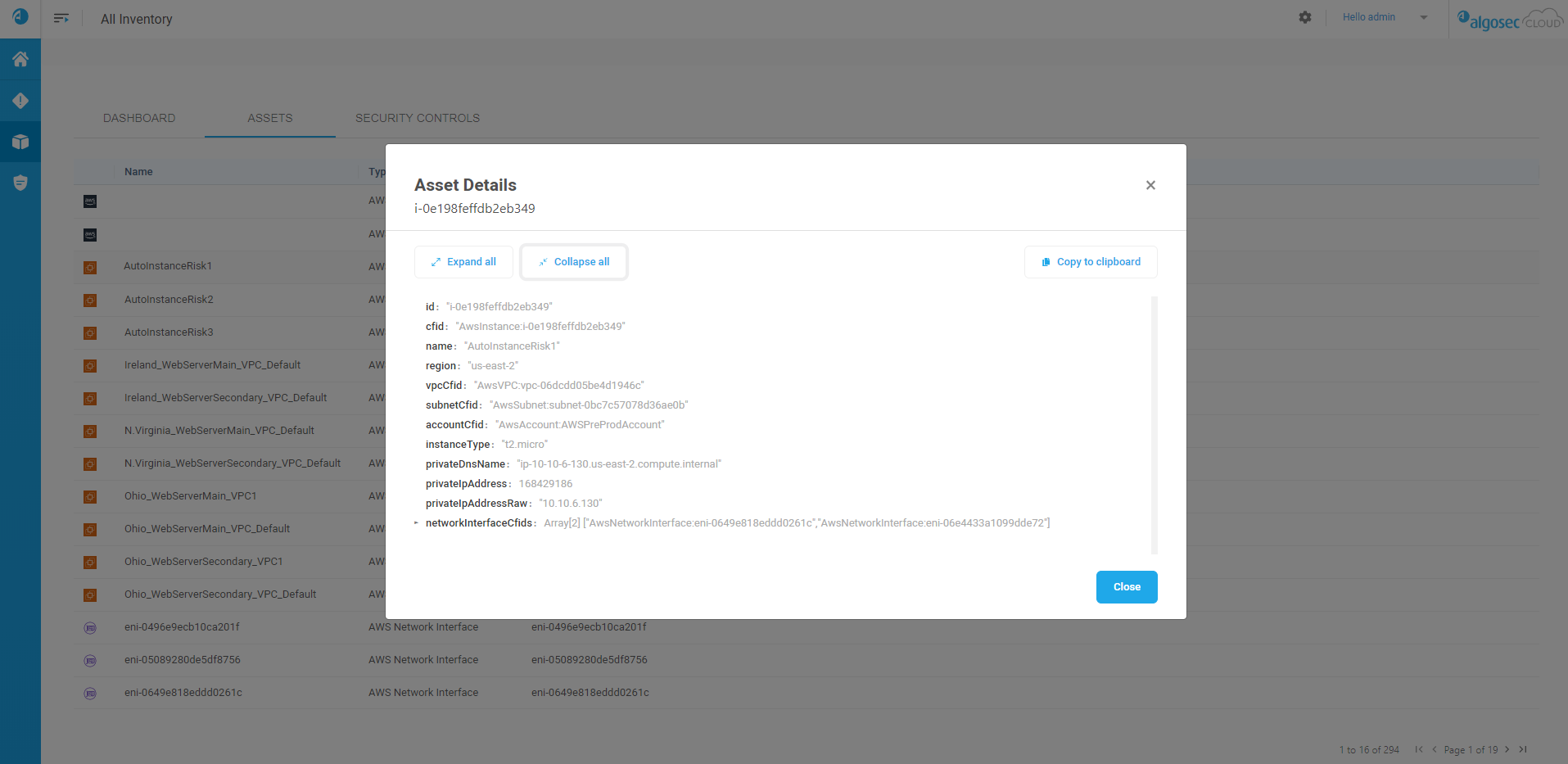
View asset and security control details
Now you can access full details about your assets and security controls from the ACE inventory.
On the INVENTORY page, click the ASSETS or SECURITY CONTROLS tabs to view lists of available items in your inventory.
Click an item to view it's details. For example:
In the Asset or Security Control details dialog, click:
- Expand All or Collapse All to view more or fewer details
- Copy to clipboard to copy the full list of details elsewhere
For more details, see Review Account Status and Onboard AWS Accounts to Cloud Network Security.
Azure Firewall (classic) service tag support
ACE now enables you to select one or more service tags as the destination in a network rule on Azure Firewall (classic).
For example:
For more details, see Manage Network Policies and Field Reference per Rule Type.
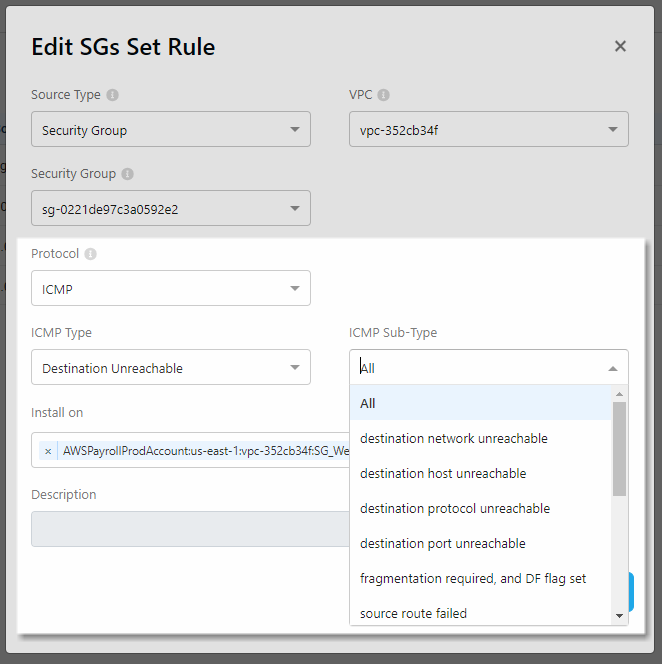
AWS Security Group ICMP support
In AWS SGs policies , define rules with specific ICMP types. Depending on the ICMP type you select, you may also be able to select an ICMP sub-type.
For example:
For more details, see Manage Network Policies and Field Reference per Rule Type.
We've enhanced ACE's performance to support thousands of security groups.
Add your account to ACE today! For details, see Onboard AWS Accounts to Cloud Network Security.
August 2019 updates include the following:
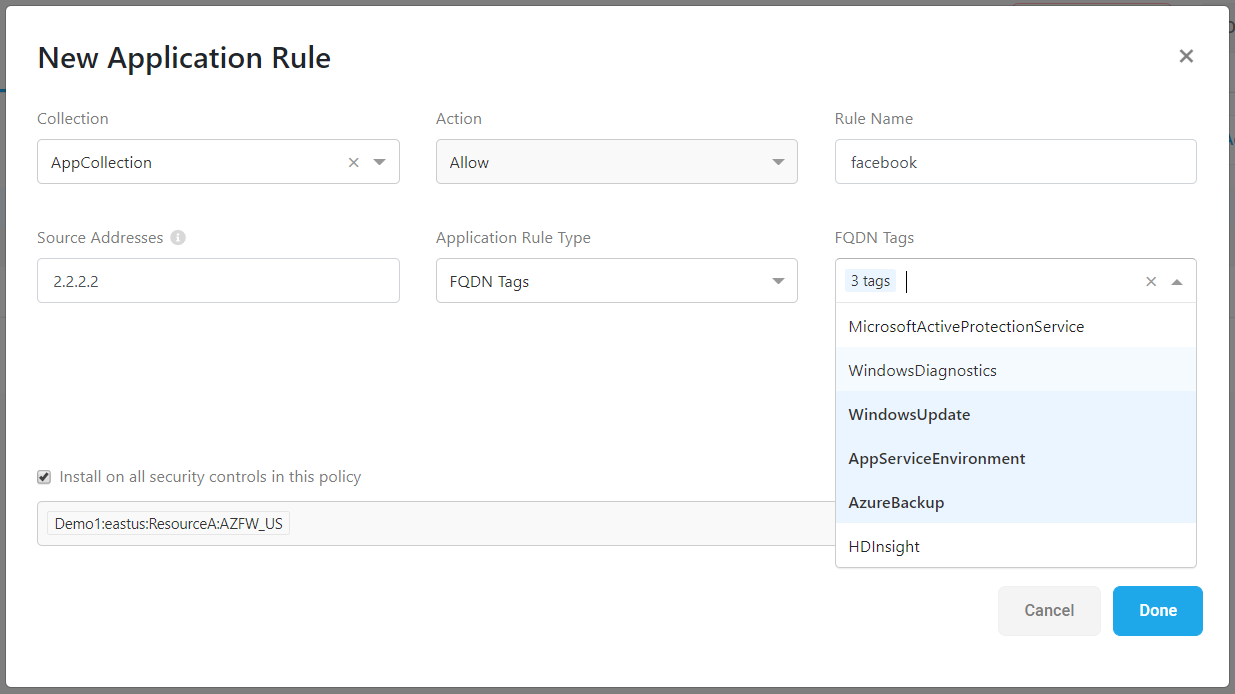
FQDN support in Azure Firewall (classic) application rules
ACE now enables you to define FQDN tags or specific target FQDNs in an application rule on Azure Firewall (classic).
For example:
For more details, see Manage Network Policies and Field Reference per Rule Type.
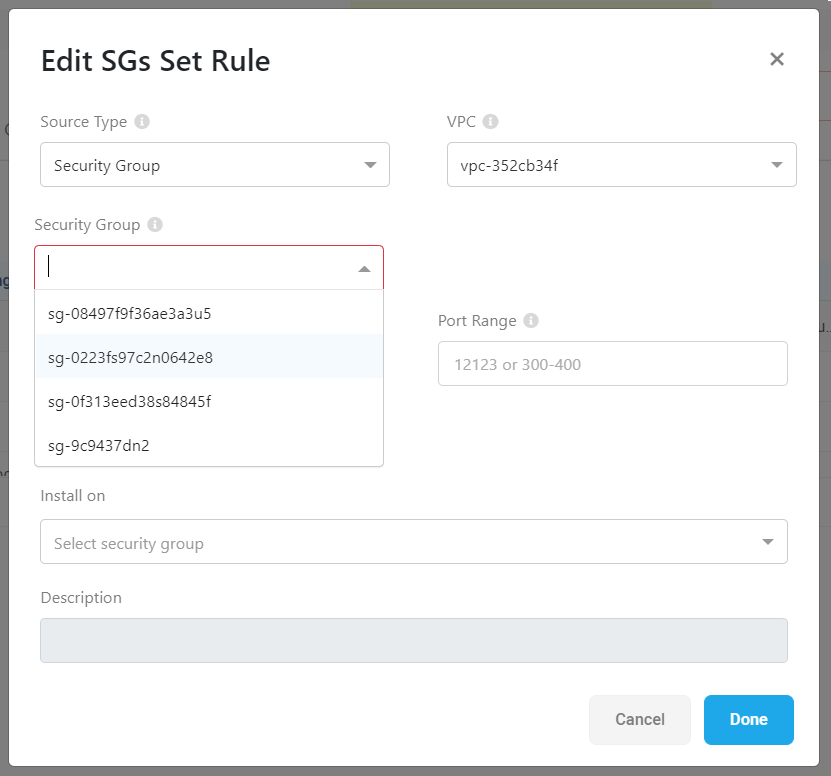
Security groups in AWS SG rules
ACE now enables you to set a security group as the source in a rule on AWS rules.
For example:
For more details, see Manage Network Policies and AWS SGs (Security Groups) controls.
July 2019 updates include the following:
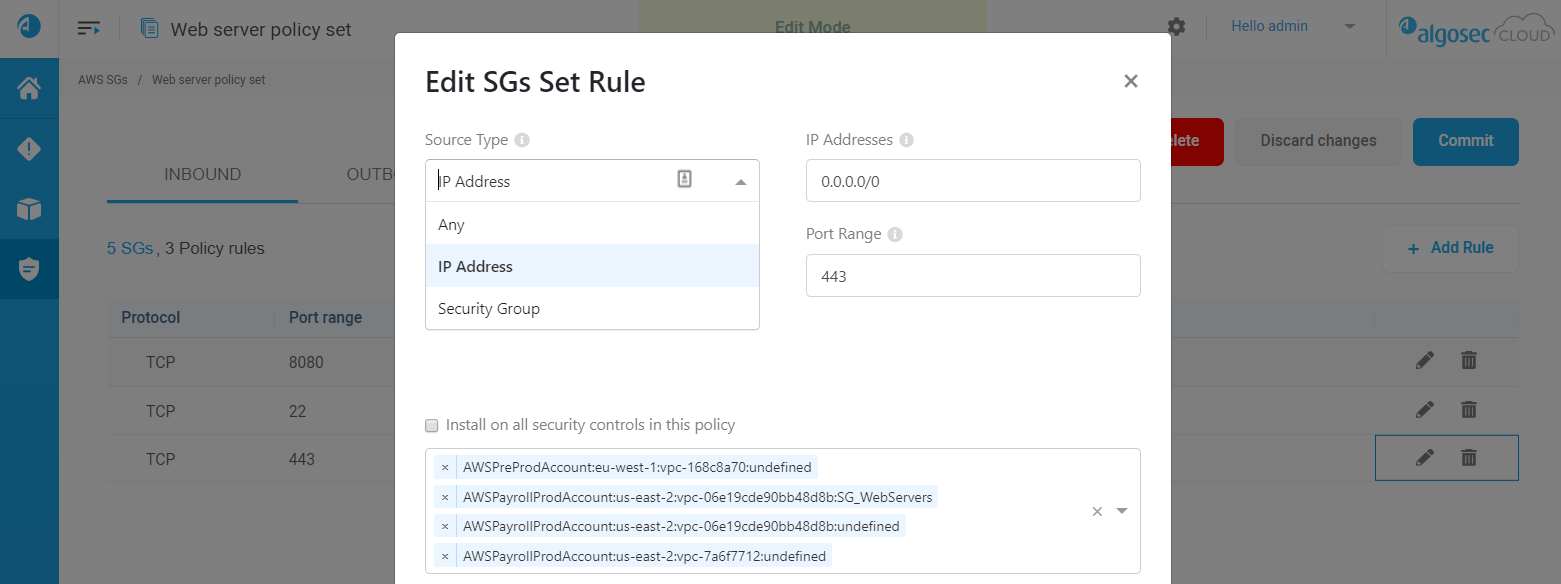
ACE now supports the ability to onboard AWS accounts to your ACE tenant, enabling you to manage your AWS network policies and view inventory from ACE.
For example, the following image shows a rule being edited in a network policies for AWS SGs:
To add an AWS account to ACE, you'll need to create a new ACE role in AWS.
ACE provides a CloudFormation template to help you create this role, or you can create it manually. For details, see Permissions Required for AWS Accounts
When modifications are made to network policies from ACE, such as adding or updating a rule, ACE now displays the status of those modifications.
For example, any failed updates are indicated above the rule table:
For more details, see Manage Network Policies.
May 2019 updates include:
- Network policies for Azure NSGs
- Security controls in your ACE inventory
- Usability updates
- Stability bug fixes
Network policies for Azure NSGs
ACE now supports Azure Network Security Groups. This enables you to create network policies for Azure NSGs, allowing you to view and manage your Azure NSG policies from a central location. This feature also supports Application Security Group (ASG) configurations.
For more details, see Manage Network Policies.
Security controls in your ACE inventory
The ACE inventory is automatically updated, and represents your cloud security assets. ACE now supports the ability to view the list of security controls associated to the accounts in your inventory.
Use the navigation tree to browse through your ACE inventory and view the security controls in each segment of your cloud estate.
Note: Inventory support for security controls currently includes NSGs and Azure Firewall (classic).
For more details, see Review Account StatusReview Account Status.
ACE now continuously monitors your configured cloud assets. This automatically synchronizes your ACE inventory and network policies s without requiring you to re-add your Azure subscriptions.
Each new version of ACE brings additional usability updates to enhance your ACE experience.
Among other updates, this version of ACE includes breadcrumbs at the top of each page to help you keep context of where you are in ACE.
For example:
This version of ACE includes the following bug fixes:
CS-486: When changes are made to a network policies and the page refreshes, ACE now retains the context and keeps you in the same place that you were viewing or editing before the refresh.
For more details, see Manage Network Policies.
CAA January 2026 Update
Dashboard Enhancement: Custom Date Range Filtering
The Misconfiguration Trends graph in the Dashboard now supports custom date range filtering, allowing you to select specific start and end dates instead of using only predefined ranges. See Explore Configuration and Misconfiguration Trends. (released 6-January-2026)
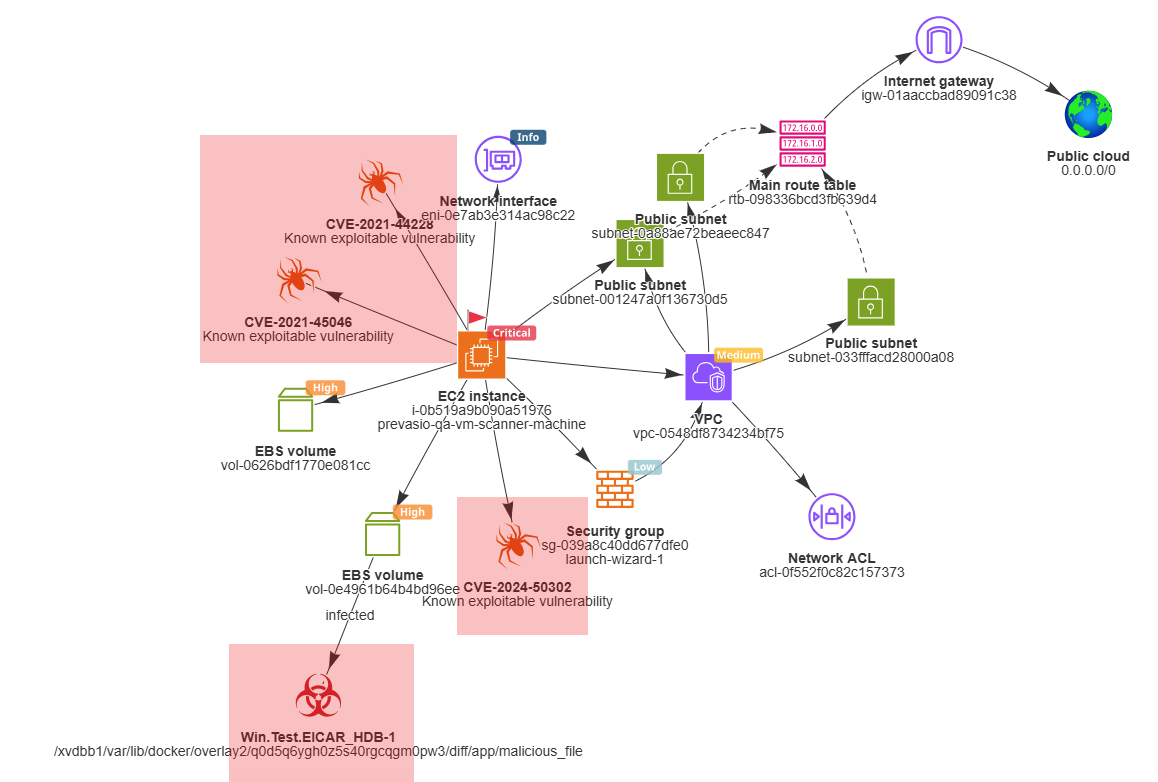
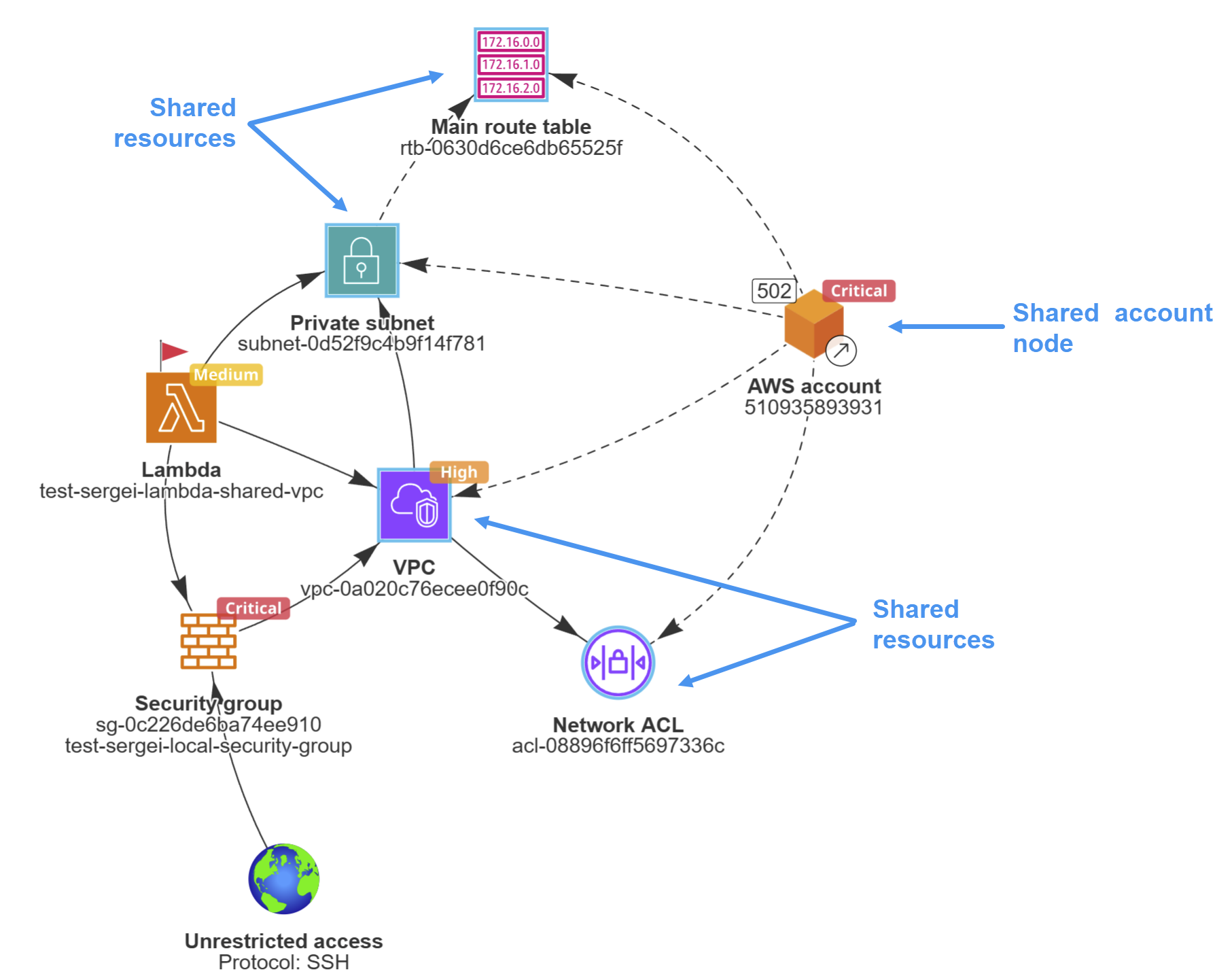
Attack Path Analysis for AWS is now available in Application Discovery, identifying when an application is potentially exploitable due to public reachability, overly permissive security groups, and known vulnerabilities or malware. When detected, ACE visually highlights the attack path in the microservice graph and shows how a compromised instance could impact downstream AWS services. Clear, actionable remediation guidance helps teams eliminate potential attack paths and reduce application-level risk. See Attack Path Analysis (AWS). (released 6-January-2026)
Flow Log Analysis for AWS is now available in Application Discovery, providing high-level visibility into real-world application traffic patterns and potential exposure. Guided steps for configuring AWS VPC Flow Logs for ACE Cloud App Analyzer make it easy to get started. See Flow Logs Analysis (AWS) and Permission Diagnostics for the Flow Logs . (released 6-January-2026)
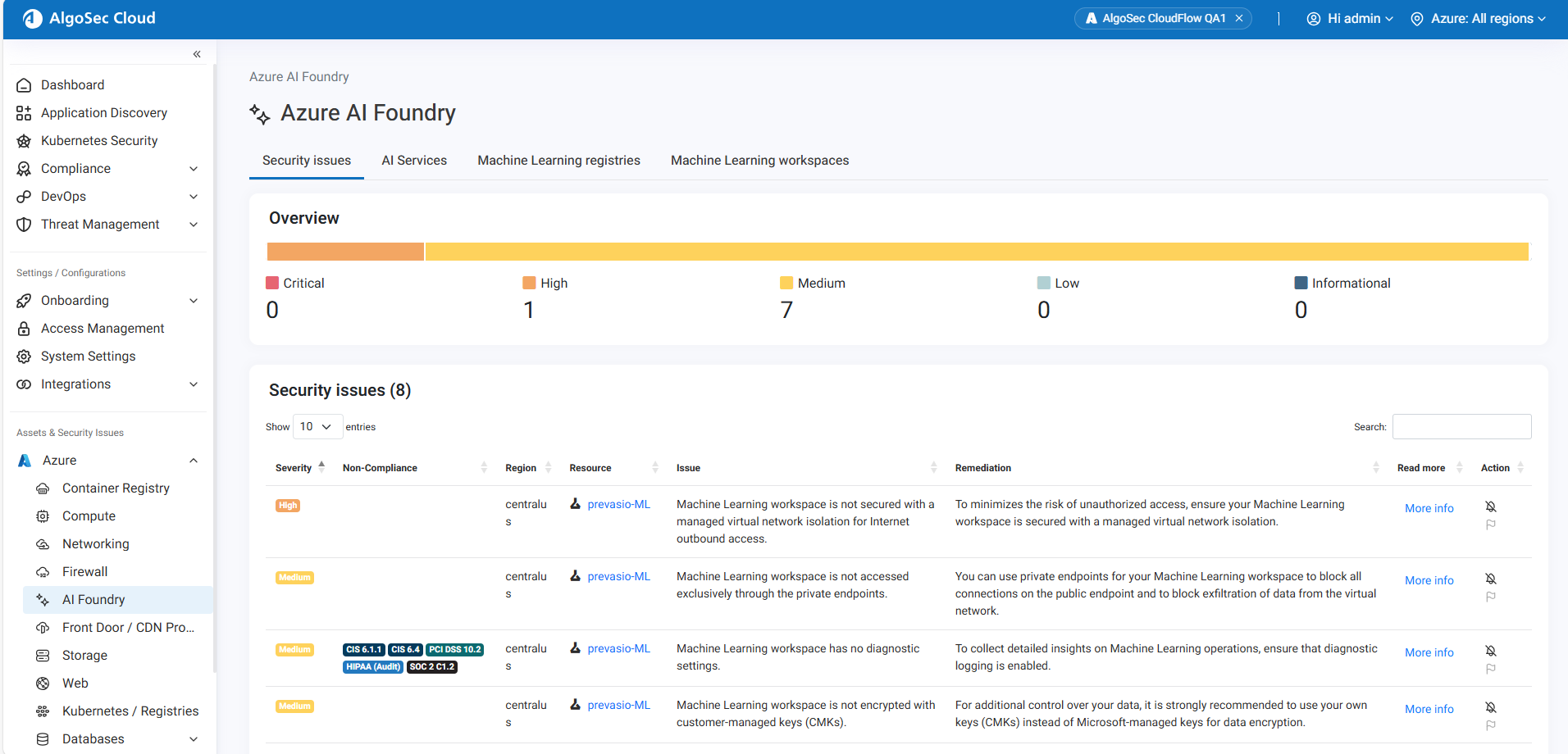
Azure AI Foundry Support in App Discovery
App Discovery now includes a new Azure AI Foundry resource category, expanding visibility into AI and machine learning services. This category covers AI Services, ML Registries, and ML Workspaces, which are automatically discovered and analyzed. New security risks are reported for these resources, and the ACE Cloud App Analyzer UI has been updated with an AI Foundry dashboard tile, an Azure AI Foundry category in the left-hand menu, and AI Foundry resources displayed alongside other resource types. (released 6-January-2026)
CAA December 2025 Update
Support for AWS Bedrock Resources
ACE Cloud App Analyzer now supports Amazon Bedrock, AWS’s fully managed generative AI service. Analyzer can now discover and collect misconfigurations for resources created in the Bedrock service. Bedrock detection supports Agent, Custom models, Model customization jobs, Knowledge base, and Guardrail resource types. To enable this support, we have added three new permissions:
-
bedrock:GetAgent
-
bedrock:GetKnowledgeBase
-
bedrock:GetGuardrail
See Permissions Required for AWS Accounts. (released 8-December-2025)
Custom Roles for Cloud App Analyzer Features
You can now create custom roles for Cloud App Analyzer features. See Custom Roles. (released 1-December-2025)
CAA November 2025 Update
Azure NIS 2 Compliance Scanning
Now for Azure, Cloud App Analyzer helps you stay compliant with the NIS 2 standard across all your cloud assets and applications. The NIS 2 compliance framework is designed to enhance the security of network and information systems across the EU. (released 19-November-2025)
CAA October 2025 Update
Automated Discovery and Support for New Regions and Availability Zones
The ACE Cloud App Analyzer now automatically detects and supports new regions added to your cloud network.
-
Dynamic Region Detection: Newly added regions are automatically identified during the next scan — whether enabled by the cloud provider or by the user.
-
Enhanced Regions Menu: The Regions menu now displays all available regions for each supported service, along with the number of resources in each region. (no badge is displayed when no services are found for a certain region)
-
Updated AWS Permissions: A new AWS permission is required — account:ListRegions — This ensures the application can automatically adapt to newly available regions, maintain accurate multi-region visibility, and avoid reliance on outdated static region lists during inventory and policy enforcement tasks.
(Released 15-Oct-2025)
CAA September 2025 Update
Improved Microservice Association in Application Discovery For AWS
To improve the efficiency of application discovery on AWS, we’ve enhanced our ability to detect and group related microservices into meaningful application-level views. The system now identifies logical links between separate microservices and clusters them into a unified application context, based on insights from CloudTrail activity that reveal communication patterns and dependencies. All associated services can now be viewed within a single, consolidated graph, providing a clear and intuitive picture of the application architecture.
Also, support for VM scan results has been added to the graph visualizations. For details, see Cloud App Analyzer Application Discovery.
(Released 27-Sept-2025)
AWS CIS v4.0 Compliance Scanning
Now for AWS, Cloud App Analyzer helps you stay compliant with the CIS AWS Foundations Benchmark version 4.0 across all your cloud assets and applications. This new version expands and updates security best practices for AWS environments, enhancing protection beyond the previously supported CIS AWS v1.5.0. See Cloud Services Risks Management. (released 23-Sept-2025)
Configure Compliance Standard Visibility
You now have full control over which compliance standards are displayed in the Cloud App Analyzer interface and included in compliance findings. See Set Compliance Standards Visibility. (Released 15-Sept-25)
You can now selectively disable scans at the tenant level, giving you greater control and flexibility. All scans are enabled by default, but administrators can turn off specific scans or disable all Cloud App Analyzer scans at once. This ensures cleaner dashboards, reduces noise from failed scans, and allows you to tailor scanning activity to your organization’s needs. See Disable Scans. (Released 14-Sept-25)
Updates to the Cloud App Analyzer Dashboard
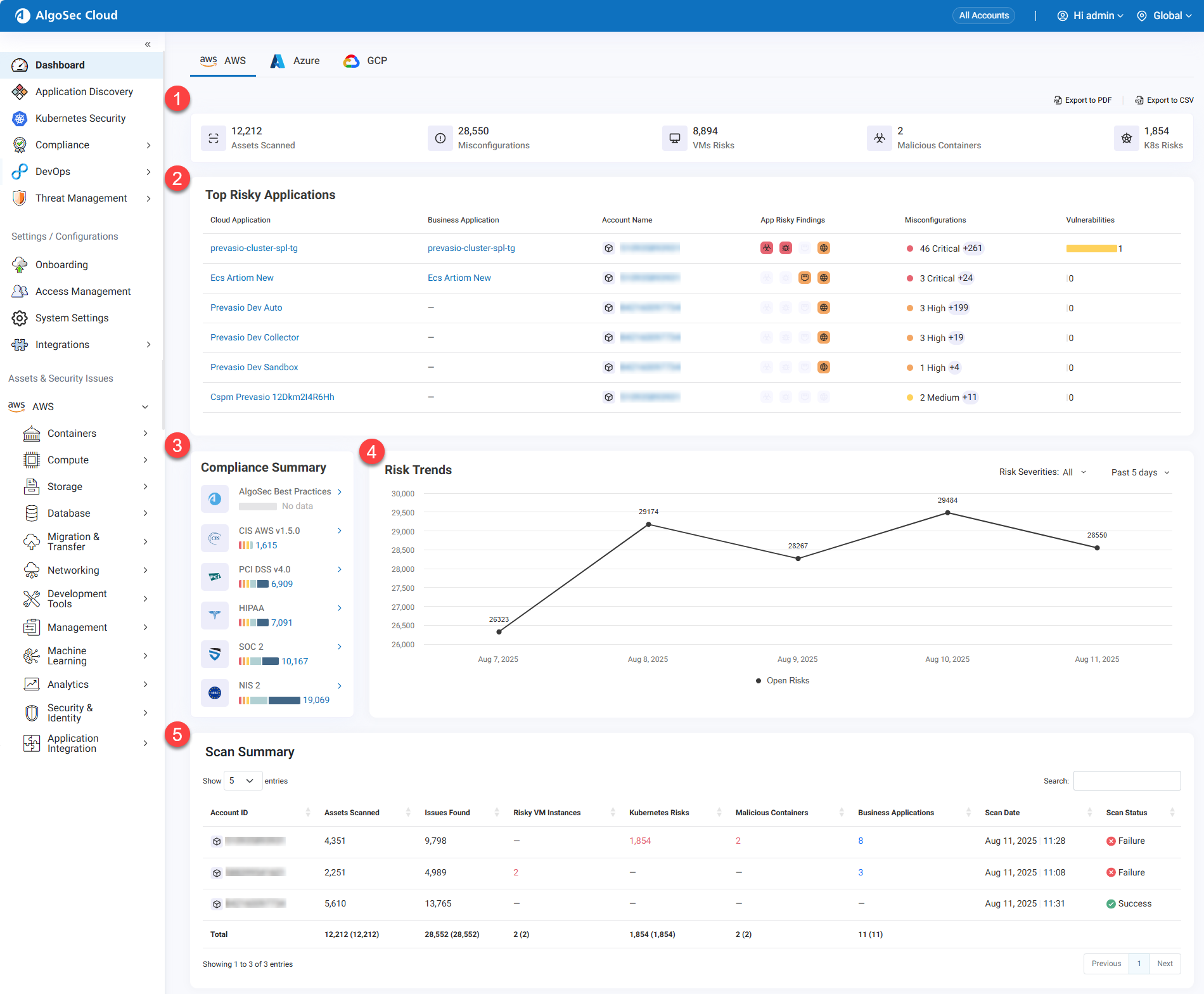
We’ve made several improvements to help you see risks, compliance, and scan results more clearly at a glance:
-
Top Bar Summary Enhancements: A new summarizing strip at the top of the dashboard. In single-account view, the top bar now also includes the Scan Status for quick visibility.
-
Top Risky Applications: Displays the top 6 highest-risk applications directly in the dashboard.
-
Compliance Summary: Now breaks down compliance information by severity level.
-
New Risk Trends in Multi-Account Dashboard: Multi-account view now includes risk trend visualizations.
-
Scan Summary Updates: The Scan Status column now uses simplified labels: Failure, In Progress, or Success, with additional details available for each status when you hover over it.
See Getting Around Cloud App Analyzer. (Released 14-Sep-2025)
CAA July 2025 Update
Improved Microservice Association in Application Discovery For AWS
To improve the efficiency of application discovery on AWS, we’ve enhanced our ability to detect and group related microservices into meaningful application-level views. The system now identifies logical links between separate microservices and clusters them into a unified application context, based on insights from CloudTrail activity that reveal communication patterns and dependencies. All associated services can now be viewed within a single, consolidated graph, providing a clear and intuitive picture of the application architecture.
Also, support for VM scan results has been added to the graph visualizations. For details, see Cloud App Analyzer Application Discovery.
(Released 10-July-2025)
Support for GCP-managed Kubernetes Service, GKE, Scanning
Now for GCP, Cloud App Analyzer now scans for Kubernetes-related risks such as risky configurations, vulnerabilities, and exposed secrets. It also integrates results from both static and dynamic container analyses for the containers running workloads in GKE. See Kubernetes Services Risks Management. (released 3-July-2025)
Now for AWS, Cloud App Analyzer helps you stay compliant with the NIS 2 standard across all your cloud assets and applications. The NIS 2 compliance framework is designed to enhance the security of network and information systems across the EU. (released 3-July-2025)
CAA May 2025 Update
AWS WAF Support in Cloud App Analyzer
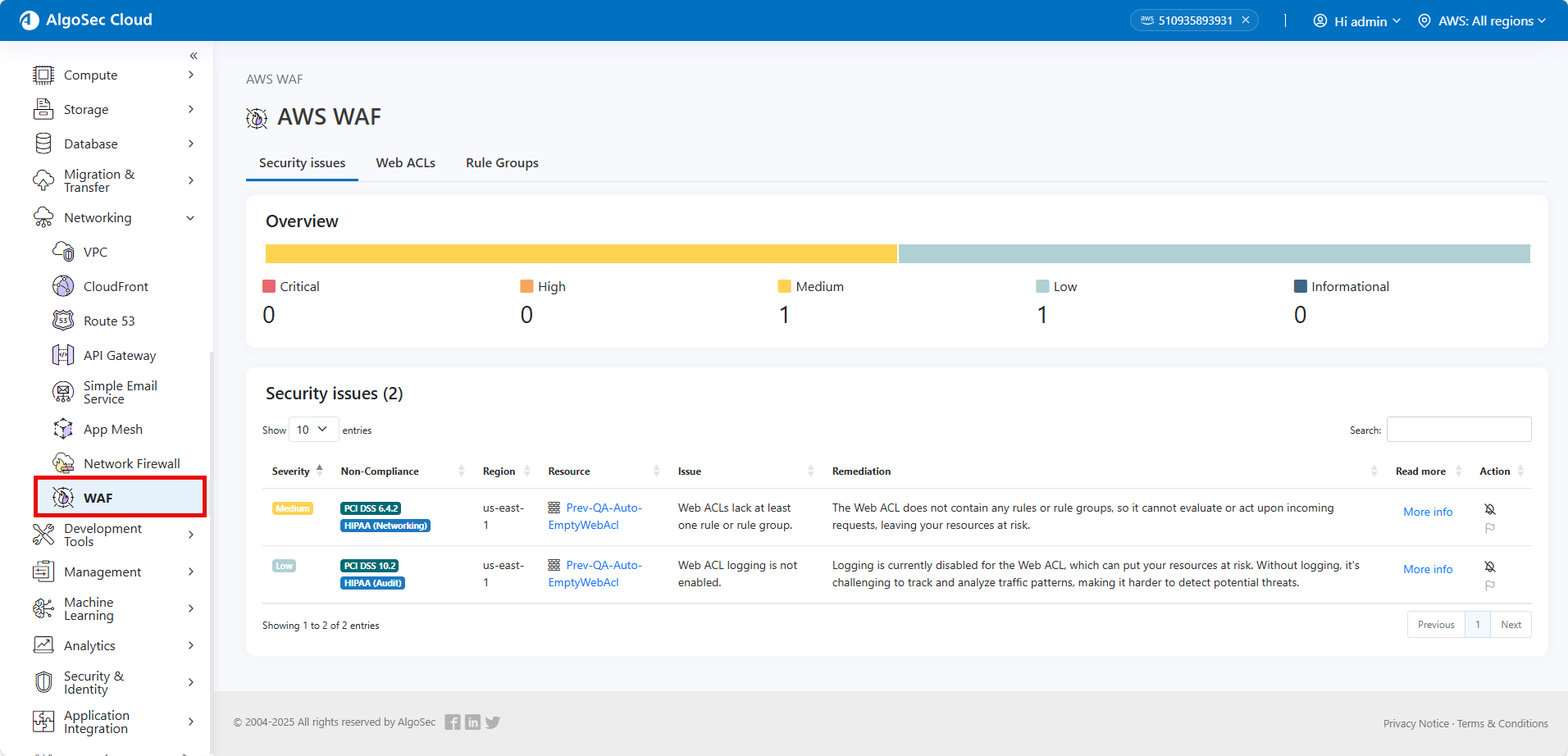
We’re excited to announce that Cloud App Analyzer now supports AWS WAF (Web Application Firewall), enabling visibility of misconfigurations. This new capability empowers you to seamlessly integrate WAF configurations into your security workflows, giving you greater control and protection. Gain insights into your Web Access Control Lists for improved application-level threat management. Analyze and manage AWS WAF rule groups to fine-tune your WAF policies. Expanded support for related AWS WAF resource types provide a more comprehensive security view. For additional required permissions, see Permissions for AWS WAF Support. (released 14-May-2025)
Global Risk Suppression Across All Accounts and Resources
In Cloud App Analyzer, you can now suppress all occurrences of a specific risk across every account and resource in your environment. Use this option to globally suppress an alert rule—ideal for company-wide risks you’ve deemed unnecessary to monitor. For details, see Suppress and Unsuppress Risks. (Released 8-May-2025)
Azure Native Firewall Misconfiguration Scans
The ACE Cloud App Analyzer now identifies misconfigurations in Azure Native Firewall. Results appear under Assets & Security Issues > Azure > Firewall > Security Issues. Specifically, CAA checks whether the Azure Native Firewall has the required tags and other CF misconfigurations. (released 3-May-2025)
CAA April 2025 Update
GCP and Azure SOC 2 Compliance Scanning
Now for Google Cloud Platform and Azure, Cloud App Analyzer helps you stay compliant with the SOC 2 standard across all your cloud assets and applications. The SOC 2 compliance framework is designed to ensure third-party service providers securely store and process client data. (released 18-Apr-2025)
View Mapped Business Applications from AppViz
You can view and manage the mapping in ACE between cloud applications discovered by ACE Cloud App Analyzer that have been imported into AppViz as business applications. See View Mapped Business Applications from AppViz. (Released 11-Apr-2025)
Powerful App Discovery Enhancements
Boost your App Discovery process with these powerful enhancements:
-
View Workload Statistics: Gain immediate insights into resource usage for discovered workloads. See View Workload Statistics.
-
Assign Application Names via Resource Tags: Get consistent naming across your infrastructure with a single tag. See Assign Application Names via Resource Tags .
-
Highlight Nodes in Graphs: Spot key resources instantly in the visual discovery graph. See Highlight nodes in the dependency graph.
-
New “Resources” Field in Microservice Table: Get a clear overview of each microservice’s constituent resources at a glance. See Resources.
(Released 2-Apr-2025)
CAA March 2025 Update
AWS cross-account resource sharing
Cloud App Analyzer now supports discovering applications whose resources are cross accounts. The AWS collector gathers ownership details for the following resource types:
-
EC2 instances
-
Internet gateways
-
Network interfaces
-
VPCs
-
Subnets
-
Route tables
-
Security groups
-
VPC endpoints
-
Network ACLs
If any resource is from another AWS account, an AWS account node is added to the dependency graph.
The badge on this node shows how many risks were detected across the applications, discovered in that external account.
Clicking the node opens the applications page with a deep link to the selected AWS account. (Released 4-Mar-2025)
Cloud App Analyzer Application Discovery now supports Azure AKS Integration
Cloud App Analyzer Application Discovery now discovers and visualizes the structure and organization of AKS clusters, highlighting Kubernetes-related risks such as risky configurations, vulnerabilities, and exposed secrets. It also integrates results from both static and dynamic container analyses for the containers running workloads in AKS. See Cloud App Analyzer Application Discovery. (Released 3-Mar-2025)
CAA February 2025 Update
Now for AWS, Cloud App Analyzer helps you stay compliant with the SOC 2 standard across all your cloud assets and applications. The SOC 2 compliance framework is designed to ensure third-party service providers securely store and process client data. (released 18-Feb-2025)
Introducing the new Cloud App Analyzer VM Scanner that enhances cloud workload security by providing agentless scanning for virtual machines, starting with support for AWS EC2 instances. This robust solution addresses the growing complexity of securing workloads in cloud environments, focusing on:
-
Vulnerability Assessment
-
Antivirus and Malware Detection
-
Exposed Secrets Identification
See Enable Virtual Machine Security. (released 7-Feb-2025)
CAA January 2025 Update
AWS Organizational Unit insights in Cloud App Analyzer
Cloud App Analyzer now displays AWS account organizational unit information (when available), expanding AWS account search and filter capabilities to include organizational units. You can view the new Organizational Unit (Account OU) column on the AWS Dashboard as well as in multi-account data tables. See Getting Around Cloud App Analyzer. (released 14-Jan-2025)
CAA December 2024 Update
Quick access to Cloud Network Security from Cloud App Analyzer
For a holistic view of your associated firewall policies and associated risks, use the new link Go to AlgoSec Cloud located in the user menu. See 6 User name (with dropdown menu). (released 17-Dec-2024)
Improved Cloud App Analyzer Navigation
We’ve reorganized the menu navigation so that it now groups items in a more logical way. This includes creating a new Settings and Configuration section. (released 17-Dec-2024)
AWS Network Firewall Networking Risk Analysis
Cloud App Analyzer now supports comprehensive risk analysis for AWS Network Firewall and Firewall Policies. This enhancement consolidates all identified issues into a single view, allowing you to easily assess risks across both firewalls and their associated policies. For each issue, you'll find detailed information, including severity levels and actionable remediation steps, empowering you to address vulnerabilities effectively and maintain a robust security posture. (released 10-Dec-2024)
CAA November 2024 Update
Streamlined Azure Onboarding: Enhanced Security with Custom Roles
We have updated the onboarding script for Azure, replacing the contributor role with a new custom role with more limited permissions, as follows:
- "Microsoft.EventGrid/eventSubscriptions/read"
- "Microsoft.ContainerRegistry/registries/read"
- "Microsoft.EventGrid/eventSubscriptions/write"
- "Microsoft.Web/sites/functions/write"
Existing customers who onboarded Azure prior then 18-Nov-2024 can now reduce the permissions by reonboarding Azure. See Cloud App Analyzer Azure Onboarding Script. (Released 18-Nov-2024)
CAA October 2024 Update
Azure onboarding script explained
We've added a new topic explaining the azure onboarding script outlining purpose and functionality of each part of the code. See Cloud App Analyzer Azure Onboarding Script. (Released 15-Oct-2024)
Enhanced Application Discovery Search field
We've enhanced the search field in Application Discovery. For both applications and microservices, you can now also search for resources types and resource labels as well as resource tags. (Released 15-Oct-2024)
Cloud App Analyzer Kubernetes Security Enhancements – AKS Integration
Cloud App Analyzer now supports Azure AKS Kubernetes Managed Service. Note that additional Azure role (Azure Kubernetes Service Cluster User Role) is required for permissions to perform a Kubernetes Services scan on the Kubernetes clusters. See Kubernetes Services Risks Management and Permissions Required for Azure Subscriptions. (Released 7-Oct-2024)
CAA September 2024 Update
Cloud App Analyzer Kubernetes Security Enhancements – EKS Integration
Cloud App Analyzer introduces comprehensive Kubernetes security monitoring, starting with AWS EKS. As Kubernetes environments become more complex, maintaining a secure posture while managing vulnerabilities and compliance violations is critical.
Key Features:
-
EKS Focus: Cloud App Analyzer now supports automatic onboarding of all Kubernetes clusters across AWS EKS, with plans for multi-cloud vendor support coming soon.
-
Auto-Discovery: Seamlessly discover all clusters within each of your AWS accounts across all regions.
-
Efficient Scanning: Each cluster undergoes an in-depth security scan by the Cloud App Analyzer Kubernetes Services scan engine. Scans take a few minutes per cluster, depending on configuration.
-
Continuous Monitoring:Cloud App Analyzer performs daily scans and continuously updates your Kubernetes security posture. Any changes, such as new clusters, deleted clusters, or new vulnerabilities, are automatically reflected, ensuring your environment remains secure and up-to-date.
By simplifying cluster management and vulnerability detection, Cloud App Analyzer helps you maintain strong security practices as your Kubernetes environment scales. See Kubernetes Services Risks Management. (Released 11-Sep-2024)
CAA August 2024 Update
Azure Support of Cloud App Analyzer Application Discovery
The Application Discovery feature has been enhanced to support Azure, expanding its capability beyond AWS. This advanced solution now identifies applications within both AWS and Azure environments, presenting a comprehensive graph of the applications' resource inter-dependencies. The graph details the application’s structure, highlights elements with security issues, and offers a visual view of complex relationships within the cloud environment. By pinpointing vulnerabilities within the application, this tool helps prioritize security issues based on their placement and impact, across both AWS and Azure platforms. See Cloud App Analyzer Application Discovery. (Released 28-Aug-2024)
CAA July 2024 Update
Kubernetes cluster risk insights
The new Kubernetes Security Dashboard to deliver insights into cluster misconfiguration, vulnerabilities and exposed secrets. Benefit from advanced visualizations and detailed analytical reports to effectively manage and mitigate security risks. See Kubernetes Services Risks Management. (Released 30-July-2024)
Cloud App Analyzer System Roles
Cloud App Analyzer now supports three system roles more granular control over user permissions, ensuring that each user has access to only the necessary features based on their role. The Admin role has full access to all settings, resources, and sections; the Security Manager role has full access except for User Management; and the Auditor role has read-only access to specified features. See Manage User Roles. (Released 23-July-2024)
New Cloud App Analyzer deployment location for Europe, the Middle East, and Africa (EMEA) region
We're excited to announce the addition of a new Cloud App Analyzer deployment location for our valued users in the Europe, the Middle East, and Africa (EMEA) region. See Logging In and Out. (Released 2-July-2024)
CAA June 2024 Update
Application Discovery Enhanced!
Our dependency graph now automatically identifies microservices within your applications. A microservice consists of an interconnected set of cloud resources that collectively perform a set of functions or service and works together with other microservices to form the larger application. See Cloud App Analyzer Application Discovery. (Released 23-June-2024)
Export your dashboard to PDF or CSV
Export your dashboard views to files in PDF or CSV format, for both single and multi-account views. This enables you to easily share the data with others or perform further analysis in a spreadsheet program. See Getting Around Cloud App Analyzer. (Released 21-June-2024)
CAA May 2024 Update
Introducing Application Discovery
Application discovery is an advanced solution designed to identify applications within customer environment and present a graph of the applications' resource inter-dependencies. This graph details the application’s structure and highlights elements with security issues, offering a view of the complex relationships within the cloud environment. By showing where vulnerabilities occur within the application, this visual tool helps prioritize security issues based on their placement and impact. See Cloud App Analyzer Application Discovery. (Released 21-May-2024)
View GCP AR CD mitigation scan history
The GAR CD Mitigation Scan History Page provides a provides a scan log of each deployment of an image in the AR . You can view a summary of all scan history or drill down for details of each GCP project. See Enable Threat Management on GCP AR. (Released 16-May-2024)
â See also: