User-Defined Network Zone Definitions: Enhanced Risk Accuracy
Note:
User-Defined Network Zone Definitions are configured as part of Custom risk profiles based on Standard Plus and affect how risks are calculated. Before defining User-Defined Network Zone Definitions, review Manage Risk Profiles to understand how Standard, Standard Plus, and Custom profiles impact risk analysis. See Manage risk profiles.
Note:
-
This feature currently applies to Azure Native Firewall.
-
For AWS Security Groups (SG): This feature is available in Early Availability upon request. Contact Support to enable user-defined zone-based risks for AWS SG. Once enabled, all AWS SG risks are recalculated using the Standard Plus risk profile, and some risks may reappear with new risk IDs.
Important: Customers who also use Azure NSG should not enable this Early Availability feature. When enabled, some Azure NSG risks may disappear.
-
To use Network Zone Definitions with Global Trusted Host Groups, see Interaction with Zones (Internal / DMZ / External)
This advanced feature enables precise definitions of network zones, leading to more accurate risk assessments and management, customized for the unique configurations of your environment.
RFC 1918 addresses are designated for private networks. ACE typically identifies these addresses as local IPs, setting them apart from public IPs in risk calculations. This binary classification, however, may not reflect the operational realities of all customers.
Our advanced approach enables custom zone definitions for our customers whose network configurations extend beyond the scope of RFC 1918's definitions of private IP definitions.
With the implementation of new zone definitions, affected risk profiles will undergo significant changes. To improve accuracy, RFC and Zone IP lists are updated only for IPs that are specifically routed by each individual device. The reclassification of network zones will affect the perceived security posture, and as a result, the risks associated with different segments of your network may increase or decrease.
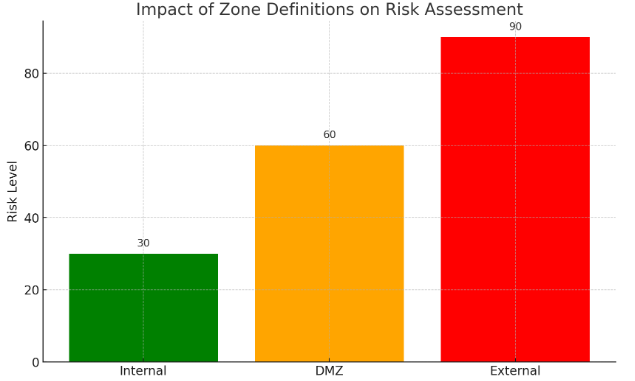
The following diagram shows how risk levels vary based on the zone classifications within the network environment:
It is important to review your security policies and risk management strategies in light of these updated classifications. The more detailed the network segmentation, the more granular the risk assessment will be, allowing for a sharper focus on potential vulnerabilities.
How does it work?
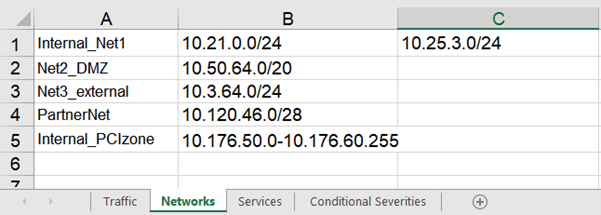
When you create a Risk Profile excel file, you can define these zones on the Network tab of the spreadsheet.
Using specific naming conventions for zones enables you to categorize them as internal, DMZ, or external. This method supersedes the default IP-based zone definitions within the RFC 1918 scope.
Networks are assigned to zones based on the following naming conventions:
|
|
Networks names containing the string 'Internal', regardless of case, are classified as internal zones. For example, Internal_Net1 |
|
|
Networks names containing the string 'DMZ', regardless of case, are classified as DMZ zones. For example, Net2_DMZ |
|
|
Networks names containing the string 'External', regardless of case, are classified as external zones. For example, Net3_External |
|
|
Networks whose names do not include the zone definition will behave as internal zones. These include networks whose names do not include the zone naming convention. |
Important: Network names must not include multiple zone indicators (for example, DMZInternal_xy).
 Internal
Internal DMZ
DMZ External
External undefined
undefined