What's New in ASMS A33.10
Release date: May 2025

We're thrilled to announce the release of ASMS A33.10, a significant update designed to empower your security operations and streamline compliance across hybrid and multi-cloud environments.
Highlights in this release include:
-
Advanced support for AWS Load Balancer available in Early Availability and Cisco Catalyst SD-WAN in General Availability, providing unprecedented visibility into complex network topologies.
-
We’ve enhanced Application Discovery with two new methods: AI Powered Application Discovery via Firewall Analyzer, and Import ACE Cloud App Analyzer Applications to AppViz— making application management both faster and smarter.
-
Compliance and risk management reach new heights with the introduction of a dedicated DORA Compliance report, NCA ECC Compliance report, integrated MITRE ATT&CK mappings, and SOC 2 compliance scanning across your cloud assets and applications.
Devices & Orchestration:
Support for IPv6 Visibility for Palo Alto Networks Panorama Devices
Release A33.10 offers IPv6 support for Palo Alto Panorama, which allows you to view policies and perform policy searches that include IPv6 objects, enhancing flexibility and efficiency in your network security operations.
Rule Modification | ActiveChange for Palo Alto Networks
You can now use ActiveChange to automatically implement changes in the rule modifications workflow for your Palo-Alto Panorama devices.
Support for Check Point Next Generation Firewall User Identity
We've introduced enhanced Check Point NGFW user identity capabilities with support for Access Role Objects (combining both network and identity) in policy management and Traffic Simulation Queries. Network details are now included in the Hostgroup definition for quick reference, while user information becomes visible upon hovering over the relevant object—making it easier than ever to manage user-based traffic control.
Check Point Syslog-based Traffic and Audit Log Collection
In this release, we have streamlined event processing by adding support for Check Point Syslog traffic log collection via the Log Exporter functionality. Meanwhile, audit logs continue to be collected for all CKP devices during analysis and monitoring. For devices running API version 1.6.1 or later, these audit logs are gathered via REST API, while older devices or instances of REST API failure will utilize SSH/OPSEC for audit log collection. See Add Check Point devices.
Edit Work Order support for Azure Firewall
FireFlow now allows you to edit Azure Firewall Work Order Recommendations. For more details, see Azure Firewall behavior.
AWS Load Balancer (Topology)
We've introduced (in Early Availability) AWS Gateway Load Balancer (GWLB) support within Traffic Simulation Query, enabling more comprehensive visibility and analysis of traffic flows. Additionally, we’ve added device tree and map support, making it easier to visualize and manage AWS GWLB configurations for enhanced network efficiency and security. For more details, see Display AWS Gateway Load Balancers in the device tree and network topology map.
Support for Cisco Catalyst (Viptela) SD-WAN (Topology)
ASMS now robustly support for Cisco Catalyst SD-WAN, encompassing seamless connectivity, device tree and network map visualization, Traffic Simulation Query functionality, and route lookup capabilities—all accessible through vManager. These features help streamline your SD-WAN management and ensure greater visibility and control across your network environment. See Cisco Catalyst SD-WAN devices in AFA.
Security Estate Visibility
User Interface Enhancements | Device Policy Page and More
Updated look and feel of a number of pages like Device Policy, Risk Profile administration, Changes Tab, Policy, and all report pages.
Automated Rule Removal or Disabling from the Policy Tab
From the Firewall Analyzer’s Policy page, you can open a FireFlow change request to remove or disable rules. See Automation from the Policy tab.
Regulatory Compliance | New DORA Compliance Report
 DORA applies across all European Union (EU) member states, ensuring a harmonized approach to operational resilience in the financial sector. See REGULATORY COMPLIANCE page.
DORA applies across all European Union (EU) member states, ensuring a harmonized approach to operational resilience in the financial sector. See REGULATORY COMPLIANCE page.
Regulatory Compliance | New NCA ECC Compliance Report
 Guidelines for cybersecurity controls as stipulated by the National Cybersecurity Authority of Saudi Arabia. See REGULATORY COMPLIANCE page.
Guidelines for cybersecurity controls as stipulated by the National Cybersecurity Authority of Saudi Arabia. See REGULATORY COMPLIANCE page.
MITRE ATT&CK Integration

We have mapped MITRE ATT&CK details to ASMS risk definitions, enhancing the correlation between known adversary tactics and your organization’s risk framework. This improvement provides clearer insights into how identified risks align with MITRE ATT&CK techniques, facilitating a more comprehensive security posture.
Rule UUID visibility in Firewall Analyzer Trust Traffic forms for Check Point and Palo Alto Networks
You can now see Originated from Device details on the Trusted Traffic tab that shows from which device the trusted rule originated. When viewing Panorama devices over version 10 and Check Point devices, you can also enable the Originated from Rule column to see the UUID of the rule. For more details, see Customize trusted traffic.
Platform:
New APIs in A33.10
New Firewall Analyzer APIs:
|
Implicit rules |
|
New FireFlow API:
Security updates | Support for TLS 1.3 and AES Key Rotation
-
We have introduced TLS 1.3 support in A33.10, bringing enhanced security and faster encrypted communications to our platform.
-
AES Key rotation:
-
Automatic key rotation upon major version upgrade: Whenever the system is upgraded to a new major version, the AES encryption keys are automatically rotated and existing passwords are re-encrypted using the new keys.
-
On-demand CLI for key rotation: At any point in time, you can manually rotate AES keys using the CLI. See Regenerate the ASMS Encryption Key.
-
Application Connectivity:
AI‑Powered Application Discovery from Firewall Analyzer as Data Source
Use AI to identify and suggest applications to add to AppViz, accelerating and enhancing your discovery process. For further information, see AI-Driven Application Discovery in AppViz.
Import ACE Cloud App Analyzer Applications to AppViz
Now you can Import cloud applications, discovered by the ACE Cloud App Analyzer, into AppViz as business applications. For further information, see Import applications from ACE Cloud App Analyzer.
Ace Cloud Enterprise (ACE)
ACE to ASMS Unified Onboarding
We’re happy to introduce unified, one‑step onboarding: When you add your AWS account (General Availability) or Azure subscription (Early Availability) into ACE, you’re automatically onboarded into ASMS as well. ASMS inherits AWS role–based access straight from ACE, ensuring secure, consistent integration across all AWS and Azure device capabilities. And because this workflow uses ACE’s existing scripts, APIs, or any other onboarding method, it’s as flexible and robust as your organization needs..
-
For Azure, see Simultaneously onboard Azure subscriptions into ACE and ASMS
-
For AWS, see Simultaneously Onboard AWS Accounts into ACE and ASMS.
Google Cloud Project Traffic Simulation Query Support – in Early Availability
In this Early Availability feature, ASMS now lets you discover Google Cloud topology paths in the AFA map and Traffic Simulation Query, with support for both Network Firewall Policies and local VPC Firewall Rules. Enable ACE–ASMS integration, and every Google Cloud project you onboard to ACE will automatically appear in the AFA tree and map. See Google Cloud Map and Traffic Simulation Query.
ACE Cloud Network Security
-
Risks & Changes Notifications
Get notifications about risk & policy changes sent via email and Microsoft Teams to selected users
-
CSV reports for Risk & policy
AlgoSec can automatically create scheduled Policy and Risk CSV reports via APIs. The report can be used for status archiving purposes and for business integration (BI). See Export risk and risk trigger details and Export Policy Sets.
-
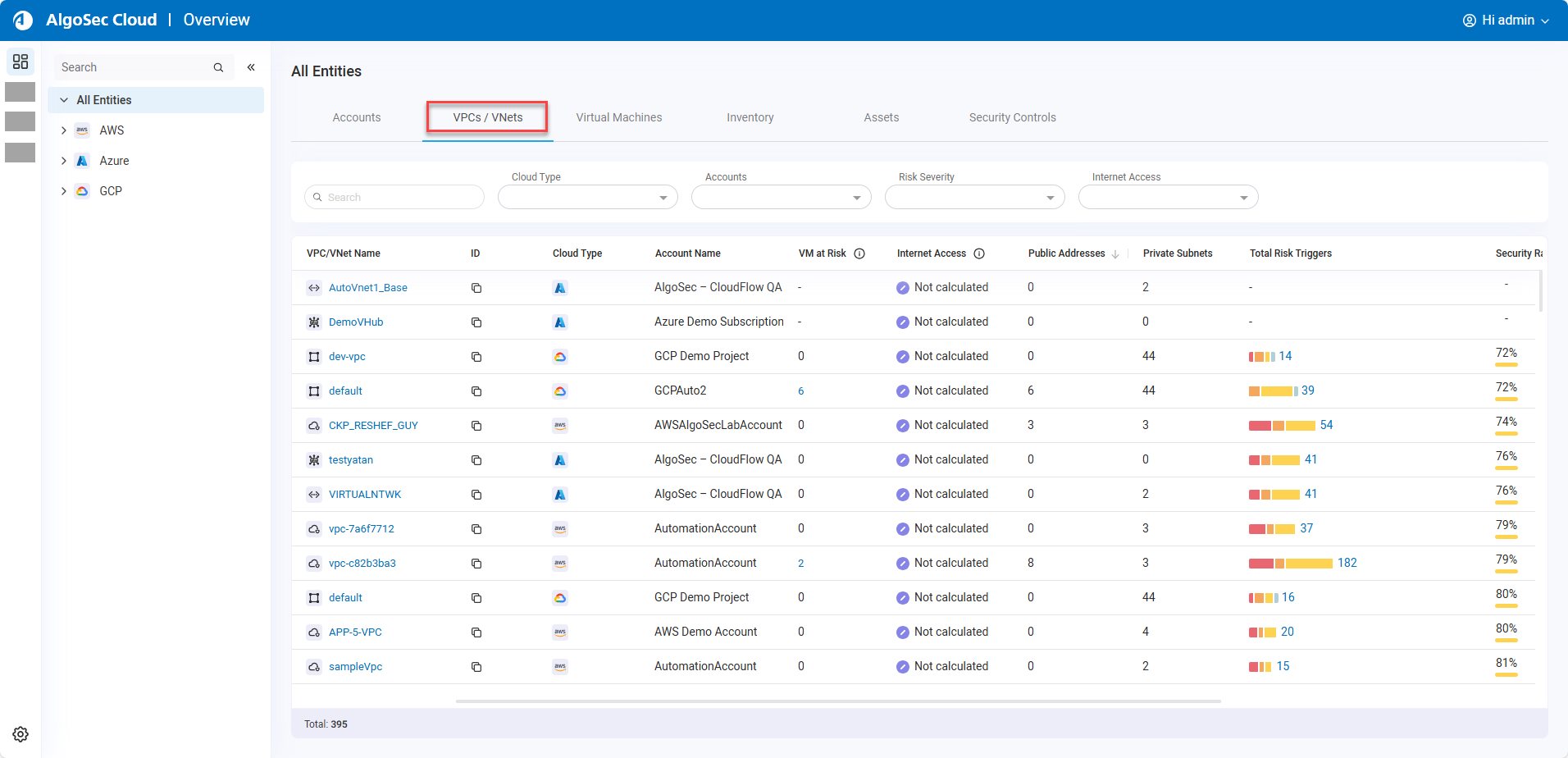
VNet/VPC overview
Explore and identify VPCs / VNets issues from a centralized tab that presents VPC / VNET related info.
-
Monitor VPC / VNet internet access
Now ACE helps you identify undesired connections to the internet. We've added an Internet Access column to the VPC / VNet tab which displays whether a VPC / VNet can access the internet from one of the private subnets defined on it. This analysis considers all the routing and policies defined on the path to the internet.
-
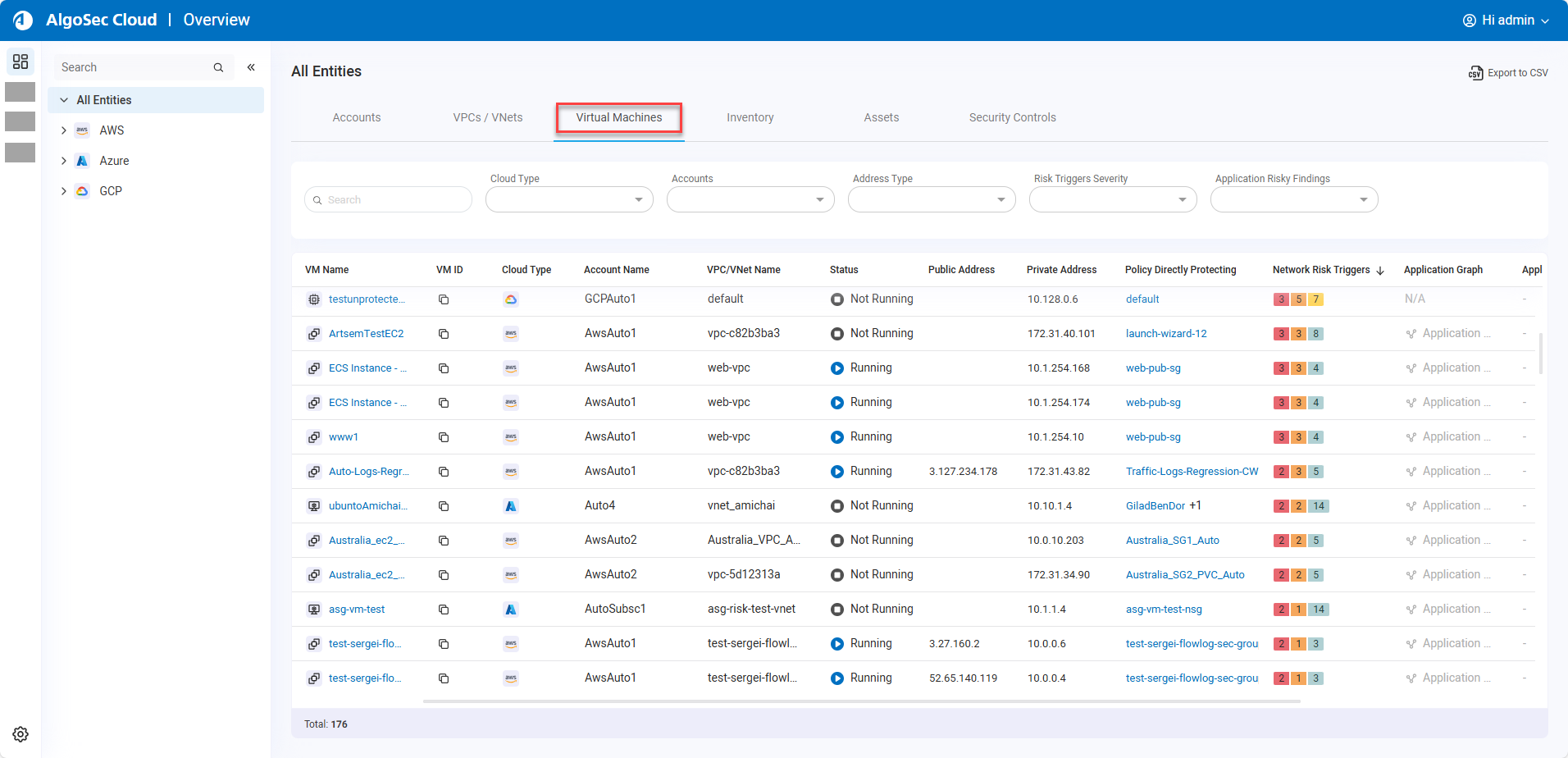
Virtual Machines Overview
The new Virtual Machine tab enables you to explore your virtual machines in a single account or across all your accounts. You can see public and private IPs configured on each VM, review the policies that directly each protect each VM and associated risks. You can also see the application dependency graph in Cloud App Analyzer associated with each VM.
-
Azure Firewall Usage Information
ACE now supports Azure Firewall usage information, leveraging Azure Firewall traffic logs to pinpoint the last time each firewall rule was used. This added visibility makes it easy to identify and generate reports on unused rules, helping you streamline policy management and optimize your Azure Firewall configuration.
-
GCP Network Firewall Policy Visibility
Cloud Network Security now supports all Google Cloud policies including Network Firewall Policy.
ACE Cloud App Analyzer:
-
Application Discovery
ACE Cloud App Analyzer Application Discovery helps you identify applications and their component microservices within your AWS and Azure environments. This makes it easier to understand how these applications and microservices connect and interact, including identifying potential security issues. See Cloud App Analyzer Application Discovery
-
New VM Scanner
The Cloud App Analyzer VM Scanner enhances cloud workload security by providing agentless scanning for Elastic Block Store (EBS) volumes attached to EC2 instances across multiple regions in an AWS account. This robust solution addresses the growing complexity of securing workloads in cloud environments, focusing on:
-
Vulnerability Assessment
-
Antivirus and Malware Detection
-
Exposed Secrets Identification
-
-
Kubernetes Security Enhancements
Cloud App Analyzer, targeting AWS EKS and Azure AKS, automatically discovers and scans clusters. Any changes in cluster configurations, such as added or deleted clusters, and updates to vulnerabilities or misconfigurations are reflected daily, ensuring users always have the latest Kubernetes security posture. See Kubernetes Security Posture Management.
-
AWS Organizational Unit Insights
Cloud App Analyzer now displays AWS account organizational unit information (when available), expanding AWS account search and filter capabilities to include organizational units. You can view the new Organizational Unit (Account OU) column on the AWS Dashboard as well as in multi-account data tables.
-
Cloud App Analyzer helps you stay compliant with the SOC 2 standard across all your cloud assets and applications.